
Today, Talos is publishing a glimpse into the most prevalent threats we’ve observed between Nov. 3 and Nov. 10. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, this post will summarize the threats we’ve observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, [Snort.org](), or [ClamAV.net]().
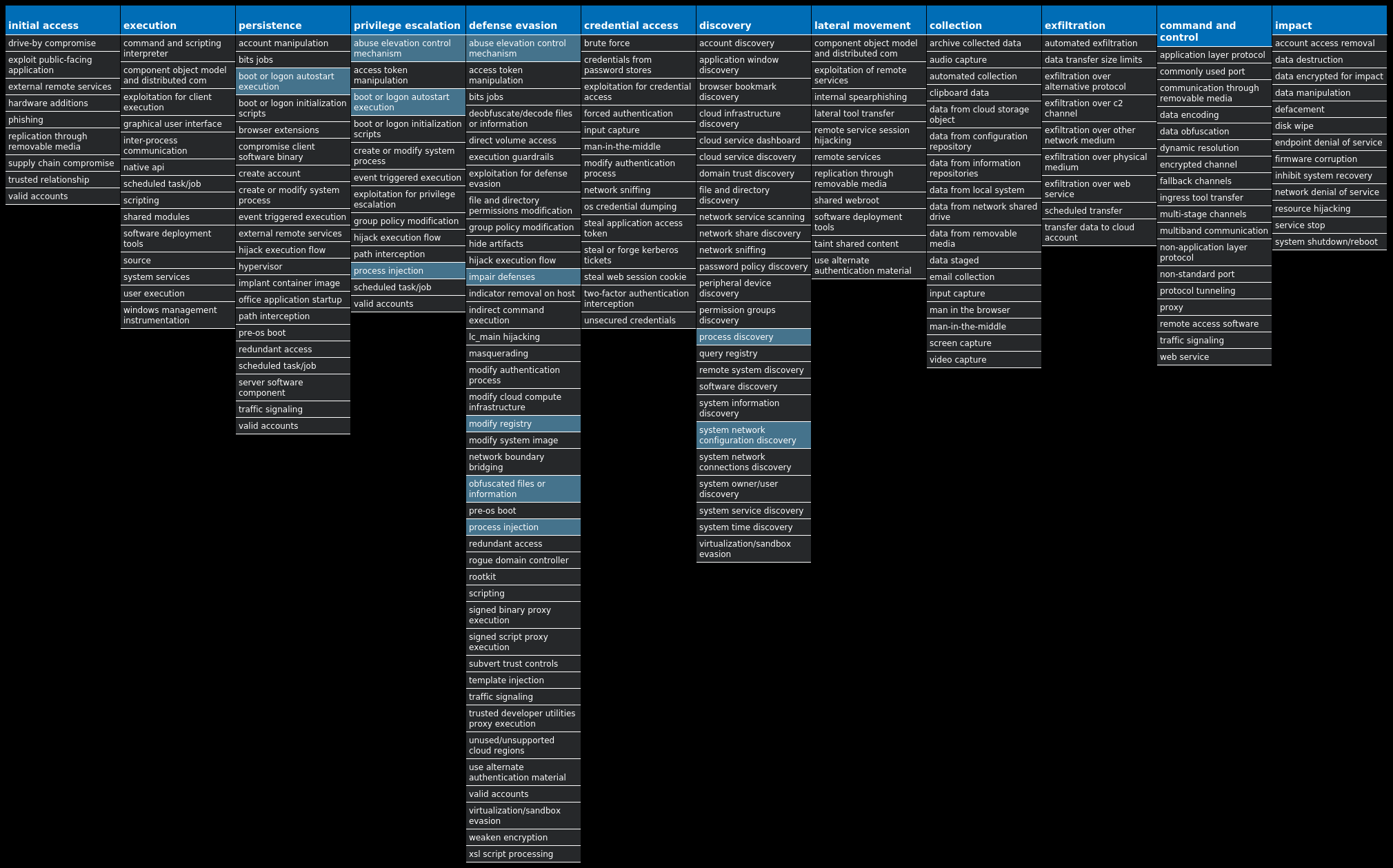
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found [here]() that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
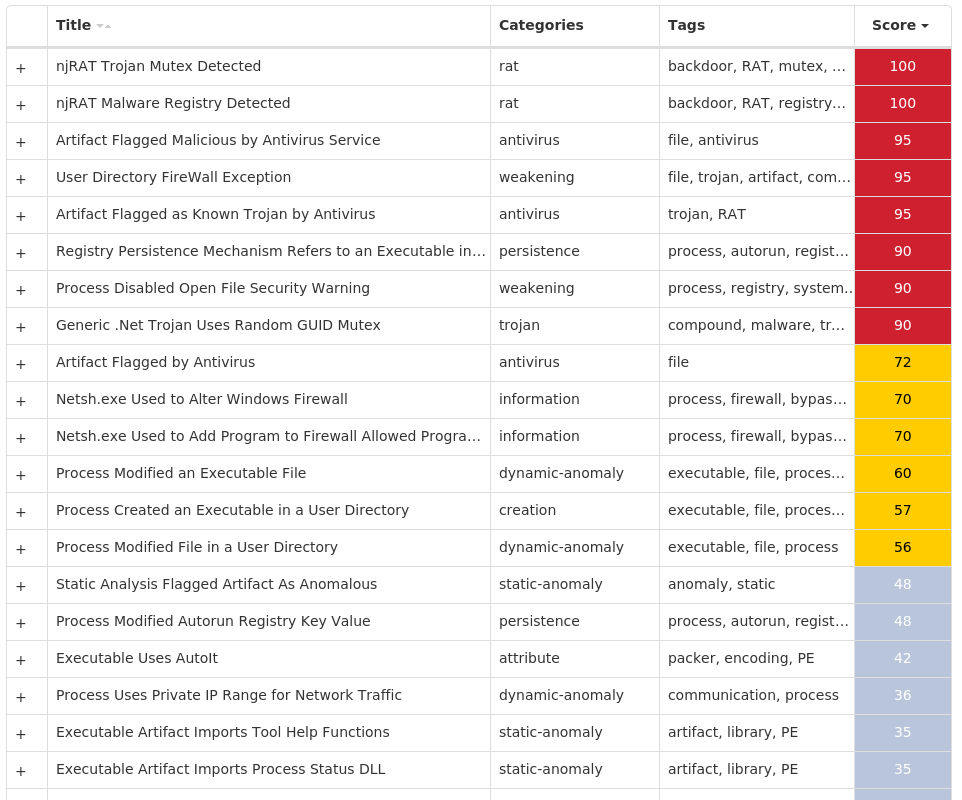
Threat Name| Type| Description
—|—|—
Win.Dropper.njRAT-10013547-0| Dropper| njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim’s webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014.
Win.Dropper.Zeus-10013588-0| Dropper| Ponystealer is known to steal credentials from more than 100 different applications and may also install other malware such as a remote access tool (RAT).
Win.Dropper.Tofsee-10013531-0| Dropper| Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator’s control.
Win.Dropper.Glupteba-10013467-0| Dropper| Glupteba is a multi-purpose trojan that uses the infected machine to mine cryptocurrency and steal sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the Bitcoin blockchain to store configuration information.
Win.Downloader.Upatre-10013406-0| Downloader| Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware.
Win.Malware.Diztakun-10013372-0| Malware| Diztakun is a trojan dropped by another malware family or downloaded by a user that will modify system settings. This malware is known for its use of Image File Execution Options (IFEO) to gain persistence and inject itself into other executables.
Doc.Malware.Valyria-10013349-0| Malware| These variants of Valyria are malicious Microsoft Word documents that contain embedded VBA macros used to distribute other malware.
* * *
## Threat Breakdown
### Win.Dropper.njRAT-10013547-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 12 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESSYSTEM
Value Name: EnableLUA`| 12
`S-1-5-21-2580483871-590521980-3826313501-500
Value Name: di`| 12
`ENVIRONMENT
Value Name: SEE_MASK_NOZONECHECKS`| 12
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESSYSTEM
Value Name: ConsentPromptBehaviorAdmin`| 12
`SOFTWARE7657C14284185FBD3FB108B43C7467BA`| 12
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 7657c14284185fbd3fb108b43c7467ba`| 12
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 7657c14284185fbd3fb108b43c7467ba`| 12
`SOFTWARE7657C14284185FBD3FB108B43C7467BA
Value Name: [kl]`| 12
`LOCAL SETTINGSSOFTWAREMICROSOFTWINDOWSSHELL
Value Name: NodeSlots`| 1
`LOCAL SETTINGSSOFTWAREMICROSOFTWINDOWSSHELL
Value Name: MRUListEx`| 1
`LOCAL SETTINGSSOFTWAREMICROSOFTWINDOWSSHELL\1
Value Name: MRUListEx`| 1
`LOCAL SETTINGSSOFTWAREMICROSOFTWINDOWSSHELL\1
Value Name: MRUListEx`| 1
Mutexes| Occurrences
—|—
`7657c14284185fbd3fb108b43c7467ba`| 12
Files and or directories created| Occurrences
—|—
`%TEMP%server.exe`| 12
`%TEMP%`| 12
`%TEMP%29222922.exe`| 1
`%TEMP%67816781.exe`| 1
`%TEMP%49284928.exe`| 1
`%TEMP%29242924.exe`| 1
`%TEMP%61196119.exe`| 1
`%TEMP%29892989.exe`| 1
`%TEMP%23692369.exe`| 1
`%TEMP%28942894.exe`| 1
`%TEMP%46274627.exe`| 1
`%TEMP%960960.exe`| 1
`%TEMP%70157015.exe`| 1
`%TEMP%63296329.exe`| 1
#### File Hashes
`00ac33ba819475ab380691c51b37ef3f0aae4789dea3ee19a941dc2875350a91
0dcd6cf9cca20830f39bf99fc803ce4036f60a8c9599cbf8d690d63b15edd7c4
1047e229661a188dd1b094366c558834435208bb909b2ad14bb221eb1c2c81b7
113f0a0e7072f324ad84c649d08970ee7e68e334061a099f0c1b6d9413951985
1987b7a30ffdcca9651037e997520d4326271232f8ac40e470c5697ae1a74d92
48144f08dfb3de926ad22f24b600bea45c1138fd7d4581b32aa25662439c6d82
4ffc3afac19e6da3d800391745ce2ff9eedc1d8b19de0cf5ab95cd432a55829c
58fe188a03e36361c73216b1fca0c3f471e1b5b582af50d4755f681fad664790
6a81e146ef0ebf60390eefd50f8ba98b1bb003bbb14ed0d358be18a5810db989
7e7e12bca94dedba69a99691400bd54adcedb12ccb39a98c663e553c882d3f52
c9d1a2d3921d5aa33d493069c33a8a852df063f0e4b9313b05fc1c7a1eec4fbe
d5f6dadb21774b0ddcef4a8ee027e6c953701a3a2b3744eed53664da88a4f1f0
`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
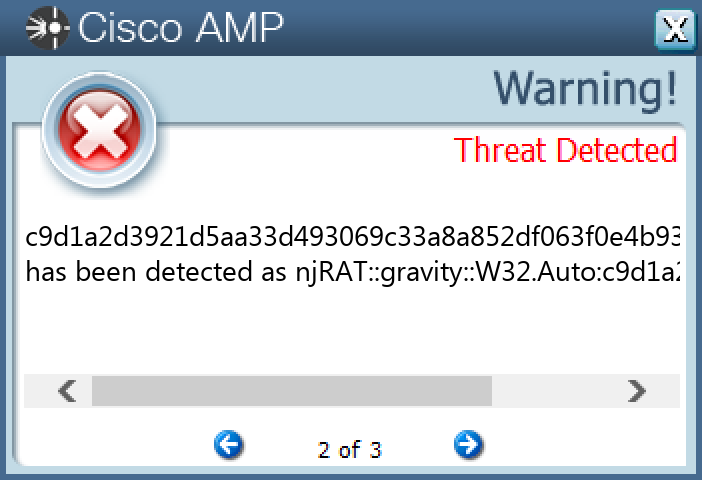
#### Secure Malware Analytics
#### MITRE ATT&CK
* * *
### Win.Dropper.Zeus-10013588-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 30 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472F-A0FF-E1416B8B2E3A}
Value Name: FaviconPath`| 7
`SOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES{0633EE93-D776-472F-A0FF-E1416B8B2E3A}
Value Name: Deleted`| 7
`SOFTWAREMICROSOFTINTERNET EXPLORERSEARCHSCOPES
Value Name: DefaultScope`| 7
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXTSTATS{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}`| 7
`SoftwareMicrosoft`| 7
`SOFTWAREMICROSOFTINTERNET EXPLORERPRIVACY
Value Name: CleanCookies`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
Value Name: CheckSetting`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting`| 4
`SOFTWAREDC3_FEXEC`| 3
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: Taskmgr`| 2
`SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: UserInit`| 2
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: {1A01E4EA-2D84-D670-B0DB-AEA399D273CB}`| 2
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: LANDrivers`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: help`| 1
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: help`| 1
`SOFTWAREMICROSOFTKEWUZA
Value Name: Kuombao`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: {8E249526-629F-428A-AE89-37BA344B74E9}`| 1
`SOFTWAREMICROSOFTPAHUIH
Value Name: Ozzunaso`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: {ACEB48EA-5F14-3060-00C6-58E8C8BD1132}`| 1
`SOFTWAREWOW6432NODEMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: Shell`| 1
`SOFTWAREMICROSOFTDACOU
Value Name: Raohfyiqu`| 1
`SOFTWAREMICROSOFTMAQU
Value Name: Izalfe`| 1
Mutexes| Occurrences
—|—
`UACMutexxxxx`| 16
`Local{}`| 7
`GLOBAL{}`| 6
`UFR3`| 3
`DC_MUTEX-TKAU2Y6`| 2
`Global19e8f421-7c3b-11ee-9660-001517aeb5c3`| 1
`Global1d29d6e1-7c3b-11ee-9660-0015174de944`| 1
`Global1ba38501-7c3b-11ee-9660-001517b129f4`| 1
`DC_MUTEX-V8SHNMZ`| 1
`Global31c933c1-7c8b-11ee-9660-0015171a3bbd`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`192[.]229[.]211[.]108`| 7
`13[.]107[.]21[.]200`| 5
`142[.]250[.]64[.]65`| 1
`31[.]170[.]164[.]170`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`www[.]bing[.]com`| 7
`cacerts[.]digicert[.]com`| 7
`c0p1[.]com`| 2
`salarsokoot[.]no-ip[.]biz`| 2
`www[.]unitedstateforus[.]com`| 2
`tf2m[.]ru`| 1
`pin47[.]blogspot[.]ru`| 1
`ftp[.]ytruhgnhvjukuffkk[.]p[.]ht`| 1
`gbproof[.]org`| 1
`spitfire[.]ufcfan[.]org`| 1
`maldovaars[.]com`| 1
Files and or directories created| Occurrences
—|—
`%APPDATA%`| 10
`%TEMP%tmp.bat`| 7
`%APPDATA%.exe`| 7
`%SystemRoot%SysWOW64Driverstask.exe`| 2
`%APPDATA%InstallDir`| 1
`%APPDATA%InstallDirhelp.exe`| 1
`%System32%windi32.exe`| 1
`%ProgramData%systemskey.ini`| 1
`%APPDATA%Utusuvuw.oxi`| 1
`%TEMP%cd8e8b5b178c2d9e5acbdeda4854746eb2709cba2fbb2e986ae1dc25f6c0d575.exe`| 1
`%TEMP%YaCheck.exe`| 1
`%APPDATA%Weyfeqsyl.vot`| 1
`%APPDATA%Ivlovqinee.asy`| 1
`%TEMP%5d673897a553689e7b4ca6d3be149211f1027f9c82891af1ce65ea1c9639119b.exe`| 1
`%TEMP%report_05-11-2023_18-26-11-11B0A35710D760E40567A55CF3411F9E-NLGD.bin`| 1
`%TEMP%NO_PWDS_report_05-11-2023_18-26-11-11B0A35710D760E40567A55CF3411F9E-NLGD.bin`| 1
`%APPDATA%Hyraixviaqf.alh`| 1
`%APPDATA%Onuvytalyk.cea`| 1
`%APPDATA%Ypephuni.ryo`| 1
`%APPDATA%Ziyblousoxh.ili`| 1
`%SystemRoot%serwos.exe`| 1
#### File Hashes
`097f1d24084ad3668f6f92daa4fc05da8540623492c158ea41ee7ec86399bd21
1d5efb1de624668fa8dbc3bde4e29f3a1c57491afa34ed7006c01821fc9324d1
28ec85247bb5cfc649e866fd234cfa219ec1fc580dee22bb14889a7654361eb6
2cb399731194831e8aef70fa92249eae3ac2c53d78df8601e48d824315d0f507
4c91493d94e0dfb3e814f465e0cb050177168a6dbb916572d994f09b3c116c7c
4d565325e1c7e54210f3178909fc05d45984b4bc623d9fe3804497f713604e9c
4f23fa7f21f6b529f2581cee723ac0f4ceaefac922868063e0c4d533ac475ddd
4f3823d6c5cc2500edbfe0909c60667b126e0439e77c8b1d5c4c40d459b96387
527fad1b322cf36c0b367766e560f8bb18181c172d824884d1a2ebf40f6a35bd
55cc7012c73a0f31823c4bd740affc2eb1efdeecdfc7c7a569d5d666d6dc48d5
5d673897a553689e7b4ca6d3be149211f1027f9c82891af1ce65ea1c9639119b
5eba33c82756f682fab6f35ee6d16e3675d5cd611fbf1dc46996fd24fa7f5ea2
79b3c719494efd43623afeadf817746d663819c88f2b6f67e92fb48c5092eba4
7fc8139b2e5cace8c217c164f62097748cf1125fdba8de1b41e1858f540bf6c9
83053718f2278338d9b3c934c5645f94f5625d66a56d28e11424cd2f9e46004f
83a048271aefcc6707c1d994f55d78a85d3d05c734185b93381ed20888043c06
947d964061c1cb1ecf83cd9af68acd729ba992c807c6f2defbe0c595562c690b
956275197ed36332417fe84b947e5d7ac894fb67fa262dc765444c952a13b5bc
a4ab9fb82f2c093ea3466b57609da2503e28c245ea0554a2a228ab41dde68a5c
aa546035f13f04ca14585c866f35b54e38a631064cee8d8012d3a477b2c33d89
b6748ee9af728376aea6171e27fa0281421b9404e6ba150ff99fc726241db140
b9a641ff22644aa474e91b92b6e1c71b91d057b1315d291f2f22b9713dd5608a
bb8bbeb6a2496926919a70a4dd3817a20e8f0137afb3f13f3fc010b8681eed43
c0f4f1ac3a0ceb4d6623f88a54ee15e6e73bcecb02e0c4230d4acd9f00746e80
c2560bc32b415ad78cddee6794738b8484575932ea3237acd61a2d1e4389c412`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
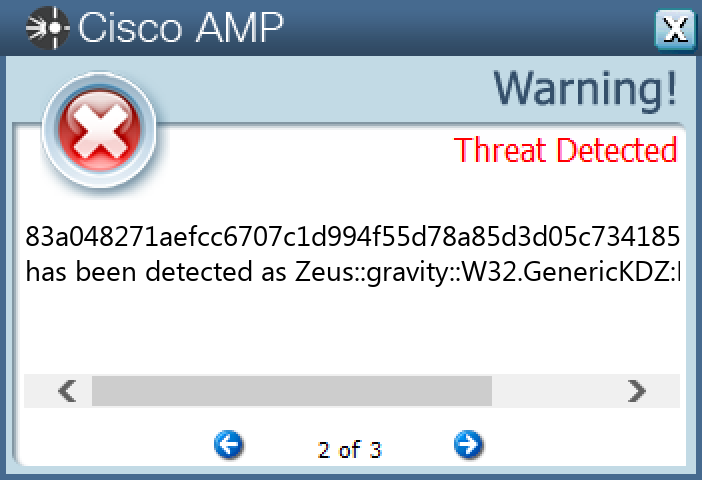
#### Secure Malware Analytics
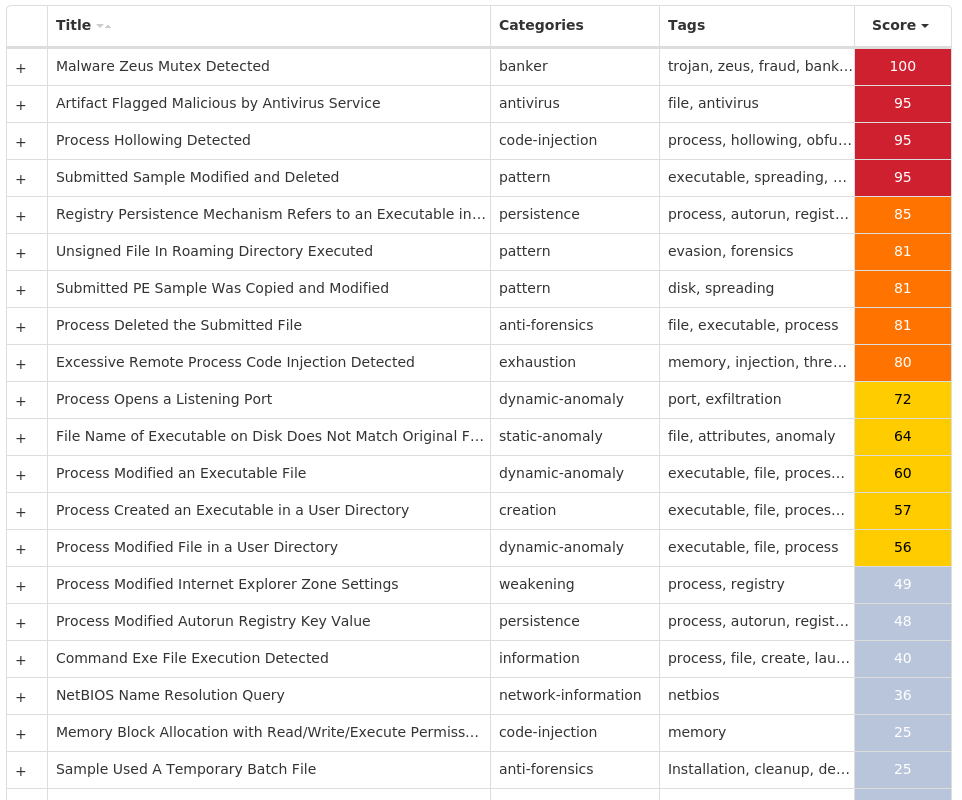
#### MITRE ATT&CK
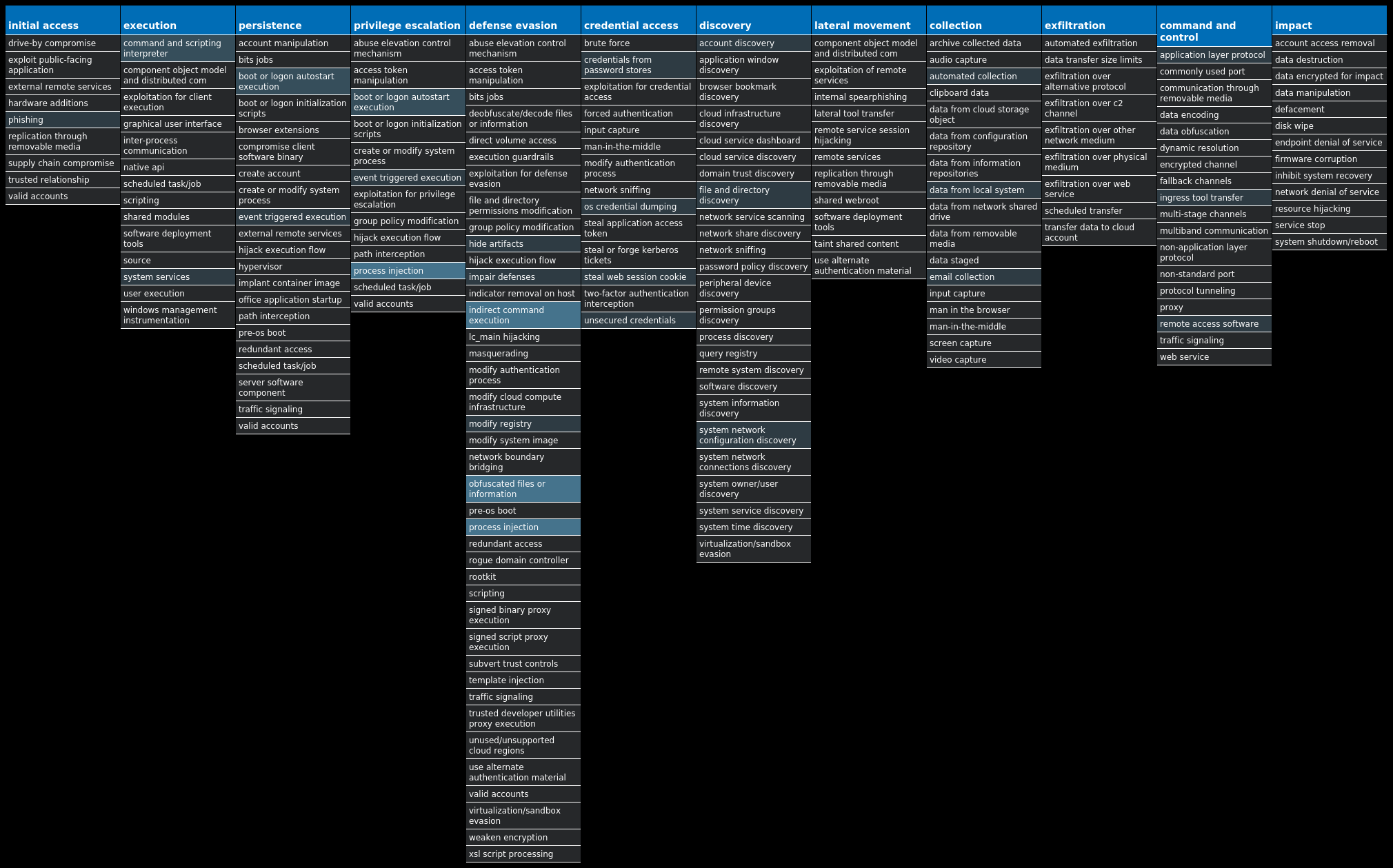
* * *
### Win.Dropper.Tofsee-10013531-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 17 samples
Registry Keys| Occurrences
—|—
`SYSTEMCONTROLSET001SERVICES`| 14
`SYSTEMCONTROLSET001SERVICES
Value Name: Type`| 14
`SYSTEMCONTROLSET001SERVICES
Value Name: Start`| 14
`SYSTEMCONTROLSET001SERVICES
Value Name: ErrorControl`| 14
`SYSTEMCONTROLSET001SERVICES
Value Name: DisplayName`| 14
`SYSTEMCONTROLSET001SERVICES
Value Name: WOW64`| 14
`SYSTEMCONTROLSET001SERVICES
Value Name: ObjectName`| 14
`.DEFAULTCONTROL PANELBUSES`| 13
`.DEFAULTCONTROL PANELBUSES
Value Name: Config2`| 13
`SYSTEMCONTROLSET001SERVICES
Value Name: Description`| 13
`.DEFAULTCONTROL PANELBUSES
Value Name: Config0`| 13
`.DEFAULTCONTROL PANELBUSES
Value Name: Config1`| 13
`SYSTEMCONTROLSET001SERVICES
Value Name: ImagePath`| 13
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64blniewvr`| 2
`SOFTWAREMICROSOFTASSISTANCECLIENT1.0SETTINGS
Value Name: IsConnected`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64isupldcy`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64oyavrjie`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64vfhcyqpl`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64mwytphgc`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64eoqlhzyu`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64gqsnjbaw`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64zjlgcutp`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64dnpkgyxt`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64lvxsogfb`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64akmhdvuq`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`176[.]113[.]115[.]136`| 14
`80[.]66[.]75[.]4`| 14
`176[.]113[.]115[.]135`| 14
`45[.]143[.]201[.]238`| 14
`176[.]113[.]115[.]84`| 14
`62[.]122[.]184[.]92`| 14
`80[.]66[.]75[.]77`| 14
`83[.]97[.]73[.]44`| 14
`31[.]13[.]65[.]174`| 13
`31[.]13[.]65[.]52`| 13
`172[.]217[.]165[.]132`| 10
`93[.]115[.]25[.]49`| 10
`34[.]120[.]241[.]214`| 10
`93[.]115[.]25[.]10`| 9
`93[.]115[.]25[.]73`| 9
`93[.]115[.]25[.]13`| 8
`93[.]115[.]25[.]110`| 8
`158[.]160[.]73[.]47`| 8
`149[.]154[.]167[.]99`| 6
`172[.]217[.]21[.]164`| 6
`23[.]0[.]18[.]123`| 6
`84[.]201[.]152[.]220`| 6
`104[.]47[.]53[.]36`| 4
`20[.]70[.]246[.]20`| 4
`87[.]240[.]129[.]135`| 3
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`249[.]5[.]55[.]69[.]in-addr[.]arpa`| 14
`www[.]google[.]com`| 14
`vanaheim[.]cn`| 14
`249[.]5[.]55[.]69[.]bl[.]spamcop[.]net`| 13
`249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org`| 13
`249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net`| 13
`249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org`| 13
`249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org`| 13
`i[.]instagram[.]com`| 13
`microsoft-com[.]mail[.]protection[.]outlook[.]com`| 13
`microsoft[.]com`| 13
`www[.]instagram[.]com`| 13
`www[.]evernote[.]com`| 10
`steamcommunity[.]com`| 7
`www[.]tiktok[.]com`| 6
`t[.]me`| 6
`api[.]steampowered[.]com`| 6
`www[.]youtube[.]com`| 4
`oauth[.]vk[.]com`| 4
`identity[.]bitwarden[.]com`| 4
`www[.]ebay[.]co[.]uk`| 3
`api[.]vk[.]com`| 3
`ustawienia[.]poczta[.]onet[.]pl`| 3
`work[.]a-poster[.]info`| 2
`api[.]twitter[.]com`| 2
*See JSON for more IOCs
Files and or directories created| Occurrences
—|—
`%SystemRoot%SysWOW64`| 14
`%SystemRoot%SysWOW64configsystemprofile`| 13
`%SystemRoot%SysWOW64configsystemprofile:.repos`| 13
`%TEMP%.exe`| 12
`%ProgramData%MicrosoftAssistanceClient1.0en-USHelp_MValidator.Lck`| 1
`%TEMP%qzfqodv.exe`| 1
`%TEMP%foufdsk.exe`| 1
#### File Hashes
`03408910e1c86cc056f6135cb25bfdce0a3530c3dedd2d96dc6a40602f837c25
1599d9770df3e105a97d69cc47a49732db055e9e7a2dc5e7c777b8b33d3a7e35
1c1062e65701fdea8fa0eca0884f974b8c9e6cfe70391dfc33fcbf5594b1ebf8
201287642e01dd6fcc785929ac1dd66a9b9961f95128267d220993af7f3d4c88
2955d095548626a3a61cf4358d7d6de5f3233d14592f94e0616a74b3169dab96
2c4bb17a2e6d629b65c33e0c0c59ecf4dd36e5b8d51cb3c46ce9310f7c81138c
3d0d45b889aa467906cb79f015ea61d6b80f19b4d454affabe12bfe4bed95961
42ba3cb49ff67fd0526e68328c20c1387f8c671ccb5f0a2eb832c50d9c950770
518e73ce19f80568856c6fdc5256a36bce0e0a3d90c10fad0785a49126ac3773
70b11bca91cb73e563a87fd4a09fa1c8618c650cfb19d1ac7933c39b35cd8a0c
80015dfd0fb4f0867daa13132c1ac922cc94c850853b874bae77e42c5248a7ee
98c2ff26ab1bc639c2f1600d6127245b719dbfe619c784a9458b826d5aeeda4b
cc0cdaa2852647954c8cabd65e9643ce8ad5efd7b375aa8ebae117b6239aada1
d6ac332db3811db38ec9a3901df479e6e76a12f7cc2485d52ad6d3395f65006f
f73955aea9b55ae0a5088f688ab408a394c2a6cfb88d4a8ae55370ff4356fd16
f909a687d10996b76a0b847d7fbd686231b4f60c3c134e1bdb4144555fd67a13
ffb9de19ee6cc9a60877abaac8fb9aa14922438b47603084a2470330644de239
`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
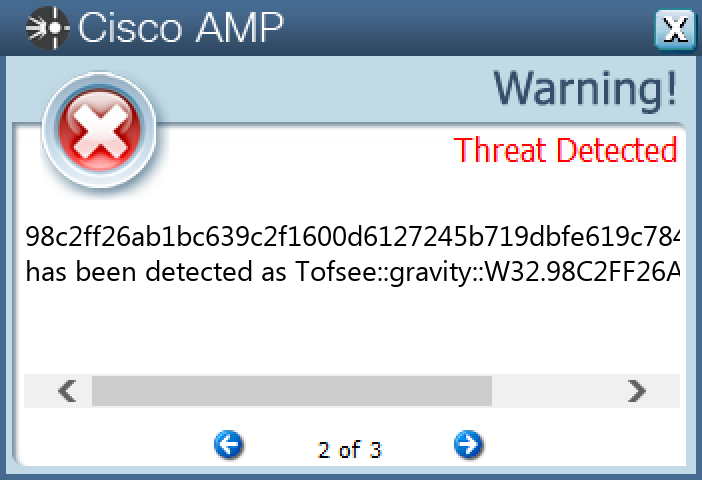
#### Secure Malware Analytics
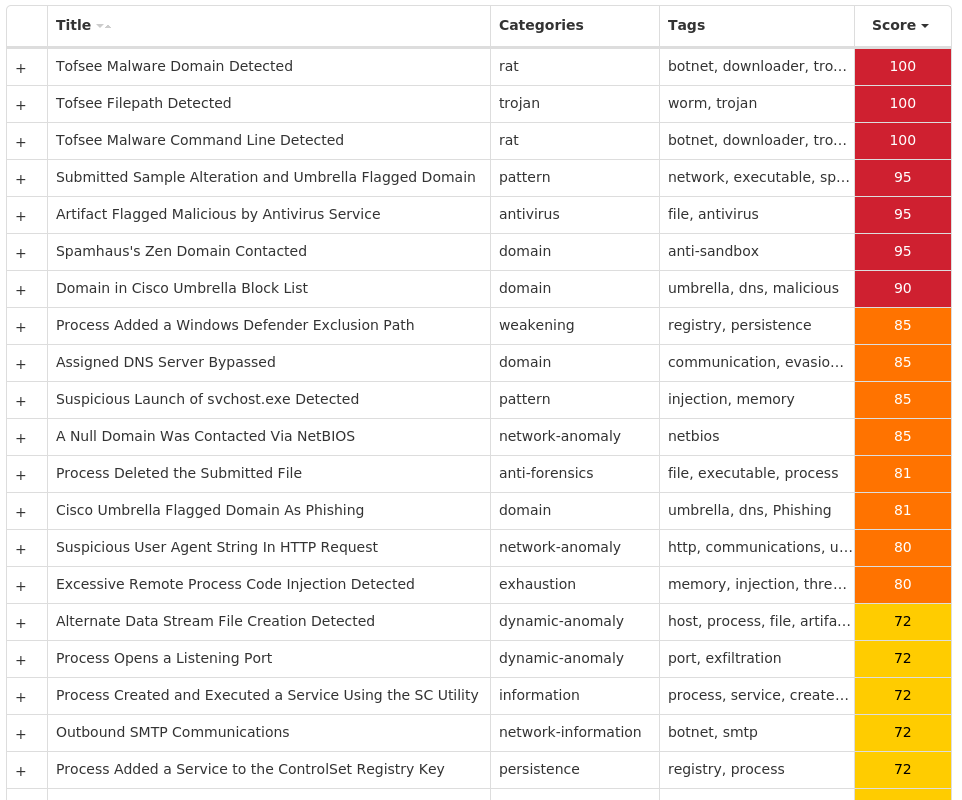
#### MITRE ATT&CK

* * *
### Win.Dropper.Glupteba-10013467-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 12 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTA1890984
Value Name: PatchTime`| 12
`SOFTWAREMICROSOFTA1890984
Value Name: PGDSE`| 12
`SYSTEMCONTROLSET001SERVICESVBOXWDDM
Value Name: DisplayName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXWDDM
Value Name: WOW64`| 12
`SYSTEMCONTROLSET001SERVICESVBOXWDDM
Value Name: ObjectName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: Type`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: Start`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: ErrorControl`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: ImagePath`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: DisplayName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: WOW64`| 12
`SYSTEMCONTROLSET001SERVICESVBOXSF
Value Name: ObjectName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: Type`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: Start`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: ErrorControl`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: ImagePath`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: DisplayName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: WOW64`| 12
`SYSTEMCONTROLSET001SERVICESVBOXMOUSE
Value Name: ObjectName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXGUEST
Value Name: Type`| 12
`SYSTEMCONTROLSET001SERVICESVBOXGUEST
Value Name: Start`| 12
`SYSTEMCONTROLSET001SERVICESVBOXGUEST
Value Name: ErrorControl`| 12
`SYSTEMCONTROLSET001SERVICESVBOXGUEST
Value Name: ImagePath`| 12
`SYSTEMCONTROLSET001SERVICESVBOXGUEST
Value Name: DisplayName`| 12
`SYSTEMCONTROLSET001SERVICESVBOXGUEST
Value Name: WOW64`| 12
Mutexes| Occurrences
—|—
`GlobalSetupLog`| 12
`GlobalWdsSetupLogInit`| 12
`Globalh48yorbq6rm87zot`| 12
`WininetConnectionMutex`| 12
`Globalqtxp9g8w`| 12
`GlobalxmrigMUTEX31337`| 6
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`204[.]79[.]197[.]219`| 12
`20[.]150[.]79[.]68`| 9
`104[.]21[.]23[.]184`| 8
`20[.]150[.]38[.]228`| 6
`142[.]250[.]15[.]127`| 5
`20[.]150[.]70[.]36`| 5
`162[.]159[.]134[.]233`| 4
`172[.]67[.]212[.]188`| 4
`185[.]82[.]216[.]104`| 4
`162[.]159[.]130[.]233`| 3
`3[.]33[.]249[.]248`| 3
`185[.]82[.]216[.]108`| 3
`185[.]82[.]216[.]111`| 3
`162[.]159[.]133[.]233`| 2
`162[.]159[.]129[.]233`| 2
`74[.]125[.]128[.]127`| 2
`172[.]253[.]120[.]127`| 2
`185[.]82[.]216[.]96`| 2
`162[.]159[.]135[.]233`| 1
`81[.]3[.]27[.]44`| 1
`142[.]250[.]112[.]127`| 1
`142[.]250[.]144[.]127`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`msdl[.]microsoft[.]com`| 12
`vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net`| 12
`vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net`| 12
`cdn[.]discordapp[.]com`| 12
`walkinglate[.]com`| 12
`stun1[.]l[.]google[.]com`| 5
`stun[.]sipgate[.]net`| 3
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]createupdate[.]org`| 3
`stun4[.]l[.]google[.]com`| 2
`stun3[.]l[.]google[.]com`| 2
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]alldatadump[.]org`| 2
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]localstats[.]org`| 2
`server10[.]alldatadump[.]org`| 2
`stun[.]l[.]google[.]com`| 1
`stun[.]stunprotocol[.]org`| 1
`stun2[.]l[.]google[.]com`| 1
`stun[.]ipfire[.]org`| 1
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]filesdumpplace[.]org`| 1
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]allstatsin[.]ru`| 1
`server3[.]statscreate[.]org`| 1
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]statscreate[.]org`| 1
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]theupdatetime[.]org`| 1
`79102df1-5f9d-4ca9-bdf6-1fa1060285b4[.]uuid[.]myfastupdate[.]org`| 1
`server3[.]createupdate[.]org`| 1
`server1[.]myfastupdate[.]org`| 1
*See JSON for more IOCs
Files and or directories created| Occurrences
—|—
`%SystemRoot%LogsCBSCBS.log`| 12
`%SystemRoot%rss`| 12
`%SystemRoot%rsscsrss.exe`| 12
`%TEMP%csrss`| 12
`%TEMP%csrssdsefix.exe`| 12
`%TEMP%csrsspatch.exe`| 12
`%System32%driversWinmon.sys`| 12
`%System32%driversWinmonFS.sys`| 12
`%System32%driversWinmonProcessMonitor.sys`| 12
`%SystemRoot%windefender.exe`| 12
`%TEMP%Symbols`| 12
`%TEMP%Symbolsntkrnlmp.pdb`| 12
`%TEMP%Symbolsntkrnlmp.pdb9E22A5947A15489895CE716436B45BE02`| 12
`%TEMP%Symbolsntkrnlmp.pdb9E22A5947A15489895CE716436B45BE02download.error`| 12
`%TEMP%Symbolspingme.txt`| 12
`%TEMP%Symbolswinload_prod.pdb`| 12
`%TEMP%Symbolswinload_prod.pdbB7B16B17E078406E806A050C8BEE2E361`| 12
`%TEMP%Symbolswinload_prod.pdbB7B16B17E078406E806A050C8BEE2E361download.error`| 12
`%TEMP%dbghelp.dll`| 12
`%TEMP%ntkrnlmp.exe`| 12
`%TEMP%osloader.exe`| 12
`%TEMP%symsrv.dll`| 12
`%TEMP%csrssDBG0.tmp`| 12
`%System32%Taskscsrss`| 12
`%TEMP%csrssinjector`| 12
*See JSON for more IOCs
#### File Hashes
`053421a64d181eacb1e3c1bb16e87107462a32c11c91c7f77059adf82198dd4a
18e21947b1c4b6a364e6844183a2e1146a7aff868f7659de8ff4e2094c138aae
1ff3ea05dc55c0f1bcf63d5ed247c30db85ead74eb543e7fa42d612f5a877a58
2b6fe7559d8372ace429d8e8e96ff196d0af56593a31b33d8b6967f3e92de824
2c3498ae141cab2a551e48070676e127882cd72d56ac29b742a968042aa380ca
39322869eed23d913a8e2ab6fbd902e9bc1d1a2a5d2c537b9ecabe10172723c6
5bc8c1bfbf0506a24f4561666117a459f91404b859b61112a0a709404f2cb3d9
aa7c8cd6668998b0a41960ae3a65c30fec966c81c9ec49a3e8f6b85e1faeda34
ccfe83f9d4edf14bc10432f13b7d536893f967d9aba631c4a58c2333d78eb202
cfb46da0a07f529ccf93fa018e57a878ea1a8192587757d4e4d1789225787310
d29b1f159ddc23aa0ce5bd9603bce5707516d026da67cba7997a15ad06dd291a
eef3627e8e0145aa519300d639898f7478ae1f0151eb1b5b788c834ffc6f786b
`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
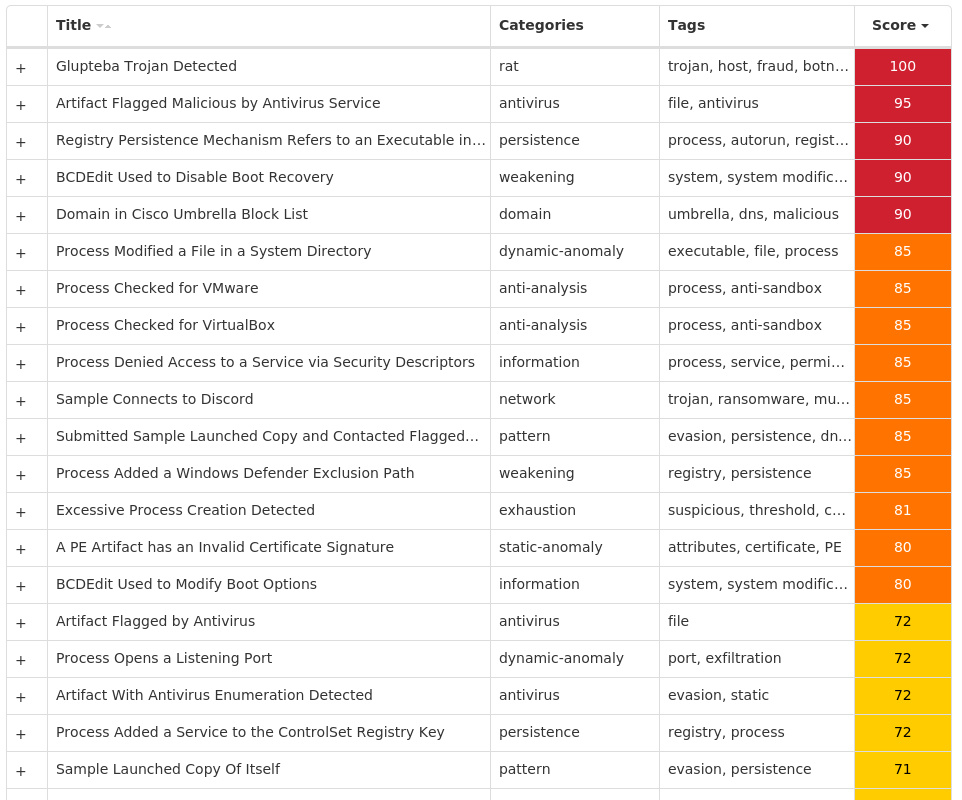
#### MITRE ATT&CK

* * *
### Win.Downloader.Upatre-10013406-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 67 samples
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`104[.]18[.]114[.]97`| 36
`104[.]18[.]115[.]97`| 30
`95[.]143[.]141[.]50`| 1
`68[.]55[.]59[.]145`| 1
`37[.]57[.]144[.]177`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`icanhazip[.]com`| 66
Files and or directories created| Occurrences
—|—
`%TEMP%murzuja.exe`| 66
#### File Hashes
`02627c827c7ed7cb06e0b8b8579f09d41309a34dedc21f6cbfda0c4ad111e633
02909ed4e0457bf8342cc7f6b5a40da25879b344b1193fa2902a946f35b87edf
036c65acf57caf215ad7f2b61b514588aaf57b834116c9414ccf4be0153d8dd0
04042ea6ec8b598fcb8ead8f8002f64568ead807aecb5801f44cc28a4ce034ff
0a6ffe8c5e7617aa0e44f415937d84008660f31af54d00322791dda2dba6a9be
0a9d65e29aff36bfd2c98bf5c0a8ccf246da39e11c3fc5b1a67c693c735a9f8a
0dbcd3c2f5e21d195f9061c8a8efdba3aa33ebe74dcff73cf5ecdca637b730f7
0e6bdb6f60252434dd2b0136025d7c1f3ef12f078a2223f8a249635cd56adeb3
0eb45a5851243f1f75a3c81ac14f13427dc57d9acf04557f0ef422cb105c4c96
1063a4d37d9f88b22d74bd04c0c6f7935ba89a6d2dbed6cc74b32c4fb8416647
11ab4795253d6c47f03139b8fbd20662798c4826b0499050497083452337918a
19ef0532a84339ab7cefb178631ea3715b27f9cfdf403428f584b5c609f9a21c
1b462cc5e7c02e976468b4385af3aa0fc331b92c5d26866b4d0828b6917778d7
1e69a3611389c0a022da61343c970fc223112e19770fce3eea6f5d6a7688da7a
206c7347eb7b833f93fbd9443946f58f5b186d12199d597b36ae3da0d59fd8d1
2171271cb6b501695f5d4ed386b756929e133b7d7ae4effb81d6297937dfd54e
22c28311a81fc7c7edf453514b2dacfa5740b770a1cb04ec2dcd5c3b142564b0
22df8ec37631f3914b9c533c50ba28ba603c04674300fedf032822830c110e16
248de47e1f95e84826ddd16ba9d75976ac08b2f964925317b9029c3e4f88a9f0
29355acdbb6325357a7e102ef75271e9a4b76584480dbe2684dbb67776beffb6
2a4a2c50d96b49fa61b1cccf3500db4a8e5a9b078bcf1a95a5f932c242fb1198
2a92e428519d5243b702cfbbd3d15470d68cf70b51b46234fb48a6f9c311b367
2aeba5724cde048b812473a94bfe63e6c781e498cf00c7b1c6202c6f3d717de7
2bf2d78f43dddf5b894a588e9a60cead65485dd4fe1934132e56f85bb72df707
2c5fe5a61d53230430f719ed030a92a52b14d62822db8386db1deb8bb9dff3cc`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
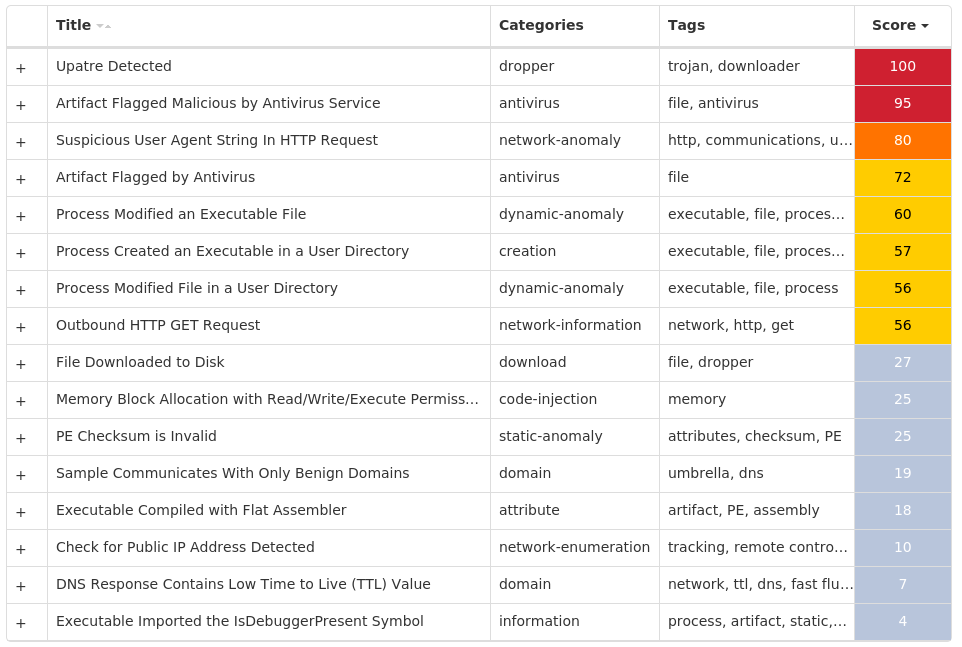
#### MITRE ATT&CK

* * *
### Win.Malware.Diztakun-10013372-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 25 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESSYSTEM
Value Name: DisableTaskMgr`| 25
`SYSTEMCONTROLSET001SERVICESSR
Value Name: Start`| 25
`SYSTEMCONTROLSET001SERVICESWUAUSERV
Value Name: Start`| 25
`SOFTWAREPOLICIESMICROSOFTWINDOWSINSTALLER
Value Name: DisableMSI`| 25
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESEXPLORERRUN`| 25
`SOFTWAREWOW6432NODEMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGONNOTIFY`| 25
`SOFTWAREPOLICIESMICROSOFTWINDOWSINSTALLER`| 25
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUNSERVICES`| 25
`SOFTWAREPOLICIESMICROSOFTWINDOWSFIREWALL`| 25
`SYSTEMCONTROLSET001SERVICESSR`| 25
`SYSTEMCONTROLSET001SERVICESALERTER`| 25
`SYSTEMCONTROLSET001SERVICESALERTER
Value Name: Start`| 25
`SOFTWAREWOW6432NODEMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: DisableCAD`| 25
`SOFTWARECLASSESWINRAR`| 25
`SOFTWARECLASSESWINRARSHELL`| 25
`SOFTWARECLASSESWINRARSHELLOPEN`| 25
`SOFTWAREWOW6432NODEMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: SFCDisable`| 25
`SOFTWAREPOLICIESINTERNET EXPLORER`| 25
`SOFTWAREPOLICIESINTERNET EXPLORERCONTROLPANEL`| 25
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESWINDOWSUPDATE`| 25
`SOFTWARECLASSESFILTER`| 25
`SOFTWAREWOW6432NODEMICROSOFTINTERNET EXPLORERDESKTOP`| 25
`SOFTWAREWOW6432NODEMICROSOFTINTERNET EXPLORERDESKTOPCOMPONENTS`| 25
`SOFTWAREWOW6432NODEMICROSOFTCTFLANGBARADDIN`| 25
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONEXPLORERSHAREDTASKSCHEDULER`| 25
Mutexes| Occurrences
—|—
`GlobalC::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!010a0`| 25
`GlobalC::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!011ba4`| 25
`GlobalC::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!012c2c`| 25
`GlobalC::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!014d3c`| 25
Files and or directories created| Occurrences
—|—
`%SystemRoot%system.ini`| 25
`TEMPautorun.inf`| 25
`config.sys`| 25
`%SystemRoot%winstart.bat`| 25
`autoexec.bat`| 25
`TEMPwinlogon.exe`| 25
`TEMPAGENT.exe`| 25
`TEMPSLEEP_TEST.sys`| 25
`TEMPSPOOKY.sys`| 25
`TEMPVAGRANT.exe`| 25
`TEMPVIRUS.txt`| 25
`TEMPwininit.ini`| 25
`%SystemRoot%dosstart.bat`| 25
`%System16%autoexec.nt`| 25
`%System16%config.nt`| 25
#### File Hashes
`0021a7ecd30ec9e7d784c42ae64271b6048666c0a24505f7b35ef6398c6e67de
009086e24a5a00bddd3eba55592afdacdb8af0348aa92689317b53da6e75fe31
04697012f791c6f216166eb1f51ff28acdbfdc1d48bba4519e5f87fcec3ccc81
057c03cf6a446c6e6cc69410735bc5566aca6b67e6a0e6a047e599733f158aec
0655d055f9828c562a1b8c595da7cdffd364e6cc8f8cb4fb2dace02def3a72a2
06c6175c09dc4990aa5a585910133b1654d5ad9e830e055f0485eedcd9ccbf03
06d5e06ed0350ba3aceed5c8c4dc51a823a96356de2c643c3f82e0168b3c45e3
0942b6c9cae0fde214be04c00f82df9ba16b8807c15e9d77794c1eeaee529ee6
09b3aea967bd842df4122c7fe680177c8f61c1db2d7fab4b718226f3f49e0a88
0bb8cc324149c2667dd7ad9a3b0485ecfe28fc2d987351d3291eb6674d158f06
0c6665ef8f2b001e2b59c003d1b16620f914ef1b2942eb75042246c2a03a2acc
111969b54597e9302f881219a619bc5575860c6c7145cd7420c5d5ed3e7678f1
111a4c38d54f738ec137dbdb05fbca0b836297c1f1bdbe0d14af8c184c1e8285
1236be8ea5e03b19cdd1e426d363f3048ca0a0a2ca95bdb85354463ca2bb12ef
126bcb577c45b6a6d50686d695c7cf499ca56f3565b97a50b75fcfa1cd5436ef
13a8758f0372e94b3150a99d0f9eaba106888969602e97f111d8d9754bba5898
14519a8eea3064280ee285be6d20a9b115235a87911d4acd810a104136d941be
155ee1b57f1b81a893d8b4dc1e4d82bfc41aba7efa230efde3d4d799dd8bab96
165b625e83b0384f62ddce37be56c40f8f9edb963f6db4ce2ecc64eb76e48393
16bd1b3ae60631d1c6a5930370439c450a9dc7caf0bf830639211d639975ec26
16c0c7b6e6442a4c0474ca5d191264a720a21ea403c666bd7250730e6cc743ad
16f83afc6db86047f9e4052d1dbed7bbb863ef9b97b6952992da9dc1b5d3c37c
17154f668675360454fa5d307bdfa6460f2ac7c774934d823011290882f2d783
17853c83a9406c9ac07a189d3b968187f6c784f454da643ff816052e056e44f4
18140ff47b13e4a95522916681d8c47382fd7590730a2d03254119d09042d170`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
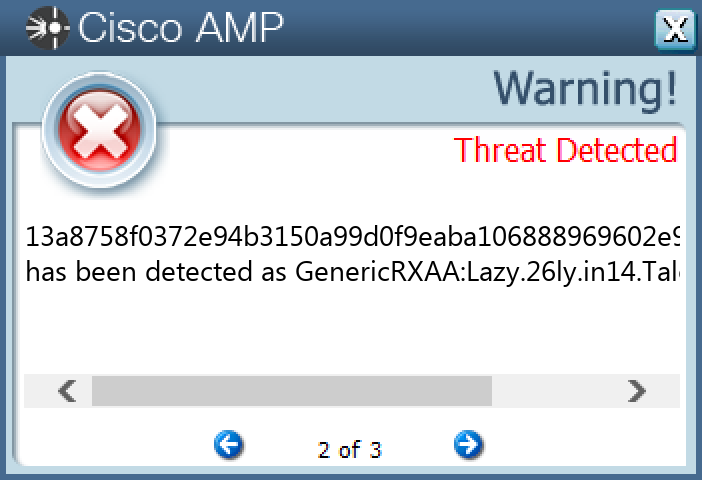
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Doc.Malware.Valyria-10013349-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 13 samples
Registry Keys| Occurrences
—|—
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTRECOVER
Value Name: Name`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTRECOVER
Value Name: Path`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTRECOVER
Value Name: Extensions`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTWRDPRFCTDOS
Value Name: Name`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTWRDPRFCTDOS
Value Name: Path`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTWRDPRFCTDOS
Value Name: Extensions`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTWORDPERFECT6X
Value Name: Name`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTWORDPERFECT6X
Value Name: Path`| 13
`SOFTWAREWOW6432NODEMICROSOFTOFFICE14.0WORDTEXT CONVERTERSIMPORTWORDPERFECT6X
Value Name: Extensions`| 13
Mutexes| Occurrences
—|—
`Local10MU_ACB10_S-1-5-5-0-67863`| 13
`Local10MU_ACBPIDS_S-1-5-5-0-67863`| 13
`LocalWinSpl64To32Mutex_10960_0_3000`| 13
Files and or directories created| Occurrences
—|—
`%LOCALAPPDATA%MicrosoftWindowsTemporary Internet FilesContent.Word~WRD0000.doc`| 13
`%TEMP%.tmp`| 13
`%TEMP%tst69.tmp`| 1
`%TEMP%tstF7.tmp`| 1
#### File Hashes
`000b51af496336d202cf40f4b0afa91ab678962705825d49d53454915b0fd651
1bbf337f74ddfc46c865bc1d0fab402ce75f7687a1081d791f89e3b97633038f
20cb7b1e4c59f6c9308d8a079fbf898b44222ec909ded047696261a849eeb033
28716226e1413862e88614d499c19a2d3b7ac8d3b2e0321a688ddf19af549056
4b4f60d8f108aca734d102581e253f16abed5e506b8cb51801f9b36b5ab0d8c4
776fbfaef493c436c8f7ea4f025e587734f48f67c7d5ad660275f4e40fcc6b47
79ae3f16462f7e32ad2e8a45f79f166a2321c78c16564af8ee36f32cf616ce4e
97f82ae47b756502c4db71811843856efce5c449e0bba48178b9c27d1f98f987
b83f2a183484e660d3b5b4399c7069f62a7b9b22b4461bf2961633c03cd3f944
c89c5bcd3a3a85c6b80005f47998b8cffbf08565c63f5805f3fb187c0b4c2c0b
d21913c6b3fd6e35c7c8346f336cd9b373babbbdbfcdc61e48a9f3360218542f
d665edff65709c124fc043bb61747a3a17e85bf6ed0ba666eca66dd02f5dec40
d74f29c45c88422bd8ec3d11b660677adb0eb8dfafb6dfc1d685ddf2cfe5fa54
`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
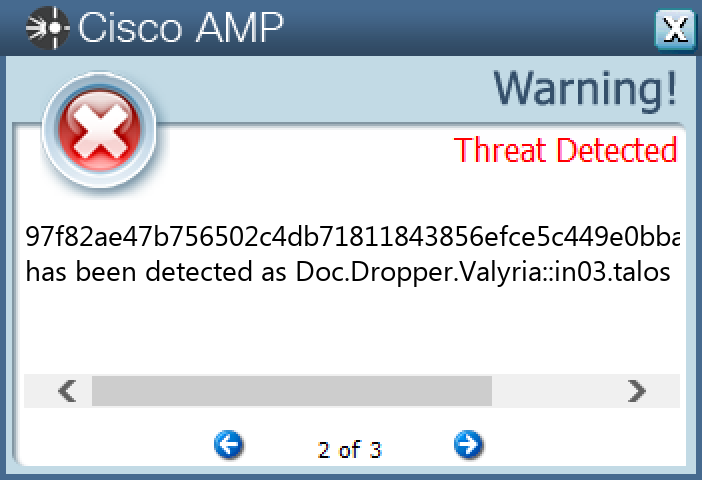
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *Read More

