## **Microsoft Patch Tuesday Summary**
Microsoft has fixed 55 vulnerabilities (aka flaws) in the June 2022 update, including three (3) vulnerabilities classified as **_Critical_** as they allow Remote Code Execution (RCE). This month’s Patch Tuesday cumulative Windows update includes the fix for one (1) zero-day vulnerability ([CVE-2022-30190]()). Microsoft also released an advisory for Intel Processor MMIO Stale Data Vulnerabilitie to address four (4) Intel vulnerabilities ([Microsoft Advisory 220002](), [Intel-SA-00615]()).
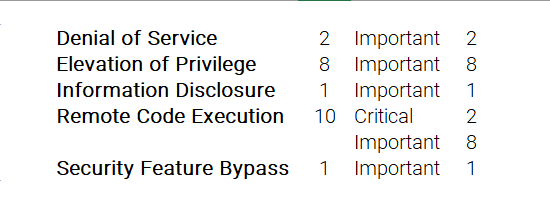
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege, Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing vulnerabilities.
The June 2022 Microsoft vulnerabilities are classified as follows:

* * *
# Notable Microsoft Vulnerabilities Patched
This months [advisory]() covers multiple Microsoft product families, including Azure, Developer Tools, Edge-Chromium Browser, Microsoft Office, SQL Server, System Center, and Windows.
A total of 25 unique Microsoft products/versions are affected.
Downloads include Azure Hotpatch, Cumulative Updates, Monthly Rollup, Security Only, and Security Updates.
* * *
## [CVE-2022-30190]() | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
Microsoft has fixed the widely-exploited _**Windows Follina MSDT zero-day**_ vulnerability tracked as[ CVE-2022-30190]() in the June 2022 Updates.
The update for this vulnerability is in the June 2022 cumulative Windows Updates. Microsoft strongly recommends that customers install the updates to be fully protected from the vulnerability. Customers whose systems are configured to receive automatic updates do not need to take any further action.
[Exploitability Assessment](): **_Exploitation Detected._**
* * *
## Microsoft Guidance on Intel [Processor MMIO Stale Data Vulnerabilities]()
## [Microsoft Advisory 220002](), [Intel-SA-00615]()
On June 14, 2022, Intel published information about a class of memory-mapped I/O vulnerabilities known as [Processor MMIO Stale Data Vulnerabilities]().
An attacker who successfully exploited these vulnerabilities might be able to read privileged data across trust boundaries. In shared resource environments (such as exists in some cloud services configurations), these vulnerabilities could allow one virtual machine to improperly access information from another. In non-browsing scenarios on standalone systems, an attacker would need prior access to the system or an ability to run a specially crafted application on the target system to leverage these vulnerabilities.
These vulnerabilities are known as:
* [CVE-2022-21123]() | Shared Buffer Data Read (SBDR)
* [CVE-2022-21125]() | Shared Buffer Data Sampling (SBDS)
* [CVE-2022-21127]() | Special Register Buffer Data Sampling Update (SRBDS Update)
* [CVE-2022-21166]() | Device Register Partial Write (DRPW)
**Important**: These vulnerabilities might affect other operating systems and service providers. We advise customers to seek guidance from their respective vendors.
## Windows Server 2022 Azure Edition Core Hotpatch ([KB5014677]()) **OS Build 20348.770**
Windows Server 2022 Azure Edition Core Hotpatch ([KB5014677]()) addresses 22 unique vulnerabilities, ranging in severity from a CVSSv3.1 score of 5.3/10 to 8.8/10, as summarized below.
* * *
### [CVE-2022-30136]()** | Windows Network File System Remote Code Execution (RCE) Vulnerability**
This vulnerability has a CVSSv3.1 score of 9.8/10.
This vulnerability could be exploited over the network by making an unauthenticated, specially crafted call to a Network File System (NFS) service to trigger a Remote Code Execution (RCE).
[Exploitability Assessment](): **_Exploitation More Likely._**
* * *
### [CVE-2022-30158]()** | Microsoft SharePoint Server Remote Code Execution (RCE) Vulnerability**
This vulnerability has a CVSSv3.1 score of 8.8/10.
An authenticated attacker with access to a server that has Sandboxed Code Service enabled could execute code in the context of the web service account.
The attacker must be authenticated and possess the permissions for page creation to be able to exploit this vulnerability.
[Exploitability Assessment](): **_Exploitation Unlikely_**.
* * *
### [CVE-2022-30163]()** | Windows Hyper-V Remote Code Execution (RCE) Vulnerability**
This vulnerability has a CVSSv3.1 score of 8.5/10.
To exploit this vulnerability, an attacker could run a specially crafted application on a Hyper-V guest that could cause the Hyper-V host operating system to execute arbitrary code.
Successful exploitation of this vulnerability requires an attacker to win a race condition.
In this case, a successful attack could be performed from a low privilege Hyper-V guest. The attacker could traverse the guest’s security boundary to execute code on the Hyper-V host execution environment.
[Exploitability Assessment](): **_Exploitation Less Likely._**
* * *
### [CVE-2022-30139]()** | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution (RCE) Vulnerability**
This vulnerability has a CVSSv3.1 score of 7.5/10.
This vulnerability is only exploitable if the MaxReceiveBuffer LDAP policy is set to a value higher than the default value. Systems with the default value of this policy would not be vulnerable.
For more information, please see [LDAP policies]().
Successful exploitation of this vulnerability requires an attacker to prepare the target environment to improve exploit reliability.
[Exploitability Assessment](): **_Exploitation Less Likely._**
* * *
### [CVE-2022-30145]()** | Windows Encrypting File System (EFS) Remote Code Execution (RCE) Vulnerability**
This vulnerability has a CVSSv3.1 score of 7.5/10.
Successful exploitation of this vulnerability requires an attacker to prepare the target environment to improve exploit reliability.
[Exploitability Assessment](): **_Exploitation Less Likely._**
* * *
## Microsoft Last But Not Least
Earlier in June, Microsoft released Microsoft Edge (Chromium-based) vulnerabilities on June 9 Microsoft Edge (Chromium-based) Remote Code Execution (RCE) Vulnerability ([CVE-2022-22021]()) and an additional four (4) vulnerabilities on June 13 ([CVE-2022-2011](), [CVE-2022-2010](), [CVE-2022-2008](), [CVE-2022-2007]()).
* * *
# Notable Adobe Vulnerabilities Patched
Adobe released six (6) [advisories]() with updates to fix 46 vulnerabilities affecting Adobe Animate, Bridge, Illustrator, InCopy, InDesign, and RoboHelp Server. Of these 46 vulnerabilities, 40 are rated as **_Critical_**; ranging in severity from a CVSSv3.1 score of 5.5/10 to 7.8/10, as summarized below.

## [APSB22-24]()** | Security updates available for Adobe Animate**
This update resolves one (1) **_Critical_** vulnerability.
_[Adobe Priority](): 3_
This update resolves a [critical]() vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user.
* * *
## [APSB22-25]()** | Security updates available for Adobe Bridge**
This update resolves 11 **_Critical_** and one (1) _**Important **_vulnerability.
_[Adobe Priority](): 3_
This update addresses [critical]() and [important]() vulnerabilities that could lead to arbitrary code execution, arbitrary file system write and memory leak.
* * *
## [APSB22-26]()** | Security updates available for Adobe Illustrator**
This update resolves 13 **_Critical_**, and four (4) **_Important _**vulnerabilities.
_[Adobe Priority](): 3_
This update resolves [critical]() and [important]() vulnerabilities that could lead to arbitrary code execution and memory leak.
* * *
## [APSB22-29]()** | Security updates available for Adobe InCopy**
This update resolves eight (8) **_Critical_** vulnerabilities.
_[Adobe Priority](): 3_
This update addresses multiple [critical]() vulnerabilities. Successful exploitation could lead to arbitrary code execution.
* * *
## [APSB22-30]()** | Security updates available for Adobe InDesign**
This update resolves seven (7) **_Critical_** vulnerabilities.
_[Adobe Priority](): 3_
This update addresses multiple [critical]() vulnerabilities. Successful exploitation could lead to arbitrary code execution.
* * *
## [APSB22-31]()** | Security updates available for RoboHelp Server**
This update resolves one (1) **_Moderate_** vulnerability.
_[Adobe Priority](): 3_
Adobe has released a security hotfix for RoboHelp Server 11 (Update 3) and prior releases. This hotfix resolves a security vulnerability that allows end-users with non-administrative privileges to manipulate API requests and elevate their account privileges to that of a server administrator.
This update resolves a vulnerability rated [moderate](). Successful exploitation could lead to privilege escalation.
* * *
## About Qualys Patch Tuesday
Qualys Patch Tuesday QIDs are published as [Security Alerts]() typically late in the evening on the day of [Patch Tuesday](), followed later by the publication of the monthly queries for the [Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard]() by Noon on Wednesday.
* * *Read More
References

Back to Main


