
Itâs [Patch Tuesday]() again. Microsoft is addressing fewer individual vulnerabilities this month than last, but thereâs still plenty to keep admins and defenders occupied.
Three zero-day vulnerabilities are vying for your attention today: a lone Microsoft Publisher vulnerability as well as a couple affecting Windows itself. None is marked as publicly disclosed, but Microsoft has already observed in-the-wild exploitation of all three.
One zero-day vulnerability is a Security Features Bypass vulnerability in Microsoft Publisher. Successful exploitation of [CVE-2023-21715]() allows an attacker to bypass Office macro defenses using a specially-crafted document and run code which would otherwise be blocked by policy. Only Publisher installations delivered as part of Microsoft 365 Apps for Enterprise are listed as affected.
[CVE-2023-23376]() describes a vulnerability in the Windows Common Log File System Driver which allows Local Privilege Escalation (LPE) to SYSTEM. Although Microsoft isnât necessarily aware of mature exploit code at time of publication, this is worth patching at the first opportunity, since it affects essentially all current Windows hosts.
[CVE-2023-21823]() is described as a Remote Code Execution (RCE) vulnerability in Windows Graphics Component, but has Attack Vector listed as Local. This apparent inconsistency is often accompanied with a clarification like: âThe word Remote in the title refers to the location of the attacker. […] The attack itself is carried out locally.â No such clarification is available in this case, but this is likely applicable here also. Microsoft also notes the existence of mature exploit code.
Microsoft is also releasing patches for nine critical RCE vulnerabilities. A more varied selection than last month, February 2023 includes critical RCE in an SQL Server ODBC driver, the iSCSI Discovery Service, .NET/Visual Studio, three in network authentication framework PEAP, one in Word, and two in Visual Studio only. Microsoft has not observed in-the-wild exploitation for any of these vulnerabilities, nor is any of them marked as publicly disclosed. Microsoft predicts that most of these are less likely to be exploited, with the exception of the PEAP vulnerabilities.
Microsoftâs recent announcement about the potential [inclusion of CBL-Mariner CVEs in the Security Update Guide]() is now reflected in the list of covered products, but there arenât any CBL-Mariner vulnerabilities this Patch Tuesday.
SharePoint Server makes another appearance today with [CVE-2023-21717](), which allows an authenticated user with the Manage List permission to achieve RCE. Admins responsible for a SharePoint Server 2013 instance may be interested in the FAQ, which includes what Microsoft optimistically describes as a clarification of the existing servicing model for SharePoint Server 2013.
This is the first Patch Tuesday after the end of Extended Security Updates (ESU) for Windows 8.1. Admins responsible for Windows Server 2008 instances should note that ESU for Windows Server 2008 is now only available for instances hosted in Azure or on-premises instances hosted via Azure Stack. Instances of Windows Server 2008 hosted in a non-Azure context [will no longer receive security updates](), so will forever remain vulnerable to any new vulnerabilities, including the two zero-days covered above.
## Summary charts
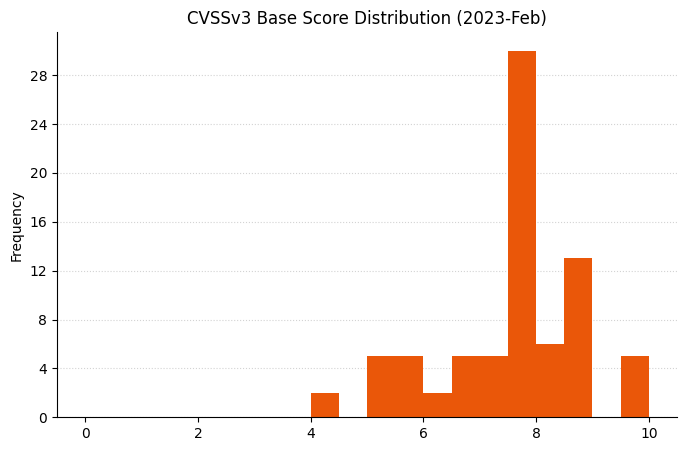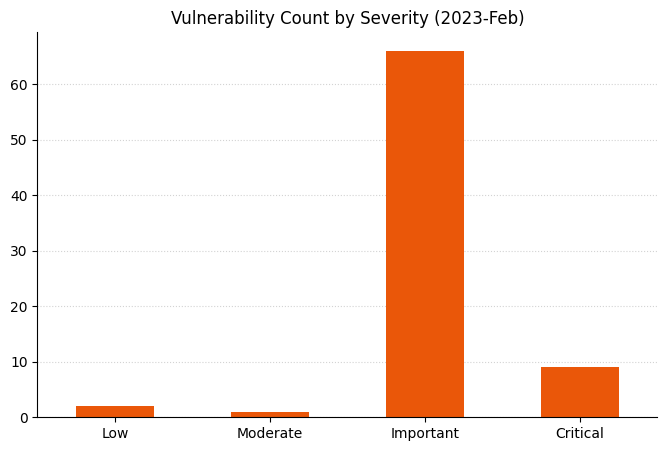
## Summary tables
### Apps vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-23378]() | Print 3D Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-23377]() | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-23390]() | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8
### Azure vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21777]() | Azure App Service on Azure Stack Hub Elevation of Privilege Vulnerability | No | No | 8.7
[CVE-2023-21564]() | Azure DevOps Server Cross-Site Scripting Vulnerability | No | No | 7.1
[CVE-2023-23382]() | Azure Machine Learning Compute Instance Information Disclosure Vulnerability | No | No | 6.5
[CVE-2023-21703]() | Azure Data Box Gateway Remote Code Execution Vulnerability | No | No | 6.5
### Browser vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-23374]() | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | No | No | 8.3
[CVE-2023-21720]() | Microsoft Edge (Chromium-based) Tampering Vulnerability | No | No | 5.3
[CVE-2023-21794]() | Microsoft Edge (Chromium-based) Spoofing Vulnerability | No | No | 4.3
### Developer Tools vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21815]() | Visual Studio Remote Code Execution Vulnerability | No | No | 8.4
[CVE-2023-23381]() | Visual Studio Remote Code Execution Vulnerability | No | No | 8.4
[CVE-2023-21808]() | .NET and Visual Studio Remote Code Execution Vulnerability | No | No | 8.4
[CVE-2023-21566]() | Visual Studio Elevation of Privilege Vulnerability | No | No | 7.8
[CVE-2023-21553]() | Azure DevOps Server Remote Code Execution Vulnerability | No | No | 7.5
[CVE-2023-21567]() | Visual Studio Denial of Service Vulnerability | No | No | 5.6
[CVE-2023-21722]() | .NET Framework Denial of Service Vulnerability | No | No | 4.4
### Device vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2019-15126]() | MITRE: CVE-2019-15126 Specifically timed and handcrafted traffic can cause internal errors (related to state transitions) in a WLAN device | No | No | N/A
### ESU vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21800]() | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8
### ESU Microsoft Office Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21823]() | Windows Graphics Component Remote Code Execution Vulnerability | Yes | No | 7.8
### ESU Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21803]() | Windows iSCSI Discovery Service Remote Code Execution Vulnerability | No | No | 9.8
[CVE-2023-21689]() | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | No | No | 9.8
[CVE-2023-21690]() | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | No | No | 9.8
[CVE-2023-21692]() | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | No | No | 9.8
[CVE-2023-21799]() | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21685]() | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21686]() | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21684]() | Microsoft PostScript Printer Driver Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21797]() | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21798]() | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21802]() | Windows Media Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-21805]() | Windows MSHTML Platform Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-21817]() | Windows Kerberos Elevation of Privilege Vulnerability | No | No | 7.8
[CVE-2023-21822]() | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7.8
[CVE-2023-21812]() | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8
[CVE-2023-23376]() | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Yes | No | 7.8
[CVE-2023-21688]() | NT OS Kernel Elevation of Privilege Vulnerability | No | No | 7.8
[CVE-2023-21801]() | Microsoft PostScript Printer Driver Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-21811]() | Windows iSCSI Service Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21702]() | Windows iSCSI Service Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21700]() | Windows iSCSI Discovery Service Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21813]() | Windows Secure Channel Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21818]() | Windows Secure Channel Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21816]() | Windows Active Directory Domain Services API Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21695]() | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | No | No | 7.5
[CVE-2023-21691]() | Microsoft Protected Extensible Authentication Protocol (PEAP) Information Disclosure Vulnerability | No | No | 7.5
[CVE-2023-21701]() | Microsoft Protected Extensible Authentication Protocol (PEAP) Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21820]() | Windows Distributed File System (DFS) Remote Code Execution Vulnerability | No | No | 7.4
[CVE-2023-21694]() | Windows Fax Service Remote Code Execution Vulnerability | No | No | 6.8
[CVE-2023-21697]() | Windows Internet Storage Name Service (iSNS) Server Information Disclosure Vulnerability | No | No | 6.2
[CVE-2023-21693]() | Microsoft PostScript Printer Driver Information Disclosure Vulnerability | No | No | 5.7
[CVE-2023-21699]() | Windows Internet Storage Name Service (iSNS) Server Information Disclosure Vulnerability | No | No | 5.3
### Exchange Server vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21706]() | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21707]() | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21529]() | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21710]() | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 7.2
### Microsoft Dynamics vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21778]() | Microsoft Dynamics Unified Service Desk Remote Code Execution Vulnerability | No | No | 8.3
[CVE-2023-21572]() | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 6.5
[CVE-2023-21807]() | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.8
[CVE-2023-21570]() | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4
[CVE-2023-21571]() | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4
[CVE-2023-21573]() | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4
### Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21716]() | Microsoft Word Remote Code Execution Vulnerability | No | No | 9.8
[CVE-2023-21717]() | Microsoft SharePoint Server Elevation of Privilege Vulnerability | No | No | 8.8
[CVE-2023-21715]() | Microsoft Publisher Security Features Bypass Vulnerability | Yes | No | 7.3
[CVE-2023-21721]() | Microsoft OneNote Spoofing Vulnerability | No | No | 6.5
[CVE-2023-21714]() | Microsoft Office Information Disclosure Vulnerability | No | No | 5.5
### SQL Server vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21705]() | Microsoft SQL Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21713]() | Microsoft SQL Server Remote Code Execution Vulnerability | No | No | 8.8
[CVE-2023-21806]() | Power BI Report Server Spoofing Vulnerability | No | No | 8.2
[CVE-2023-21528]() | Microsoft SQL Server Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-21718]() | Microsoft SQL ODBC Driver Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-21704]() | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 7.8
[CVE-2023-21568]() | Microsoft SQL Server Integration Service (VS extension) Remote Code Execution Vulnerability | No | No | 7.3
### System Center vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21809]() | Microsoft Defender for Endpoint Security Feature Bypass Vulnerability | No | No | 7.8
[CVE-2023-23379]() | Microsoft Defender for IoT Elevation of Privilege Vulnerability | No | No | 6.4
### Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score
—|—|—|—|—
[CVE-2023-21804]() | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7.8
[CVE-2023-21819]() | Windows Secure Channel Denial of Service Vulnerability | No | No | 7.5
[CVE-2023-21687]() | HTTP.sys Information Disclosure Vulnerability | No | No | 5.5Read More
References

Back to Main


