On September 16, GitHub Security learned that threat actors were targeting GitHub users with a phishing campaign by impersonating CircleCI to harvest user credentials and two-factor codes. While GitHub itself was not affected, the campaign has impacted many victim organizations. Today, we are sharing details of what weve learned to help raise awareness of this phishing campaign and protect potential future victims.
Reported versions include messages like these, which imply that a users CircleCI session expired and that they should log in using GitHub credentials.
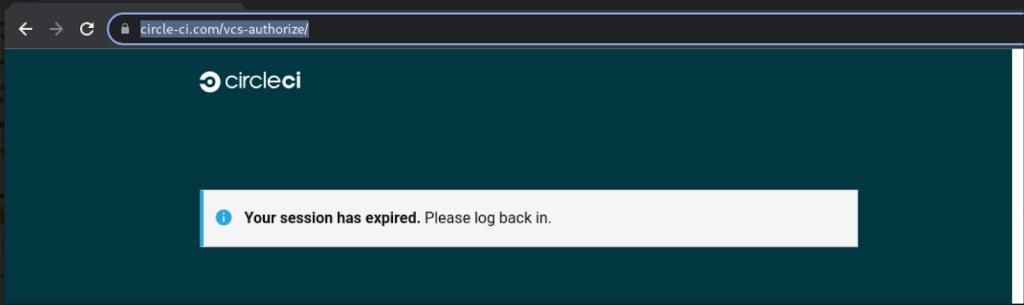
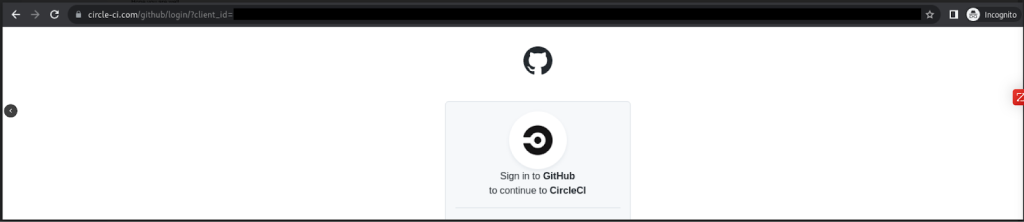
Clicking the link takes the user to a phishing site that looks like the GitHub login page but steals any credentials entered. For users with [TOTP-based two-factor authentication]() (2FA) enabled, the phishing site also relays any TOTP codes to the threat actor and GitHub in real time, allowing the threat actor to break into accounts protected by TOTP-based 2FA. Accounts protected by [hardware security keys]() are not vulnerable to this attack.
The threat actor uses the following tactics:
* If the threat actor successfully steals GitHub user account credentials, they may quickly create GitHub personal access tokens (PATs), authorize OAuth applications, or add SSH keys to the account in order to preserve access in the event that the user changes their password.
* In many cases, the threat actor immediately downloads private repository contents accessible to the compromised user, including those owned by organization accounts and other collaborators.
* The threat actor uses VPN or proxy providers to download private repository data via compromised user accounts.
* If a compromised account has organization management permissions, the threat actor may create new GitHub user accounts and add them to an organization in an effort to establish persistence.
Known phishing domains as of September 21, 2022:
* circle-ci[.]com
* emails-circleci[.]com
* circle-cl[.]com
* email-circleci[.]com
We are sharing this today as we believe the attacks may be ongoing and action is required for customers to protect themselves.
## How GitHub responded to protect users of GitHub.com[]()
Upon conducting our analysis, we reset passwords and removed threat actor-added credentials for impacted users, and we notified all of the known-affected users and organizations that we discovered through our analysis. If you did not receive an email notice from us, then we do not have evidence that your account and/or organization was accessed by the threat actor at this time. We suspended all identified threat actor accounts, and we will continue to monitor for malicious activity and notify new victim users and organizations as needed.
We will continue to respond to new phishing domains as we discover them. See below for more steps you can take to protect yourself from phishing.
## What GitHub customers and organizations need to know[]()
If you believe you may have entered credentials on a phishing site:
* [Reset your password]()
* [Reset your two-factor recovery codes]()
* [Review your personal access tokens]() for unexpected or unused tokens
* [Take additional steps]() to review and secure your account.
In order to prevent phishing attacks (which collect two-factor codes) from succeeding, consider using [hardware security keys]() or [WebAuthn 2FA](). Also, consider using a browser-integrated password manager to autofill passwords for familiar websites. Many commercial and open source options exist, including browser-based password management native to popular web browsers. If your password manager doesnt recognize the website youre visiting, it might be a phishing site.
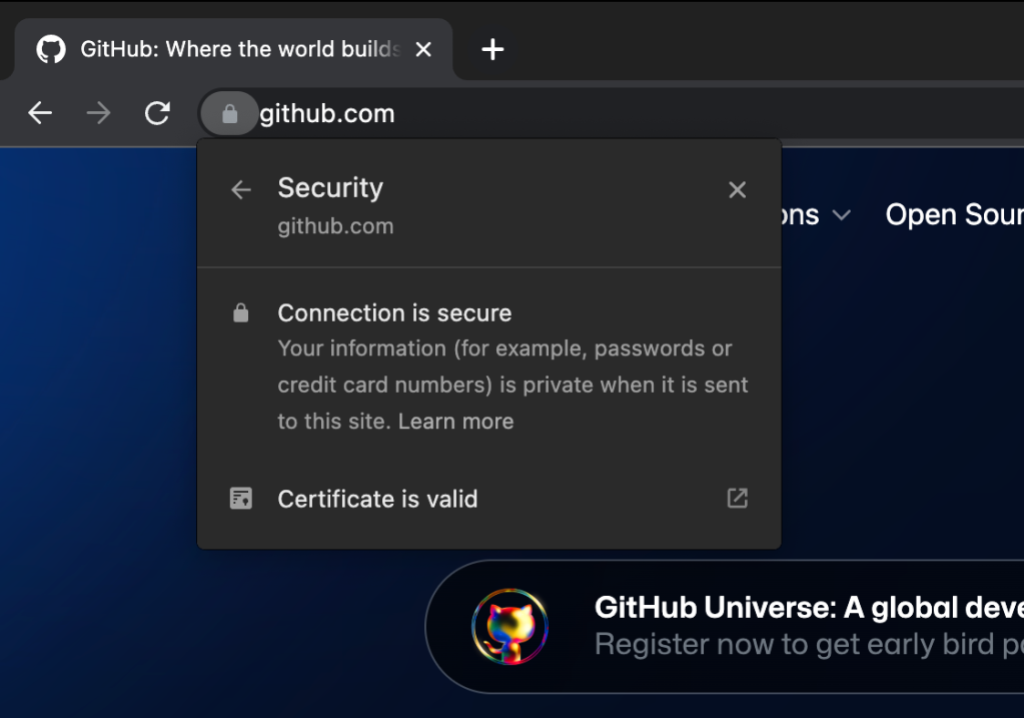
To verify that youre not entering credentials in a phishing site, confirm that the URL in the address bar is https://github.com/login and that the sites TLS certificate is issued to GitHub, Inc.
## If you have questions or concerns[]()
If youve received phishing emails related to this phishing campaign, please [contact GitHub Support]() with details about the sender email address and URL of the malicious site to help us respond to this issue.
The security and trustworthiness of GitHub and the broader developer ecosystem is our highest priority. Our investigation is ongoing, and we will continue to remediate and notify affected users as needed.Read More
References

Back to Main


