[]()
It’s not a new concept that Office 365, Salesforce, Slack, Google Workspace or Zoom, etc., are amazing for enabling the hybrid workforce and hyper-productivity in businesses today. However, there are three main challenges that have arisen stemming from this evolution: (1) While SaaS apps include a host of native security settings, they need to be hardened by the security team of the organization. (2) Employees are granting 3rd party app access to core SaaS apps that pose potential threats to the company. (3) These SaaS apps are accessed by different devices without their device hygiene score even being checked.
#### **1 Misconfiguration Management**
It’s not an easy task to have every app setting properly configured at all times. The challenge lies within how burdensome this responsibility is each app has tens or hundreds of security settings to configure, in addition to thousands of user roles and permission in a typical enterprise, compounded by the many compliance industry standards and frameworks that organizations strive to follow.
The complexity of securing SaaS apps is only increased by the fact that often the SaaS app owner sits _outside_ the security team, in the department that most uses the app (think Sales has CRM app, Marketing has automation app) and they are untrained and not focused on the security upkeep of the app. It all amounts to just how burdensome and unrealistic it is to expect security teams to be able to stay in control of the organization’s SaaS stack.
#### **2 3rd Party App Access**
OAuth 2.0 has greatly simplified authentication and authorization and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user’s authorization for specific permissions. An app can request one or more scopes. Through the approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
When it comes to local machines and executable files, organizations already have control built-in that enables security teams to block problematic programs and files. It needs to be the same when it comes to SaaS apps.
#### **3 Device-to-SaaS-User Posture **
From the first entry through to the device posture, security teams need to be able to identify and manage the risks coming from SaaS users and their associated devices. A device with a low hygiene score poses a high risk depending on which apps this employee is using. In the case of a highly privileged user, an unsecured device can pose an even higher level of risk for an organization. The security team needs the ability to correlate SaaS app users, their roles, and permissions with their associated devices’ compliance and integrity levels. This end-to-end approach enables a holistic zero-trust approach to SaaS security that is only now coming into the picture.
#### **SaaS Security Posture Management Handles the SaaS Stack Challenges **
That’s why Gartner named SaaS Security Posture Management (SSPM) a MUST HAVE solution to continuously assess security risks and manage the SaaS applications’ security posture in the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021.” Other cloud solutions don’t offer preventative coverage. For example, a CASB solution is event-driven; CASB will alert the organization to a SaaS leak or breach only once it has occurred.
An SSPM solution, like [Adaptive Shield](), comes into play to enable security teams to identify, analyze, and prioritize misconfigurations as well as provide visibility to 3rd party apps with access to their core apps and Device-to-SaaS-User posture management.
[Click here to schedule a 15-minute demo of Adaptive Shield’s SSPM solution]().
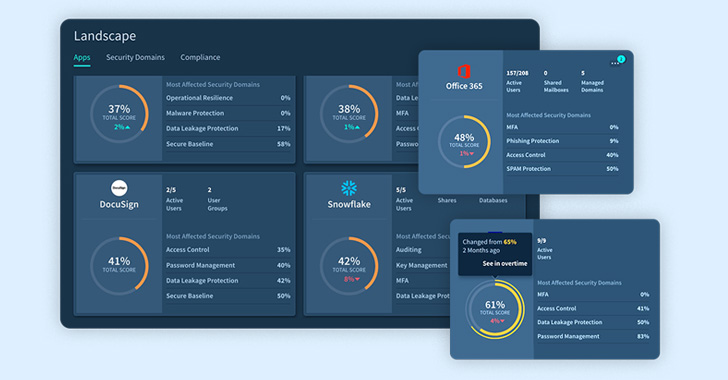
Adaptive Shield lets you filter and slice the data by app, domain, and compliance frameworks.
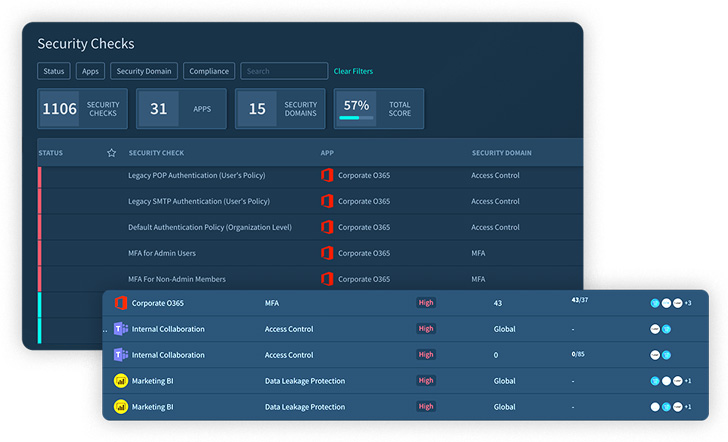
The core of the solution is the detailed and granular security checks being continuously performed across the SaaS stack, while security teams can address misconfigurations immediately or create a ticket that integrates with any ticketing system:
[]()
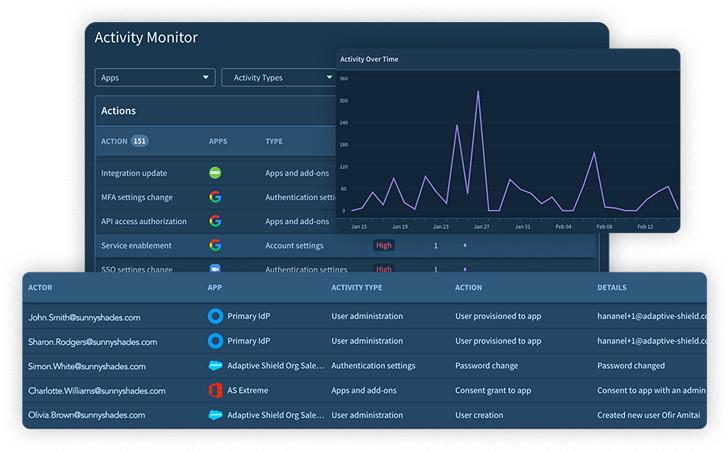
Through the Activity Monitoring feature, Adaptive Shield monitors the activities of privileged users:
[]()
[Click here to schedule a 15-minute demo ]()to see all features and functionalities.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


