A potential improper access control vulnerability exists in the JSON-RPC interface of the Bosch Smart Home Controller (SHC) before 9.8.905 that may result in reading or modification of the SHC's confi ...
Continue Reading
May 30, 2022
[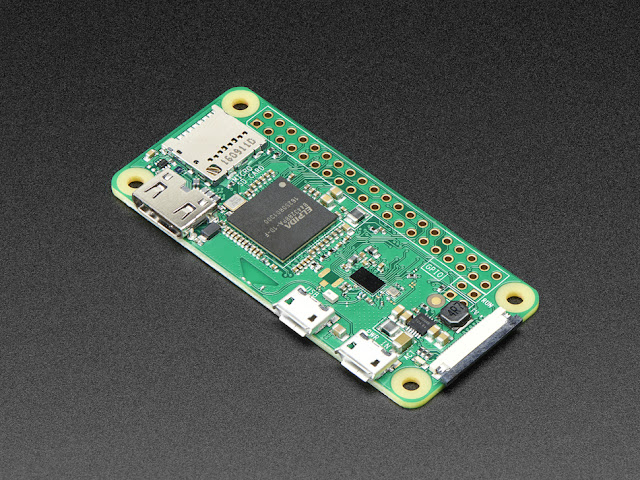]() P4wnP1 A.L.O.A. by MaMe82 is a framework which turns a R ...
Continue Reading
May 30, 2022
[]() Today, Talos is publishing a gl ...
Continue Reading
May 30, 2022
[]() Today, Talos is publishing a gl ...
Continue Reading
May 30, 2022
An issue was discovered in the firewall3 component in Inteno IOPSYS 1.0 through 3.16. The attacker must make a JSON-RPC method call to add a firewall rule as an "include" and point the "path" argument ...
Continue Reading
May 30, 2022
An update that solves one vulnerability and has two fixes is now available. Description: This update for icinga2 fixes the following issues: - Info that since version 2.12.0 following securit ...
Continue Reading
May 30, 2022
I would like to start this post by talking about Microsoft vulnerabilities, which recently turned out to be much more serious than it seemed at first glance. 
May 30, 2022

Back to Main


