
Locating sensitive information, personally identifiable information (PII) and questionable assets in the cloud.
### TL; DR
I had a curiosity driven excursion into the public clouds of AWS and Azure to find what is publicly hosted and who by. As anticipated, the results were extremely broad and interesting as I found PII, various web applications, login portals, source code, and adult material.
Please note that this blog will not include all steps of reconnaissance as that is a topic for another blog.
### Phase One Passive OSINT
### Shodan OSINT
There are two ways you can approach Shodan OSINT, the web application or the CLI tool, and both have their own advantages and quirks. Using the web application allows you to export the results to a .gzip file whereas the CLI tool can be used with a good ol fashioned copy and paste or using **shodan download**.
**cloud.service:”azureCloud” country:GB,US http.title:”swagger” http.status:200**
^- Searching for API documentation.
**cloud.service:”azureCloud” http.status:200 country:GB,US -http.title:”Your Azure Function App is up and running.” -http.title”IIS Windows Server**
^- Searching for web services that are not default splash pages.
**cloud.provider:”Azure” country:GB,US http.status:200 http.title:”Index of /” ssl:true**
^- Searching for web apps with directory listings enabled and SSL. You can remove ssl:true.
**cloud.provider:”Azure” hostname:”cloudapp.net” http.status:200,302**
^- Searching for cloud apps.
**cloud.service:”AzureCloud” http.status:200 http.title:”api”**
^- Searching for APIs.
**cloud.provider:”Amazon” http.status:200,302 http.title:”Index of /”**
^- Searching for web apps with directory listings enabled on AWS.
It should be noted that the http.title:Index of / search does not work on the CLI version. The CLI version of these search terms are the exact same other than the precursory **shodan search** command.
Once decompressing the gzip files, I used various Linux manipulation tools to parse the data, which will be covered later in this post.
### Worthy Mentions
Before we proceed, I would like to quickly highlight some other cloud tools and services that are useful. Please note that other cloud tools and services can be used to gain similar information.
**GrayhatWarfare**
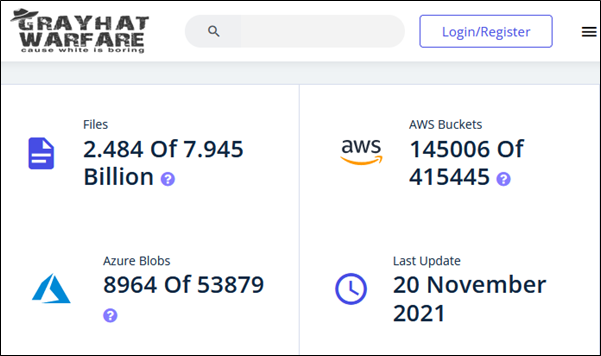
##### **Figure 1 – Homepage**
[GrayhatWarfare]() is a service that scans the internet and stores URLs of publicly accessible AWS Buckets and Azure Blobs. You can use this service to search for specific filetypes and keywords, so you could limit the results to a potential target. My standout moment was when I found an S3 bucket used by a company that sells personalised gifts someone had uploaded this photo to be used in a personalised gift.

##### **Figure 2 – Anniversary gift?**
**Azure AD Internals (AAD Internals)**
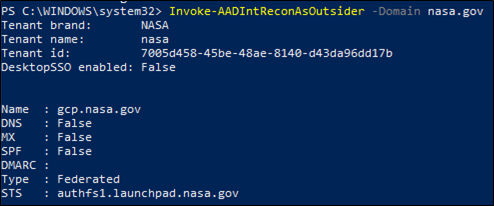
##### **Figure 3 – Recon**
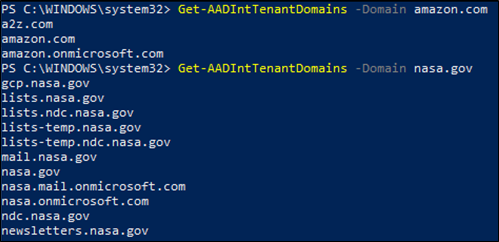
##### **Figure 4 – Amazon and Nasa Azure domains**
[AAD Internals]() is a well-known PowerShell module for administering and exploiting Azure AD and Office 365. At time of writing this blog, there are 176 functions that range from legitimate administration CRUD functions (create, read, update, delete) to hack functions that include recon, extracting data, kill chain functions and more.
You can see in Figure 3 and 4 that I have discovered various Tenant domains for NASA and Amazon, additionally, Figure 3 shows the Tenant ID for NASA and some other DNS information.
You can also use it to enumerate valid user accounts as shown below.
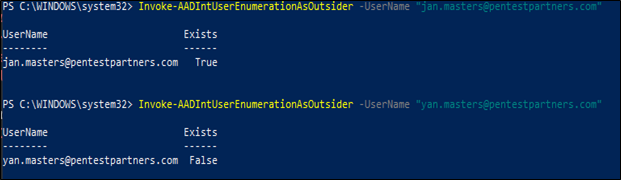
##### **Figure 5 – User enumeration**
**AzureSpeed**
##### **Figure 6 IP Lookup**
##### **Figure 7 – Features**
[AzureSpeed.com]() is an open-source project that is focused on testing speed, latency and various other things; however, I mainly use it to confirm that an IP is an Azure IP and its associated services and features. You can use this to get a list of IPs to run through OSINT services to find alive hosts, which you could then use to mass-collect certificates to parse for domains.
**Google Dorks**
I can comfortably say that all usable cloud services, such as virtual machines, require unique subdomain names for the vendors service. You can use this to your advantage to either perform DNS lookups or use Google dorks such as site: blob.core.windows.net
You can find a list of these domains and subdomains [here]().
Some notable AWS domains and subdomains are:
* AWS Apps: awsapps.com
* S3: s3.amazonaws.com
* EC2: compute.amazonaws.com
* Elastic/Application Load Balancer: elb.amazonaws.com
* AWS API Gateway: execute-api.region.amazonaws.com (inurl:execute-api site:amazonaws.com)
* OpenSearch(Elasticsearch): es.amazonaws.com
##### **Figure 8 – Google results for amazonaws.com**
##### **Figure 9 – Google results for blob.core.windows.net**
### Phase Two Active Enumeration
### Confirming Shodan OSINT
The first step is to parse my Shodan downloads to convert them into easy-to-use target files to feed into various tools. Please note that other jq strings and Linux text manipulation tools exist. Also, Nano is the best.
1. Parse Shodan JSON files
jq -r ‘[.http.host, .port, .http.title] | @csv’ path/to/file.js > output-file.txt
Results:
“x.x.x.x”,80,”Index of /”
2. Extract IPs
cat output-file.txt | cut -d “,” -f 1 | sort -u
Results:
x.x.x.x
x.x.x.x
3. Extract ports
cat output-file.txt | cut -d “,” -f 2 | sort -u | sed -z ‘s/n/,/g;s/,$/n/
**Results:**
x,x,x,x,x
As previously mentioned, you can feed these IPs into various tools and in my case, passive OSINT services and tools to find domain names, certificate details, cached sites, and such. This yielded a lot of results, here are some of the best examples.
### Interesting Findings
This section will mainly contain screenshots of some resources that were of interest. A lot of these resources should not be publicly accessible as they either present an opportunity to an attacker or breach regulations such as GDPR, which could result in large fines.
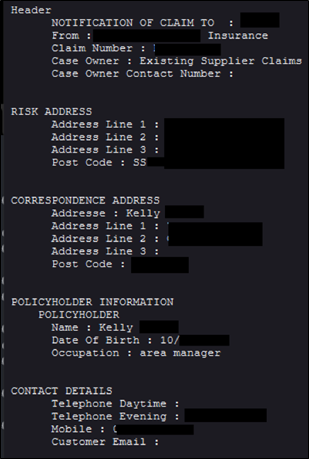
##### **Figure 10 – #1 Directory Listing Insurance Specialist – Insurance claim**
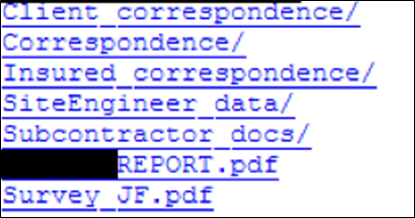
##### **Figure 11 – Snippet**
This company was hosting a publicly accessible web server with web directory listing enabled, which included various sensitive documents such as insurance claims, company data, software, and emails. We disclosed this issue to the IT department and the issue was swiftly resolved. A spokesperson stated they have conducted a full investigation and are implementing additional controls to prevent any repeats.
##### **Figure 12 – #2 Directory Listing Currency Exchange & Transfers**
This company was also hosting a web app with directory listing and zero access controls, which exposed **EXTREMELY** sensitive data. It should be noted that this issue was resolved very shortly after identification, without any input from PTP. It seems like this was a new installation that was temporarily exposed.
##### **Figure 13 – #3 Directory Listing Unknown**
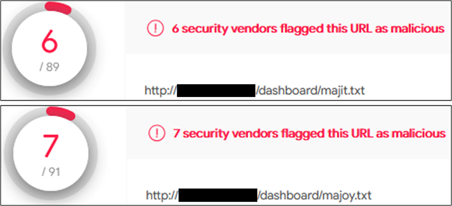
##### **Figure 14 – Publicly accessible malware**
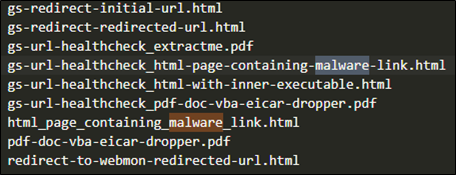
##### **Figure 15 – Virtual machine hosting malware**
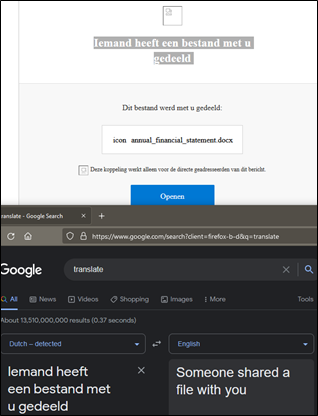
##### **Figure 16 – Office365 based phishing landing page**
There was also one that used an EC2 instance to host a publicly accessible Apache server that held his porn collection The other file names were extremely questionable, so I have decided to only include this one.
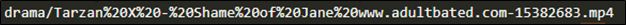
##### **Figure 17 – Adult movie collection**
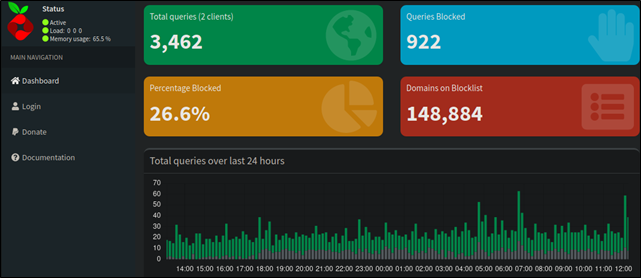
##### **Figure 18 – Cloud hosted Pi-hole**
The publicly accessible Pi-hole could be maliciously configured to create a machine-in-the-middle scenario if credentials are identified via brute force, phishing attacks or previously compromised credentials.
### Conclusion
Cloud assets (in many cases) are not secure by default and can be made publicly accessible very easily, which can lead to your assets being discovered and scraped by various online services. Unfortunately, the remediation advice is not simple as this issue spans various services across different vendors, which use the same technology but different terminology.
A good place to start would be to place these services behind firewalls/network security groups/network ACLs and to secure permissions on data services such as S3 buckets.
The post [Security Blog]() first appeared on [Pen Test Partners]().Read More
References

Back to Main


