[]()
Amazon, in December 2021, patched a high severity vulnerability affecting its [Photos app]() for Android that could have been exploited to steal a user’s access tokens.
“The Amazon access token is used to authenticate the user across multiple Amazon APIs, some of which contain personal data such as full name, email, and address,” Checkmarx researchers João Morais and Pedro Umbelino [said](). “Others, like the Amazon Drive API, allow an attacker full access to the user’s files.”
The Israeli application security testing company reported the issue to Amazon on November 7, 2021, following which the tech giant rolled out a fix on December 18, 2021.
The leak is the result of a misconfiguration in one of the app’s components named “com.amazon.gallery.thor.app.activity.ThorViewActivity” that’s defined in the [AndroidManifest.xml file]() and which, when launched, initiates an HTTP request with a header containing the access token.
[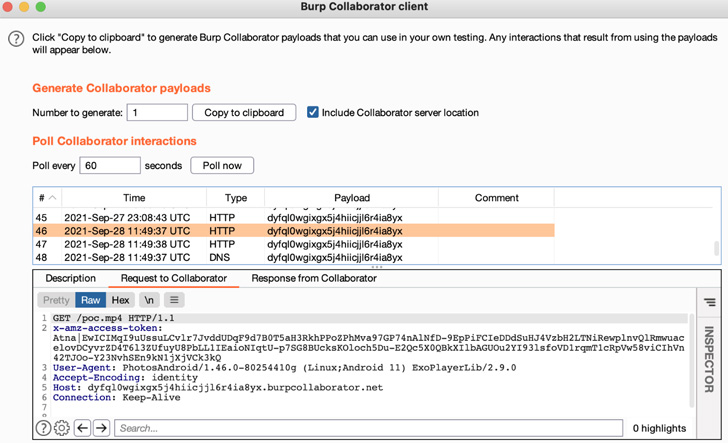]()
In a nutshell, it means that an external app could send an [intent]() a message to facilitate communication between apps to launch the vulnerable activity in question and redirect the HTTP request to an attacker-controlled server and extract the access token.
Calling the bug a case of broken authentication, the cybersecurity company said the issue could have enabled malicious apps installed on the device to grab the access tokens, granting the attacker permissions to make use of the APIs for follow-on activities.
This could vary from deleting files and folders in Amazon Drive to even exploiting the access to stage a ransomware attack by reading, encrypting, and re-writing a victim’s files while erasing their history.
Checkmarx further noted that the vulnerability might have had a broader impact given that the APIs exploited as part of its proof-of-concept (PoC) constitute only a small subset of the entire Amazon ecosystem.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


