
Today, Talos is publishing a glimpse into the most prevalent threats we’ve observed between Feb. 10 and Feb. 17. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, this post will summarize the threats we’ve observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, [Snort.org](), or [ClamAV.net]().
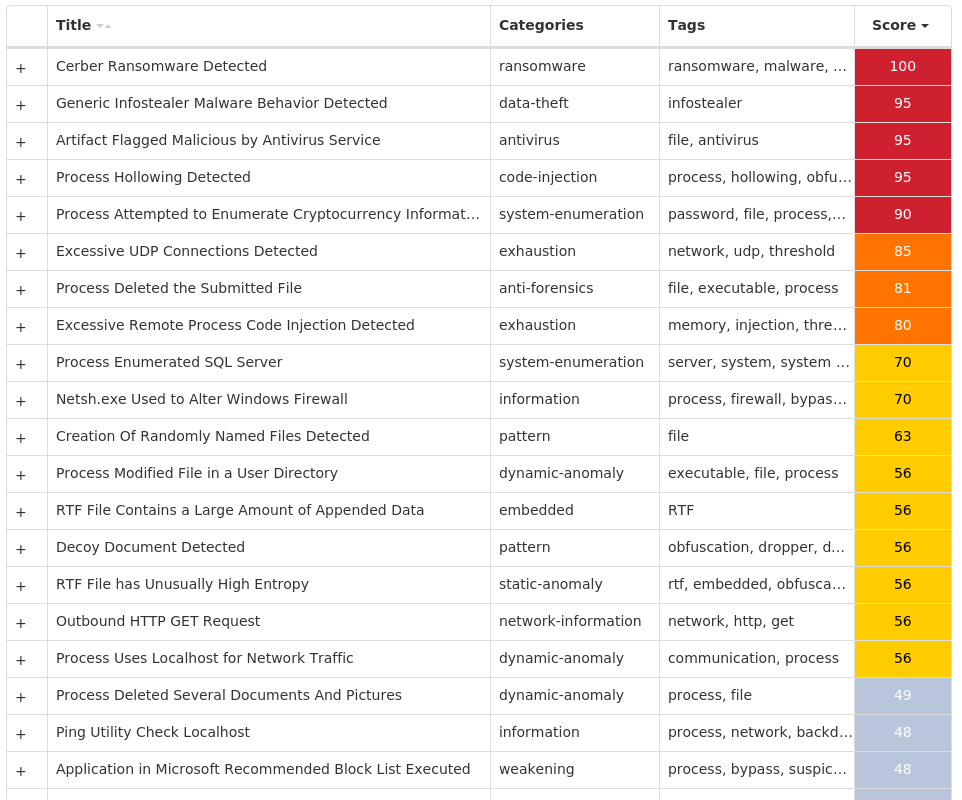
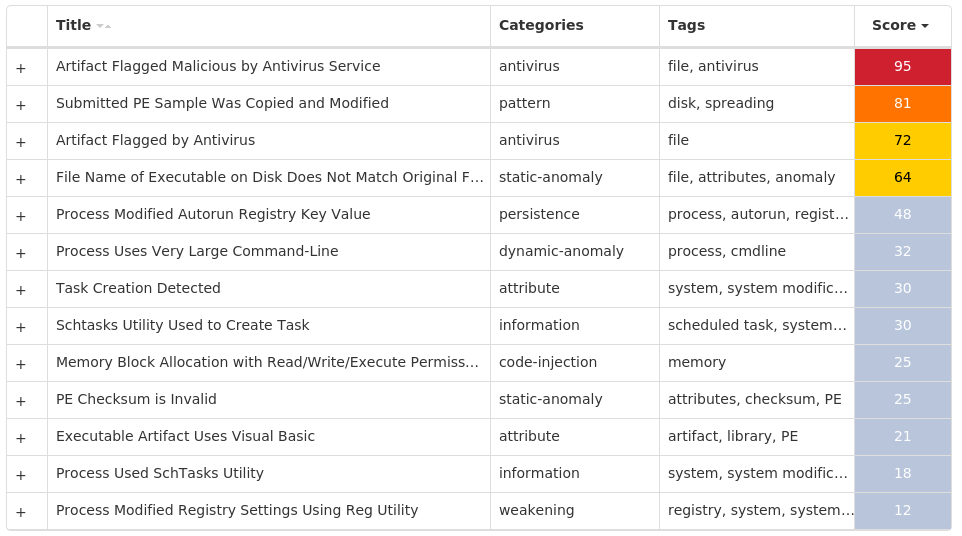
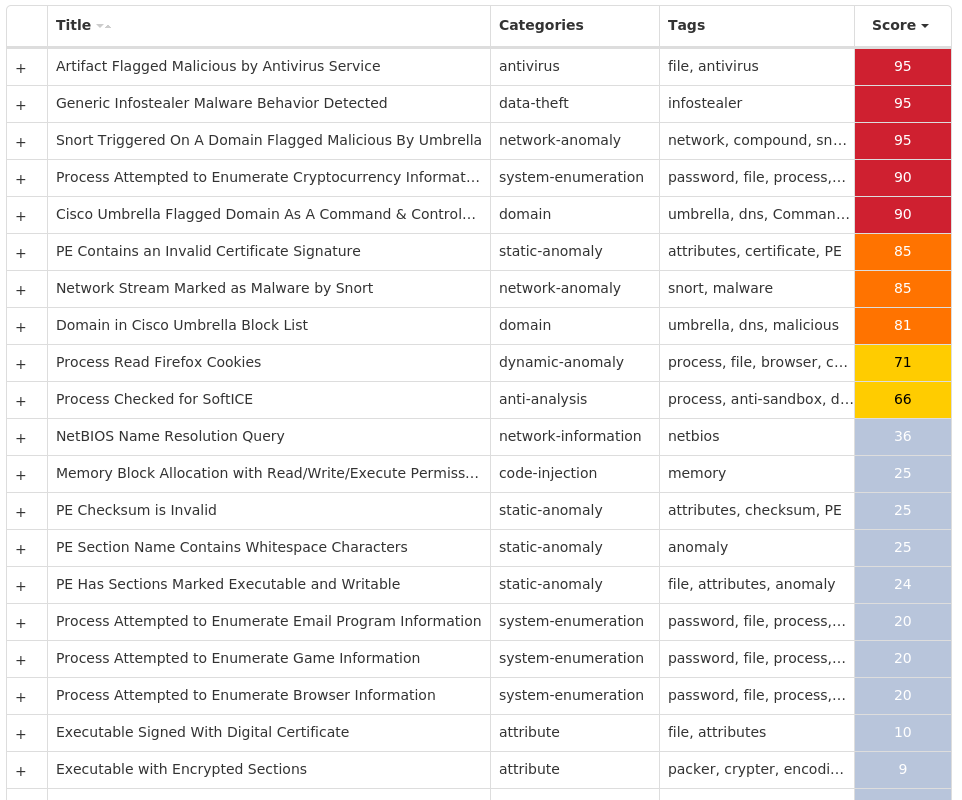
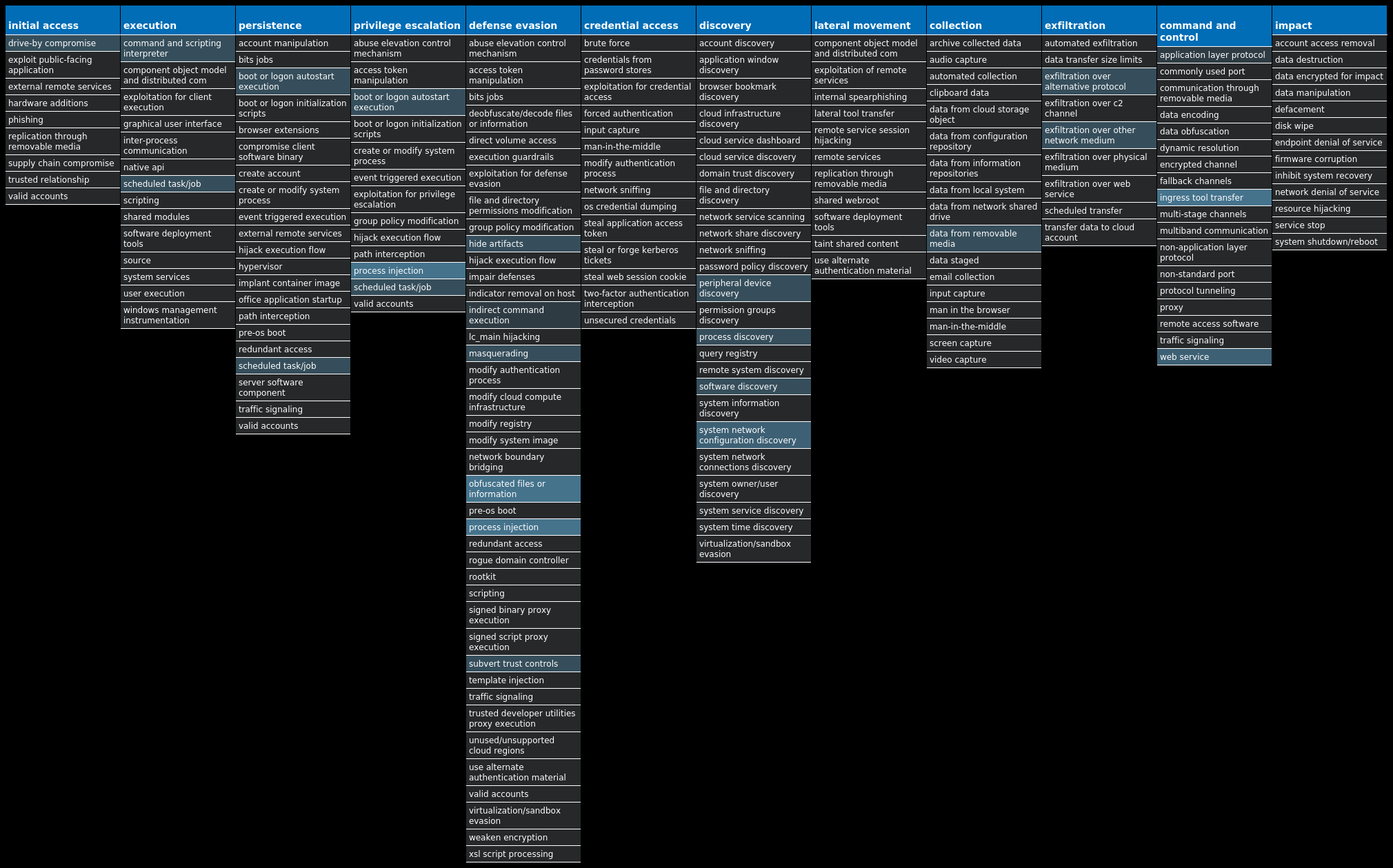
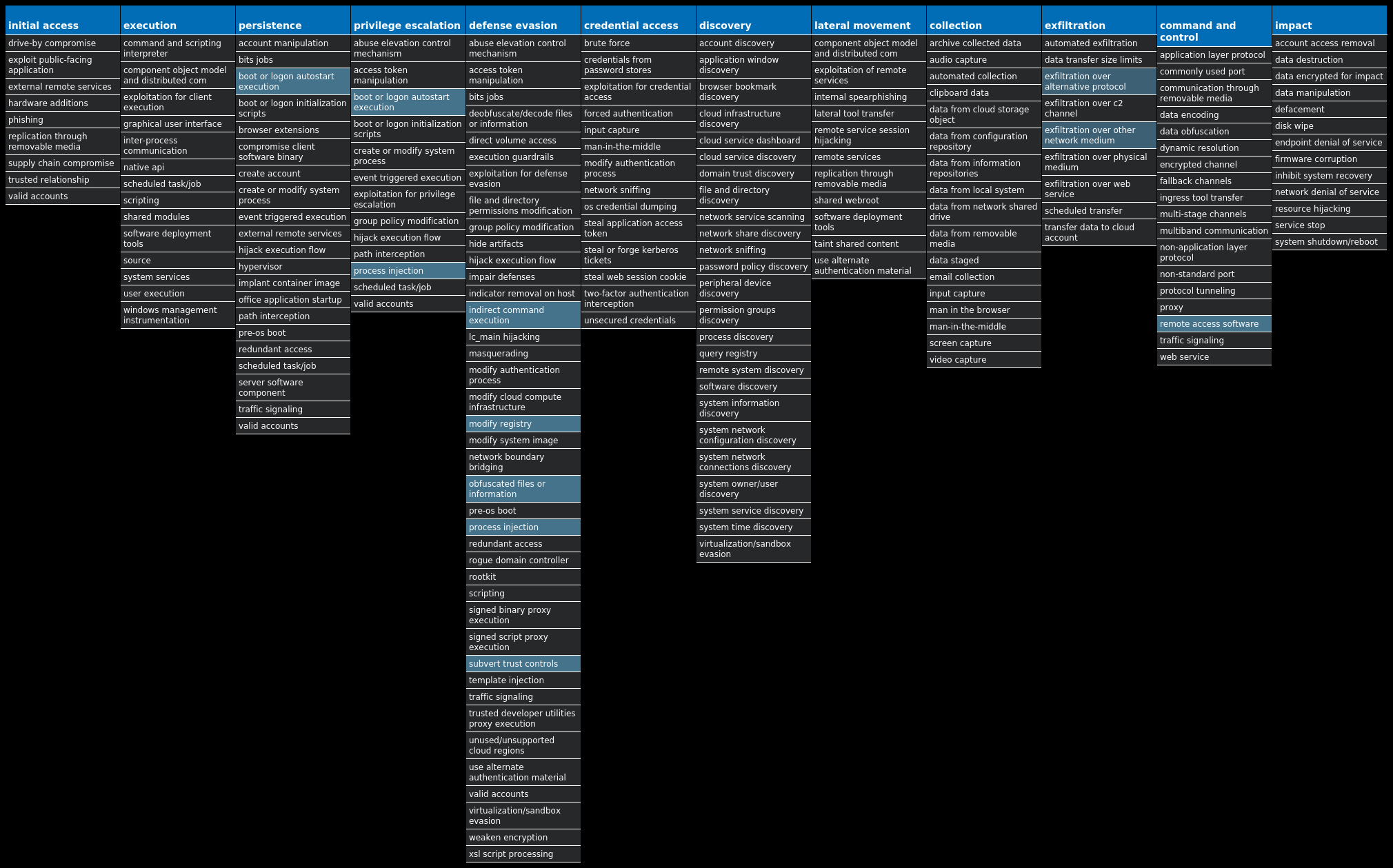
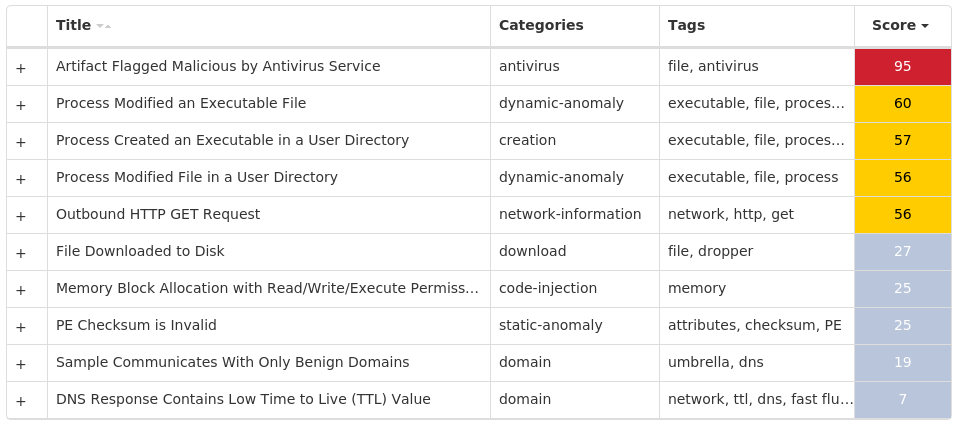
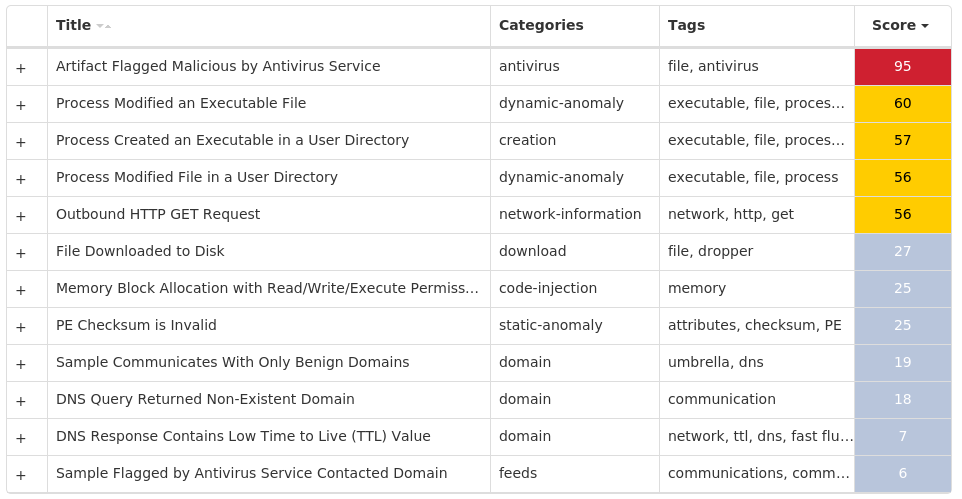
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found [here]() that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name| Type| Description
—|—|—
Win.Ransomware.Cerber-9987352-0| Ransomware| Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension “.cerber,” although in more recent campaigns, other file extensions are used.
Win.Dropper.LokiBot-9987759-0| Dropper| Lokibot is an information-stealing malware designed to siphon sensitive information stored on an infected device. It is modular in nature, including the ability to steal sensitive information from several popular applications. It is commonly pushed via malicious documents delivered via spam emails.
Win.Dropper.Ramnit-9987280-0| Dropper| Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It can also steal browser cookies and try to hide from popular antivirus software.
Win.Dropper.Gandcrab-9987386-0| Dropper| Gandcrab is ransomware that encrypts documents, photos, databases and other important files using the file extension “.GDCB,” “.CRAB” or “.KRAB”. Gandcrab is spread through both traditional spam campaigns, as well as multiple exploit kits, including Rig and Grandsoft.
Win.Dropper.TrickBot-9987411-0| Dropper| Trickbot is a banking trojan targeting sensitive information for certain financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB scripts.
Win.Dropper.DarkComet-9987724-1| Dropper| DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. The malware can download files from a user’s machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
Win.Packed.Shiz-9987720-0| Packed| Shiz is a remote access trojan that allows an attacker to access an infected machine to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site.
Win.Packed.Zbot-9987774-0| Packed| Zbot, also known as Zeus, is a trojan that steals information such as banking credentials, using methods like key-logging and form-grabbing.
Win.Malware.Upatre-9987791-0| Malware| Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables such as banking malware.
* * *
## Threat Breakdown
### Win.Ransomware.Cerber-9987352-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 11 samples
Mutexes| Occurrences
—|—
`shell.{381828AA-8B28-3374-1B67-35680555C5EF}`| 11
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`94[.]21[.]172[.]0/27`| 11
`94[.]22[.]172[.]0/27`| 11
`94[.]23[.]172[.]0/22`| 11
`178[.]128[.]255[.]179`| 10
`104[.]20[.]21[.]251`| 5
`172[.]66[.]42[.]238`| 5
`172[.]66[.]41[.]18`| 5
`104[.]20[.]20[.]251`| 4
`172[.]67[.]2[.]88`| 2
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`api[.]blockcypher[.]com`| 11
`bitaps[.]com`| 10
`chain[.]so`| 10
`btc[.]blockr[.]io`| 10
`hjhqmbxyinislkkt[.]1j9r76[.]top`| 1
Files and or directories created| Occurrences
—|—
`%TEMP%d19ab989`| 11
`%TEMP%d19ab9894710.tmp`| 11
`%TEMP%d19ab989a35f.tmp`| 11
`%LOCALAPPDATA%MicrosoftOfficeGroove1SystemCSMIPC.dat`| 11
`_READ_THI$_FILE__.hta`| 11
`_READ_THI$_FILE__.txt`| 11
`pcuserspublicrecorded tvsample mediawin7_scenic-demoshort_raw.wtv`| 8
#### File Hashes
`06b444d20ea1a2fc7726b4e1bc2c03708cb0719dd09db2e41604dc2f30755dfc`
`14bff12c186c1042535d7ca79bab96738ddd5dbdc975ac4fb271113c01ff8c02`
`14c70464b6367a5a9afe3254d5ceb04013896506cac23bead508b4a004429157`
`17eaac07edc82c30cdcdb7e7ac163d9aa67607af29c25324de84a40fe4084e0f`
`27fb7cd60bb97d1fe8ba827b8537191511391fb49c97da1208e982c325b4bc48`
`5d14e28719b83655d43461ea60f557e24c365269ffc41993e6c51eb7fa794f1c`
`73c3883e26a9a403053c673859709b0a43fb32de196c71d86c4e7480b78207ee`
`8be38ae7931c75bc6d8cb80fc9a2d95660eb269f321970cc7da453238bcd7482`
`ca5f7747f518aa7b48e3454643860cd8d9909bbc965f6955ea70c8889ffe4504`
`dacf34683b6aaf0f233d22d99eb5af7cdab36398e2e86af52ea53464e8be1539`
`f73a96e66ead8238a4d5d83cf076456cd7e5b47558dbb5dc52e2ce9f9d91beac`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
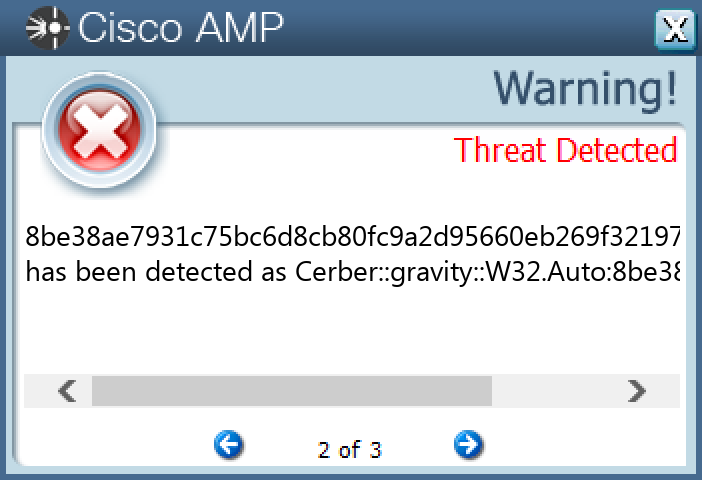
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Win.Dropper.LokiBot-9987759-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 18 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUNONCE
Value Name: LLENES`| 18
`SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONSCHEDULETASKCACHETASKS
Value Name: DynamicInfo`| 1
Files and or directories created| Occurrences
—|—
`%ProgramData%TVINDINGER.scr`| 18
`%System32%TasksLLENES`| 18
#### File Hashes
`07f02393195d8c9d597419c4ca54eb4dc90b2e847763d3d479caa69935411bc0`
`0be581f5f102f0fce5d5cf26b69942231d842cd7b221f008f0e633deeee05500`
`1621a2bb84b4c0d8e88be841f5bbf2d9457bba1d316d674faa7bc9c64bd50fea`
`1e9623428570505c6ee127a9afaa4741c2ed8958c77f59367edfeaa0660ecaa7`
`64f47d30e8f110c89ed56a7c8344bc17aa46df114ec9d19cc3dae5889ad7cd79`
`6bc3d5bdea707ec5ef5fbffd0ee59ba99b1ca0a0fdaf7bb294549b067f397a98`
`6bfeb75aef998110a3a4e1ac4f5b8dcfce294ddc87d533c78a26fe0d111c4f5f`
`7479bfd01c46646868bab0ad2839fafd1d850aa8386600a9580e1c0f53e28370`
`78bcde4345b33c5ad9a30a07e0ab9e858b93aef79a6862a1ffa2e092502484e1`
`90d22eeb34f609676a6afc04b431851565d50f497b5a731391b4a7ded766b201`
`9c5b4f080db8c8a25d52e1353d1672d72b8b663464774a6f4ed103c3c4798d67`
`9f88c5ca55ed9d689f59af586c55bbacfd9680677f8b8061377505cae622bafd`
`a18f7246f1250ba929c3c58b858939668e8ce96da1187148cb126ef399e42b8a`
`b86886b7f3d80e751d0bba0f3a22c63613be992973fe4f8f0dacf2883f8d4dde`
`c1a398db47a98d88de0ce57b36a29f67828f6ec6343bdf13e8323b33b8cddbe2`
`dc896be13aed92322cd28ddacd63286ce933c335f3f2745d9ce53fee65298c4b`
`dd355884a68a133f02930c8937e082cd4aca1124d6a1e61f0aed07bebaad053c`
`fff5ccde8416fb79e016aaadecf5abd40786c84f76d137e6d792293c40a22576`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
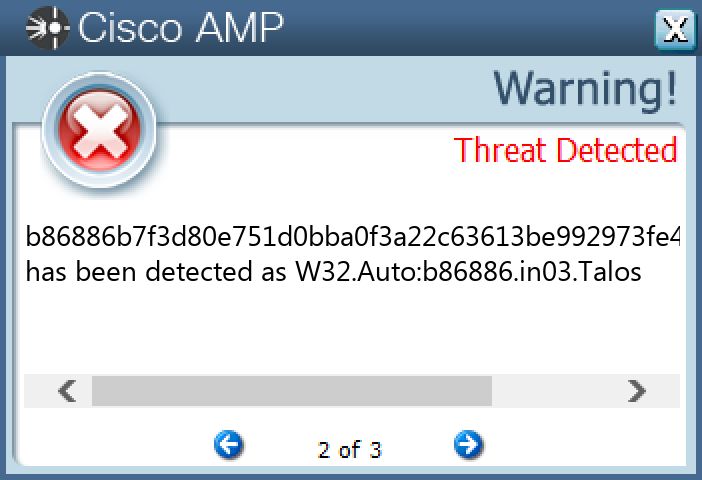
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Win.Dropper.Ramnit-9987280-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 75 samples
Mutexes| Occurrences
—|—
`b3c4139ec8994c68bbff2d53a795f301`| 17
`iwqdo`| 1
`mabwk`| 1
`bewc`| 1
`kcmkg`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`74[.]208[.]208[.]183`| 17
`74[.]208[.]175[.]106`| 8
`74[.]208[.]181[.]179`| 7
`23[.]94[.]163[.]16`| 4
`198[.]12[.]107[.]243`| 4
`198[.]71[.]56[.]73`| 3
`74[.]208[.]33[.]148`| 3
`74[.]208[.]151[.]209`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`cryptotab[.]me`| 4
`portexgame[.]xyz`| 2
`loadlink[.]xyz`| 2
Files and or directories created| Occurrences
—|—
`%System32%TasksDriverUpdates`| 17
`%TEMP%RES.tmp`| 17
`%TEMP%.tmp`| 17
`%TEMP%.dll`| 17
`%TEMP%.out`| 17
`%TEMP%.0.cs`| 17
`%TEMP%.cmdline`| 17
`%LOCALAPPDATA%Yandex`| 4
`%LOCALAPPDATA%YandexYaAddon`| 4
`%SystemRoot%Tasksiwqdo.job`| 1
`%SystemRoot%Tasksmabwk.job`| 1
`%TEMP%-5yl__pn.dll`| 1
`%TEMP%-5yl__pn.0.cs`| 1
`%TEMP%-5yl__pn.cmdline`| 1
`%TEMP%-5yl__pn.out`| 1
`%TEMP%iln_-8bo.0.cs`| 1
`%TEMP%iln_-8bo.cmdline`| 1
`%TEMP%iln_-8bo.dll`| 1
`%TEMP%iln_-8bo.out`| 1
`%TEMP%fhg_fw_h.0.cs`| 1
`%TEMP%fhg_fw_h.cmdline`| 1
`%TEMP%fhg_fw_h.dll`| 1
`%TEMP%fhg_fw_h.out`| 1
`%TEMP%_rbzi2m4.0.cs`| 1
`%TEMP%_rbzi2m4.cmdline`| 1
*See JSON for more IOCs
#### File Hashes
`02bd161beee232d6ecf9c7a8a0fe80c2545227451547459f4612c5da81ba5b5b`
`0368afd2468ede3c2a87c5988d8d880017b66907890d36285d4e878585ff1ff5`
`041401ea1601b14048afc6b726d4b417ca8aa1a6358e51744ee4a123ba636f87`
`08eb344569251e4fc99c3de92a7bf8d8ac36a1c6aa410273dd1e063ededb4a42`
`096d82b60d52de1e7ec7e85c234db5bf8140730051127e87b5e8957c332b19f2`
`0d62d5ab9c799ad6d0121505f965400007cecc4f2b7fd5f907e69bb96e1f83c4`
`0e8673929faeaed582fbb578afa829f9363e7e297e2fea9addbe5a679ae5c038`
`0fdb520255fdc09c07c596f670e077e7e974af4e9b2df6fa254ef034631d950c`
`10bbc14c15b368e4a48aba3cf2e6e0192e73e3e190c1952df5d6a13f57295d9e`
`14a3bcfe545de508cb00e55ed07bf88577f1f705ca6cdd15b733235f1d384729`
`1b6e4c705bd5306e35649e5ee0812c80a0cdfa60b045454f488dd7ef8f55d473`
`2107ea6810560dcedfc5a4ed35a11caa5619cba7cde29557642482b83dccdf27`
`2a6578cf548414e7f684ddb608b09d0584c6ee755e16bec78624368d2463b508`
`2ba72a8de72521e03d24fd9c062d7c1d11e347198f09fbfc9726f78739a50baf`
`2cf0e11b4d3ed524a99a327e52a246b73d5d91ff938bcbe58d31d4511d2b910f`
`2d3ce270807d037b5cdc8ec95351c82ad17e03508ef554cdb9b4b419d0084e26`
`2e0fc89b9e4676bf7966ed1485581ca395d01bea1ea89df0c0529f5281bc73b0`
`3642e57a9da01bd7b6b5d9a1054c21fbbc73656e7253f0b7434fc952c9761b6d`
`37e19470f3e2161ae58a9bda0a9fdce6e7ba726ee13027d5a50f7bcd1b891818`
`380bf2a2bac7a49b9dfaa3dae8b56397672108ab24f41dfb3d670ffb28f6a825`
`3a5f79652f87ccb4c9798113f7a919f9f88cf4221de4486d249a24eac1e846fc`
`3b69ea5e38470aa747535697b40dc6f5a2924ce2c44ff8b809459bdbd41edf7d`
`3c6b98c113741da5f2ac7896a314b8800bf60d90ab6e2ef7acb7380460d51f16`
`3e71f6d4e7142c28ee7fcc14925293f0c4608b0e0ae3a8e025faff261b4263b1`
`418458f7a25840f6c8b8a9982dec09d02e297b93aeb73e2e87ce30eaf171622a`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
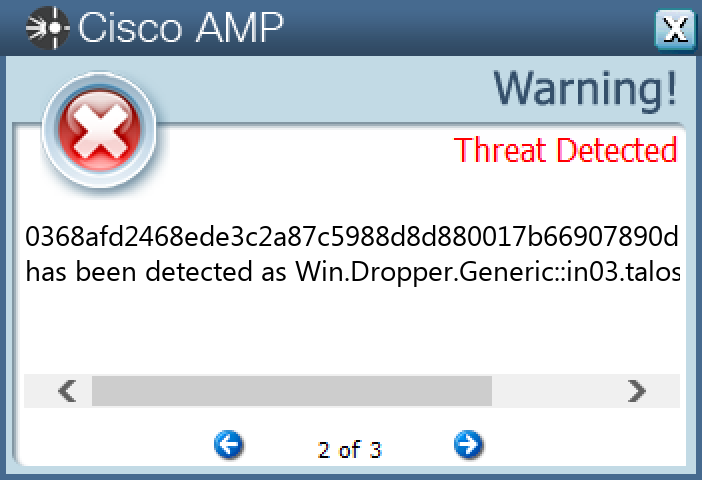
#### Secure Malware Analytics
#### MITRE ATT&CK
* * *
### Win.Dropper.Gandcrab-9987386-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 16 samples
Registry Keys| Occurrences
—|—
`SOFTWAREKEYS_DATA`| 4
`SOFTWAREKEYS_DATADATA`| 4
`SOFTWAREKEYS_DATADATA
Value Name: public`| 4
`SOFTWAREKEYS_DATADATA
Value Name: private`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXTSTATS{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}`| 1
Mutexes| Occurrences
—|—
`A16467FA-7343A2EC-6F235135-4B9A74AC-F1DC8406A`| 6
`10853E93BDB42AC8C03259A196091EB198B68E3C`| 4
`Global8B5BAAB9E36E4507C5F5.lock`| 4
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`139[.]59[.]208[.]246`| 4
`130[.]255[.]73[.]90`| 4
`185[.]121[.]177[.]177`| 4
`192[.]42[.]116[.]41`| 4
`204[.]11[.]56[.]48`| 4
`193[.]183[.]98[.]66`| 4
`5[.]135[.]183[.]146`| 4
`185[.]121[.]177[.]53`| 4
`169[.]239[.]202[.]202`| 4
`144[.]76[.]133[.]38`| 4
`51[.]254[.]25[.]115`| 4
`51[.]255[.]48[.]78`| 4
`23[.]56[.]169[.]147`| 3
`15[.]188[.]214[.]230`| 3
`51[.]15[.]229[.]127`| 2
`35[.]205[.]61[.]67`| 1
`23[.]221[.]227[.]165`| 1
`23[.]221[.]227[.]172`| 1
`13[.]37[.]189[.]21`| 1
`23[.]56[.]169[.]152`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`www[.]msftncsi[.]com`| 4
`d3s1[.]me`| 4
`kiyanka[.]club`| 4
`proxy-exe[.]bit`| 4
`www[.]billerimpex[.]com`| 4
`www[.]macartegrise[.]eu`| 4
`dom2[.]website`| 4
`apps[.]identrust[.]com`| 2
`www[.]poketeg[.]com`| 1
Files and or directories created| Occurrences
—|—
`%APPDATA%AdobeAcrobat9.0JavaScriptsKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeAcrobat9.0KRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeAcrobat9.0SecurityKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeAcrobatKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeFlash PlayerAssetCacheKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeFlash PlayerAssetCacheTRFRW6GUKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeFlash PlayerKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeFlash PlayerNativeCacheKRAB-DECRYPT.txt`| 4
`%APPDATA%AdobeKRAB-DECRYPT.txt`| 4
`%APPDATA%IdentitiesKRAB-DECRYPT.txt`| 4
`%APPDATA%KRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash Player#SharedObjectsKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash Player#SharedObjectsYXTRFETGKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash PlayerKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash Playermacromedia.comKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash Playermacromedia.comsupportKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash Playermacromedia.comsupportflashplayerKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaFlash Playermacromedia.comsupportflashplayersysKRAB-DECRYPT.txt`| 4
`%APPDATA%MacromediaKRAB-DECRYPT.txt`| 4
`%APPDATA%Media Center ProgramsKRAB-DECRYPT.txt`| 4
`%APPDATA%MicrosoftAccessKRAB-DECRYPT.txt`| 4
`%APPDATA%MicrosoftAddInsKRAB-DECRYPT.txt`| 4
`%APPDATA%MicrosoftCredentialsKRAB-DECRYPT.txt`| 4
`%APPDATA%MicrosoftCryptoKRAB-DECRYPT.txt`| 4
`%APPDATA%MicrosoftCryptoRSAKRAB-DECRYPT.txt`| 4
*See JSON for more IOCs
#### File Hashes
`011d8dcf09e7c54b212d4037f7a71ac101b38af87f59587527924ab7262fba41`
`0c9a8168c677c7d0f142bf2fb40911129fba345b6f2cc987e330200270b26e8c`
`0e24bd59a7468274a57a681b6b864591747db3af0ee1c00e24e61516b57ecc57`
`198f1ff97b3eeb1f167b6a620173f3f3dae13b2d25a9cfd4378f19904df07682`
`2c6f1952bf690b431ab3d7fb0c5e09e9d3fb23d4d77d987c12ca2b5827ef20bb`
`3dddef51b9ae680dcd1a2bb65f7c1d0a012d16bae4b34fcbc734687d29818bde`
`458c95a42deef0f5e7607899260126cf4b3c775200e9da6bad210f185d2cbff5`
`83af4f8b7564e214be08bb6565bb8639a351798be2ea899ac8d7587ece452e53`
`8f4ee5d0479a95e21085b79b27bf715e6e1a713284143945da888cfb7db34354`
`993bf34450e99ae94dc4ab207f94b5a76d9d58d5409e8c3b33997d8101ead59e`
`9a63c28232e75a2f33f12a67fcfc36b066629e969bbfc8c62a9d8fdd1228ee9c`
`b5cbe9afa4667aec874360e40ed65629e454eb3d855dc0830b6a3b8f3ba36a4d`
`d5a91ecaaa28f02c643345715e70fda018185cd6e263532b35054425d63ac790`
`f4c8798bbc75092d7f4ef15f8c03c332e3c3b573e47c206a8805b5f2350abda3`
`f7ed8a78e183bf47923b494c986ad97492a7af97cb6bd8cb4f42ab009052819e`
`ffa35debf7c75fa5edbca2a5bec9cee472fe56c376d94c30e6bb7f4ac6c9c353`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
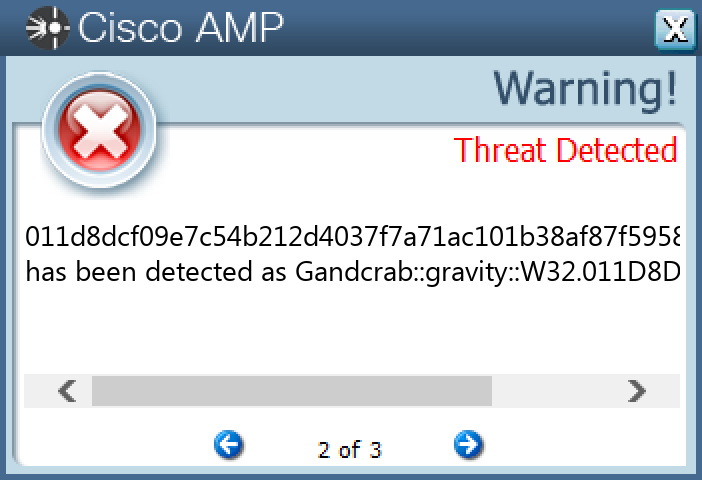
#### Secure Malware Analytics
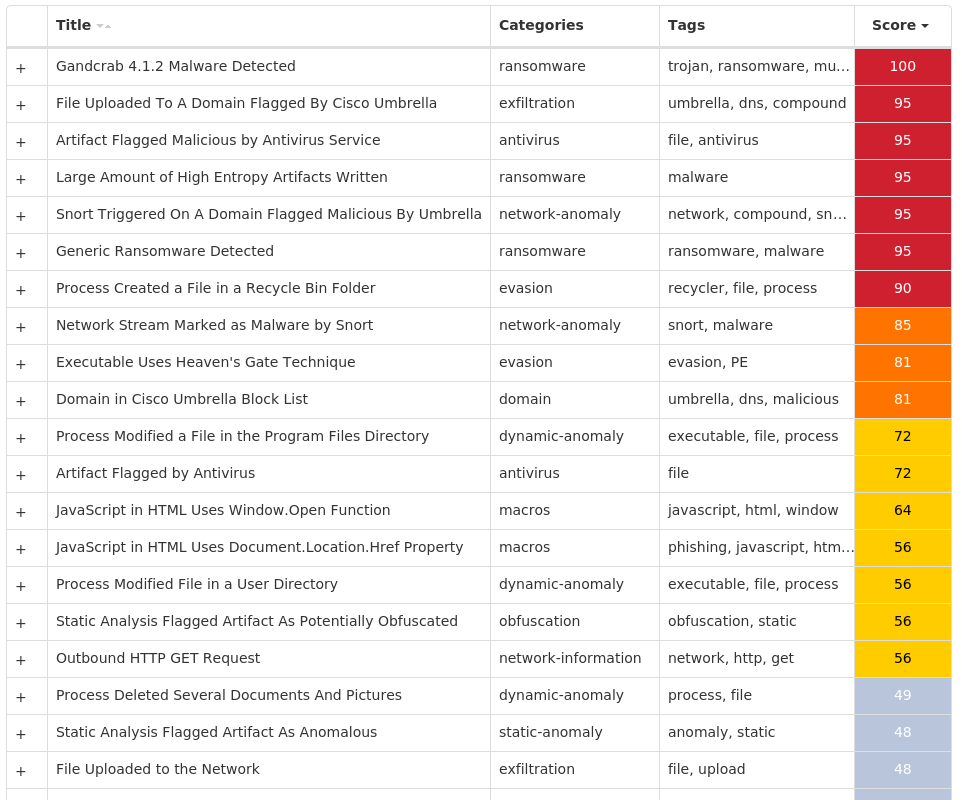
#### MITRE ATT&CK
* * *
### Win.Dropper.TrickBot-9987411-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 25 samples
Mutexes| Occurrences
—|—
`42601376242144035359`| 5
`15975048583708818909`| 4
`215537997439818625`| 3
`37191566291602894610`| 2
`32517245571140230538`| 2
`4509300882563198255`| 2
`6587820802774785799`| 2
`4012840982513237125`| 1
`10818456253260829694`| 1
`2456360213273612178`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`elosadywo[.]pl`| 5
`inydufevi[.]pl`| 4
`utesoryzy[.]pl`| 3
`oloqucovu[.]pl`| 2
`ikurumona[.]pl`| 2
`upikemugo[.]pl`| 2
`ikymucucy[.]pl`| 2
`uzawabono[.]pl`| 1
`upuhisadi[.]pl`| 1
`ufyjelefe[.]pl`| 1
#### File Hashes
`01987037a00d02cef3050228a5c851e241c6aa9ec931e109756bc999dcf1c88f`
`0c2dd463bf50ddbabc71dc084848ce95f78972c0600aa26bed751e5bef18057e`
`12a376757c742e6f94031b9286e9b4c0025092a65bdc0f0a15cc6125e66eee35`
`1932391e0efe4f06e8de343cbfb922accd4a9f2e0e4cba9c83621471713dc34f`
`1943fa2ca5fd556d27f0b571e41e0447f3dec7e9991375590133315ddcc2d7f6`
`1b9263870412c0947f709b1045f9e8fa21afd08c6444536ae261408ffbb1c046`
`1c6caf1c53dde8437efbc6efa952215dcd30e33065a0a8156a3c38435af4c3a8`
`28d76e4d23fcf2f994cbda0cc2bcee9208af9eb9cc7cefb4b737574ae12eb14d`
`2f1348fc757fe991abbcde8dfedde245bffb06270a4dd52aa210447c3b827916`
`423c4ec707ea2743fcecacd8d08826c1a885a9d1fdeae3e424bdefea426b97c3`
`52aab1fe985479e1fc98d520caa011f977ae858605cd532de95730cde39760d2`
`59756273791a7fcc28951ffbb252c5e8206487ebc1d3975f7fe1c12da5f2226c`
`5adc95e24e7a2d0cfad0fe91a94ab3ab63e3749348b8bbf5c278db267efe8b76`
`5f2c6c223db3cec8c103bbdee1321c2ff4301652ff51cf9524d91e4f7864a7d2`
`6477fa75e074c14bd33376825a9fe7f59f8e7a923828e418823769885a4f6ca8`
`6d48bb5316929dff81f3b0280a242dce971c0861cb47ba9ad3e0049025652e0b`
`71656bab86e7c96d3f293a9b0a4b5e2b6d87c454796d070760383f14d2d92c81`
`74094e2772540474f893ad07860f49cc618fee75ec8e275bdc6332ac2c1a3ced`
`82b638848df5e8f1ae07a0fda4dbe376cad1bbadaef1473742a98919e741696d`
`89c72fd3a0ad686e8277a2cc74d3ae885dbc97cafef1bb0f7560f182df098d90`
`8a6ea1a10a9ce26e7a30729c5a60cb29edbce32fa39bc8984ccbb33281688725`
`950970aeedb226f0e03d1d85966d52138f482d3500fda7c0216034304acd67d8`
`9733d44e41600aea32ec42c44016c9d3abc50973ffe7f7f8d281e7f6a13d65bd`
`9b2f63670a1e5724b69a25d6de99250636f453fe46823c6766a7dfa7ea2625b9`
`a5c2f8d2e689be5b36e6e34223323965eb8d832217af5c5f93a8bfb3c24a35f2`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
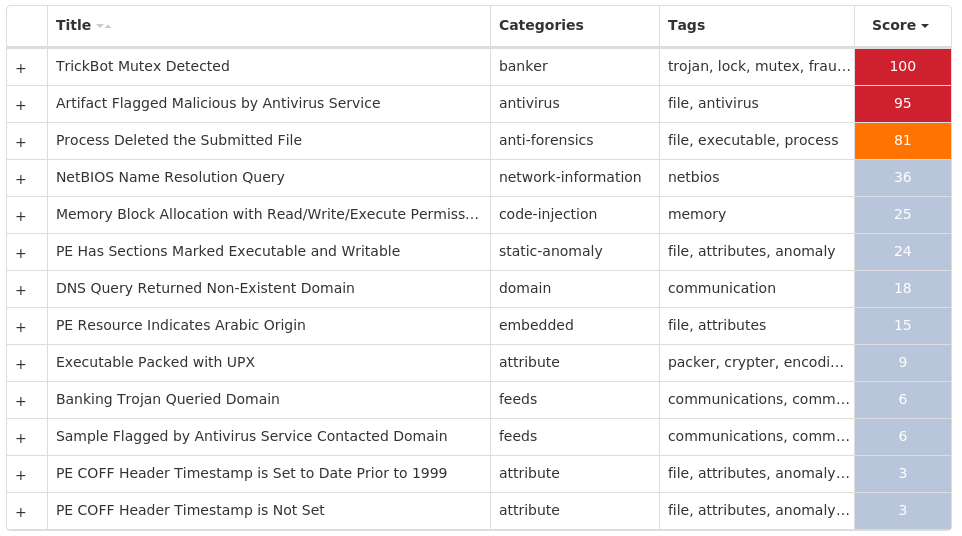
#### MITRE ATT&CK

* * *
### Win.Dropper.DarkComet-9987724-1
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 28 samples
Registry Keys| Occurrences
—|—
`SOFTWAREREMOTE
Value Name: NewIdentification`| 24
`SOFTWAREREMOTE
Value Name: NewGroup`| 24
`SOFTWAREREMOTE`| 24
`SOFTWAREREMOTE
Value Name: FirstExecution`| 24
Mutexes| Occurrences
—|—
`Administrator5`| 24
`xXx_key_xXx`| 24
`PFS7NJ0GG650A3`| 24
`Global62c608e1-84fc-11ed-9660-001517a057b6`| 1
`Global19563541-ab9e-11ed-9660-001517d2a55d`| 1
`Global19d95f61-ab9e-11ed-9660-001517a99db1`| 1
`Global1a63ada1-ab9e-11ed-9660-0015172fcdb5`| 1
Files and or directories created| Occurrences
—|—
`%TEMP%Administrator7`| 24
`%TEMP%Administrator8`| 24
`%TEMP%Administrator2.txt`| 24
`%APPDATA%98B68E3C`| 24
`%APPDATA%98B68E3Cak.tmp`| 24
`default.html`| 24
#### File Hashes
`00dd7043f8f736d307e8d432dc4d53e169a0d01bbaf18c8e9c26d3d702b5b901`
`05cf1d6e467dcacb7a8426d686aad3e467bebf56f14094a730acda703f6a8110`
`0870345c9baf599cafbdbf6c178af59bb84ca29132be8f25a99b631a5812f2c0`
`0f00ea2de2b3fbd975b0bf81b93ac892a32b9b38505ca7934975824994de5bfa`
`17358278cec9baf2cc39db83075199b08f063744cdbc368503e0d9f480599c6f`
`23b2a05f66fe4463b4a9b247e2553b3ab3e457d7692bcda4ef80b451a807cec7`
`2f21b95df665d9a895eb142d540ec232775dae8ca6d3fff982110eafd98a276d`
`31106ecb5d2fc5a71e523638369efe1f98ce94d1e972d6f21a2eac30f248756a`
`387edb31d8fbb1478a702773203645ad00d423444a7ce2213b693a35bffa1db8`
`5114f0e28f24ae8b78e9b7f1bc8a7275b8c5df906bfa5051c82cc58ef0560e19`
`51b176c359d6ccd836ba35283c65b1936f45d79ea410ea877cfc88478192ed74`
`5f97bd4dd258cc40c67b0ee332ec1404bd4a42574b1f263f417a9bae926200f6`
`6c1219e68eeb403bbca8f012f3add1a65e0a8e3657436e69adf731d0f8617199`
`6fc939a835debb66a1718a11701631bdc8485cf8481bc031a1533a566fea0df1`
`741bec34feb048eb37de1cd12cb70ed1d18e3aaa18af112538976d04fcc183ad`
`745d2dbca92dfbb840b1cbd69f71bf25248012838f1e586968ba3bfac9570141`
`7f4676305a5cc0968444f30f1cdbfa04aed721176db2d20401fffb7c596c3302`
`84644a768c0ee235e16fd5a58e022b22a620c2e88b0b1f983ae72aa8e469a0bf`
`88e478cbdf1cf481bd1b16daed1efde0eb243e144b0cf72cd27c20349dc82a93`
`89b43b0ba7a914bd0c9f14f2db38aa24a221252b9f4d53600affca3986b3c88c`
`993f856b5f28b0d05087f2d109dbf575f8fc9e9604496deb833b2af8bdc913a6`
`9f46a0aa254284347749d901fd9ca394bdbe7c9a14db990e493ed74f3b064445`
`a75a74d8013f9efed45a98a3d5b2fb21f3e0f381240582ec398270a1562e3a46`
`ab6a6f36256049b826b5034e820f8f160f19ddcbbacb32421dcf88f07f23a406`
`b1f8c81db53ca15ca183f93dab27fae3d8ffa4ecebc1edd9944abcb1cd9ae25a`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
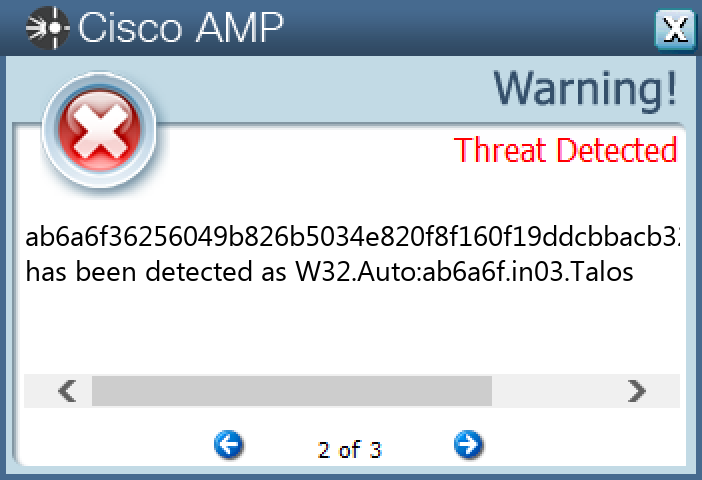
#### Secure Malware Analytics
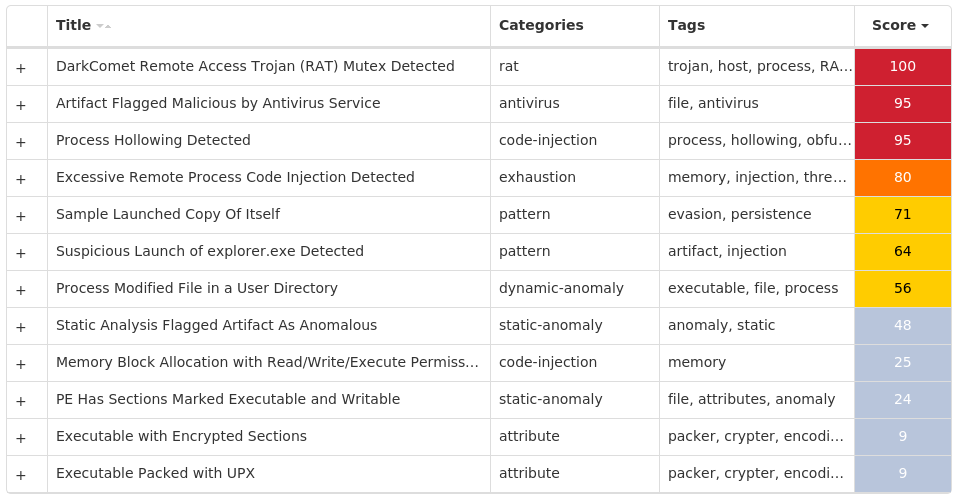
#### MITRE ATT&CK

* * *
### Win.Packed.Shiz-9987720-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 17 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: 98b68e3c`| 16
`SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: userinit`| 16
Mutexes| Occurrences
—|—
`Global`| 17
`674972E3a`| 16
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`194[.]195[.]211[.]98`| 16
`13[.]107[.]21[.]200`| 12
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`www[.]bing[.]com`| 16
`bloodguiltiness[.]com`| 16
Files and or directories created| Occurrences
—|—
`%SystemRoot%apppatchsvchost.exe`| 16
#### File Hashes
`0c2997425536269afe16a8b8b6c4be49f7e580897cad9e754ca4f381adb26bae`
`14bccab22d068b3f5b4938b0559f808b13b393490948f21c14952d6b68238eec`
`1ebc5c21db31eda328cce469c9c056a352d1ab6fcaa825b7deaf56bf05b0b832`
`1f1f395ecb32379dbb2184c475f2cb12e8ad9850830f16892283f68886def842`
`3e9ab9a9d9908138887813e35ad0e3f5939b4fd2b63500928e47b6f708f0d7c3`
`60991b4ce81c27bdf0b89e5856c2a22c662f34ad7b67f27ef14e64eef4d27e48`
`9b52e5276250652efa36ff6a4ee5212ffa7a7220db6f44ca1be7fed689b9eb86`
`9b8a1b42707e3cf61bc5167c45287c231c15f05d21c781512ba7a42418fa663e`
`ae0e6672faa1fed222b66f2f28e5a84bdfc6eb2b870e12d1017bdb31b8bda566`
`ae70ed3cc01b0631a382136060c3085407e98e09205ed786b9fee5e5a20a139d`
`b49e6e226ecfbe22f5e14f8581e5fbdf82e0660b31aac0d91a59252100f535e6`
`c4211dcd759802490cf3295c434c6f406f65c3b4b4e53292e1daaaaa5cf13d0e`
`cb1505686cf31cdd0ff71e5c3dc3875f7e3f90166996dbaf04956f39bb7fbb40`
`ce6e4769ebfda72940dc984db39956ef6f1f0becdd076262f4181a29f7591b54`
`d27abb5761c73a05e6d2e729fc5a39f0de881d44e81465a2e5742ee251a61386`
`d2a13fc8ea13355725e0db940203aaf57acc059464735950345defc4140ff4d0`
`f7e62e5bcc96a9820b674ef0134222e0050acb2035b8f8260e84b6afcc6e643d`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
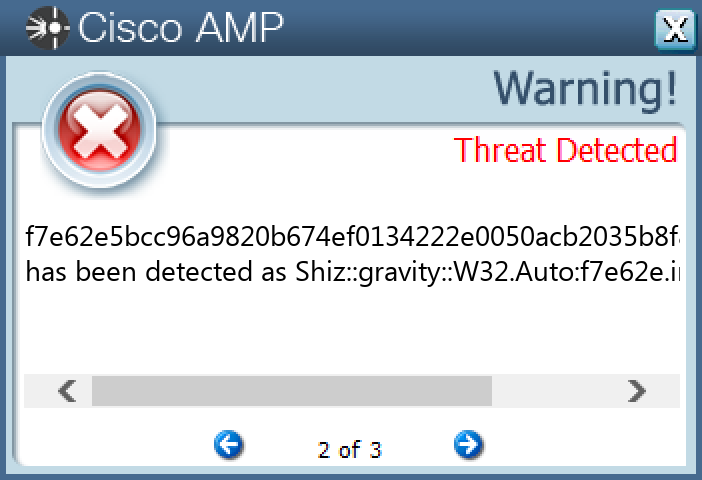
#### Secure Malware Analytics
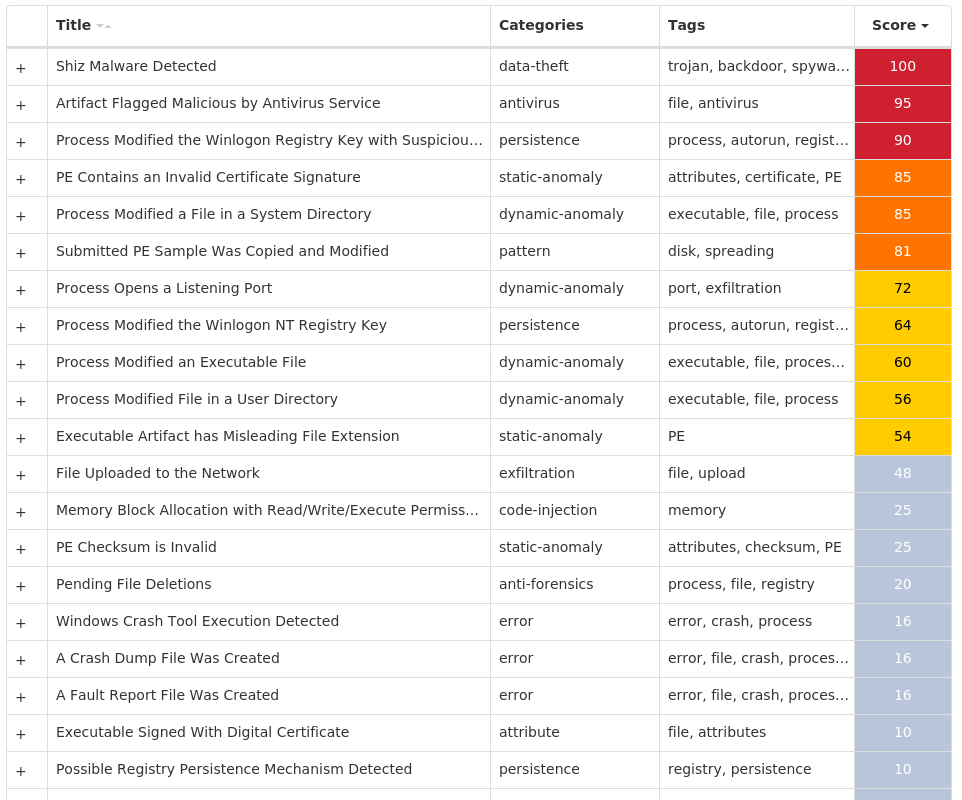
#### MITRE ATT&CK
* * *
### Win.Packed.Zbot-9987774-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 90 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORERSTARTPAGE
Value Name: StartMenu_Balloon_Time`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`77[.]68[.]74[.]189`| 90
`54[.]235[.]219[.]186`| 88
`23[.]221[.]227[.]172`| 40
`23[.]221[.]227[.]165`| 39
`23[.]221[.]227[.]169`| 8
`23[.]3[.]13[.]152`| 2
`23[.]3[.]13[.]129`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`apps[.]identrust[.]com`| 90
`steve[.]dxstorm[.]com`| 90
`benefitanswers[.]co[.]uk`| 90
Files and or directories created| Occurrences
—|—
`%TEMP%pdflauncher.exe`| 90
#### File Hashes
`0134f50d273b3bbfc40f69b037ceeb8c4a0f9c57ef55e14cc564b2647c91d50b`
`0308c618d462657e6fa1ab1566ea439fe7bc8fa175e00c3b3cb92b7de0a15fad`
`0339ade6fc92c17d85d0a3063e1090d1d88f3e7013c63f962ac238ca6a5be0f2`
`03dd7a9a03627752acd6276135953f4e23a567211cda122055fe945ac058547e`
`04049bf401f386b71c3f9370076fa0388ef36317379bd27a3d77521f319ef66c`
`05a90746447511e32622f90440082d5ea344c81f408f2a8180a1a62554f4e563`
`06b5d0d4827be79fc4eb1f518ad2f64cb8011c878172e0f44f9563b7233060be`
`072854dbde422a9f17539752183436f9df9e13cd508e0705adf0a2fedd4b01c6`
`079bb9784c275de6cec815b7fd8fc1ad35ce0cbaabbb5108ebf741fcfd02c008`
`08db7034fce7c18a40454d7d3371739a5a27b324f07a3a84ece5daec32d1b78e`
`094128fb2e38e2feff3360d922c08340c5ab51f4e5941d4b2e5e4e136886da40`
`09cb932db632c40a5da9d5b50bac23d3aaa68a69bfaefdd6f9763d61ede0c343`
`0afe581c70113703a47f4a4a320025d8c42287f3d2b0f50294417e1105d4265b`
`0b66628a42bf861e41ac999ecef8edd7e200cbea9127c0eb6b3c1b94894a9cfe`
`0b66ff19dded846c3ac661dda9a53af6fbc4f87164d160de4077164992152a65`
`0ca014f86962ffa520a1761912131c403e38f512ea37dae6d6ad669c9c5a3e6d`
`0e8761857683220f2f36a62feb8ed9912a555bbcfbca1e38edb201ca1cd91561`
`0f04fc60a33db62f9f2683efeb0f13701cb2847fe33b15391fb1038162481243`
`0fc67b499b0d5c5a42183bcdfb947fe44e3684597844f75e9d88bd9a9b3630d9`
`1014177749ae458c7ac423564a0eda01319c5b68ea6b6c1c177e600a10d822eb`
`101ddaf72d55116c5f72c5d5226f7aa8e7d7814c7cf28503e97a6eaf9e8e22f7`
`106e36ed4efd530cadc507496a32ba2fbb3f40e6e6a860128c38dec4cb56767e`
`11df0c2317b792d8e2c71e51cba375f26fa79c3893dee13bc5b3948b173cc128`
`12d34ae371b5b947943eb4feb650c8e8549e74f3d17a178bbdc9e129ff555f76`
`134cbcb9d9f7d69f3121eeeb8e6fd0b69075ec5755d34b1bb84506507c2fa804`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Win.Malware.Upatre-9987791-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 29 samples
Registry Keys| Occurrences
—|—
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: LanguageList`| 28
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`101[.]53[.]147[.]26`| 28
`23[.]221[.]227[.]165`| 16
`23[.]221[.]227[.]172`| 9
`23[.]221[.]227[.]169`| 2
`23[.]3[.]13[.]152`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`apps[.]identrust[.]com`| 28
`tuhostingprofesional[.]net`| 28
`anuudyog[.]com`| 28
Files and or directories created| Occurrences
—|—
`%TEMP%supdater.exe`| 28
#### File Hashes
`010243c7767a6b837801673fec5f7e2633a0e11c879cfeefb2bd4db175a7816a`
`02ee375ae0dccec565db9e27ba3b24718760cdacd85b8cd74ed6102325114c65`
`05d00dd79e4213b8aa6f2d89e84fd9e183bf900d39d36ab2f013ab67f8291be3`
`060023bf7c5d1145bb08fffbc448274c20dd80c85a80e57f0df823e9f3c79c8a`
`067258b2e61211b48cda093ec5472e6fc9af69126cd9df35d1a07694f5c24ffb`
`089ab142bc7f8da4183552f2171a6c286cd794238cdb24c5ea1518fd45aa3367`
`0c726ff73b0d2611da857e263fad49b26526fec7f94843a1f1f524e0d48dc753`
`0c8737ef332da6de9b470248f936c9aa177d4fd2aba7ffc8c9ed47fda93d7bdd`
`1156286e6dbd4cfb3f9c4aa84d4eef23440bfb8e2f21b07f6f5354590a1c3f72`
`16f0667362c8c5dd9335987ab41c24b92036945c9d1c0ddea04d90948516cb22`
`17641c06747629a7720673f5dd039f5bf7df239ae1f8958ed3dc2f7705226d0c`
`1855312928b2aa88ad5ac89ba51a862d4b2de4eeb33a0ae886e5e1966e780aae`
`1c15b4eaf47ca47b54bd28bc9b153a8ede290944494061ba2bb5b8c85469d4b0`
`1d0578ae82bfd0fa95e9ed545cf5ed279950afd7a9d781b56b2da199644f94c5`
`1e26e6342757fc44a0481be553a7da9cfc7e7bee74f8d047ecdd3db48099cb8e`
`1e854f3b2e5ac899a6b7af69222158dc863dbb6df3e772de4370fb9760d81420`
`212e75aa87694683016e93419f5cbc8780ac745fdc1042bd386eeda4062cc249`
`23c32f21fc7ec2b52e8c7ac55e5d1e3dacdacc436d5ee85f8ab9720f027aaf8d`
`23ebe4536966753f6bbab01b39ffccb11c53be2e165511457945bd27b037aba1`
`24db56ac2049c9a8301b1da437ba4b444ffca88c878aba8edd742ef011768ccd`
`24dca6c92172a2f6c6fd58cfdba88b1a6aa0be1ce57fc0675d5ca0da8df65a53`
`25092b994541d8745e19da88f5a4a0fe4f11aa56eac0f3d8dc61d63c1add3556`
`256e5aaff5776ae40c7e6125768229deb6b17682d6bd92985bc22f7c917e24c6`
`25e9b2184b29eb5da0c534c675bee126c09ddccd01f1c653612b6fb07342d732`
`2784a7512e3c82f8525f358ea544fc613f7d47fc421004e0803dc1dd1e35d2d6`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *Read More
References

Back to Main


