[]()
Malicious actors are resorting to voice phishing (vishing) tactics to dupe victims into installing Android malware on their devices, new [research]() from ThreatFabric reveals.
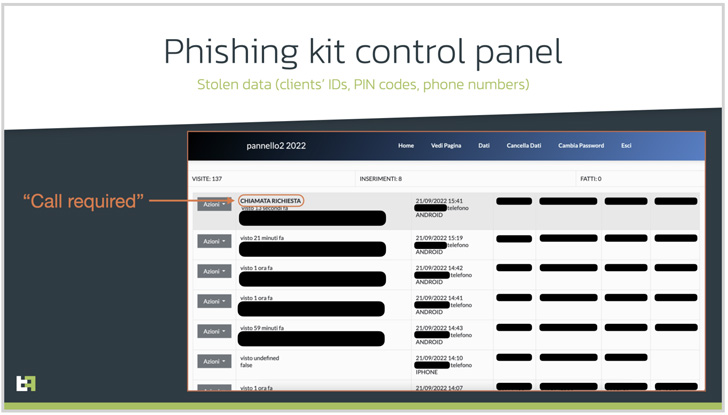
The Dutch mobile security company said it identified a network of phishing websites targeting Italian online-banking users that are designed to get hold of their contact details.
Telephone-oriented attack delivery (TOAD), as the social engineering technique is called, involves calling the victims using previously collected information from fraudulent websites.
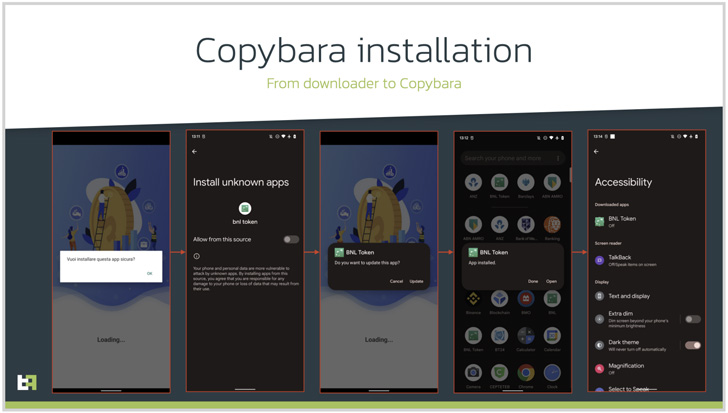
The caller, who purports to be a support agent for the bank, instructs the individual, on the other hand, to install a security app and grant it extensive permissions, when, in reality, it’s malicious software intended to gain remote access or conduct financial fraud.
In this case, it leads to the deployment of an Android malware dubbed [Copybara](), a mobile trojan first detected in November 2021 and is primarily used to perform on-device fraud via overlay attacks targeting Italian users. Copybara has also been confused with another malware family known as [BRATA]().
[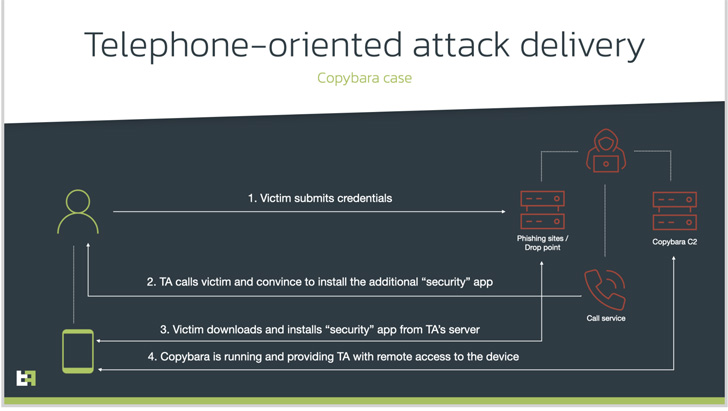]()
ThreatFabric assessed the TOAD-based campaigns to have commenced around the same time, indicating that the activity has been ongoing for nearly a year.
Like any other Android-based malware, Copybara’s RAT capabilities are powered by abusing the operating system’s accessibility services API to gather sensitive information and even uninstall the downloader app to reduce its forensic footprint.
[]()
What’s more, the infrastructure utilized by the threat actor has been found to deliver a second malware named SMS Spy that enables the adversary to gain access to all incoming SMS messages and intercept one-time passwords (OTPs) sent by banks.
The new wave of hybrid fraud attacks presents a new dimension for scammers to mount convincing Android malware campaigns that have otherwise relied on traditional methods such as Google Play Store droppers, rogue ads, and smishing.
“Such attacks require more resources on [threat actors’] side and are more sophisticated to perform and maintain,” ThreatFabric’s Mobile Threat Intelligence (MTI) team told The Hacker News.
[]()
“We also like to point out that targeted attacks from a fraud success perspective are unfortunately more successful, at least in this specific campaign.”
This is not the first time TOAD tactics are being employed to orchestrate banking malware campaigns. Last month, the MalwareHunterTeam [detailed]() a similar attack aimed at users of the Indian bank Axis Bank in a bid to install an info-stealer that impersonates a credit card rewards app.
“Any suspicious call should be double checked by calling your financial organization,” the MTI team said, adding “financial organizations should provide their customers with knowledge about ongoing campaigns and enhance the client apps with mechanisms to detect suspicious activity.”
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


