[]()
Malicious actors such as Kinsing are taking advantage of both recently disclosed and older security flaws in Oracle WebLogic Server to deliver cryptocurrency-mining malware.
Cybersecurity company Trend Micro said it [found]() the financially-motivated group leveraging the vulnerability to drop Python scripts with capabilities to disable operating system (OS) security features such as Security-Enhanced Linux ([SELinux]()), and others.
The operators behind the [Kinsing malware]() have a history of scanning for vulnerable servers to co-opt them into a botnet, including that of [Redis](), [SaltStack](), [Log4Shell](), [Spring4Shell](), and the Atlassian Confluence flaw ([CVE-2022-26134]()).
The Kinsing actors have also been involved in campaigns against container environments via [misconfigured open Docker Daemon API ports]() to launch a crypto miner and subsequently spread the malware to other containers and hosts.
The latest wave of attacks entails the actor weaponizing [CVE-2020-14882]() (CVSS score: 9.8), a two-year-old remote code execution (RCE) bug, against unpatched servers to seize control of the server and drop malicious payloads.
It’s worth noting that the vulnerability has been [exploited in the past]() by multiple botnets to distribute Monero miners and the Tsunami backdoor on infected Linux systems.
[]()
Successful exploitation of the flaw was succeeded by the deployment of a shell script that’s responsible for a series of actions: Removing the [/var/log/syslog]() system log, turning off security features and cloud service agents from Alibaba and Tencent, and killing competing miner processes.
The shell script then proceeds to download the Kinsing malware from a remote server, while also taking steps to ensure persistence by means of cron job.
“The successful exploitation of this vulnerability can lead to RCE, which can allow attackers to perform a plethora of malicious activities on affected systems,” Trend Micro said. “This can range from malware execution […] to theft of critical data, and even complete control of a compromised machine.”
## **TeamTNT actors make a comeback with the Kangaroo Attack**
The development comes as researchers from Aqua Security identified three new attacks linked to another “vibrant” cryptojacking group called TeamTNT, which voluntarily shut shop in November 2021.
“TeamTNT has been scanning for a misconfigured Docker Daemon and deploying alpine, a vanilla container image, with a command line to download a shell script (k.sh) to a C2 server,” Aqua Security researcher Assaf Morag [said]().
What’s notable about the attack chain is that it appears to be designed to break [SECP256K1 encryption](), which, if successful, could give the actor the ability to calculate the keys to any cryptocurrency wallet. Put differently, the idea is to leverage the high but illegal computational power of its targets to run the ECDLP solver and get the key.
Two other attacks mounted by the group entail the exploitation of [exposed Redis servers]() and misconfigured Docker APIs to deploy coin miners and Tsunami binaries.
TeamTNT’s targeting of Docker REST APIs has been [well-documented]() over the past year. But in an [operational security blunder]() spotted by Trend Micro, credentials associated with two of the attacker-controlled DockerHub accounts have been uncovered.
[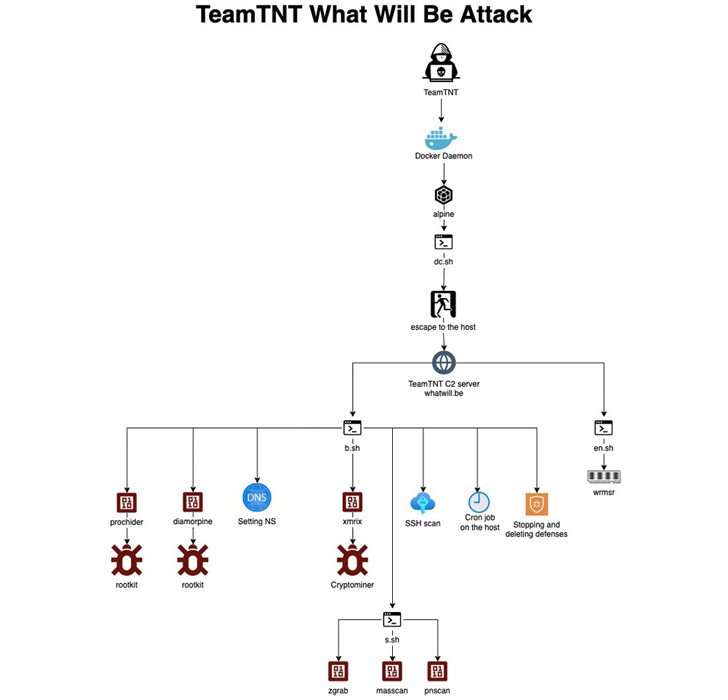]()
The accounts alpineos and sandeep078 are said to have been used to distribute a variety of malicious payloads like rootkits, Kubernetes exploit kits, credential stealers, XMRig Monero miners, and even the Kinsing malware.
“The account alpineos was used in exploitation attempts on our honeypots three times, from mid-September to early October 2021, and we tracked the deployments’ IP addresses to their location in Germany,” Trend Micro’s Nitesh Surana [said]().
“The threat actors were logged in to their accounts on the DockerHub registry and probably forgot to log out.” Alternatively, “the threat actors logged in to their DockerHub account using the credentials of alpineos.”
Trend Micro said the malicious alpineos image had been downloaded more than 150,000 times, adding it notified Docker about these accounts.
It’s also recommending organizations to configure the exposed REST API with TLS to mitigate adversary-in-the-middle (AiTM) attacks, as well as use credential stores and [helpers]() to host user credentials.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


