[]()
Let’s face it: we all use email, and we all use passwords. Passwords create inherent vulnerability in the system. The success rate of phishing attacks is [skyrocketing](), and opportunities for the attack have greatly multiplied as lives moved online. All it takes is one password to be compromised for all other users to become victims of a data breach.
To deliver additional security, therefore, digital identities rely on verification plasters. MFA (multi-factor authentication) often falls back to knowledge factors such as password resets and OTP codes, but these are still vulnerable. As long as credentials can be shared or intercepted, they can be misused.
What is needed is a paradigm shift from knowledge-based credentials to strong possession-factor security that can’t be compromised, alongside other verification security such as biometrics.
A new possession-factor API now aims to do precisely that, replacing knowledge-based credentials, by using the SIM card for possession factor device binding and user authentication, thus reducing the possibility of phishing.
## **Phishing: a human problem**
Phishing and other types of social engineering rely on the human factor to be the weakest link in a breach. They make use of the convenient, credential-based access afforded to the average user of a platform, by tricking those average users into sharing credentials. And it works: [83%]() of organizations surveyed said they experienced a successful email-based phishing attack in 2021.
## **Even 2FA codes are now targets**
It’s common knowledge that passwords can be shared and, therefore, easily phished. But a lesser-known fact is that many forms of 2FA such as the OTP or PIN code added in an effort to reinforce the known weaknesses in passwords are also phishable.
Even worse, criminals are now targeting these methods specifically: researchers recently found that [over 1,200]() phishing kits designed to steal 2FA codes are out in operation.
The answer to identity and access management, therefore, is not to apply more patches that kill the user experience, as these don’t truly keep attackers out. Instead, MFA needs a stronger, simpler possession factor with nothing to type, meaning nothing to phish.
Purpose-designed MFA possession factors include security dongles or tokens. But they’re expensive, and not something the average user will buy. Stronger security for everyone can only work with devices that are widely available, easy to use, easy to integrate, and cost-effective.
Enter the SIM card. It’s inside everyone’s mobile phone, and is built on cryptographic security when connecting to mobile network authentication.
Now, for the first time, an [API from tru.ID]() opens up SIM-based mobile network authentication to every business and app developer, meaning you can leverage the security of the SIM card as a secure possession factor for MFA.
## **SIM-based authentication: the new phishing-resistant possession factor **
The SIM card has a lot going for it. SIM cards use the same highly secure, cryptographic microchip technology that is built into every credit card. It’s difficult to clone or tamper with, and there is a SIM card in every mobile phone so every one of your users already has this hardware in their pocket.
The combination of the mobile phone number with its associated SIM card identity (the IMSI) is a combination that’s difficult to phish as it’s a silent authentication check.
The user experience is superior too. Mobile networks routinely perform silent checks that a user’s SIM card matches their phone number in order to let them send messages, make calls, and use data ensuring real-time authentication without requiring a login.
Until recently, it wasn’t possible for businesses to program the authentication infrastructure of a mobile network into an app as easily as any other code. tru.ID makes network authentication available to everyone.
[Adding the tru.ID SDK]() into existing account journeys that use the mobile phone number instantly enables possession-factor security for every user. Moreover, with no extra input from the user, there’s no attack vector for malicious actors: SIM-based authentication is invisible, so there’s no credentials or codes to steal, intercept or misuse.
tru.ID does not access the user’s SIM card. Instead, it verifies SIM card status directly with the mobile operator in real-time. It checks that a phone number hasn’t been assigned to another SIM and for recent SIM changes, helping to prevent SIM swap fraud.
## **An example scenario to enable SIM-based verification**
Even though there are a number of processes described in the scenario below, the end user of the system has to do only one thing provide their mobile phone number.
**1 ** After the user provides their mobile number, the tru.ID API performs a lookup for the phone number to determine which mobile network operator (MNO) it is assigned to.
[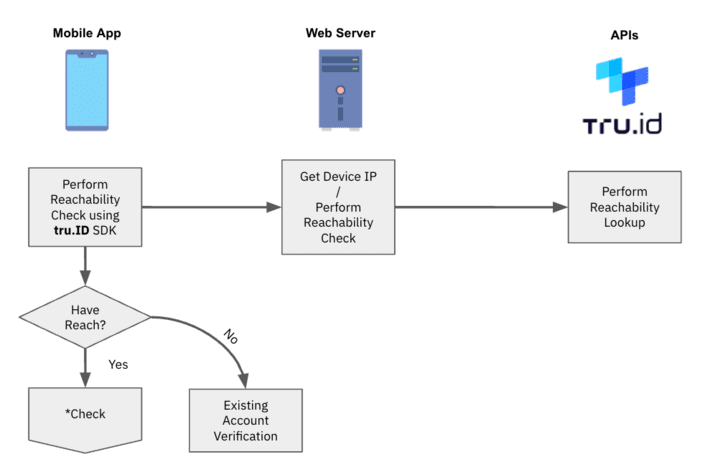]()
**2 ** tru.ID requests from the MNO a unique Check URL to begin the mobile authentication workflow.
**3 ** tru.ID stores the MNO’s Check URL, and returns a tru.ID Check URL to your web server for the mobile device to open.
[]()
**4 ** The mobile application opens the tru.ID Check URL. It is preferred to use tru.ID SDKs for this because it forces the web request to be over a mobile data session.
**5 ** The MNO will receive the web request via a redirect from the tru.ID platform.
**6 ** The final redirect takes the device to the web server’s redirect url endpoint. The body of this request will contain a ‘code’ and the ‘check_id’, and the web server submits this code to tru. ID’s API to complete the SubscriberCheck process.
[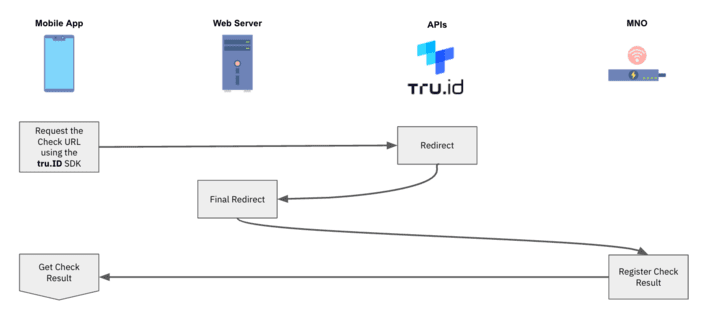]()
**7 ** The MNO then determines if the phone number associated with the authenticated mobile data session matches the phone number associated with the requested Check URL. If it does, then the phone number has been successfully verified.
**8 ** tru.ID performs a SIM card look up and stores the result of its status.
**9 ** On completion of the Check URL request, and when the SIM card status has been retrieved, the mobile application can request the result of the phone verification from the tru.ID API.
[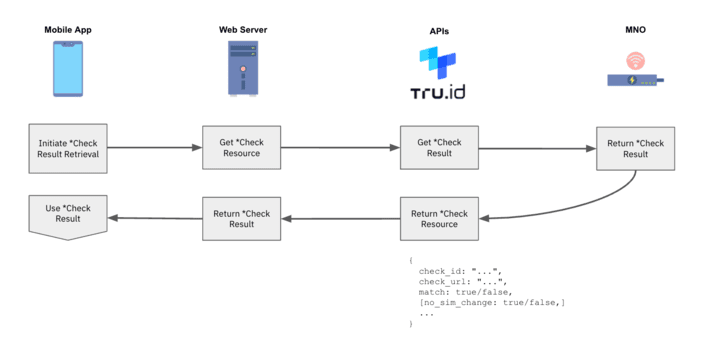]()
**10 ** Use the phone verification match and SIM card change `no_sim_change` properties within your application logic.
[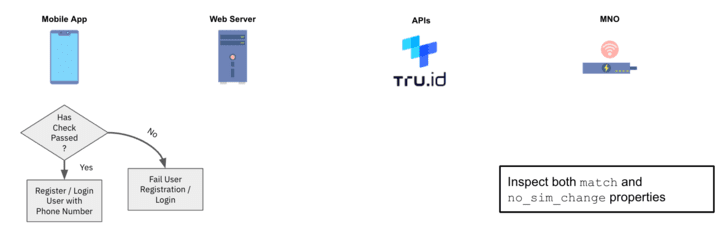]()
## **How to get started**
With tru. ID’s developer platform, you can start testing SIM-based authentication right away, for free, and make your first API call within minutes.
To find out how next-gen authentication can deliver high security, low friction authentication experiences to your users, simply book a free [demo]() or visit [tru.ID]().
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


