
Today, Talos is publishing a glimpse into the most prevalent threats we’ve observed between Jan. 20 and Jan. 27. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, this post will summarize the threats we’ve observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, [Snort.org](), or [ClamAV.net]().
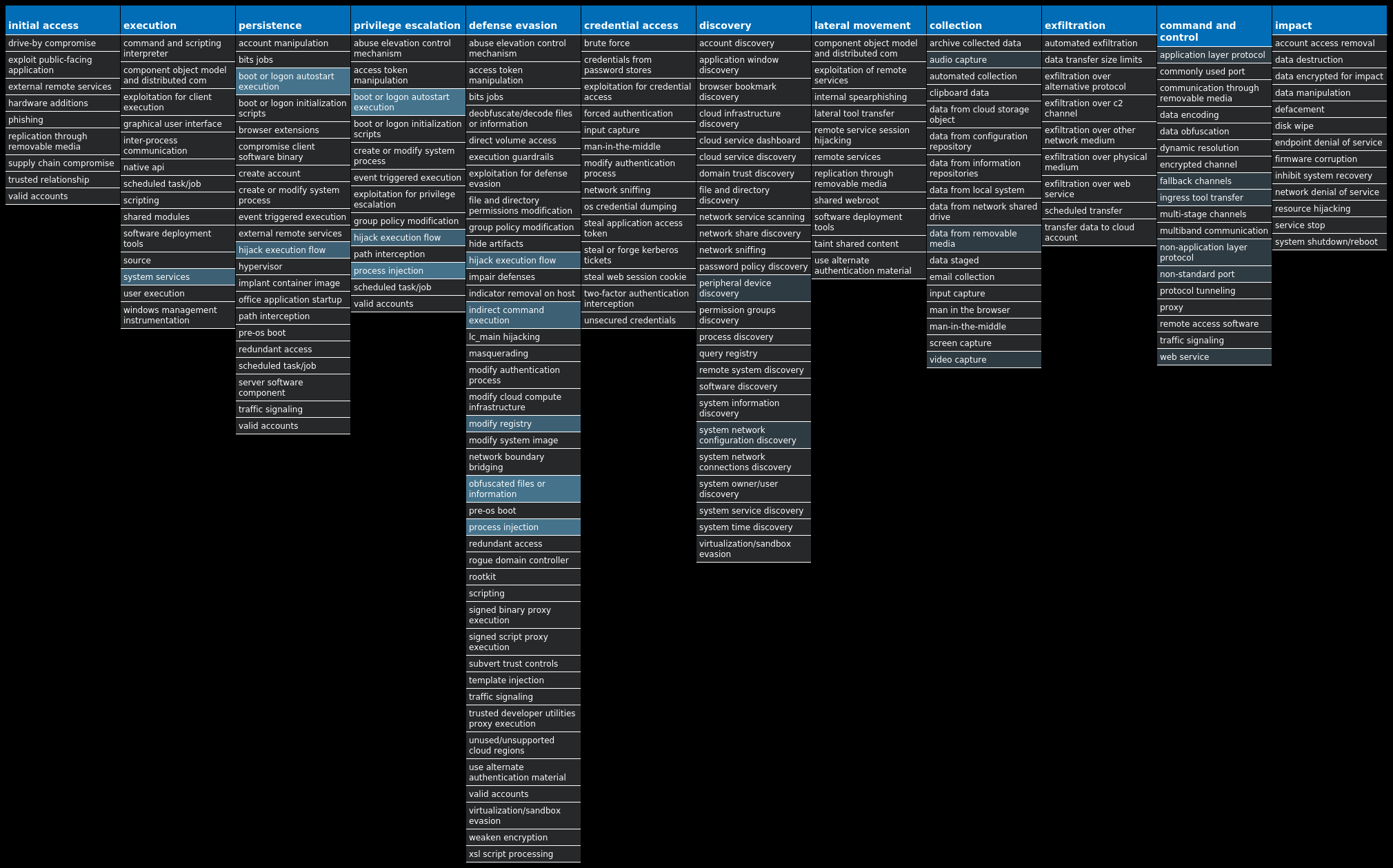
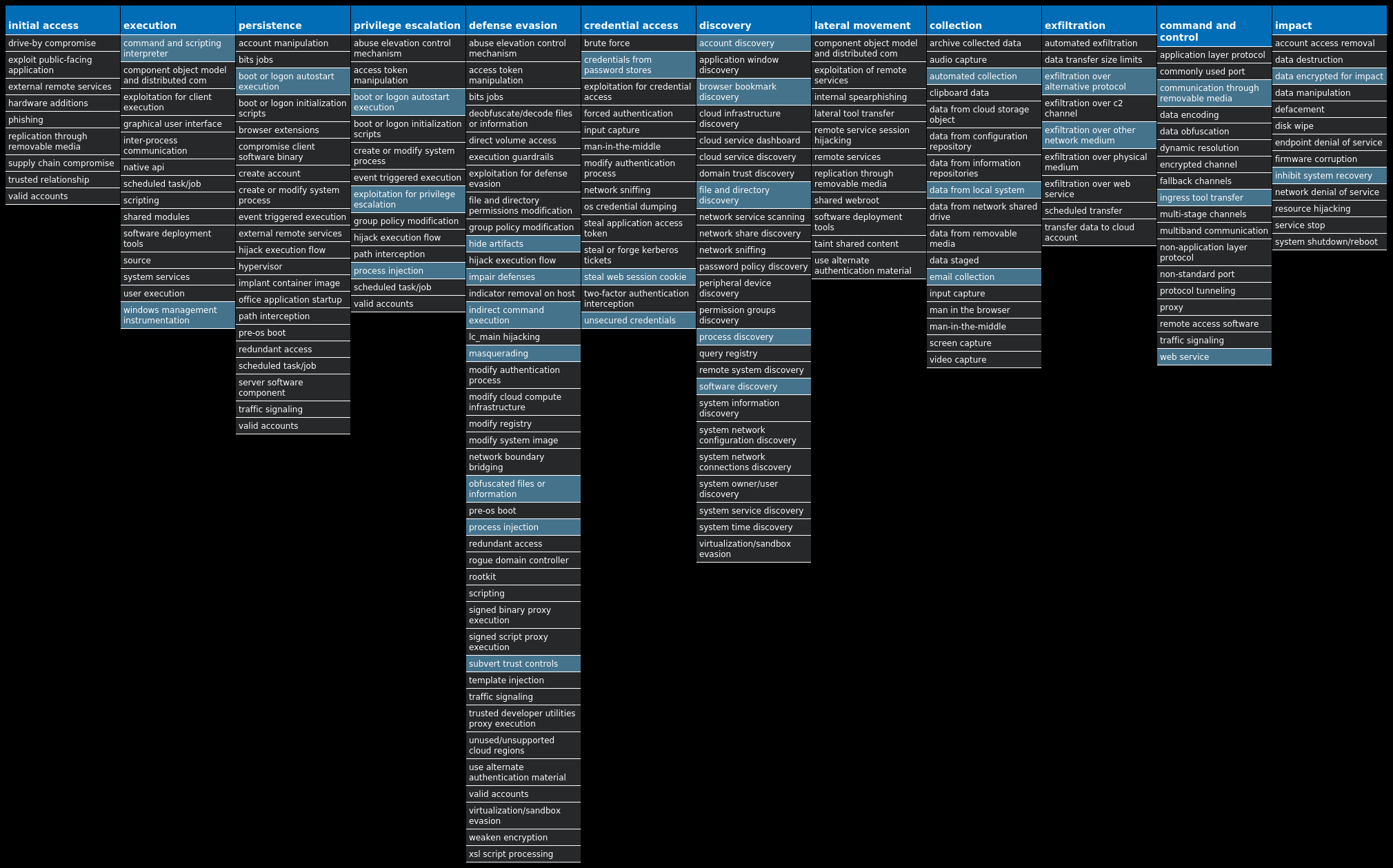
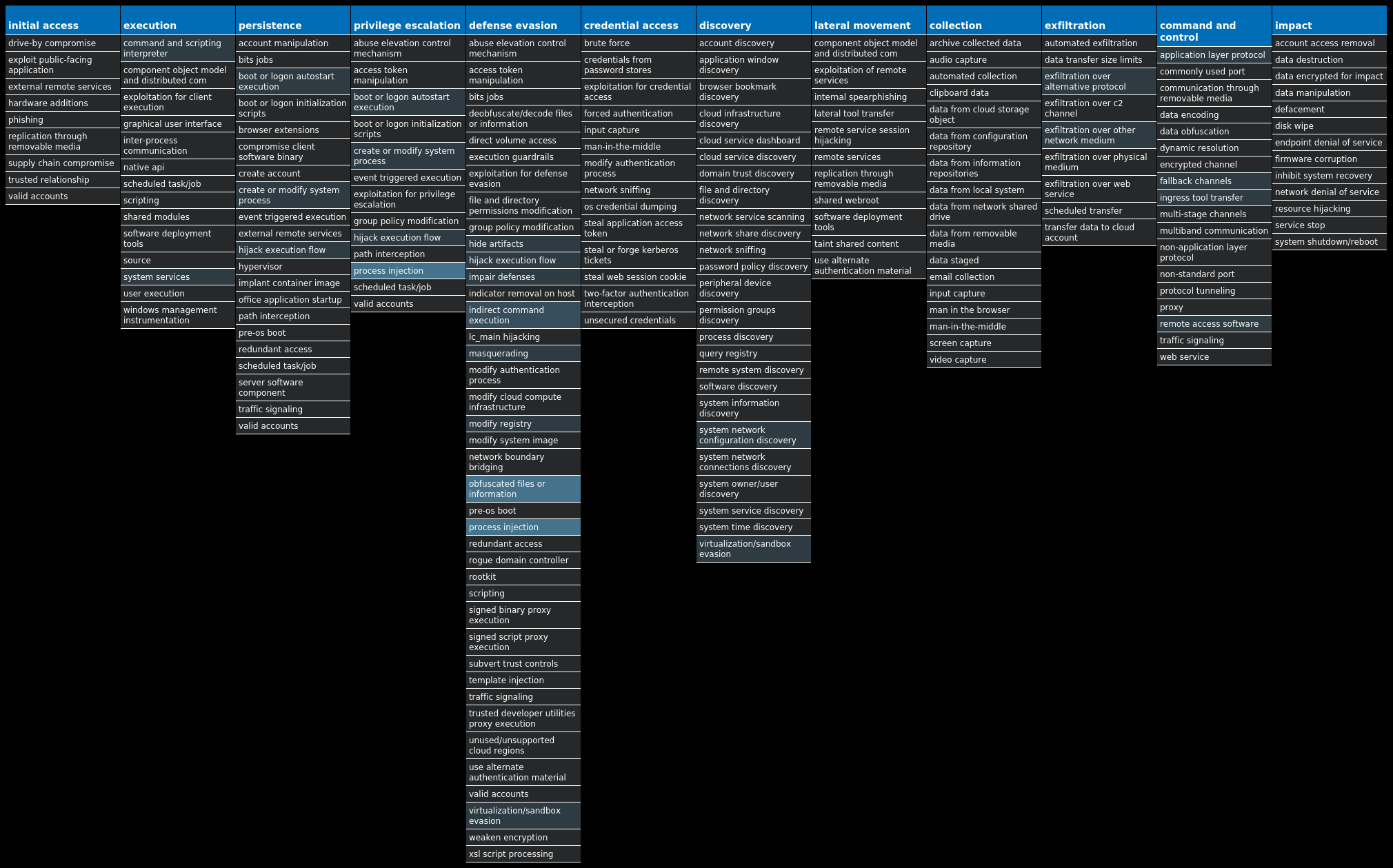
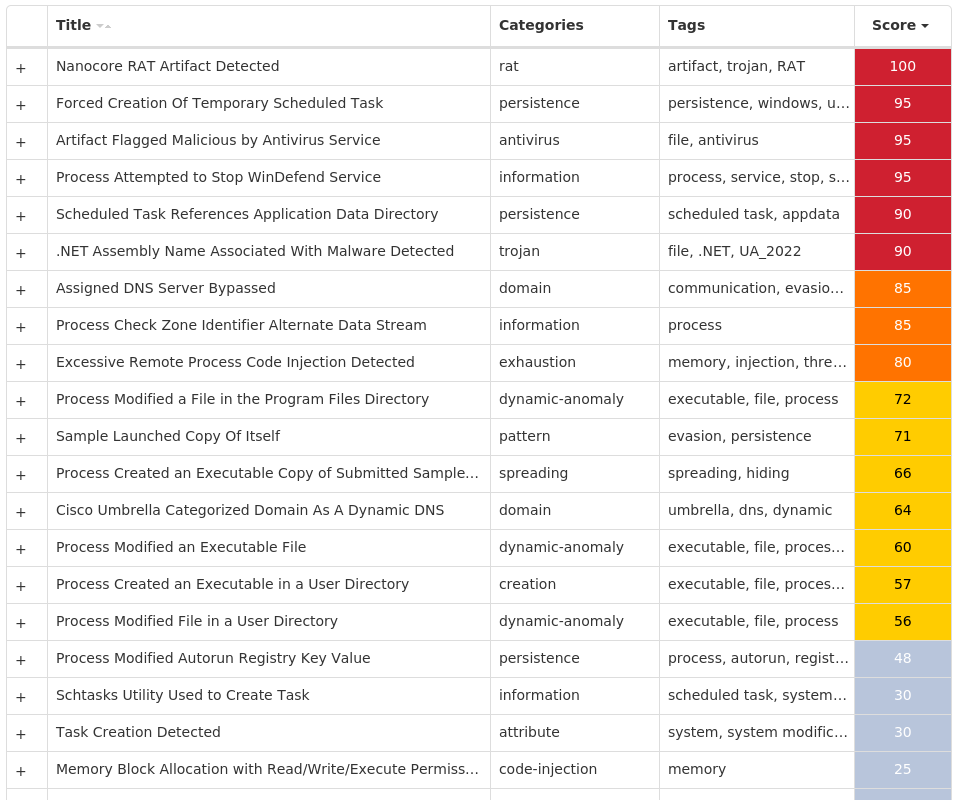
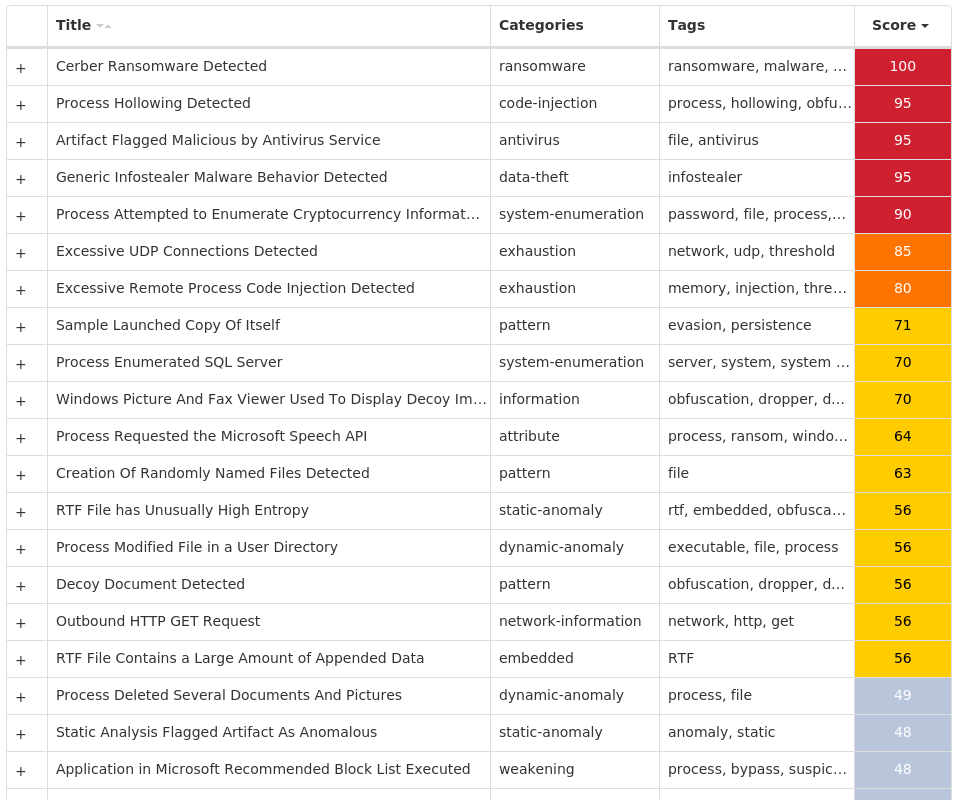
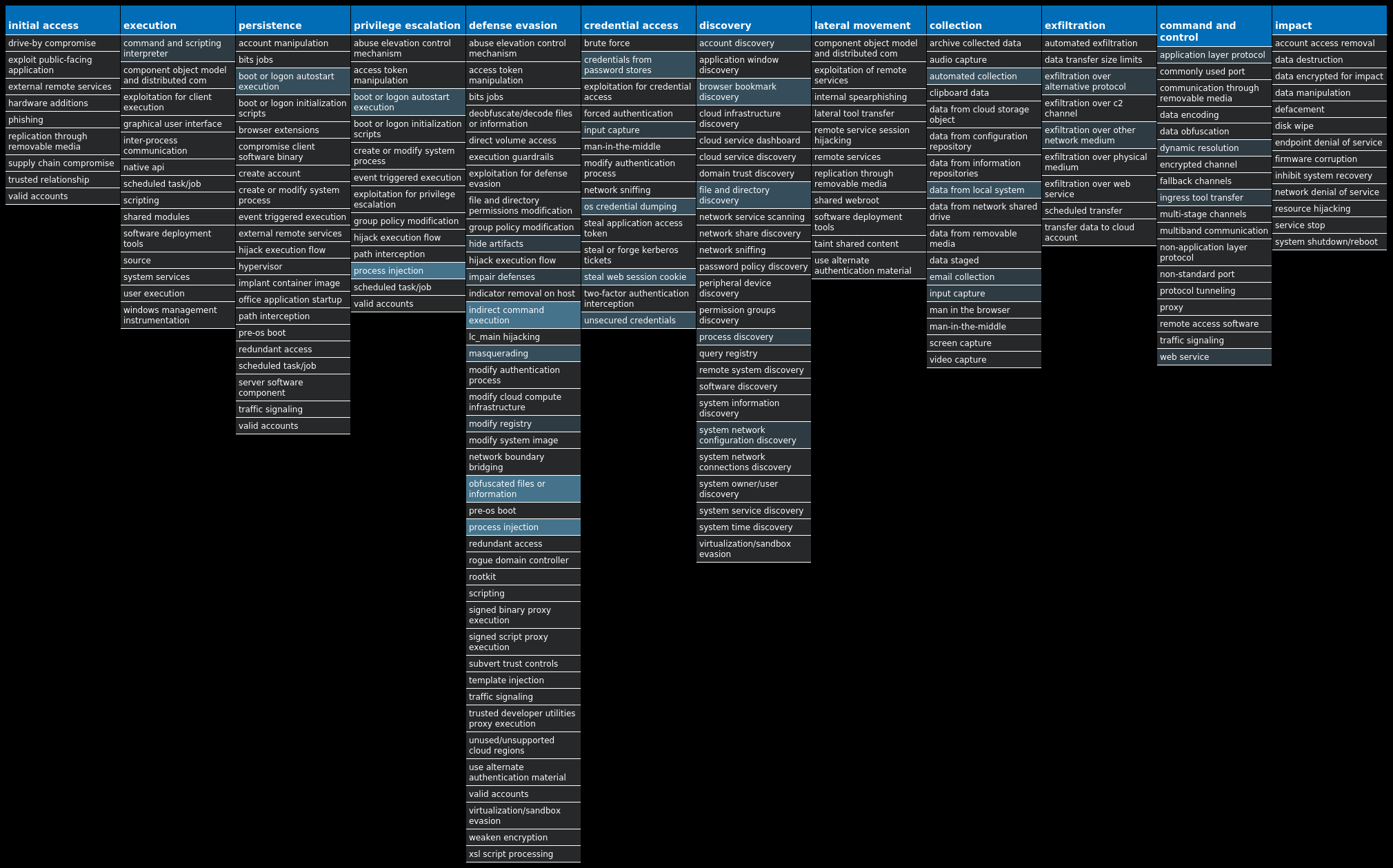
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found [here]() that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name| Type| Description
—|—|—
Win.Dropper.HawkEye-9984948-0| Dropper| HawkEye is an information stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media.
Win.Dropper.Zegost-9984959-1| Dropper| Zegost is a remote access trojan designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. Zegost appears to be derived from Gh0stRAT, which is a well-known remote access trojan that had its source code leaked, thus significantly lowering the barrier to entry for actors looking to modify and reuse the code in new attacks.
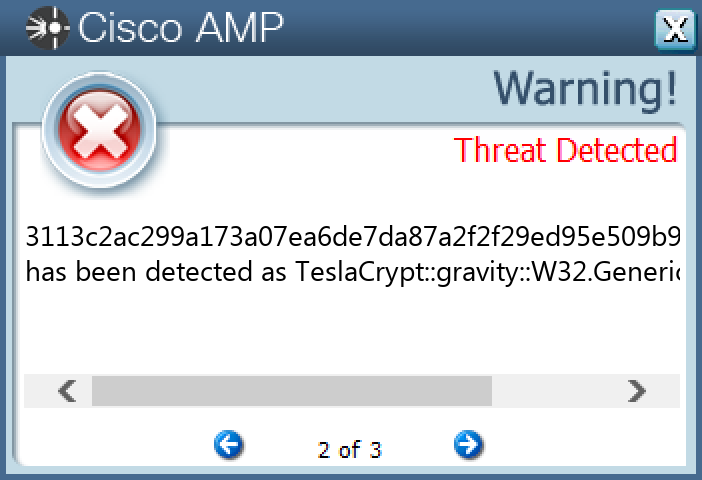
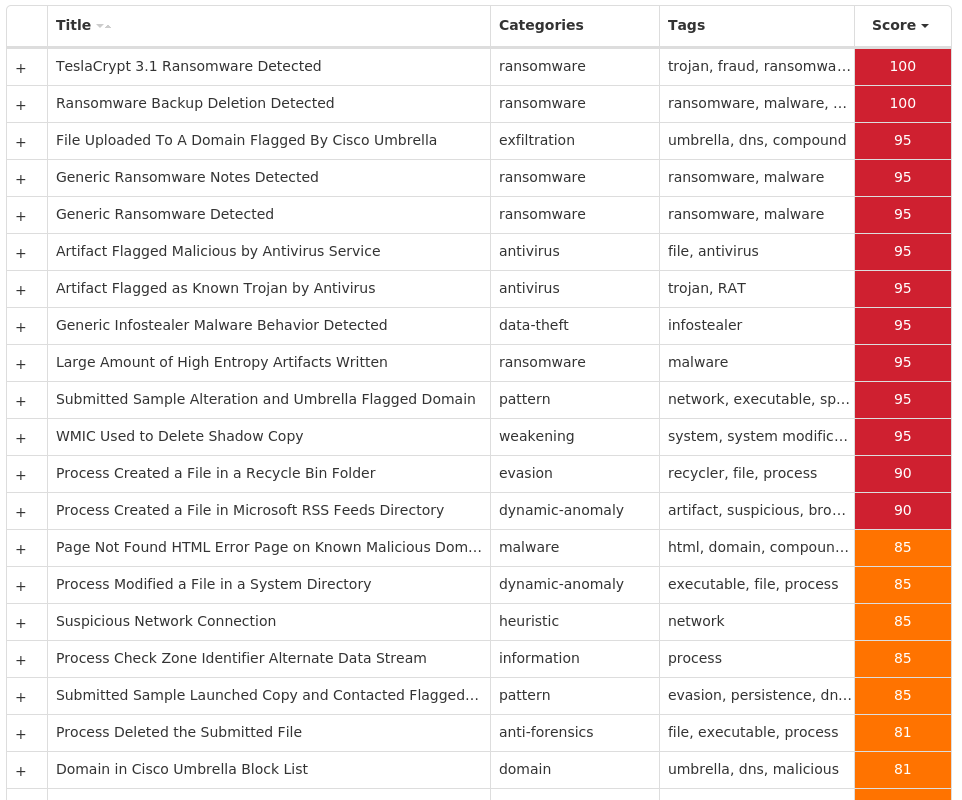
Win.Ransomware.TeslaCrypt-9985040-0| Ransomware| TeslaCrypt is a well-known ransomware family that encrypts a user’s files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the extortion request, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily.
Win.Ransomware.Tofsee-9985077-0| Ransomware| Tofsee is multi-purpose malware that features several modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator’s control.
Win.Dropper.Zeus-9985129-0| Dropper| Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing.
Win.Dropper.LokiBot-9985173-0| Dropper| Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails.
Win.Dropper.Nanocore-9985222-0| Dropper| Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes.
Win.Ransomware.Cerber-9985289-0| Ransomware| Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension “.cerber,” although in more recent campaigns, other file extensions are used.
Win.Dropper.Bifrost-9985293-0| Dropper| Bifrost is a backdoor with more than 10 variants. Bifrost uses the typical server, server builder, and client backdoor program configuration to allow a remote attacker to execute arbitrary code on the compromised machine. Bifrost contains standard RAT features including a file manager, screen capture utility, keylogging, video recording, microphone and camera monitoring, and a process manager. Bifrost uses a mutex that may be named “Bif1234” or “Tr0gBot” to mark its presence on the system.
* * *
## Threat Breakdown
### Win.Dropper.HawkEye-9984948-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 25 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORERADVANCED
Value Name: Hidden`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: Windows Update`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`104[.]16[.]154[.]36`| 1
`208[.]123[.]117[.]2`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`whatismyipaddress[.]com`| 1
`s3[.]dedicatedpanel[.]net`| 1
Files and or directories created| Occurrences
—|—
`%APPDATA%pid.txt`| 1
`%APPDATA%pidloc.txt`| 1
`%TEMP%holdermail.txt`| 1
`%TEMP%holderwb.txt`| 1
`%APPDATA%WindowsUpdate.exe`| 1
#### File Hashes
`06572f2182ef9dfaf3b8c7d2e025a18a2f4529fb989ad41fd54e17c3532aac0b`
`178319c41b50d3b78e36d6ac9105b81cbbe74375ce13b271e3ede79222f83854`
`234f8d4603971d0c86b5a4ccd06212b785ec6a260f9c692db3cced7d3ae6ce77`
`235bdaa330b9305eb30b08c8e63e28d318bcdb640e87e2bac1f77caf643e2494`
`255a56ac4fda1184eabc21cca66983c70bd795c99851802595441c5151e4a152`
`2ba523bc65c1f954e3f45324986840c5a910b4cd6d992d4bc228cbb86def8e98`
`3af54f2049dbc175ef4c589aa376141586711dd724617ed87e0a5bc7f1e431c0`
`4370bb6226f36558266a224de5ebb1582208f82bafdf9f2e2617a5cdace9d377`
`508708e5f5ab169299334434b17fc926d7972b9cc601e0f588ec979a6fb67f4a`
`549887b9e8e1ffe1e95a31a287c61ca265dd864b886034c22e4bf12bedb5ac91`
`60355c9d953b39905ec1d23237cc8339b2e1ffe0eb29bc8028dde75bddedd8db`
`71b210336d2277a498c150e99ddfb99750b8e481fb6dd0d647b7be571c2629f1`
`7628f72251de0d74df47361bb228fc34abdc121212d6da40936052a5215054e6`
`9143f2fe92b76f3a42dbeddccb738a397e2d07e5060046a367ed6c1a2c543dd4`
`a1d8085822a839d8e4f5078584dadc2221738309dbb6e386deb60c4cb8685d90`
`a3f5688c1f1d5473722fd4a6ae84be5c4f8235db2789fd1e77929cfbb026078a`
`a41cf4f43bdf0ca8bd515799702f62a1ff811d898f823d1c0225422a54376607`
`a6f20cc5f0a34adf5ac4582936e5407e48397db18847afa6ea3068c707cc40dd`
`b30e4856fd0b7adacf553023314db78e88638cd6ee9a14f2f0b8e3dad8fff98c`
`b66a4c2e0b22011ba409167c9bb663997b180a35f50fbe124bc0439403d65e74`
`d28b60289c250c1a5a2661dd4a57839cfa3e273f5ef5b068624ff99a2ccc2b65`
`d49278e577526a1839a13cb7066aabf02ea2d59cc7bb1c922404270cab602c1b`
`de4afe7e3fe9fc07edbf818ef66a0534844a9daf92d843b3402d67946222637e`
`e0ee8c2858064cf3eb1bb7a467aa07e9804255570d7b6e25ddfe927cef2d83f8`
`e21e57541123a49fdfde9912b959fda0bdf5c5fb951094a44bda3fed61ee0c06`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
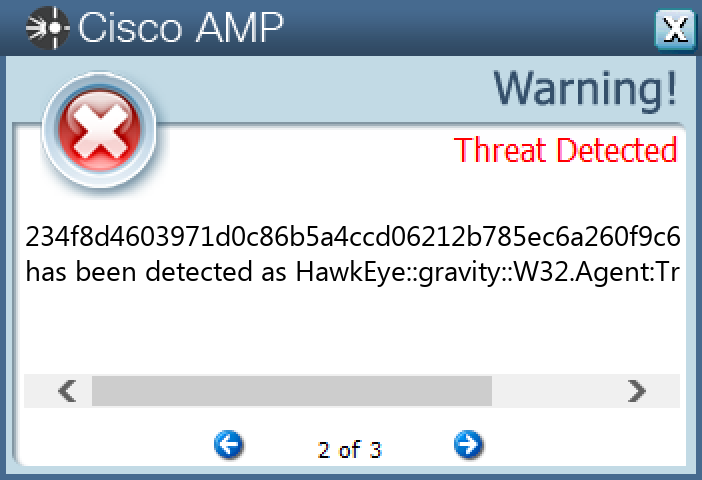
#### Secure Malware Analytics
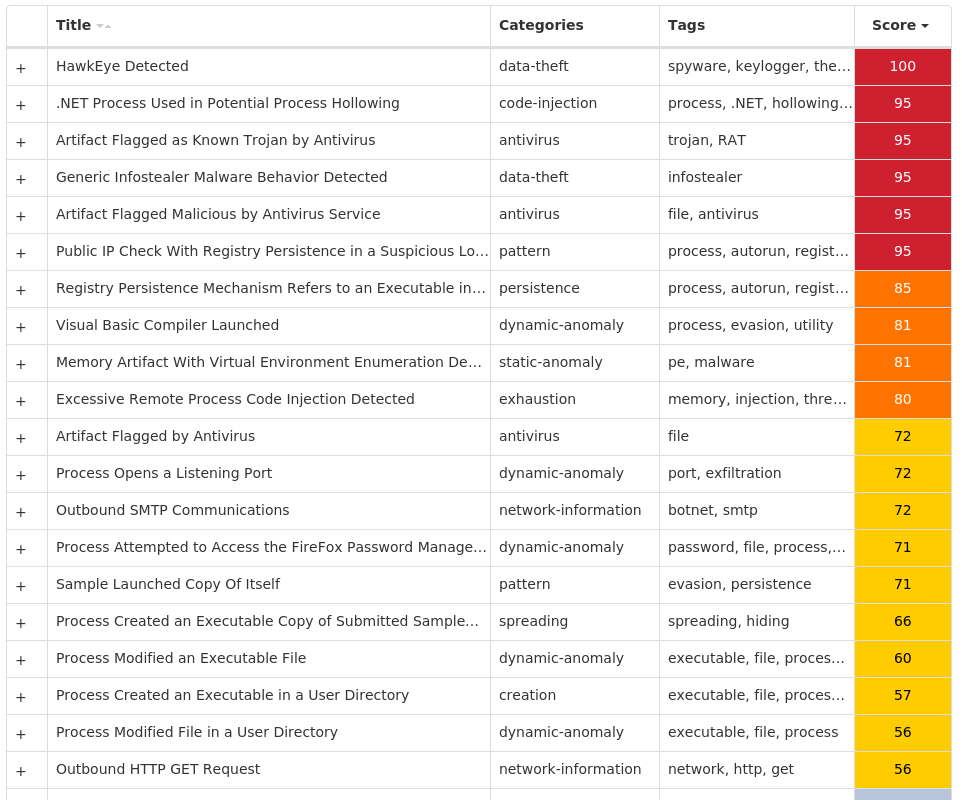
#### MITRE ATT&CK

* * *
### Win.Dropper.Zegost-9984959-1
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 10 samples
Registry Keys| Occurrences
—|—
`SYSTEMCONTROLSET001SERVICESRS`| 7
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ConnectGroup`| 7
`SYSTEMCONTROLSET001SERVICESRS
Value Name: MarkTime`| 7
`SYSTEMCONTROLSET001SERVICESRS
Value Name: Type`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: Start`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ErrorControl`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ImagePath`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: DisplayName`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: WOW64`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ObjectName`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: Description`| 5
`SYSTEMCONTROLSET001SERVICESRS
Value Name: FailureActions`| 5
`SYSTEMCONTROLSET001CONTROLRSETSR BQMYSGMF`| 1
`SYSTEMCONTROLSET001CONTROLRSETSR BQMYSGMF
Value Name: ConnectGroup`| 1
`SYSTEMCONTROLSET001CONTROLRSETSR BQMYSGMF
Value Name: MarkTime`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: Type`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: Start`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: ErrorControl`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: ImagePath`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: DisplayName`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: WOW64`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: ObjectName`| 1
`SYSTEMCONTROLSET001SERVICESRUNTIME BROKER
Value Name: Description`| 1
Mutexes| Occurrences
—|—
`Global58026681-1745-11ed-9660-001517439349`| 1
`csq1.e2.luyouxia.net:24705:Rsetsr bqmysgmf`| 1
`127.0.0.1:8000:Rscsso omyumyeq`| 1
`127.0.0.1:8000:Rsgewq wsqscuqa`| 1
`dlos1245.e2.luyouxia.net:21516:Rszhzn ppzrdglm`| 1
`182.61.134.76:8000:Rsidcj jyuwqkyj`| 1
`121.4.85.235:1499:Rsgkcs icmwmkam`| 1
`w794754387.e2.luyouxia.net:29523:Rswsue csscaksq`| 1
`43.230.169.58:8000:Rsvurb jfjqyucm`| 1
`112.18.159.112:34567:Runtime Broker`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`180[.]97[.]221[.]120`| 2
`43[.]230[.]169[.]58`| 2
`123[.]99[.]198[.]201`| 1
`121[.]4[.]85[.]235`| 1
`182[.]61[.]134[.]76`| 1
`124[.]248[.]66[.]214`| 1
`112[.]18[.]159[.]112`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`lqwljs[.]cn`| 1
`sjlwql[.]top`| 1
`dlos1245[.]e2[.]luyouxia[.]net`| 1
`w794754387[.]e2[.]luyouxia[.]net`| 1
`csq1[.]e2[.]luyouxia[.]net`| 1
Files and or directories created| Occurrences
—|—
`%ProgramFiles(x86)%Terms.exe`| 1
`%ProgramFiles(x86)%Microsoft Qbeuxn`| 1
`%ProgramFiles(x86)%Microsoft QbeuxnWywssvd.exe`| 1
`%SystemRoot%SysWOW64Mawyace.exe`| 1
`%ProgramFiles(x86)%Ezsszfx.exe`| 1
`%ProgramFiles(x86)%Bjrvlbx.exe`| 1
`%ProgramFiles(x86)%RuntimeBroker.exe`| 1
#### File Hashes
`1e31145e87fcaf55e61e38d4aa7f4dc71be19d35ff3f747a684e488805b07594`
`3ddcaa1008f22e9abddf2252d69ee1724a21a1d07005584ac42505539e5379a6`
`6d448045dbe5f11cca8ac423edb230c38279b201fbb512d5dc5f1207a93cbb17`
`7b61780a7a04cc483f25f790fbe210086748626a1de1988340cb35895f7df70e`
`7f399111c9b70c0de1b51525fec281e6eb6a39af6802a0abe626678af0d1ced3`
`87233e65e7b07831749fb294687632b8ef51b2f155d412024a561243288e08b6`
`a607a60d0d952d7d73649ce327646fe2de7f7cdaa2ca7785faa7851b9b8d100c`
`d6457c55dd9eba5fd8078e7bacf965c65232d713a1e037064f3617ad4d45844f`
`f6647a78d8bf05b80830dfd013a7876b4f9619c16433478a4fd2b69fbac9d0d9`
`fc7a21b32715e94357d9e7659b18d93b5401e63187e9952b50b45a23673abc99`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
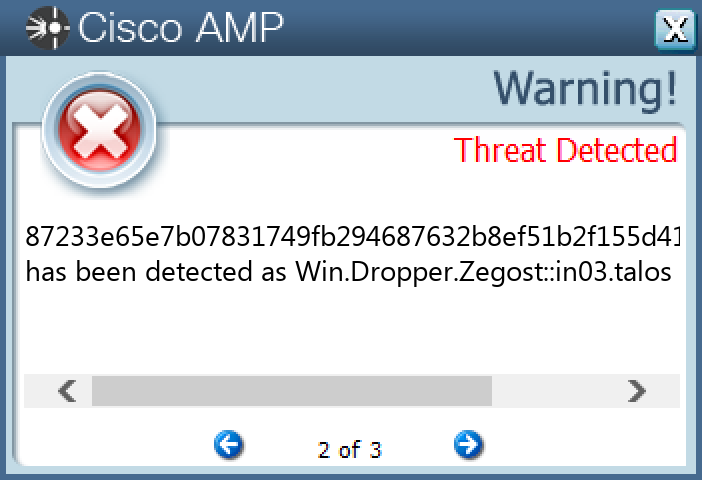
#### Secure Malware Analytics
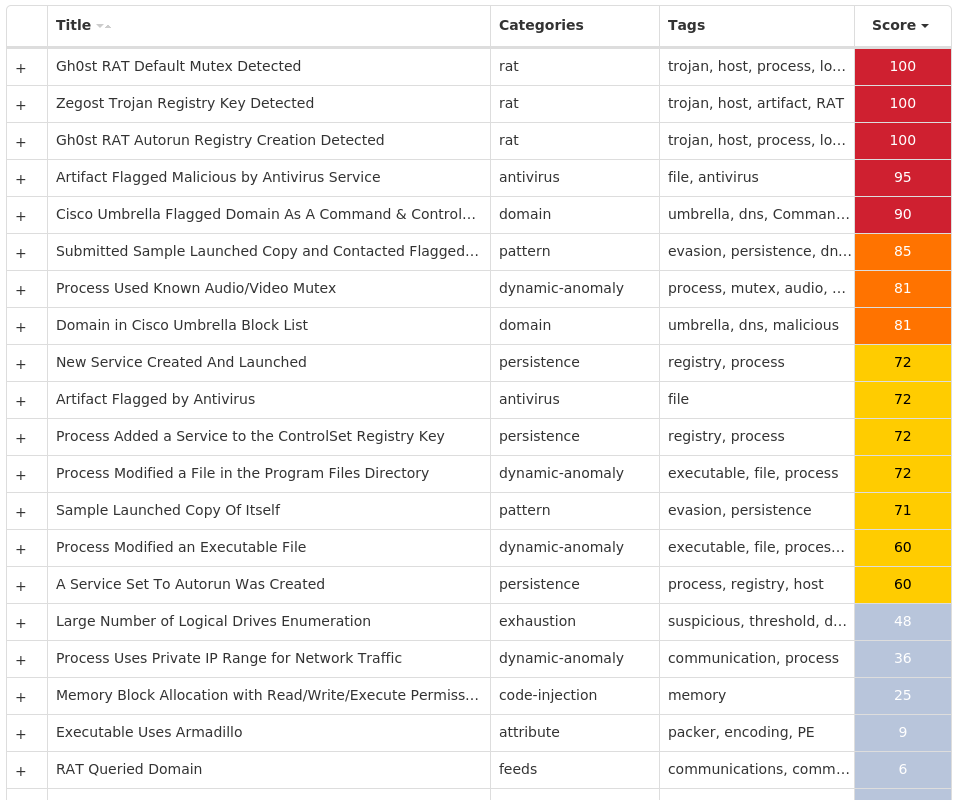
#### MITRE ATT&CK
* * *
### Win.Ransomware.TeslaCrypt-9985040-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 16 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESSYSTEM
Value Name: EnableLinkedConnections`| 16
`SOFTWAREXXXSYS`| 16
`SOFTWAREXXXSYS
Value Name: ID`| 16
`Software`| 16
`Software
Value Name: data`| 16
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: aingokyddfin`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: xynflbfpqxfg`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: xsrdyarnlxkb`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: nrosuypgjita`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: uqjergivpotl`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: cokwmnrosuyg`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: xhcqdmqiixoc`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: fsglxsrdyang`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: bajwwakyuxyv`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: urbajwwakyuy`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: xenfsxranlku`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: xxynflbfqxsl`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: dcpegxxynflb`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: xxynflbfpqxe`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: wwakyuxyvyly`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: wakyuxyvalcg`| 1
Mutexes| Occurrences
—|—
`ityeofm9234-23423`| 16
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`85[.]128[.]188[.]138`| 16
`162[.]241[.]224[.]203`| 16
`34[.]98[.]99[.]30`| 16
`154[.]219[.]146[.]245`| 16
`23[.]221[.]227[.]165`| 10
`23[.]221[.]227[.]169`| 6
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`biocarbon[.]com[.]ec`| 16
`imagescroll[.]com`| 16
`music[.]mbsaeger[.]com`| 16
`stacon[.]eu`| 16
`surrogacyandadoption[.]com`| 16
`worldisonefamily[.]info`| 16
`apps[.]identrust[.]com`| 16
Files and or directories created| Occurrences
—|—
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$I08BO8F.xlsx`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$I11KHR4.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$I5QKHLN.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$I62TWBD.ppt`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$I6FZORX.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IABMX83.pdf`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IAJ2Y6R.pdf`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IALGTCS.xlsx`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IGTBBSA.accdb`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IH49RPF.ppt`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IH71GGR.ppt`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IJKODPH.pdf`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IJP965K.accdb`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IKY5R3M.pdf`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IMYCSIT.pdf`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$ISLP722.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IXLC77A.pdf`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IXUL2U1.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IYSR1FU.ppt`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$IZ2GMJW.XLSX`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$R08BO8F.xlsx`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$R11KHR4.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$R5QKHLN.doc`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$R62TWBD.ppt`| 16
`$Recycle.BinS-1-5-21-2580483871-590521980-3826313501-500$R6FZORX.doc`| 16
*See JSON for more IOCs
#### File Hashes
`046979df42da0affa983d6c73be7ad19afacbb6a05a28855cd302a24624ebb97`
`10a0df06ed33b5ed2771a316abc7cc9a621c2097fa9a4522d9c0ac31c4953b70`
`2bce73c239a95080211fbfbc5b5268e1fecc81b3e5348ca391d00486dfe67d70`
`3113c2ac299a173a07ea6de7da87a2f2f29ed95e509b9dc6e7128ea9a8796266`
`31e2b0639ccb2499f79c4d45a037a1b6db52e4d0145605076d5a3b28fe564566`
`4559e437ee99d1f7cf2727597e030fade0c452c3ae0649e4669306372522db22`
`4f7473bb503c036c12d8e5850f3aaeb1c8abe9cab4dd8b16314f258999eaa5cf`
`6fd825e2bddea82cbc88fccbfdd50f425aa05047ffab0b511fb55c3f85ae88e4`
`8837ded9097e82948c53a4c875d66ff10271127e93702f89a8e4a9265625564d`
`91df821cfa7634ff2b6e08a73533885f3ed24c19aa61d3f5d5e346b97d1f1590`
`acbbd4b0c721c51bd9e510823659b521536ce43aad5eb324783c1c9e03e94974`
`cb998389d745287bc242eb23fe128d50bb42198b6e2cf7092e9576471cf25a38`
`d89d2f295b2a07e6bf0bf6c2a1b47c8221700746b781a5e537099c212da6b06b`
`d91e331d39b96788c6c7fb7ab3bf652d46f53be628331a7753ed1955e5f717be`
`e5db44290dea09182ee4383925805ee3bc901966cba16d7c05704b5a01eed95a`
`ee0ca0f158ba207090b00152ac85b17e4ba097335bcf9242ca8246e849bcf537`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK
* * *
### Win.Ransomware.Tofsee-9985077-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 18 samples
Registry Keys| Occurrences
—|—
`.DEFAULTCONTROL PANELBUSES`| 3
`.DEFAULTCONTROL PANELBUSES
Value Name: Config2`| 3
`.DEFAULTCONTROL PANELBUSES
Value Name: Config1`| 3
`.DEFAULTCONTROL PANELBUSES
Value Name: Config0`| 3
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: Type`| 1
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: Start`| 1
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: ErrorControl`| 1
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: DisplayName`| 1
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: WOW64`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT`| 1
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: ObjectName`| 1
`SYSTEMCONTROLSET001SERVICESIJPLOJAV
Value Name: Description`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: Type`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: Start`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: ErrorControl`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: DisplayName`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: WOW64`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: ObjectName`| 1
`SYSTEMCONTROLSET001SERVICESGHNJMHYT
Value Name: Description`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64ijplojav`| 1
`SOFTWAREMICROSOFTWINDOWS DEFENDEREXCLUSIONSPATHS
Value Name: C:WindowsSysWOW64ghnjmhyt`| 1
`SYSTEMCONTROLSET001SERVICESQRXTWRID`| 1
`SYSTEMCONTROLSET001SERVICESQRXTWRID
Value Name: Type`| 1
`SYSTEMCONTROLSET001SERVICESQRXTWRID
Value Name: Start`| 1
`SYSTEMCONTROLSET001SERVICESQRXTWRID
Value Name: ErrorControl`| 1
Mutexes| Occurrences
—|—
`Global`| 8
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`31[.]13[.]65[.]52`| 3
`176[.]113[.]115[.]136`| 3
`80[.]66[.]75[.]4`| 3
`176[.]113[.]115[.]154/31`| 3
`176[.]113[.]115[.]158`| 3
`176[.]113[.]115[.]239`| 3
`176[.]113[.]115[.]135`| 3
`94[.]100[.]180[.]90`| 2
`31[.]13[.]65[.]174`| 2
`77[.]88[.]21[.]125`| 2
`212[.]42[.]75[.]240`| 2
`52[.]223[.]241[.]7`| 2
`40[.]93[.]207[.]0`| 2
`142[.]250[.]176[.]196`| 2
`142[.]251[.]35[.]163`| 2
`20[.]53[.]203[.]50`| 2
`141[.]8[.]193[.]185`| 2
`23[.]3[.]13[.]35`| 1
`66[.]254[.]114[.]41`| 1
`40[.]97[.]188[.]2`| 1
`200[.]147[.]36[.]76`| 1
`104[.]47[.]18[.]97`| 1
`104[.]23[.]141[.]25`| 1
`104[.]23[.]139[.]25`| 1
`104[.]23[.]143[.]25`| 1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`249[.]5[.]55[.]69[.]bl[.]spamcop[.]net`| 3
`249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org`| 3
`249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net`| 3
`249[.]5[.]55[.]69[.]in-addr[.]arpa`| 3
`249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org`| 3
`249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org`| 3
`i[.]instagram[.]com`| 3
`microsoft-com[.]mail[.]protection[.]outlook[.]com`| 3
`microsoft[.]com`| 3
`www[.]google[.]com`| 3
`svartalfheim[.]top`| 3
`www[.]instagram[.]com`| 2
`video-weaver[.]lax03[.]hls[.]ttvnw[.]net`| 2
`www[.]google[.]nl`| 2
`imap[.]mail[.]ru`| 2
`imap[.]ukr[.]net`| 2
`imap[.]yandex[.]ru`| 2
`www[.]tiktok[.]com`| 1
`www[.]ebay[.]co[.]uk`| 1
`www[.]omegle[.]com`| 1
`imap[.]aol[.]com`| 1
`www[.]pornhub[.]com`| 1
`outlook[.]office365[.]com`| 1
`front1[.]omegle[.]com`| 1
`ebay[.]com`| 1
*See JSON for more IOCs
Files and or directories created| Occurrences
—|—
`%SystemRoot%SysWOW64configsystemprofile`| 3
`%SystemRoot%SysWOW64configsystemprofile:.repos`| 3
`%SystemRoot%SysWOW64ijplojav`| 1
`%SystemRoot%SysWOW64ghnjmhyt`| 1
`%SystemRoot%SysWOW64qrxtwrid`| 1
`%TEMP%dsgdwcyb.exe`| 1
`%TEMP%gnnrscmx.exe`| 1
`%TEMP%ysizcadm.exe`| 1
#### File Hashes
`52d043fde53ca1f8206e8cccec0a6202608927cbe1ccc66c897ce7806e0bb8db`
`52f7941f779a31924cbdc50ea92481821281f9ed61e1751689e6d0d77a28b865`
`573c4a98edae30752a2a3153796707b149bd8fefe265509e6a4e95e64a00edde`
`6017f05c453161374cfd6f9729b6b2e12d5e22f34e64c854700aeba843e512b4`
`685db303322dd68e66a46447b37022cdc4d0000576cad05eef5234eb09dc9f31`
`712f57fd1ad51878132bf31a9c10845cfdd201268b5f29683f331daaa94064e0`
`8b945dac10d16c2f76a20b497a392f9782768d4ec233c38890c5b4e4d347b7e0`
`8c766a9efc8d743b072044be56b41a98eaa0750d17bd9940fd334423bf4163d5`
`942b61d7f36de871315070d6b89f8bee9d49f043fd115b710b202138209a51a7`
`9f7538929d41e712d2f0af226ca663c890b07301140d8569f071a43815dd39b4`
`a378313d3462b42b4bd6f81218d6ddcad3c58730042a09d6ea7d2724de6ad8f5`
`a8dab16a73c683ced6a88ba70b1b3fba1d06d5c214e3b8a534b69c49ceab3bac`
`b7371868a517e14b30fc12515aa5dfea39f3786ce1a14b0061815d462302eebe`
`c8ecbd53f00218c14ea066848502f5828f7f77cde4fcee3b66e9c72088ab1ca8`
`d4ded32b48c5896ea5c338e2f0fb6131ec4365d2aca874901f979ef1b34cff53`
`dd14921b8274f08aebcfe6d02359191fec130e13feffbde9b4cb88f9810bc10b`
`e6f650114bc7e368a97786dacf73d57f3c4b8766f895fe2a570781ec9e8f6f28`
`f68d76ebc0c51240fccaccd641c66f1e0059b5ccfeabff3737fc5e5bbab1ddb7`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
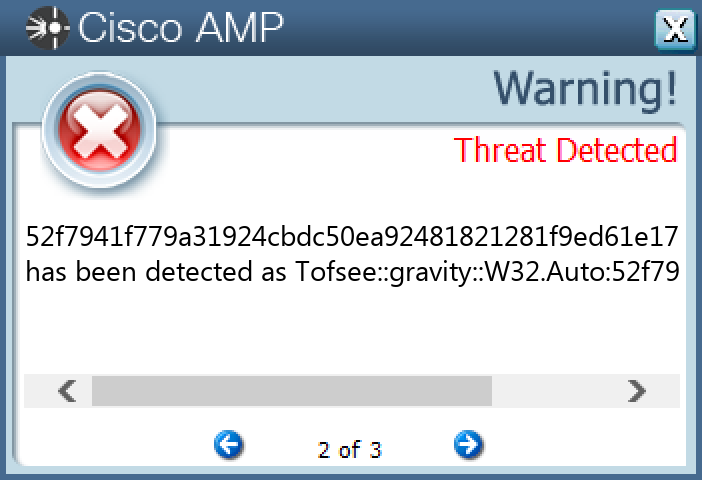
#### Secure Malware Analytics
#### MITRE ATT&CK
* * *
### Win.Dropper.Zeus-9985129-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 26 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTINTERNET EXPLORERPRIVACY
Value Name: CleanCookies`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONACTION CENTERCHECKS{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
Value Name: CheckSetting`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: {AA56720F-EB83-D818-7B46-E026C6F642DC}`| 1
`SOFTWAREMICROSOFTZOOZIN
Value Name: Yqameb`| 1
`SOFTWAREMICROSOFTZOOZIN`| 1
Mutexes| Occurrences
—|—
`Local{8D47BEAD-2721-FF09-7B46-E026C6F642DC}`| 1
`Local{A847581D-C191-DA09-7B46-E026C6F642DC}`| 1
`Local{DF676CEF-F563-AD29-7B46-E026C6F642DC}`| 1
`GLOBAL{}`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`muzze[.]biz`| 1
Files and or directories created| Occurrences
—|—
`%APPDATA%Moefylavai.hig`| 1
`%TEMP%tmp264ba9dd.bat`| 1
`%TEMP%tmp4e248681.bat`| 1
`%APPDATA%Moe`| 1
`%APPDATA%Xeit`| 1
`%APPDATA%Xeitottyga.exe`| 1
#### File Hashes
`024e7d89552b263467f912568ccd95181ac718f4a8e5012e5c6ec1aacf2f77e4`
`0483f996d51c910d04083acc2057c6889473e9dde561dc1f9b9535f738e594a1`
`0f6486fdaf98bb93a0557a3c44bb906d41b4c0e00c007bcad189914fae85be7c`
`16d63848bec52a9eaf184bdaa704674657c1a6b31cf50696b95cac7244fdc358`
`17877bc57bf371e332f3f59d46102319728261a80090791293be290056020b0e`
`1ac1fcff08cf6b2df798710c364bec4113d44c3447806dfc566191c0c5db7bb5`
`1c6cd22f8fdfc8219861db803349bce1cdeaa5cd880dae609e1a1667b5d022ad`
`1f4457b541ac0ad19951d39a1e260b1733210c68c7bc16932d0f3467f2e7c8b6`
`216e23b13eebcede1492f9414ef926bf49e825a42470bc265458debb103330ba`
`2426d26e4924f9514d674304627480a7cfb43e5e5ff1d1876321c188502374dc`
`2460deaefede5b79219cffdc473e5a9fc371d15b7797fa70d8449b4c4f9abe8d`
`274192458297e01466260a43ded24165efa899fe4448c73198f0de81766e2527`
`298f72fc3b9de5eb91ae3d6102526b832ae3365647d569877242d51e566f4029`
`347ccb8f6bb23038c9cd690cd5a4ce3ad79824ee65a1ce7477987fd106b5fd32`
`3654aaff7c3064cb607cac6d1211e7e64cafd5ceacfb0a416dbba719bdffc2cd`
`403122fe822bb9bc87aff93a2c93471a9360413d519781950d6871a8daeaf94d`
`4190f82a028deb2d0f399520e034a6f1ab5a78d14c4d1433be8ba4a6d2f70b41`
`4272e583ff2c4b9ce0e507cf339d14d750c05288b897557d0fd672c6f23fc8bf`
`427d2cfa6470def7183affabff2d26e582ee71dbb824e265261f01d86be2ac26`
`4a6538cbea79e455429465ced98f32a8736abe8a5a919d9f4f1446060a3f6c54`
`507cdd0ac8cfffd9815c86431289eac78ee92f1aa19825ee82d29e6650858dd5`
`5170ccdc6131e2f4341274bac186dddde935f77c0f3d3d6dc429171714f856ff`
`5308632516b9ae13e416fc7450750a8239a0d8a5aaa99e80af00ca5fb97d2386`
`6a432b1e261b3d366681b52fdec626a5673fd0fe8f3265898aabefc7be370581`
`6a5c370e1a6326d988f483defdae1214d6c3dae5126e0b2129f90eee59e21e4b`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
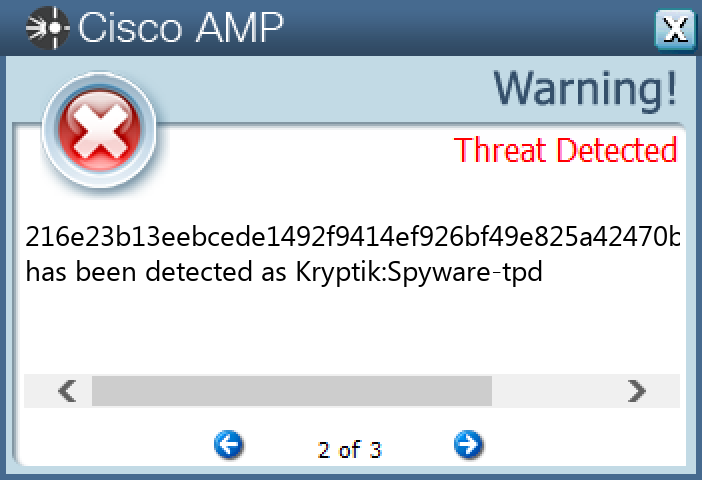
#### Secure Malware Analytics
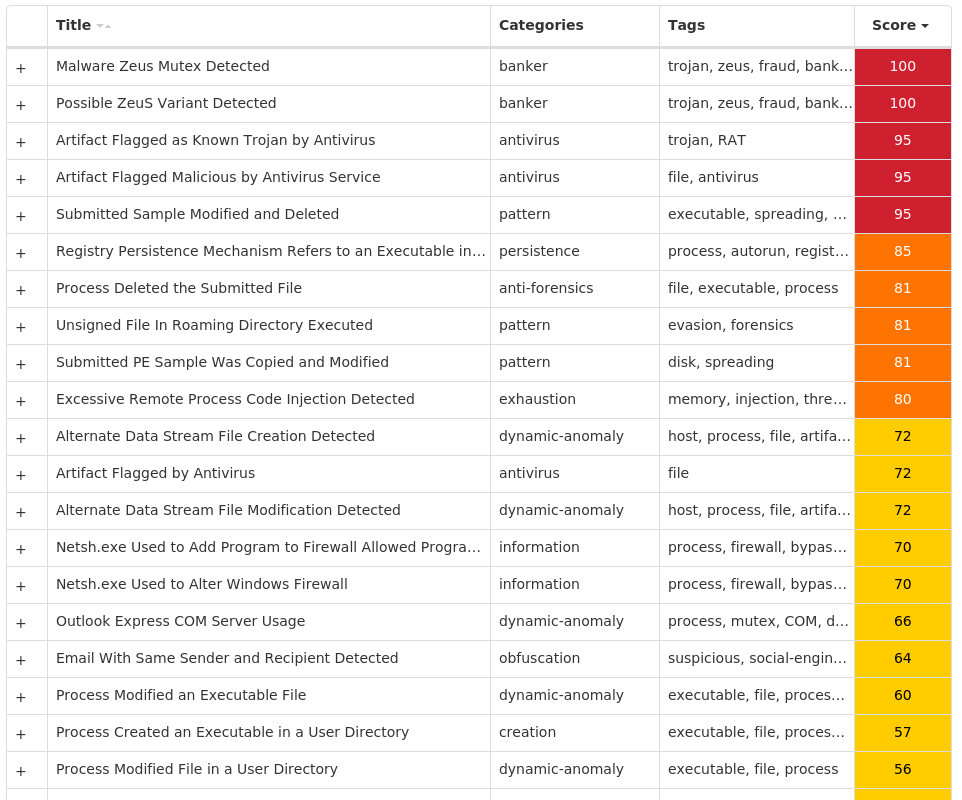
#### MITRE ATT&CK

* * *
### Win.Dropper.LokiBot-9985173-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 27 samples
Mutexes| Occurrences
—|—
`3749282D282E1E80C56CAE5A`| 1
`Globalf5549e21-9b80-11ed-9660-00151711fe83`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`sibiusmart[.]ro`| 1
Files and or directories created| Occurrences
—|—
`%APPDATA%D282E1`| 1
`%APPDATA%D282E11E80C5.lck`| 1
`%APPDATA%MicrosoftCryptoRSAS-1-5-21-2580483871-590521980-3826313501-500a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5`| 1
#### File Hashes
`0042a5fcd4c4e430c71d076dc5c95eac93069d77dfe821f412285bac7fa4597b`
`02f2e2f38004334f9c00f100f8eb03c80b85e25bf3fae085c1f2b1289d4cdce3`
`031c093a692f78038810f3249aacaf17b29b579432cabebe0344136c5812d1d4`
`04cebc586fb7609a622cb97edc1648efe1dd5109d8bfa8e6a5c65fd06e8a8c4a`
`05f2cbf468cbc1f49fa11344598a33343463c6a1b98e41a61e715b5a8e046d4a`
`09023da9a9c788b0b4f8fe97555f3f4487b37f29e64431c6dcfb269bfcdaeef3`
`0a34c917f81a02e080f92d9c5a4fe2c134da87861ea9e8cf54a99e027aa02583`
`0b8922eb675b84835d295358355ed825b98ba56f6ad2fb5a246a39dc2422a74a`
`19291bfe2f477f9a462f7bfec2a1a29ba596b8693b0f3130eb1fd2c532312b54`
`1c5e0c66477b508177bd9da97721bb97607f65374dedfddc711057aecc15aed5`
`1e1fb567710358f2f81e72642528581e08807786da92014303979f5fdd7149bc`
`1f93e1ad55e298fdade05c00dd0220ca9d3b26ab8044310388357ab0b900cefa`
`20da9b41f6f1c34732f193eb011f1b9bd25c29289fb687bfcfd14f74d14d6689`
`289a9718bf44f945cd95db839964ab225e347ac7490a5c89c8aa0a93f6474895`
`2b271dd0350ebce6ddd239803988c3f9a64aeee314cd032eb1d9d1ebfe26a8d2`
`2b2c302f12a0cf798e3621efe73064f0e938643956c07668fd8b54451b9acaec`
`367b0bcfe9894c93d7c2f9993a8ecbea7b0c16d6992752afd97e8a749a3f80af`
`38e9b92df247ef59650d723e0b04edeec9e7bc6983176edaa8c87cec9facbed5`
`396d98aeca3665a187a2b31fb0b7e026181a4f4c11876fa62a5723caa2016af5`
`3ea57948ea5e4758ef408714b2ae55c1d214f605f8f2b776f0518a681cf7529e`
`3f32dd4bdc512625ffbd05bb51c49bbb5500d63bb68a89826c1f2744601bc38c`
`3fb4c8d385d957154279efc406c309134ec41bfe1e0a6c536be9c20ffd2850b6`
`42a65e0d026b317b0ebe217180e5391e77c7d10f4938ac14a5884ff684816679`
`42b634f4a218d5093a94881b1548667722f87fa38d915a97fe126996ddf3c4ca`
`46760a3057ab75e01adda1a49b4a156282a4ab596db0053bb59b5f1be57650f5`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
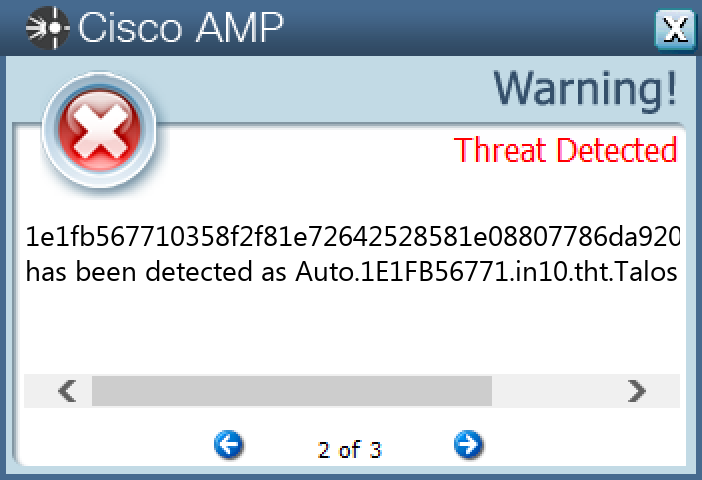
#### Secure Malware Analytics
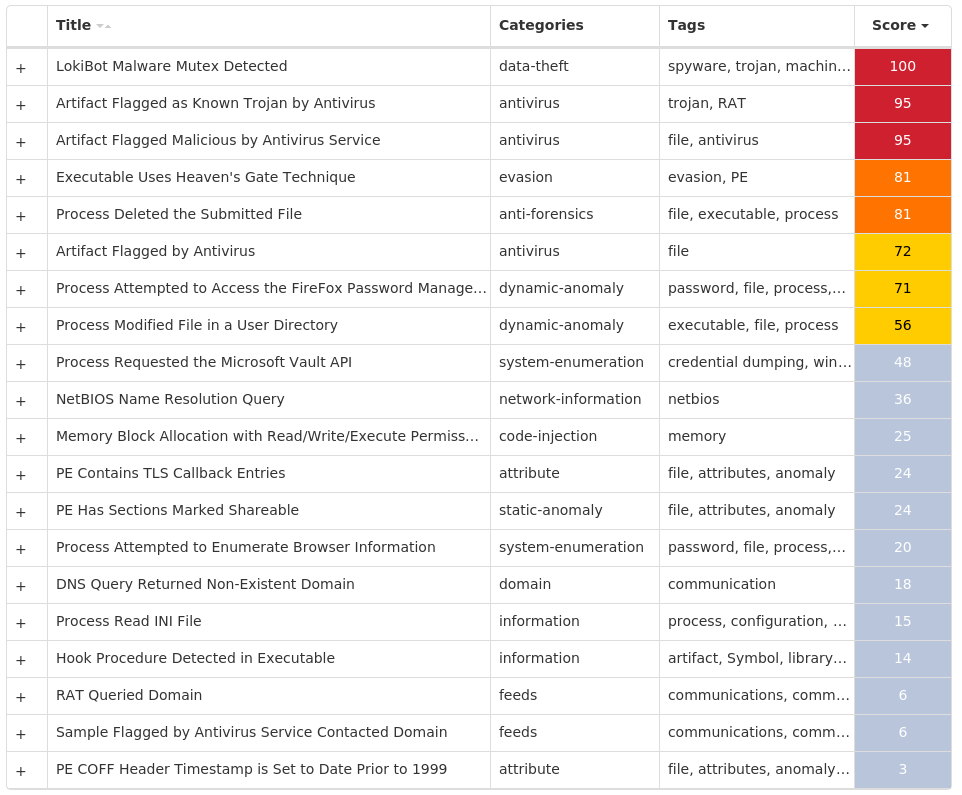
#### MITRE ATT&CK

* * *
### Win.Dropper.Nanocore-9985222-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 18 samples
Registry Keys| Occurrences
—|—
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: LanguageList`| 12
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @explorer.exe,-7001`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: UpDaTe`| 3
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: AGP Manager`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: NXLun`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: DnDcR`| 1
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @C:Windowssystem32DeviceCenter.dll,-2000`| 1
Mutexes| Occurrences
—|—
`aBdraOSHWQtfP`| 1
`ImvdLkQNiWmhZ`| 1
`FOdhZrTOEIj`| 1
`Global{cb7cb109-a06b-4fd7-8d0e-5290e77da5a5}`| 1
`RxDIBEIVVrpgGcjw`| 1
`obbAitLYlcWHDjd`| 1
`ZhStsilCCDoWCSTjZzsnSDITc`| 1
`LCEGTrpYB`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`149[.]154[.]167[.]220`| 3
`173[.]231[.]16[.]76`| 2
`84[.]200[.]69[.]80`| 1
`91[.]235[.]128[.]141`| 1
`104[.]237[.]62[.]211`| 1
`129[.]205[.]113[.]151`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`api[.]ipify[.]org`| 3
`api[.]telegram[.]org`| 3
`cp5ua[.]hyperhost[.]ua`| 1
`nonoise[.]duckdns[.]org`| 1
Files and or directories created| Occurrences
—|—
`%System32%TasksUpdates`| 5
`%TEMP%tmp.tmp`| 5
`%TEMP%UpDaTe`| 3
`%TEMP%UpDaTeUpDaTe.exe`| 3
`%System32%driversetchosts`| 1
`%ProgramFiles(x86)%AGP Manager`| 1
`%ProgramFiles(x86)%AGP Manageragpmgr.exe`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5Logs`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5LogsAdministrator`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5run.dat`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5task.dat`| 1
`%System32%TasksAGP Manager`| 1
`%System32%TasksAGP Manager Task`| 1
`%APPDATA%NXLun`| 1
`%APPDATA%NXLunNXLun.exe`| 1
`%APPDATA%DnDcR`| 1
`%APPDATA%DnDcRDnDcR.exe`| 1
`%APPDATA%THGNjTonqYzAQ.exe`| 1
`%System32%TasksUpdatesTHGNjTonqYzAQ`| 1
`%APPDATA%lisuoa2h.jv3`| 1
`%APPDATA%lisuoa2h.jv3Firefox`| 1
`%APPDATA%lisuoa2h.jv3FirefoxProfiles`| 1
`%APPDATA%lisuoa2h.jv3FirefoxProfiles1lcuq8ab.default`| 1
`%APPDATA%lisuoa2h.jv3FirefoxProfiles1lcuq8ab.defaultcookies.sqlite`| 1
*See JSON for more IOCs
#### File Hashes
`0829ed65c94d0ad265f99961d35fe56915c7b506671ae27a4ff6cae75e49cc66`
`1273b8a3054090fdf04f696dd22f284639ccb57afe9aa0a657d6fdb8fbdd3bd1`
`148a552de9c74376c409b18f2731c4dba0131c520c04a0cccb0af3364469bb73`
`2563e0db2599ab4c5d01fa046bc0706572b17a532ce52754f2977a735d8fbf01`
`371f8375dde28de80b098d9e808df9de07a5d8f0ab13d086325984d73a9cd5ed`
`3b704635a48f9ff94d44f0019e874ed71ddbc220bc3ce9f3cd7df38df120642a`
`53d55a9c88eb76405269ee02a4c4818214be23b6793b348d817ebc764506e5af`
`5fc15dd06f8ba66498c9865d6e82e6ff79c1f75284c5416ecb67baa8a604fa97`
`70d209addc0fea8ad36babd76a4b11f247dc11c9d8c1b48fffaf4b0e38efe886`
`7b9a9c4a56b756b499574a593ce6c5632f8a513abc4fd9a61844f211ffc672c8`
`90ab59d30c731411c996564775e58c6769535fd39e7ff51c48b690767c10f9e9`
`b388b8fefb3086f17b010cb86fd23957822e9d913b8d99d5ed786c7969fbaf78`
`ba846910ae2ae36a36f62eeaac3d693228dbe07d32484d23795414d5ac5908ff`
`c8d7e38a611b60fe03397645b2ae0b3bc2aaa9604c68c81f0baf6565b813fb35`
`cbf8d74421e9309ac79fd0556ef85c3b16e2bcf03fa196a5947eb3d0815cb1e6`
`cf0f97b4319ac18159cf02f905f91d07d4fe70722aefef70e32abe1b1fab9e7e`
`f7775262c09407cd3a8012620dd858aee083d645346d5419a4e16cff96eac373`
`fe8dfa5a692cbfdcc238b360d8e7e2f07b673d7d7645d9d2a2eabd245213457c`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
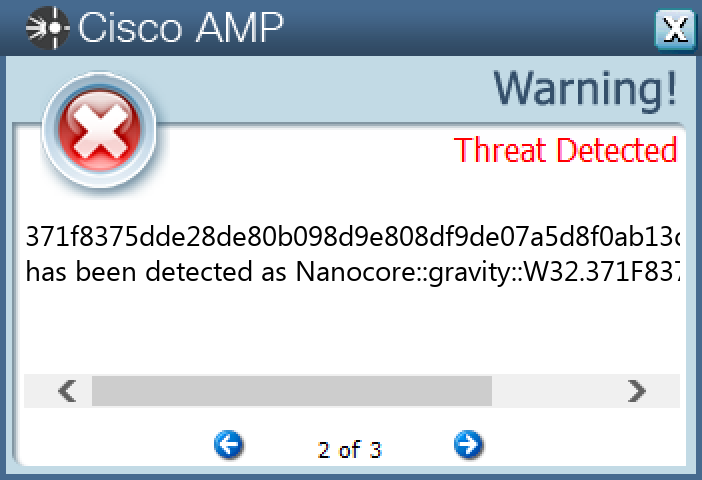
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Win.Ransomware.Cerber-9985289-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 28 samples
Registry Keys| Occurrences
—|—
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: LanguageList`| 28
Mutexes| Occurrences
—|—
`shell.{381828AA-8B28-3374-1B67-35680555C5EF}`| 28
`GlobalC::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!16613a8`| 28
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`178[.]128[.]255[.]179`| 28
`91[.]117[.]40[.]0/27`| 28
`91[.]119[.]40[.]0/27`| 28
`91[.]121[.]40[.]0/22`| 28
`172[.]66[.]42[.]238`| 14
`172[.]66[.]41[.]18`| 14
`104[.]20[.]20[.]251`| 12
`172[.]67[.]2[.]88`| 9
`104[.]20[.]21[.]251`| 7
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`api[.]blockcypher[.]com`| 28
`bitaps[.]com`| 28
`chain[.]so`| 28
`btc[.]blockr[.]io`| 28
Files and or directories created| Occurrences
—|—
`%TEMP%d19ab989`| 28
`%TEMP%d19ab9894710.tmp`| 28
`%TEMP%d19ab989a35f.tmp`| 28
`%LOCALAPPDATA%MicrosoftOfficeGroove1SystemCSMIPC.dat`| 28
`%TEMP%tmp.tmp`| 28
`%TEMP%tmp.bmp`| 28
`_HELP_HELP_HELP__.hta`| 28
`_HELP_HELP_HELP__.png`| 28
#### File Hashes
`04eb026fd69ee85a204deb1ab3d894fc95d543ff94667bc1f9baf05b77e1aa0c`
`11dd9314fe25aa3eb43b042abf8b81b9e50fcfd79528b81288e3f98961789db6`
`168ef2a56df0859de10120b164c6696d5affbf606fa9d6e79d78f6065d3edc03`
`1e0b0bfbc83d700f9583f730244b02b26b12ba1db5c50edbe3489418acc837de`
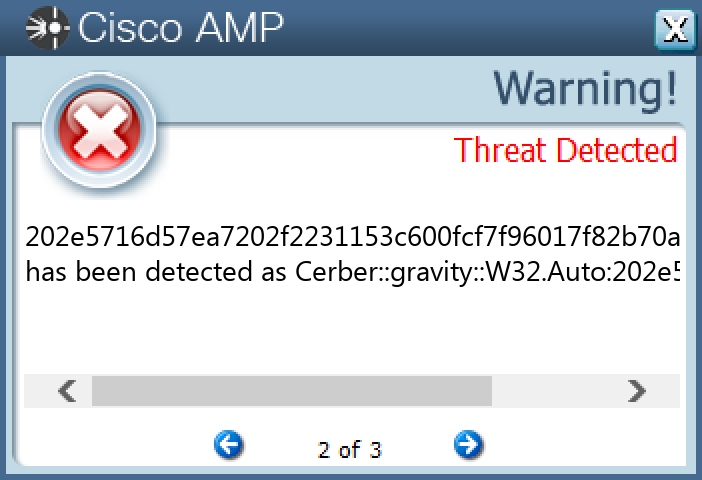
`202e5716d57ea7202f2231153c600fcf7f96017f82b70a11d6f15cb637a28779`
`258d29d87887f9e9303c0c23f466c6807c89f41ba19bc29d99d688971eb59c22`
`2e8e2e885a25bb09aa90943880e7d81b9addfc0013d76c205cc5f615028f1839`
`2f2f6a0ef0de62b9c305b24260b9208064130ea88d47a955f922a20f2be02ac0`
`31dc34001eb08664526ad2389b4b0cdf28214c595eba05bf0f84bf16fa6b119b`
`341d486619e7e2f91de5be87f1bca56ab58c3edebcdc35a949ea306cc4f2c91b`
`377df2eb0bffe8d47667a343f80f0dff71a47227369f8a63a5336736fca1718d`
`3d3382e61f289dd249b6817a694dc2c5ddfcdce7dafad7d1f3074e04bfa9442d`
`4843ee4070f7d7a3c6e06e2e1ba26014c1d1b54ba1ca6eed552ddbb7ffa76d7b`
`4e38a707a26fda9ba556cc17b79cb01121a51e6692809c18afe36e491b39174d`
`4f6e0e822cfb6ffa0cca7c80bd33a8184912e6621aa28459e06f70929d9d36d9`
`562f05f30ffb78866d0077785cfb36d11200f44dbf4abd68b4c43b016a136f8d`
`57631559806e8a977e616b9c00fbe3ff2a957d5c65bbd4bbd5fcd53a63489949`
`588c4714537fe5243b82572b8b98d2cc83cb99a18d188eaf883791e5125786da`
`5a21751f48b27dff8488521a6113a4e102164ad68f1d6ac43f90b8ad7a0ebc8d`
`693969c204a6b9714af4128612abeb08e36fbfc03bbef71accd253b0895b45b5`
`793c06d0016e679f27a26643ff229dc942588838874fa4605961c74d10c34a49`
`7e319635b05f872bcde07b37a87c45ac59a19cc403062b0a7a18125f6aa07d02`
`7f73061dda346d0528d01f811e508b5fc47076df69503576032053166340d2af`
`80654347845e9392f5039a94342f7b28c345c1ae6766939d7bda21360bf605bd`
`8444fb5e16ca451dad9a315610b43a604ded969009404bf88110f9a840cbd96b`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Win.Dropper.Bifrost-9985293-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 20 samples
Registry Keys| Occurrences
—|—
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: LanguageList`| 4
`SOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: HKLM`| 3
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: HKCU`| 3
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESEXPLORERRUN`| 3
`SOFTWARE((MUTEX))`| 2
`SOFTWAREWOW6432NODEMICROSOFTACTIVE SETUPINSTALLED COMPONENTS{5460C4DF-B266-909E-CB58-E32B79832EB2}`| 2
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @C:Windowssystem32DeviceCenter.dll,-2000`| 2
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESEXPLORERRUN
Value Name: 36412`| 2
`SOFTWARE((MUTEX))
Value Name: ServerStarted`| 2
`SOFTWAREWOW6432NODEMICROSOFTACTIVE SETUPINSTALLED COMPONENTS{5460C4DF-B266-909E-CB58-E32B79832EB2}
Value Name: StubPath`| 2
`SOFTWARE((MUTEX))
Value Name: InstalledServer`| 2
`SOFTWAREDC3_FEXEC`| 1
`SOFTWARECYBER
Value Name: NewIdentification`| 1
`SOFTWARECYBER
Value Name: NewGroup`| 1
`SYSTEMCONTROLSET001SERVICESSHAREDACCESSPARAMETERSFIREWALLPOLICYSTANDARDPROFILE
Value Name: EnableFirewall`| 1
`SYSTEMCONTROLSET001SERVICESSHAREDACCESSPARAMETERSFIREWALLPOLICYSTANDARDPROFILE
Value Name: DisableNotifications`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: MicroUpdate`| 1
`SOFTWAREMICROSOFTWINDOWS NTCURRENTVERSIONWINLOGON
Value Name: UserInit`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESEXPLORERRUN`| 1
`SOFTWARECYBER`| 1
`SOFTWARECJSXZ`| 1
`SOFTWAREWOW6432NODEMICROSOFTACTIVE SETUPINSTALLED COMPONENTS{05ACO487-3Q28-LSLC-XN56-108QEJS54A88}`| 1
`SOFTWARECJSXZ
Value Name: ServerStarted`| 1
`SOFTWAREWOW6432NODEMICROSOFTACTIVE SETUPINSTALLED COMPONENTS{05ACO487-3Q28-LSLC-XN56-108QEJS54A88}
Value Name: StubPath`| 1
`SOFTWARECJSXZ
Value Name: InstalledServer`| 1
Mutexes| Occurrences
—|—
`UFR3`| 6
`XTREMEUPDATE`| 3
`((Mutex))`| 2
`((Mutex))PERSIST`| 2
`((Mutex))EXIT`| 2
`2562100796`| 2
`lol`| 2
`CWSPROT20S`| 2
`Administrator1`| 1
`Administrator4`| 1
`Administrator5`| 1
`DCPERSFWBP`| 1
`Bif123`| 1
`CJSXz`| 1
`DC_MUTEX-3MWQJGB`| 1
`FR725I0U8LRK05`| 1
`FR725I0U8LRK05_PERSIST`| 1
`FR725I0U8LRK05_SAIR`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`20[.]72[.]235[.]82`| 2
`146[.]185[.]235[.]245`| 2
`52[.]8[.]126[.]80`| 1
`217[.]69[.]139[.]160`| 1
`208[.]91[.]196[.]46`| 1
`104[.]96[.]229[.]149`| 1
`199[.]191[.]50[.]166`| 1
`31[.]170[.]164[.]19`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`5noseqwa[.]no-ip[.]info`| 2
`ftp[.]vlakkeeetert[.]hol[.]es`| 2
`f4n6[.]hut4[.]ru`| 2
`smtp[.]mail[.]ru`| 1
`www[.]server[.]com`| 1
`ati2evxx[.]sytes[.]net`| 1
`x1[.]i[.]lencr[.]org`| 1
`kiwa[.]no-ip[.]org`| 1
`lolzor2h[.]zapto[.]org`| 1
`jalagui[.]no-ip[.]org`| 1
`www[.]webserver[.]com`| 1
`exploreinquiry[.]com`| 1
Files and or directories created| Occurrences
—|—
`TEMPufr_reports`| 5
`%TEMP%tmp.ini`| 3
`%APPDATA%MicrosoftWindows((Mutex)).cfg`| 2
`%APPDATA%MicrosoftWindows((Mutex)).dat`| 2
`%ProgramData%Local Settings`| 2
`%ProgramData%Local SettingsTemp`| 2
`%APPDATA%dclogs`| 1
`%SystemRoot%InstallDir`| 1
`%SystemRoot%InstallDirServer.exe`| 1
`%TEMP%Administrator7`| 1
`%TEMP%Administrator8`| 1
`%TEMP%Administrator2.txt`| 1
`%TEMP%x.html`| 1
`directory`| 1
`directoryCyberGate`| 1
`%APPDATA%addon.dat`| 1
`%APPDATA%Administratorlog.dat`| 1
`%HOMEPATH%DocumentsMSDCSC`| 1
`%HOMEPATH%DocumentsMSDCSCmsdcsc.exe`| 1
`TEMPufr_reportsNO_PWDS_report_25-01-2023_02-45-25-726A6BBD-JDGK.bin`| 1
`TEMPufr_reportsNO_PWDS_report_25-01-2023_02-43-24-726A6BBD-AIAB.bin`| 1
`%ProgramData%Local SettingsTempmswxle.bat`| 1
`%ProgramData%Local SettingsTempmswqmnvv.exe`| 1
`%TEMP%report_25-01-2023_02-44-14-726A6BBD-FDGN.bin`| 1
`%TEMP%isendsms_setup.exe`| 1
*See JSON for more IOCs
#### File Hashes
`0309e6c7cd2a73721e6956af2ec340c948bc5009450f76c9337ded167e60cfbd`
`26dfd674facde0f957bb4ed81e7cea4dae37114ced4d59c491d86bfc667d5dc4`
`32ac27ab6cd0654430449b0624a744169e2d0cc6769192fd79599e1ab6717632`
`3596f41561adf0d6eeb205b7414e17993f20da0590a28d2a4c94d984fd327fa8`
`49704324bbf8ffde957586c01cc85d45a970458d2697fe34f381d7cb82d7f88d`
`4c1986ea7e1ecea980fad59a62ddbf472bc2d7344c923332fd48f41dc6fbbe48`
`52fe24425eb3e6248e59fd959ce1956e09d1cbb65809f63706f0f9170ea0eb48`
`5c86c8c3bad2edd4174675a5dbab131d9b84ca5e5325431d2fa91d1c22292afa`
`6946be08c392001c142ad89213ff0860f3f3eac188b30c877e10783d435334ba`
`73d73c1a9f1e4494f550597a9d2438a79ebd900914c8b0851164aea5f1cb688e`
`7d2f5afc77e09d02b604cbdbfb5b33941914296966306761478609a23cd3a14e`
`975d3f301392e173335b801f6a12e3a7556ba00c2984a968ca033a44e69610c3`
`a6ab70d56a50d8446028ec0fef89bbde4e4a5784fd8a471b50392c0230d88fb0`
`b1da9aaa33886f2d103540ffd831f46d5f97280eca05f8013e277579cfd0051a`
`c1504e3f1b761540498a0fde42e462c0b20676502981ce84aa41049550159aab`
`c2014131fcee489c7e1c4a943237bd89dfeb5ba2ab1216ff89cfb202b00e2671`
`ca566fce1a39c24dd34479446524eac96d5e43634134e9e7616d2a18d5fba5ca`
`df05799c88e4cb5cbc2661b83e286d3247fa682dae330e6932c52a1d661935cb`
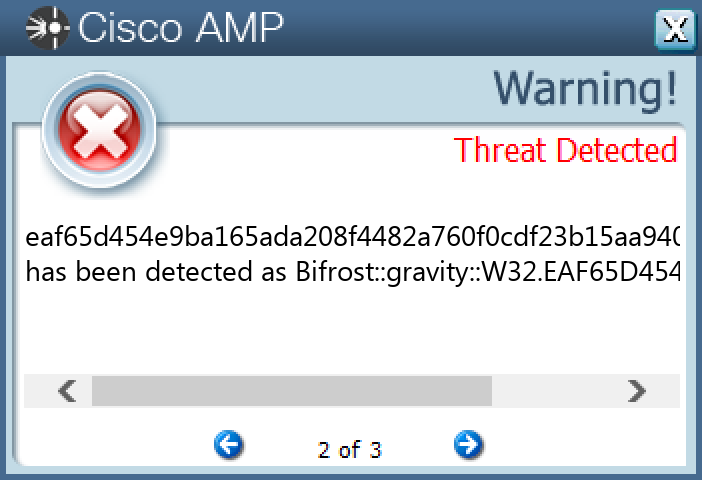
`eaf65d454e9ba165ada208f4482a760f0cdf23b15aa94022aa9617bf03609f2f`
`f5e2cf6885a62fad9a6488a8487e0490e5892bfac0dddeff515ba97b2b86d2cd`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
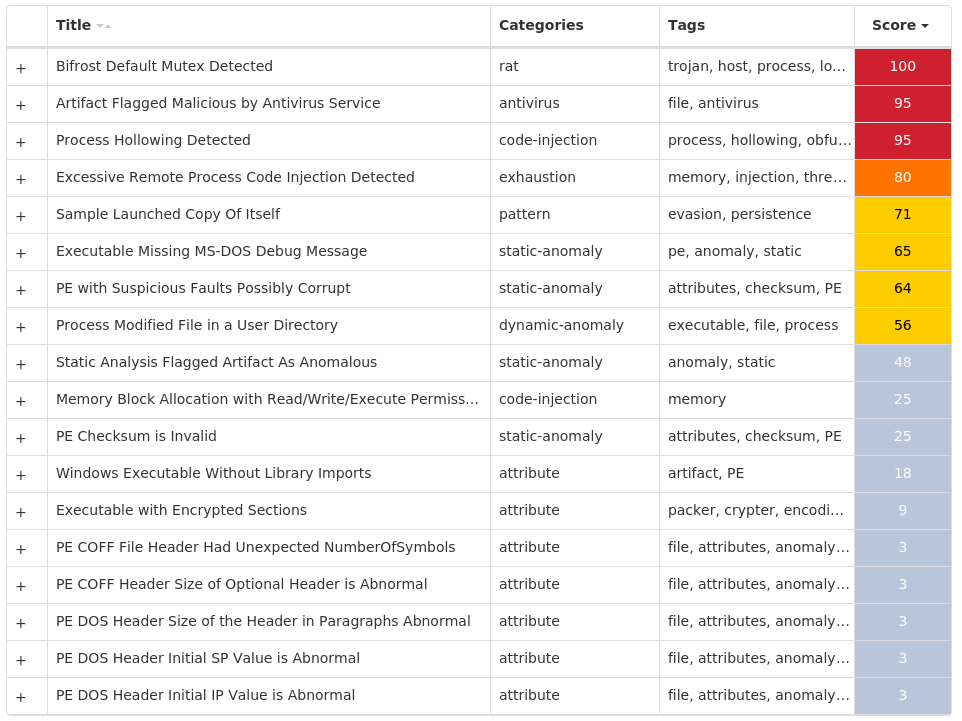
#### Umbrella
#### MITRE ATT&CK
* * *Read More

