[]()
Threat actors are capitalizing on a popular TikTok challenge to trick users into downloading information-stealing malware, according to new research from Checkmarx.
The trend, called [Invisible Challenge](), involves applying a filter called [Invisible Body]() that just leaves behind a silhouette of the person’s body.
But the fact that individuals filming such videos could be undressed has led to a nefarious scheme wherein the attackers post TikTok videos with links to rogue software dubbed “unfilter” that purport to remove the applied filters.
“Instructions to get the ‘unfilter’ software deploy [WASP stealer malware]() hiding inside malicious Python packages,” Checkmarx researcher Guy Nachshon [said]() in a Monday analysis.
The WASP stealer (aka W4SP Stealer) is a malware that’s designed to steal users’ passwords, Discord accounts, cryptocurrency wallets, and other sensitive information.
The TikTok videos posted by the attackers, @learncyber and @kodibtc, on November 11, 2022, are estimated to have reached over a million views. The accounts have been suspended.
[]()
[]()
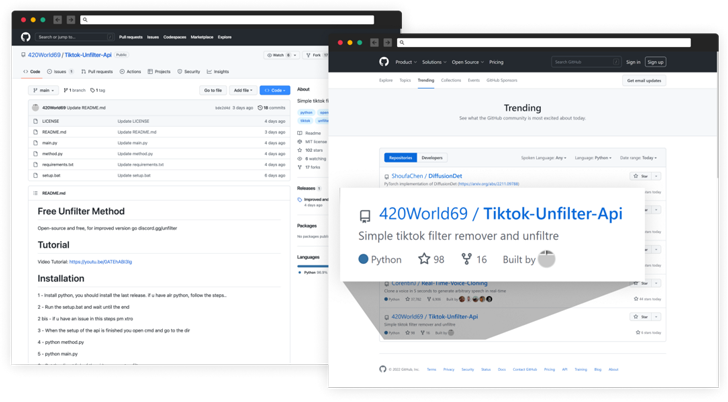
Also included in the video is an invite link to a Discord server managed by the adversary, which had nearly 32,000 members before it was reported and deleted. Victims joining the Discord server subsequently receive a link to a GitHub repository that hosts the malware.
The attacker has since renamed the project to “Nitro-generator” but not before it landed on GitHub’s [Trending repositories list]() for November 27, 2022, by urging the new members on Discord to [star the project]().
Besides changing the repository name, the threat actor deleted old files in the project and uploaded fresh ones, one of which even [describes]() the Python code as “Its (sic) open source, its not a **VIRUS**.”
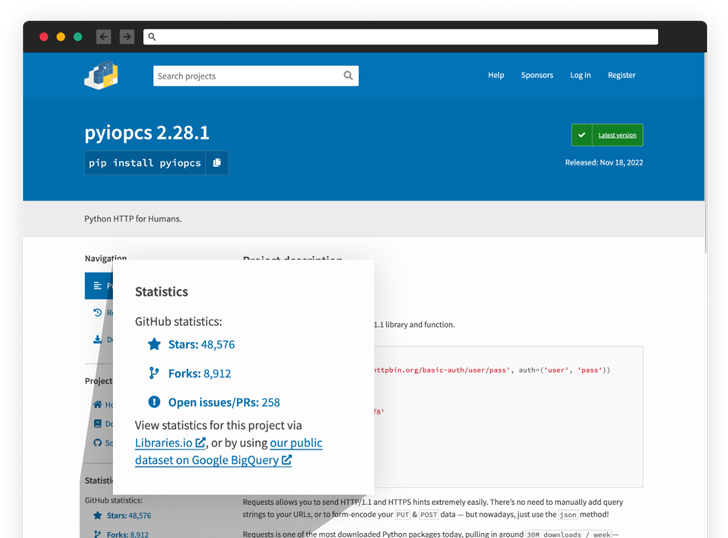
The stealer code is said to have been embedded in various Python packages such as “tiktok-filter-api,” “pyshftuler,” “pyiopcs,” and “pydesings,” with the operators swiftly publishing new replacements to the Python Package Index (PyPI) under different names upon getting removed.
“The level of manipulation used by software supply chain attackers is increasing as attackers become increasingly clever,” Nachshon noted. “These attacks demonstrate again that cyber attackers have started to focus their attention on the open source package ecosystem.”
Found this article interesting? Follow THN on [Facebook](), [Twitter _ï_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


