Today, Talos is publishing a glimpse into the most prevalent threats we’ve observed between December 29 and January 05. As with previous round-ups, this post isn’t meant to be an in-depth analysis. Instead, this post will summarize the threats we’ve observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this round up are:
* **Doc.Downloader.Trickbot-6412300-1**
Office Macro Downloader
This downloader was submitted to ThreatGrid more than 50 times on December 26. This office document downloads a multipayload Trickbot loader. This post-Christmas gift is not something that somebody just back from the holiday wants to open.
* **Doc.Dropper.Agent-6412231-0**
Office Macro Downloader
This is an obfuscated Office Macro downloader that attempts to download a malicious payload executable. The sample was unable to download the next stage so no further analysis is available.
* **Doc.Macro.Necurs-6412436-0**
Downloader
Another wave of OLE based downloaders spiked in prevalence just prior to the new year. The samples use obfuscated VBA macros to download various malware families distributed for the Necurs botnet, including Locky.
* **Ppt.Downloader.CVE_2017_8759-6413368-0**
Office Macro Downloader
These PowerPoint files contain an XML, located in ppt/slides/_rels/slide1.xml.rels, with a malicious SOAP WSDL definition that leverages CVE-2017-8759. If the file is saved as a PPSX, the slideshow will automatically start on opening, triggering the malicious code.
* **Win.Ransomware.PolyRansom-6413978-0**
Ransomware
PolyRansom variants continue to thrive in 2018. PolyRansom is polymorphic ransomware that spreads by infecting other executables. It gains persistence through an installed service, and run keys added to the registry. Its primary infection vectors are share network drives, removable media, and email.
* **Win.Trojan.Generic-6414413-0**
Trojan
This cluster provides generic detection for the Emotet Trojan downloaded onto a targets machine. Emotet is a banking trojan that has remained relevant due to its continual evolution to by pass antivirus products.
* **Win.Trojan.Multi-6413508-0**
Trojan
This trojan will potentially connect to one or more servers to receive instructions and download additional malware.
* * *
## Threats
### Doc.Downloader.Trickbot-6412300-1
#### Indicators of Compromise
**Registry Keys**
* N/A
**Mutexes**
* 316D1C7871E00
* Global552FFA80-3393-423d-8671-7BA046BB5906
* BaseNamedObjectsC1A8DFE67F9832960
**IP Addresses**
* 89[.]161[.]153[.]74
**Domain Names**
* jas-pol[.]com[.]pl
**Files and or directories created**
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsTempInue8.bat
* %AppData%localserviceWn-lbzpms.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsTempmo-r.exe
* %AppData%localservicemo-r.exe
* %TEMP%Ecmjtqf.bat
* %AppData%localserviceModulesinjectDll64_configssinj
* %AppData%localserviceModulesinjectDll64_configsdinj
* %TEMP%Wn-lbzpms.exe
**File Hashes**
* 3e5a5c672052182d9d10b0d094f07ec67f182939556c90f66236d75d4e795cd6
* 07a1d83e2fdce0b0383fc05e2931d3aa557e3eeeeca50762258431ecf6fc2c50
#### Coverage
[]()
#### Screenshots of Detection
**AMP**
[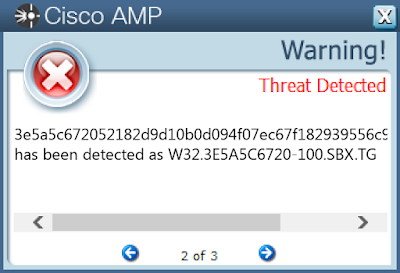]()
**ThreatGrid**
[]()
**Umbrella**
[]()
**Screenshot**
[]()
* * *
### Doc.Dropper.Agent-6412231-0
#### Indicators of Compromise
**Registry Keys**
* N/A
**Mutexes**
* N/A
**IP Addresses**
* N/A
**Domain Names**
* weekendfakc[.]top
**Files and or directories created**
* N/A
**File Hashes**
* 024782b5d080879af2a7a4280d262929e85e9815b2b37e9aeb6384a26e97895e
* 0ad1db5a012d54fe11b06cf8b8822135e5285e21ab99e7ae5c8ca1892836375b
* 1283fc95f56f1f32dcfeb5ec042a53f6e0dbd05d49c5bbc892e389cfc5613d9a
* 1a5257c6cd2e03848758d9541cbf4918194ff33669029a06baee9317d1a9a527
* 211e5c8d07af1e6b61acb7af8bb1e0fefe25bee88275f2db8d53f868dc991e0e
* 23c8026cd6414fa083f83c856c9142af5905747eabb32d0d0d839e21f941bf3e
* 25191548ef2032df4acb687d940854f134de3aa738b69fc578e5397e95496afd
* 28f9a67de7f6b79b4bf66da9d114c723e16d619f6787257eff856c71b1c7047f
* 29062cd2c2d09199fc0716485e0e3a1fff880195a92c78ecd5f0e5184ac07820
* 2b24aa417d6ab02fa9f82be1a41bc8c2e5de814057ed76074e2960d74f31d2d1
#### Coverage
[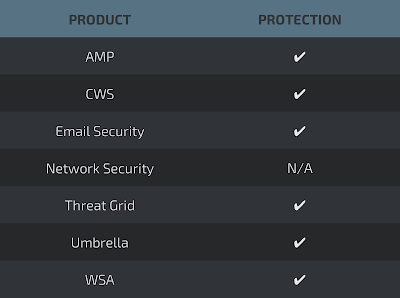]()
#### Screenshots of Detection
**AMP**
[]()
**ThreatGrid**
[]()
**Umbrella**
[]()
* * *
### Doc.Macro.Necurs-6412436-0
#### Indicators of Compromise
**Registry Keys**
* **<HKCU>SoftwareMicrosoftWindowsCurrentVersionRunOnce**
**Mutexes**
* Groove:PathMutex:tzanqCjN6dCs1QGzbKslin0UfIk=
**IP Addresses**
* 98[.]124[.]252[.]145
**Domain Names**
* pragmaticinquiry[.]org
**Files and or directories created**
* %TEMP%ASPNETSetup_00001.log..doc
* UsersAdministratorAppDataLocalAdobeAcrobat9.0Updaterupdater.log..doc
* UsersAdministratorRead___ME.html
* %TEMP%ASPNETSetup.log..doc
* UsersAdministratorAppDataLocalAdobeAcrobat9.0UpdaterRead___ME.html
**File Hashes**
* a3f68a31db23b9c7312219990bfe27bf9bb7c158fde4200c0af7a985bd7ac97d
* d4a8da30821df543407bcbbc25bf2a89db3d3f5c8d49fddeddaecd3b47c111ef
* a9db16baffc0b92aacae6647952fc2d32673998fc035493d50d32bad5bceb516
* f07f747978b7d8bed904ccadbcc49f184bc16e872f22d7b53b1030bc22ebd794
* 9b48b6bc6ee491a2b180d6b353ae8f8da230f27a0cdfc1757c58a4819664b790
* 0c51e3df0b09f14e04b268102afc9342c35fcc2460c645f9c8d21b2413910d32
* 0cfdad54484cf1d4ff9be267469edefdb98e963ffabd6beeb081a208e3fca9ac
* 1c2f0a28b5c13eb2967078d947924c9a4a5f8f845d3899986df19e8a166d3ec0
* 241f83caf5c5a23a1d7adbeaa8c392da0edadff362f41bbb5727dc71887048c4
* 305790984d5ffa713794c1732eea4f83f18da6926e415a490b2fc090f2c4e8dc
* 305f855ff8d47be5cc2d57e137a436bb2e17b1783f6cc5b8302c2df56b75afd7
* 32d85f3dded85d0375965a50991ddb7b608166f51a12b297ae981348119512da
* 36fc2029280816810324e3be9cf3a4257f0dbb1a8b11eaffdbacdead863aaf44
* 3abdf9d8249e3cc7507529aec80d93551f1fcd714a61861a69c059662aa39e9f
* 495b93c1a9940e94c14063b1e52877864d54fb544a3a32e923b0530cb03c96cf
* 4c04d8aeebdd0eb1747a9a66b10e4681328a03edcbcbd0e9921c4a74367bbd08
* 580b05987531aa4ef4bed150bd51fdbbcad5f95abb63e8439e3d4bb07eb68598
* 5c4d5f6d7d0a8d4e805c1341cadf76a924aa2fe6437d432d96f103c4319e84c2
* 6e35534f8b79187dbe2fbdd1b0a21b03752a89df5981cb6fb89154eb7b34a087
* 8f36a3ebcb2714d7f6d99d8d0672bcdf16980da788331953cba52c21fde64efb
* 962beb562acef288c5ef09f14e366d7ff3f51a00dd28b3dc5c0e388c92d3c0a2
* c2f482372523031b880b7a4f1909b30b5aa20304d0a691309484ad49a0c451d5
* cab8fcbe8bce311464418e2fcd05e55353255c511e698726e009f075de82e2ea
* ce5d33fb70fc7834d8faa7749d5cedbcb6b0958105ebe94633e2daba897612ef
* d18256e9f4062259e941028c531c5219b63446a35c524ef00554c69de2110e98
#### Coverage
[]()
#### Screenshots of Detection
**AMP**
[]()
**ThreatGrid**
[]()
**Umbrella**
[]()
**Screenshot**
[]()
* * *
### Ppt.Downloader.CVE_2017_8759-6413368-0
#### Indicators of Compromise
**Registry Keys**
* **<HKLM>SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **VRGTQ
**Mutexes**
* N/A
**IP Addresses**
* N/A
**Domain Names**
* u[.]teknik[.]io
* kistags[.]com
* graceland2017[.]com
* 0i3tenrainy[.]loan
* goochandhousego[.]pro
* dayi-yc[.]com
**Files and or directories created**
* %ProgramFiles%Rfjdconfighbch.exe
* %TEMP%dsruxkfs.0.cs
* %TEMP%dsruxkfs.cmdline
* %TEMP%dsruxkfs.err
* %TEMP%i02bp4bi.0.cs
* %TEMP%i02bp4bi.cmdline
* %TEMP%i02bp4bi.dll
* %TEMP%i02bp4bi.err
* %TEMP%tmp95D4.exe
* %TEMP%tmp970E.exe
* %AppData%Roaming982PQQP9982logrc.ini
* %TEMP%dsruxkfs.out
* %TEMP%svchost.exe
* %AppData%Roaming982PQQP9982logim.jpeg
* %AppData%Roaming982PQQP9982logrv.ini
* %AppData%Roamingtmp.exe
* %SystemRoot%SysWOW64comSOAPAssemblyhttp100u4teknik4io0HUKzO4png.dll
* %SystemRoot%SysWOW64comSOAPAssemblyhttp100u4teknik4io0HUKzO4png.pdb
**File Hashes**
* 22ae9fc528b63ecfe163c2b4c472e68869e049023be009ef118c59346247082d
* 129bddde9c3cb01c69d92d9029d5da963a0dd5a72143054f9fa97471a388e9c0
* 2d92ee55d56e96822aca748c7d69344d90a663e0db77e7ddd0ce9befa54aba98
* 3894ba1250493f0798f9212fc20e96e8114dcc218850fef13979410dc63affba
* 3a26d63160a43b64ee4f4adba0a5c19cb3ee6db2dc44c0ffb7b72b621548c4f8
* 4b4efd1527b404064604707dbf7a143745d764629d6cfcc05a6c204b66238db8
* 56b951fe25e1d0266dd49eba6b127efe63c49d71063533cee2ba3bb7eac08744
* 56ede7ef1d1e5216231c847eead200bc8b5c5f8ef7ac8389b7dc5f069b37831d
* 650abb87b45b41a344c677c0d6bb6a13cbe9a66785b87a0f2ff3fb378220448c
* 72399fbb24239a2e1897132ad0e3270103c727253275009e010c74a94f36700d
* 7b58861aab0a53cac5ac90af09723703fb47fda584fc66212ff663c52a8150a4
* 7ed5fec1aabe2e91524a9a84d2c4f4d29a8da5777289023c40ffbcc7810b2ee8
* 84593a125442a9541b2992a2934f4db5cbe1a87b6e5f5edd17982e677667c53f
* 9f9217702cc1d59edc29007f745eeec78118941f3d4f99b2f664a9677867ffb6
* b28a3bd9be8ec8d9dec980896002d84e2544acb2625e1acbbe8351d57b2b6cfc
* c0ed86aab56032d1ba313aa6b5eaabcd687caa28937f56f23832206f81ec1271
* c5b450ac63234f3d23ace0379486a33788187f14b47801971ad96ace76f85410
#### Coverage
[]()
#### Screenshots of Detection
**AMP**
[]()
**ThreatGrid**
[]()
**Umbrella**
[]()
* * *
### Win.Ransomware.PolyRansom-6413978-0
#### Indicators of Compromise
**Registry Keys**
* **<HKLM>SYSTEMCONTROLSET001SERVICESZSCGIYAL**
* **Value: **Type
* **<HKLM>SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **FacAQkYU.exe
* **<HKLM>SYSTEMCONTROLSET001SERVICESZSCGIYAL**
* **Value: **Start
* **<HKLM>SYSTEMCONTROLSET001SERVICESzscgIYAL**
**Mutexes**
* BaseNamedObjectsmMkUAokE
* Ãë@
* MkUUAgkc1
* ºë@
* poAUcoMg1
* BaseNamedObjectslEwoEIAg
* BaseNamedObjectssgwQgcAM0
* ²ë@
* fusUgwwA
* oskQowMk
* ¢ë@
* BaseNamedObjectshYsQEUYI0
* BaseNamedObjects @
* ªë@
**IP Addresses**
* N/A
**Domain Names**
* N/A
**Files and or directories created**
* %SystemDrive%Documents and SettingsAll UsersLgwg.txt
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1TempnOowsYQI.bat
**File Hashes**
* cd32c7982ceca8711ec2f6c7ad83103db41b5d2c644b9beee07c81f92efa30a5
* 1ff90f71632162646145cd91a22fdb24683cb25e54254f9c311d54cbc633fb92
* 377a4c54239536019cef4c3fb2ed835a0142f58d64bc0bf49063440b7700a0b7
* aff6517827847137411d37bafc0aee2915e87b9d2494493c1723634ba1014792
* 38c7c22fd8526dd108422befd6fd38212ef45fb30db3272d5016fa942cd2323d
* 3ab0d96b041b994d6f32a4351120b822d39b681d2c5133f12bb507fe2fb66e19
* ca8eb5e89426e3c6771a72cffac6998abce9ca2a6011207691e47df1738cdeb6
* 8957b057803dd6369f877c359b96423b61129fa3f68257c272644e1d56c7c667
* c4471377f58643e454ef33f21dc65f696567bf8700ae120caac5086f85bfeace
* 64fac9307649854e520f733df3df40ed960650103a78b8460488319156e059cf
* 1dd699b7fdb082c35677938f6f064e02e226033f995189889799adac08811a18
* 9ca5fd8ee403b418f92118836171b72a334caeb94fae9b5b46d6246742bf1345
* 78286db82473a9f1eddba51f39333a77c2b30fb582e9fe3e71d2924e060eb273
* 7e888fabc1451dce556864690cc55e70c8236db2a7b01b8726af0a5700ebafea
* 6f15dc426b87da591d0a2d4965558a22857e2b1c8e1e6fdfe9c36c8a4b50a99c
#### Coverage
[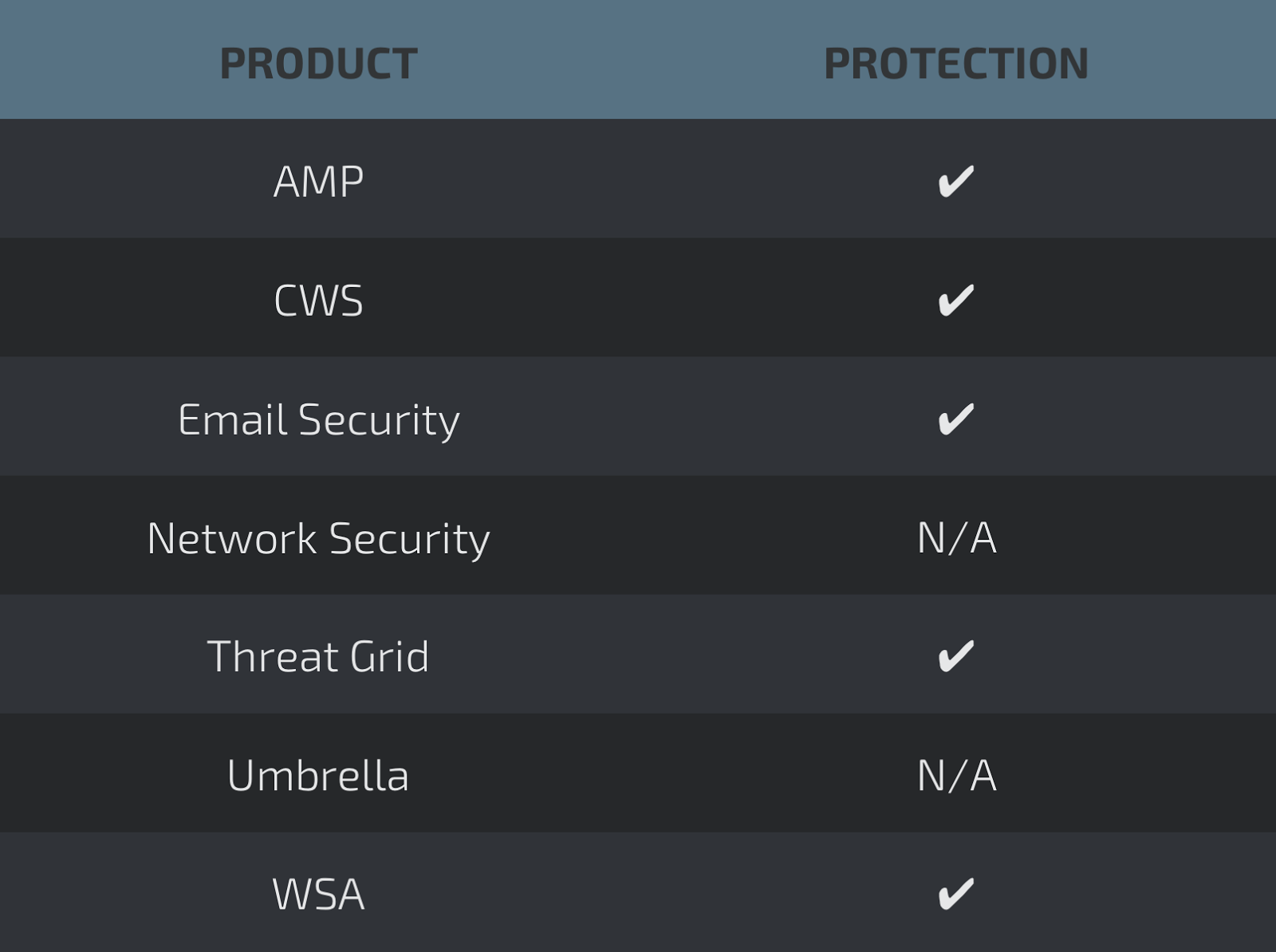]()
#### Screenshots of Detection
**AMP**
[]()
**ThreatGrid**
[]()
**Screenshot**
[]()
* * *
### Win.Trojan.Generic-6414413-0
#### Indicators of Compromise
**Registry Keys**
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **internat.exe
* **<HKLM>SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **Microsoft Windows Manager
* **<HKLM>SYSTEMCONTROLSET001SERVICESWINDEFEND**
* **Value: **Start
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **Microsoft Windows Manager
* **<HKU>SoftwareMicrosoftWindowsShellNoRoamMUICache**
* **<HKU>SoftwareMicrosoftWindowsCurrentVersionRun**
* **<HKLM>SYSTEMControlSet001ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList**
* **<HKLM>SOFTWAREMicrosoftWindowsCurrentVersionRun**
**Mutexes**
* BaseNamedObjectsb11
* b11
**IP Addresses**
* 220[.]181[.]87[.]80
* 69[.]49[.]96[.]16
**Domain Names**
* www[.]murphysisters[.]org
**Files and or directories created**
* DAV RPC SERVICE
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsTemporary Internet FilesContent.IE5H3T7LZRLm[1].exe
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1Tempcymycvgmtt.exe
* ;Z:000000000000d46c192.168.0.1vm9-116\_DeviceConfigManager.exe
* %AppData%winmgr.txt
* ;Z:000000000000d46c192.168.0.1vm9-116autorun.inf
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1Tempftoidjlwgv.exe
* ;Z:000000000000d46c192.168.0.1vm9-116DeviceConfigManager.bat
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsTemporary Internet FilesContent.IE5H3T7LZRLb11[1].exe
* %WinDir%M-5050572947025827857375865240winmgr.exe
* %TEMP%phqghumeay
* ;Z:000000000000d46c192.168.0.1vm9-116\.lnk
* %TEMP%rgjqmvnkyr
* %TEMP%edakubnfgu
* ;Z:000000000000d46c192.168.0.1vm9-116DeviceConfigManager.vbs
* %TEMP%gwhroqkhwu
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1Temprdwpamlgaz.bat
**File Hashes**
* 22bcff79015a6f2d450ff4713bc1a195f6333444e96e616fb070ccf885f790ad
* c06da956f726a78aff82e8c2ec2ed7989f227ac560511512fd609574685f6c4f
* e474e51a6f29b9e32702445797ef4baaa96b1e30fa3f212ae2953bbb843a559b
* c9329790645ae7404cd3c746b9a26bcd667b6c1c45f727e504d0833d04726488
* b95a5e8f1dc23677e9e700b44d014aeee127869e46af6a674f93d34da3c606d0
* f3ee9f0be76f80faaa683ef580e3f018e1e0108e5b4457bad379e99dda2c627f
* b010ae9122a8651be194c5bc3d49540d51287040f1a1f066e193835f942277a9
* d775f05eb68ce4ef44776de0ad2b3c6181ad6a99813612a1ce3cc8b453359482
* a3940c00bd3e8d07eb70cd23148d030a473f134a7aa19ff6b777862af6d5f8e3
* 2104784585c92828df37feab86fcabddf3ffdb2718dfc3718ae529ad9c4956e0
* 43d2b149b3e4fd33b03321d2bfb6980734d3725483fee21cd996f280618865d9
* 9e7ae2436474bbad1e9ce20f8fc7a294586fde89c39b3bd2e2fd257d269ca636
* 10c96fcbeee7e93309abc9616958ef214953f512f236ddff2db39f12a8f4a817
* 08c9fedfcf1100f8450ad930a55a2cbf7dcc0fa88b646da2c5916ff42565c575
* 113e003896939e85f048e528b6f50fa9e984009fe2677143c7cfaad9ee693293
* 0d136160f510d87af7edeeb1533979a5cdc1d1511528798d5871bbb88bb1f0f4
* 33fd94f82800a1f8551e73aebbbac4169c3c08cbe12c69e9fab52875d56c96bc
* 1b6651d1e43c7ff8dd291d178b8bad9fbfd1bb426d49da419ee7e4a4d7912ba1
* 1cfd3043ecc8fd7c254201fcafe6865dfdb1c0d6ccc343d0e62e1cab261fefa3
* 201c0ca83973186aab93376147f1b60d009ef13ec827d0de5d19b483d3c0f353
* 23db71997ed2f558e06232f600d3cc7b4e5eb58f18039923127c5b4fa7fec2f9
* 26f1a92cb36e4caff3fccc45fba269647410fbee71cc4f4a00e5d4c282ba01f8
* 2ab47d6d82225c62487054db91e804418060b3334531e09d96dc6d3630fa54b3
* 34ae5c841f6e992fe09979fff521d2e8367385260cf73112e79ce656e952bbb5
* 564ace4ef8e2c3aab367969748e02a0dee555733e9085fcc0a86b9f1b70fb7b3
#### Coverage
[]()
#### Screenshots of Detection
**AMP**
[]()
**ThreatGrid**
[]()
**Umbrella**
[]()
* * *
### Win.Trojan.Multi-6413508-0
#### Indicators of Compromise
**Registry Keys**
* **<HKU>\.DEFAULTSOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **Logman
* **<HKCU>SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONWINDOWS**
* **Value: **load
* **<HKCU>SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONWINDOWS**
* **Value: **run
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONINTERNET SETTINGS**
* **Value: **ProxyServer
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **internat.exe
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONINTERNET SETTINGS**
* **Value: **AutoDetect
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONINTERNET SETTINGS**
* **Value: **ProxyOverride
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONINTERNET SETTINGSCONNECTIONS**
* **Value: **DefaultConnectionSettings
* **<HKLM>SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **Session Manager
* **<HKLM>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESEXPLORERRUN**
* **Value: **lsm service
* **<HKCU>SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN**
* **Value: **ClipSrv
* **<HKLM>SOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionPoliciesExplorerRun**
* **<HKCU>SOFTWAREMicrosoftWindowsCurrentVersionPoliciesExplorerRun**
* **<HKU>\.DEFAULTSOFTWAREMICROSOFTWINDOWSCurrentVersion**
* **<HKCU>SoftwareMicrosoftWindowsCurrentVersionInternet SettingsZoneMap**
* **<HKCU>SOFTWAREMicrosoftWindowsCurrentVersionInternet Settings**
* **<HKU>\.DEFAULTSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorerRun**
**Mutexes**
* N/A
**IP Addresses**
* N/A
**Domain Names**
* www[.]wholists[.]org
**Files and or directories created**
* %System16%lsm.exe
* %AppData%clipsrv.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication DataMicrosoftWindowslsm.exe (copy)
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1APPLIC~1MICROS~1Windowsdllhost.exe (copy)
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication Dataspoolsv.exe
* %SystemDrive%Documents and SettingsAll UsersMicrosoftRCX2.tmp
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication DataRCX8.tmp
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication Dataspoolsv.exe (copy)
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1APPLIC~1MICROS~1WindowsRCX6.tmp
* %AppData%ieudinit.exe
* %SystemDrive%DOCUME~1ALLUSE~1clipsrv.exe
* TEMPd0a08beb99882af4b1771426905ee556.exe
* %SystemDrive%DOCUME~1ADMINI~1LOCALS~1APPLIC~1MICROS~1Windowsdllhost.exe
* UsersAdministratorAppDataLocalMicrosoftdllhst3g.exe
* %System16%smss.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication DataMicrosoftWindowsRCX4.tmp
* %WinDir%SysWOW64driversieudinit.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication DataMicrosoftWindowslsm.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication Datadllhst3g.exe
* %SystemDrive%Documents and SettingsAll UsersMicrosoftmstinit.exe (copy)
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication DataMicrosoftesentutl.exe
* %SystemDrive%DOCUME~1ALLUSE~1clipsrv.exe (copy)
* %SystemDrive%Documents and SettingsAll UsersMicrosoftmstinit.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication Datadllhst3g.exe (copy)
* %WinDir%spoolsv.exe (copy)
* UsersAdministratorAppDataLocalMicrosoftrsvp.exe
* %WinDir%logman.exe
* %WinDir%spoolsv.exe
* %SystemDrive%Documents and SettingsAdministratorLocal SettingsApplication DataMicrosoftesentutl.exe (copy)
**File Hashes**
* ec3075ac9775e3c41bc8227a00ef76905bbd96a62b813c99f277865ff353c5ce
* f4b6b76dec96cc9d530dd6cb64bdd743a115a12a7b03e41f7ec737e4d80b6850
* b1da876da56ba09770d594765727d167bf1a655247f094360e032a35d3d41461
* b82ebd17236c41d9e457f640a2871695326ef8014ebd71b7a5f37d8b2c3a4522
* b3f5ad44f682104d536c60832d2064f71d3261ffbf0e1555c236a36b505619d3
* a27376262110767a28e376b723caa46d3cc50d33da60029df8e7af024ff67be9
* f1b2bbf13bde9ce65cbe1cee7e3d86a61e0511f206ae74589329dc1fffc5f7e0
* 17023d977e2b041c8a1994e7ae69b65e10f7097febefc9b47817dd9f7985cd52
* e5c95545895dc13626b3f20b47fe2f0f1b5dc3915fef44c3c7a5352e95beb382
* 6d1b40fbdcad0c96c687f661469e39b7b10a0b083a9ea3c9f6bb959c284df149
* 7d1ae051d633a3ed3c0991aaa3ed63357804a80e67dd19ae5deab71e525947a6
* 799e5b77de09f7971f0187b69266e45f70e0cda170c615c604806ec2444ab89a
* 910b590e28bc72bc14c05d47a026ed56928ea8b6608f626555d955beccb719c8
* 7d326add0d36be4543317c4d14823e2cb380f7b07bacc1f893ec86bdd0b04468
* 5af23d9dedc83e1fe8c808fe62d858767dd95f2b9402fa785072cc7247a2e4c6
* bf828a8f3fb1a27532aa9f3fb0383a1ce3418f7dd52cefa4264ab2e3e941e8d9
#### Coverage
[]()
#### Screenshots of Detection
**AMP**
[]()
**ThreatGrid**
[]()
[]()
Read More

