
Today, Talos is publishing a glimpse into the most prevalent threats we’ve observed between Dec. 2 and Dec. 9. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, this post will summarize the threats we’ve observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, [Snort.org](), or [ClamAV.net]().
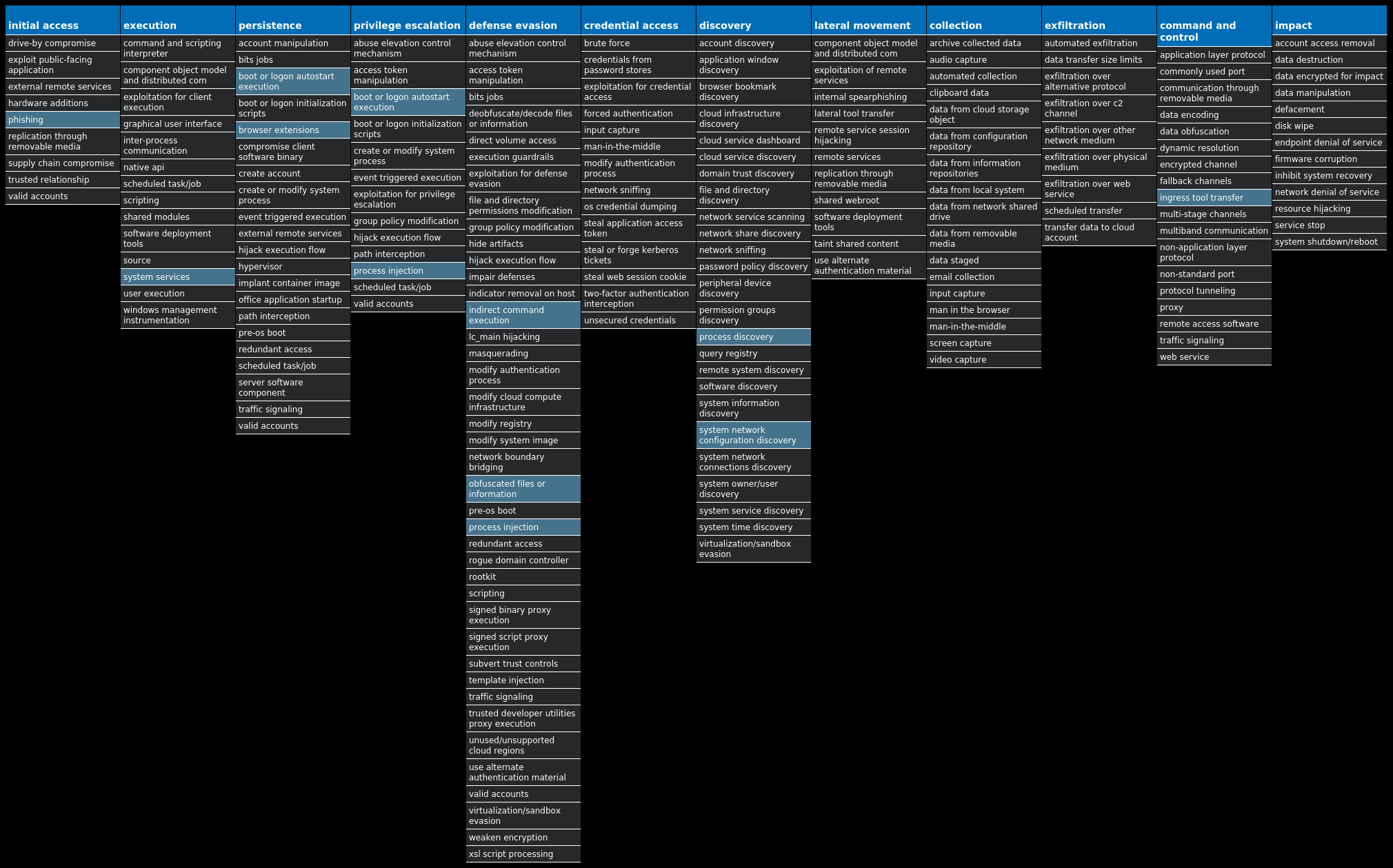
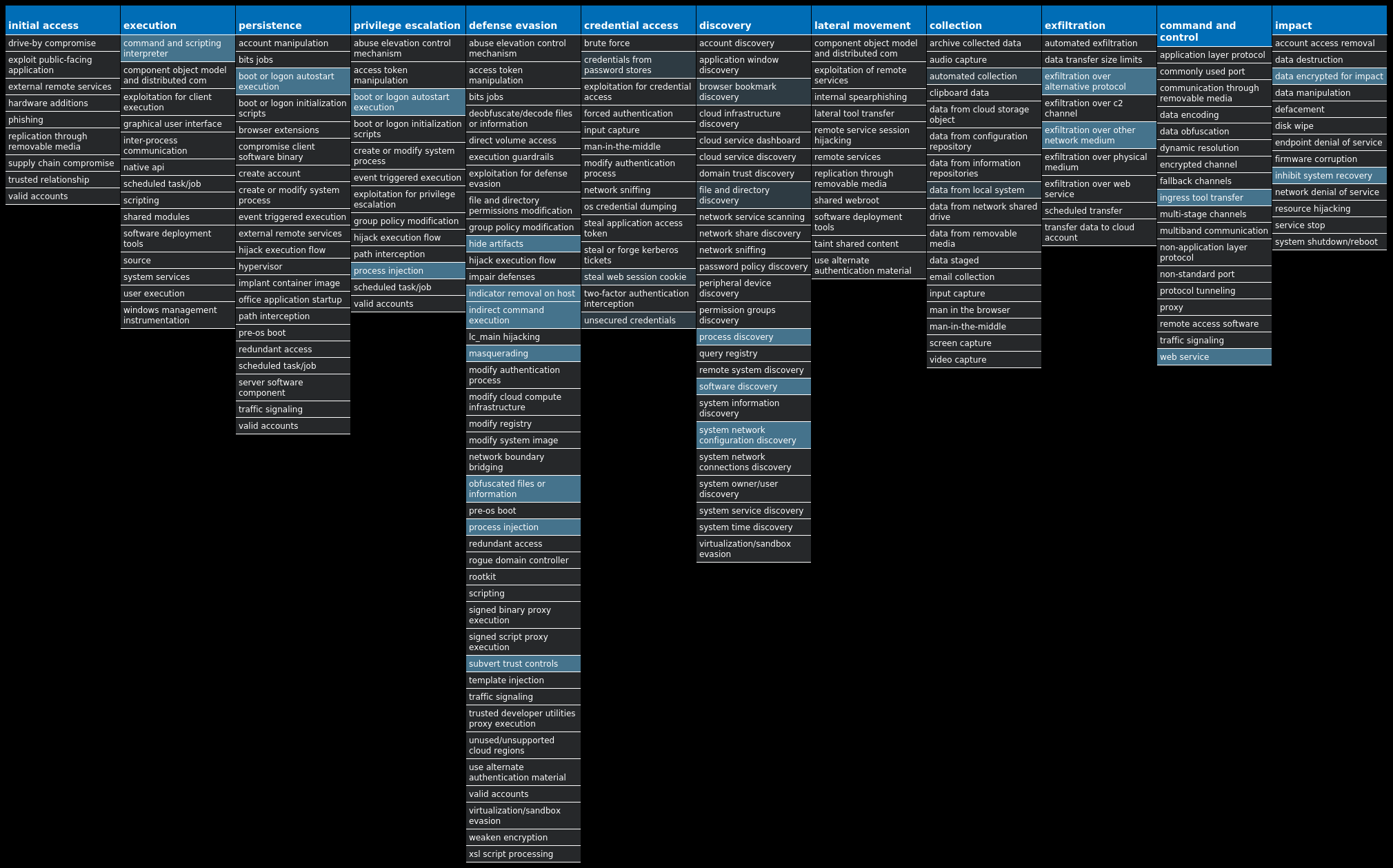
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found [here]() that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name| Type| Description
—|—|—
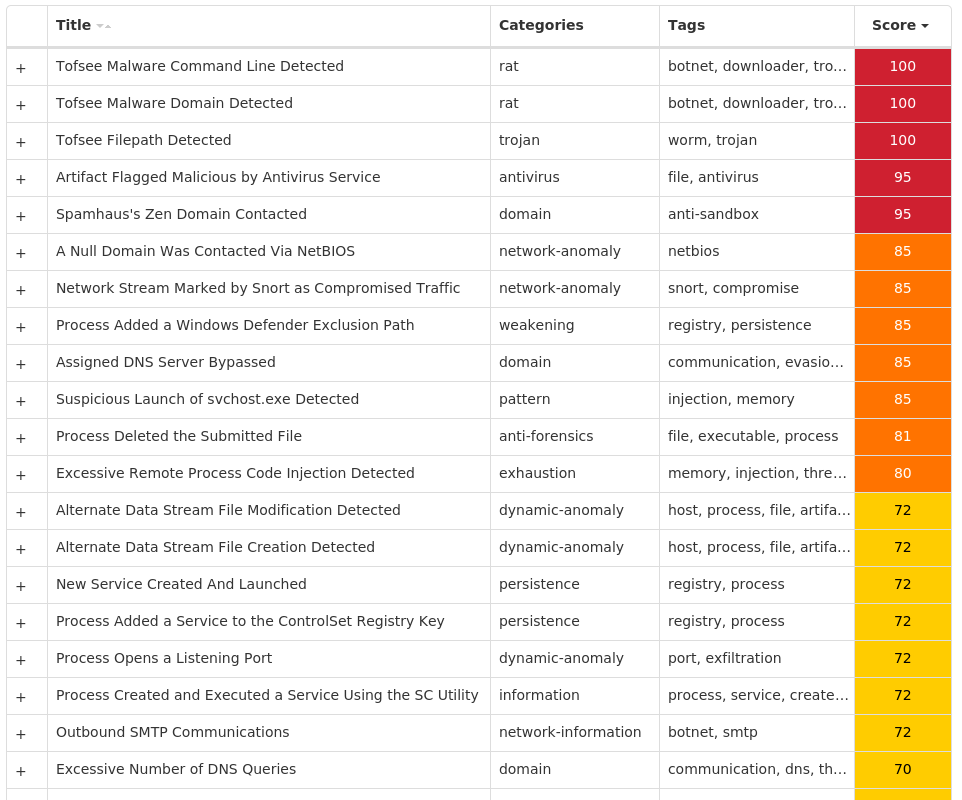
Win.Dropper.Tofsee-9980095-0| Dropper| Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator’s control.
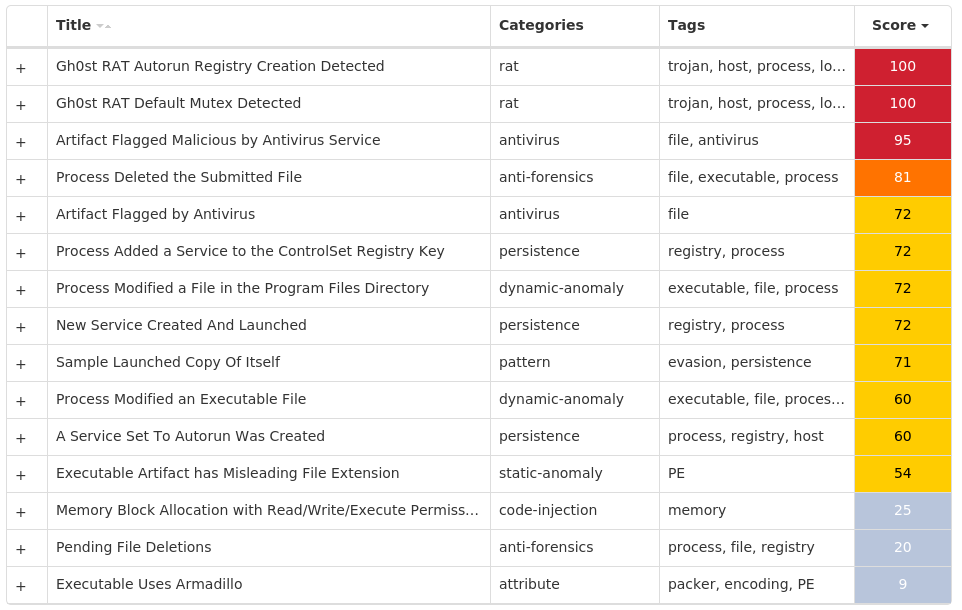
Win.Dropper.Gh0stRAT-9980136-1| Dropper| Gh0stRAT is a well-known family of remote access trojans designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. The source code for Gh0stRAT has been publicly available on the Internet for years, significantly lowering the barrier for actors to modify and reuse the code in new attacks.
Win.Malware.Barys-9980160-0| Malware| This is a trojan and downloader that allows malicious actors to upload files to a victim’s computer.
Win.Ransomware.TeslaCrypt-9980162-0| Ransomware| TeslaCrypt is a well-known ransomware family that encrypts a user’s files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily.
Win.Dropper.Remcos-9980211-0| Dropper| Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Downloader.Upatre-9980388-0| Downloader| Upatre is a trojan that is often delivered through spam emails with malicious attachments or links. It is known to be a downloader and installer for other malware.
Win.Dropper.Zeus-9980208-0| Dropper| Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing.
Win.Packed.Formbook-9980347-1| Packed| Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard.
* * *
## Threat Breakdown
### Win.Dropper.Tofsee-9980095-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 47 samples
Registry Keys| Occurrences
—|—
`.DEFAULTCONTROL PANELBUSES`| 32
`.DEFAULTCONTROL PANELBUSES
Value Name: Config2`| 32
`SYSTEMCONTROLSET001SERVICES`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: Type`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: Start`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: ErrorControl`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: DisplayName`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: WOW64`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: ObjectName`| 32
`SYSTEMCONTROLSET001SERVICES
Value Name: Description`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: LanguageList`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-100`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-101`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-103`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-102`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-1`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-2`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-4`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-3`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-100`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-101`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-102`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-103`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32eapqec.dll,-100`| 32
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32eapqec.dll,-101`| 32
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`80[.]66[.]75[.]4`| 32
`176[.]113[.]115[.]153`| 32
`176[.]113[.]115[.]154/31`| 32
`176[.]113[.]115[.]156/31`| 32
`176[.]113[.]115[.]158`| 32
`185[.]246[.]220[.]218`| 32
`142[.]250[.]80[.]4`| 26
`31[.]13[.]65[.]174`| 24
`31[.]13[.]65[.]52`| 24
`66[.]254[.]114[.]41`| 22
`40[.]93[.]207[.]0/31`| 12
`20[.]112[.]52[.]29`| 10
`64[.]88[.]254[.]180/31`| 10
`20[.]81[.]111[.]85`| 8
`20[.]84[.]181[.]62`| 8
`104[.]47[.]53[.]36`| 7
`157[.]240[.]241[.]63`| 7
`99[.]181[.]79[.]15`| 7
`142[.]251[.]40[.]238`| 6
`104[.]47[.]58[.]33`| 5
`52[.]101[.]40[.]29`| 5
`104[.]47[.]54[.]36`| 4
`104[.]244[.]42[.]66`| 4
`20[.]103[.]85[.]33`| 4
`40[.]93[.]207[.]2`| 4
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`249[.]5[.]55[.]69[.]bl[.]spamcop[.]net`| 32
`249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org`| 32
`249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net`| 32
`249[.]5[.]55[.]69[.]in-addr[.]arpa`| 32
`249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org`| 32
`249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org`| 32
`microsoft-com[.]mail[.]protection[.]outlook[.]com`| 32
`microsoft[.]com`| 32
`www[.]google[.]com`| 32
`svartalfheim[.]top`| 32
`i[.]instagram[.]com`| 24
`www[.]instagram[.]com`| 24
`www[.]pornhub[.]com`| 22
`api[.]twitter[.]com`| 13
`outlook[.]office365[.]com`| 12
`ev-h[.]phncdn[.]com`| 10
`www[.]youtube[.]com`| 8
`www[.]tiktok[.]com`| 8
`static[.]cdninstagram[.]com`| 7
`video-weaver[.]hel03[.]hls[.]ttvnw[.]net`| 7
`m[.]youtube[.]com`| 6
`imap[.]mail[.]yahoo[.]com`| 4
`identitysso[.]betfair[.]com`| 4
`work[.]a-poster[.]info`| 3
`www[.]google[.]es`| 3
*See JSON for more IOCs
Files and or directories created| Occurrences
—|—
`%SystemRoot%SysWOW64configsystemprofile`| 32
`%SystemRoot%SysWOW64configsystemprofile:.repos`| 32
`%SystemRoot%SysWOW64`| 31
`%TEMP%.exe`| 28
`%TEMP%zfxmrkb.exe`| 1
`%TEMP%gwylcuf.exe`| 1
`%TEMP%qwodibs.exe`| 1
`%TEMP%wmobskv.exe`| 1
#### File Hashes
`0186c1c7e7759379225a51ad5195f6883d87f0dd4fc95a7406a5f5110e394550`
`026c1e7682576aab35bdd6f44677840b3b3f6790589f4e6bc5f70c9b8c51e674`
`089af2387a0e21b30d76ae331b34468b7c4c1ed24f656d318c932709d311a886`
`09fd93369979085eac4b45e20a3107127a84480f3ad582ab1906600d489a6cdd`
`11b58325c447e4fad5c3ec3071817093f3860b892122a3c4535d3bdd5bd4e7b3`
`153d25cae448ed0f0e929c9c9700d24249f787c90f66e25601aa5ebb283194f8`
`1b411fd04815186d39c4e3ac05417eefe0299e49291164370122a51c89240576`
`1b5b74d151bbc9b23a474a117cd68c001a122670e240a0242d32810218492615`
`1d40a88b1ef8588364793c64b10b2fe831ac143108d10335ea098c8db9b4a28a`
`207d91d88d9fedc73b982147de55df6084ffe2028454b80a4b3c1a4b503e6d68`
`234a52159c7cc53ded1cd111bb59abd12bab5214e888a5bc6b1c60662f7ffbea`
`29808e1627e066dfdb6c6afb6ab46d72dde42f60acf35407758f64cdd0639cf9`
`2db5ec16fecbc4a28bc18b4be694ae049a2cf3a1a087873b994521820d11ed4d`
`301837c17daf5300750e923fea1b9cb5b788f2c998ecc93c9055336faebff385`
`3072e370d5da448802287762dff8d91931c530afd8fb629e2d9bacb917ca4b88`
`319f346c45cc51a7b407bbd509fe804e66ea5dd8b8a24fab20bd2a8dbdf0913f`
`3272c8ad524756808c315bd30a5f824009fb1fa4a6380d5f0910a81d1f91a664`
`397fecffafa7964e2bc7a2cd682c59440aa622238172ef596fc25e8f4afeb3f2`
`3af9d3b544efffa73762f9f33a0f9ccde31d9cce1bff8a940aa976af3ef8a77b`
`3c1f8c72c2e69790542eec1328b13e1fc220f916a20a5ad76a04cf2973fc7b0a`
`3f737e650db3fb5ccaa83c01f1fce2e67a95cb304d57a94e0fffa90a2d00c664`
`40a28f1903ead89f5307c095363773b48cc137fca2eb8d1fe1b85c0c0c5f6c06`
`45f919fe47a8f49fffedb1937cec37d254646f7ac4ecdaa55fe118f519b9af87`
`47582529f1d428d08196294a831744310cd73fd9d3ebb33b5d99c8f0a7f0d575`
`4a65eb95c352ac416f500fb4ef2913225cf9c8c85e1a677103b2dfbd5be82f59`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
### Win.Dropper.Gh0stRAT-9980136-1
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 10 samples
Registry Keys| Occurrences
—|—
`SYSTEMCONTROLSET001SERVICESRS`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: Type`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: Start`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ErrorControl`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ImagePath`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: DisplayName`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: WOW64`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: ObjectName`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: Description`| 6
`SYSTEMCONTROLSET001SERVICESRS
Value Name: FailureActions`| 6
`SYSTEMCONTROLSET001CONTROLRSGSCE SGUCOMGW`| 1
`SYSTEMCONTROLSET001CONTROLRSGSCE SGUCOMGW
Value Name: ConnectGroup`| 1
`SYSTEMCONTROLSET001CONTROLRSGSCE SGUCOMGW
Value Name: MarkTime`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN`| 1
`SYSTEMCONTROLSET001CONTROLRSUZTZ KQJEXTVY`| 1
`SYSTEMCONTROLSET001CONTROLRSUZTZ KQJEXTVY
Value Name: ConnectGroup`| 1
`SYSTEMCONTROLSET001CONTROLRSUZTZ KQJEXTVY
Value Name: MarkTime`| 1
`SYSTEMCONTROLSET001CONTROLRSWISU YECUACYA`| 1
`SYSTEMCONTROLSET001CONTROLRSWISU YECUACYA
Value Name: ConnectGroup`| 1
`SYSTEMCONTROLSET001CONTROLRSWISU YECUACYA
Value Name: MarkTime`| 1
`SYSTEMCONTROLSET001CONTROLRSCDXM RIIFDJKA`| 1
`SYSTEMCONTROLSET001CONTROLRSCDXM RIIFDJKA
Value Name: ConnectGroup`| 1
`SYSTEMCONTROLSET001CONTROLRSCDXM RIIFDJKA
Value Name: MarkTime`| 1
`SYSTEMCONTROLSET001CONTROLRSXYLX NTFSGSOE`| 1
`SYSTEMCONTROLSET001CONTROLRSXYLX NTFSGSOE
Value Name: ConnectGroup`| 1
Mutexes| Occurrences
—|—
`127.0.0.1:8000:Rsgsce sgucomgw`| 1
`ikun100.e2.luyouxia.net:25048:Rsuztz kqjextvy`| 1
`ikun100.e2.luyouxia.net:28249:Rswisu yecuacya`| 1
`127.0.0.1:17472:Rsxylx ntfsgsoe`| 1
`127.0.0.1:8888:Rscdxm riifdjka`| 1
`127.0.0.1:6666:Rsuusw uemccgci`| 1
`154.31.253.253:8000:Rsoiae ykkeoaki`| 1
`127.0.0.1:8000:Rsqigq cmekwwqs`| 1
`127.0.0.1:443:Rsqccq cygoawyq`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`47[.]52[.]162[.]13`| 7
`43[.]248[.]129[.]49`| 1
`180[.]97[.]221[.]120`| 1
`154[.]31[.]253[.]253`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`guduo[.]xyz`| 7
`ikun100[.]e2[.]luyouxia[.]net`| 2
Files and or directories created| Occurrences
—|—
`%ProgramFiles(x86)%Vrpbjrd.exe`| 1
`%ProgramFiles(x86)%Fvcbfwe.exe`| 1
`%ProgramFiles(x86)%Tbltlrr.exe`| 1
`%ProgramFiles(x86)%Cayeqau.exe`| 1
`%ProgramFiles(x86)%Microsoft Iewicw`| 1
`%ProgramFiles(x86)%Microsoft IewicwDocspgf.exe`| 1
`%ProgramFiles(x86)%Microsoft Kasiyg`| 1
`%ProgramFiles(x86)%Microsoft KasiygWaekgmk.exe`| 1
`%ProgramFiles(x86)%Microsoft Ltuyhe`| 1
`%ProgramFiles(x86)%Microsoft LtuyheCkuoeia.exe`| 1
#### File Hashes
`1f9f9e9d3864dc07d898a2daec88f0b93b7f2230384ee3a203b6877c1565f873`
`39bb3008748962f39fc51d6cbadbd8325a16bd71d1aaaf75dfe0fb48e989925a`
`573d116aa7cc5f5fe8738b9b4a7af70622e6ecea808074c6f8dba78d7ddf251f`
`8061bb22582325c8857c020c04732ded7fb356b841d280aa8bcf2cd5e2b6d40a`
`90985244c93529a62e6783dff745d947715b8c1f0a6604db09a3ea8c0bbbfaef`
`a3e8f1ff9b88830e9fa98e89043e0d0ee176cb71ae043da75463d10caca27a78`
`a5dcbc6e001530755d919c8e9fab1e00227ece126337a17aac0f2cd5ef44a133`
`d72ec6c53fae312653bc652259074ced66f213dc6dccf2f586792b6aca7735e0`
`dad5b8cc228e85f99cbcefa1b50b6eb19b5688c3f81933123aa53f40f75f85ea`
`e20980642f763160e0a26d35eda7a8fb9ea9537ddc202ab32b2dda62ab60fa96`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK
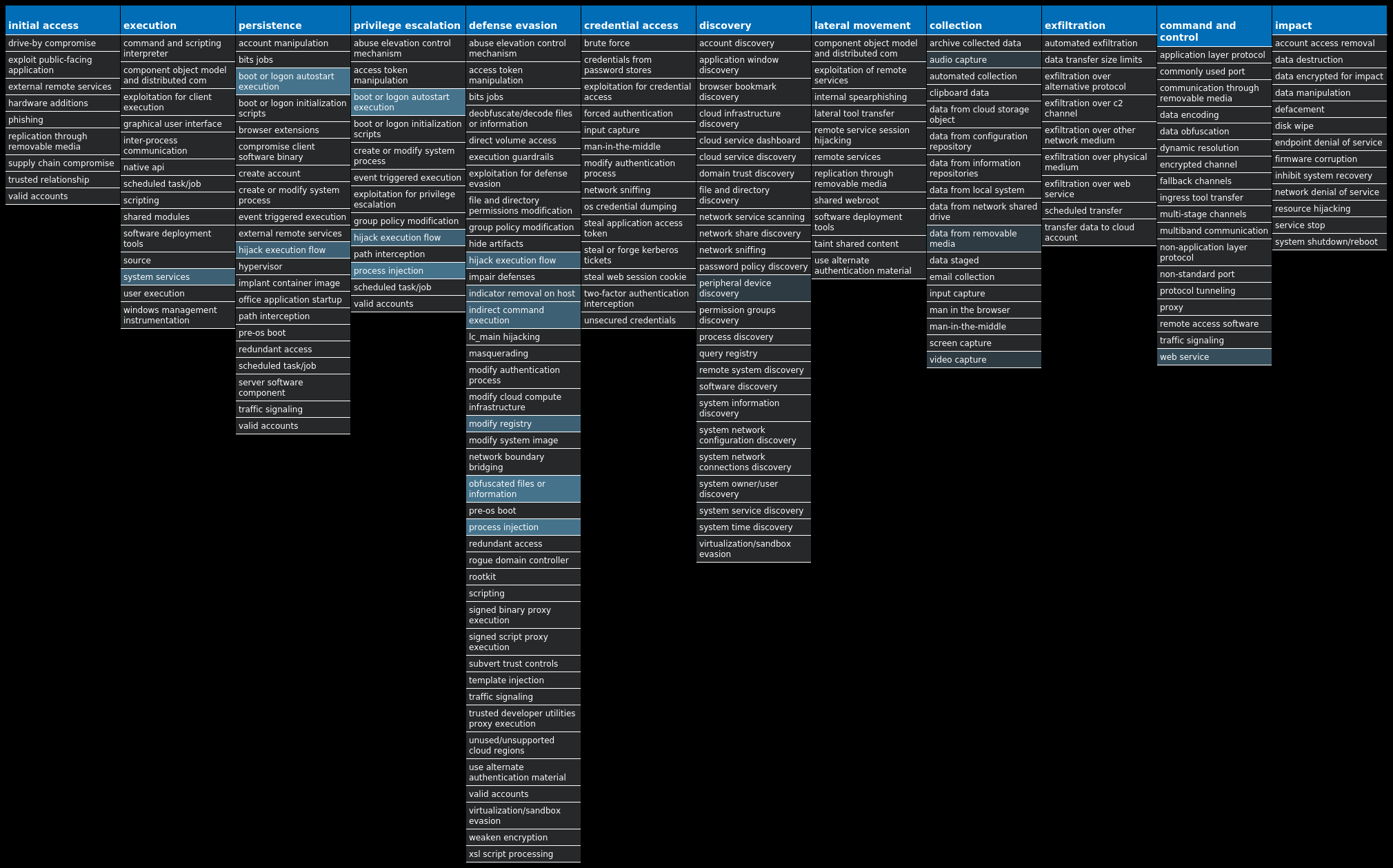
* * *
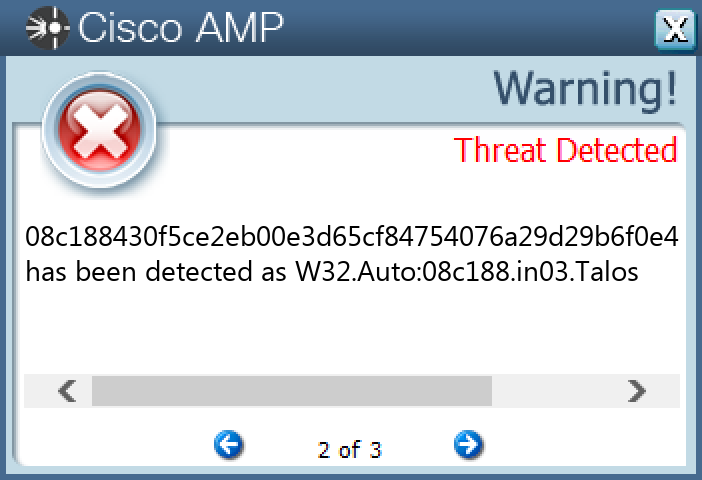
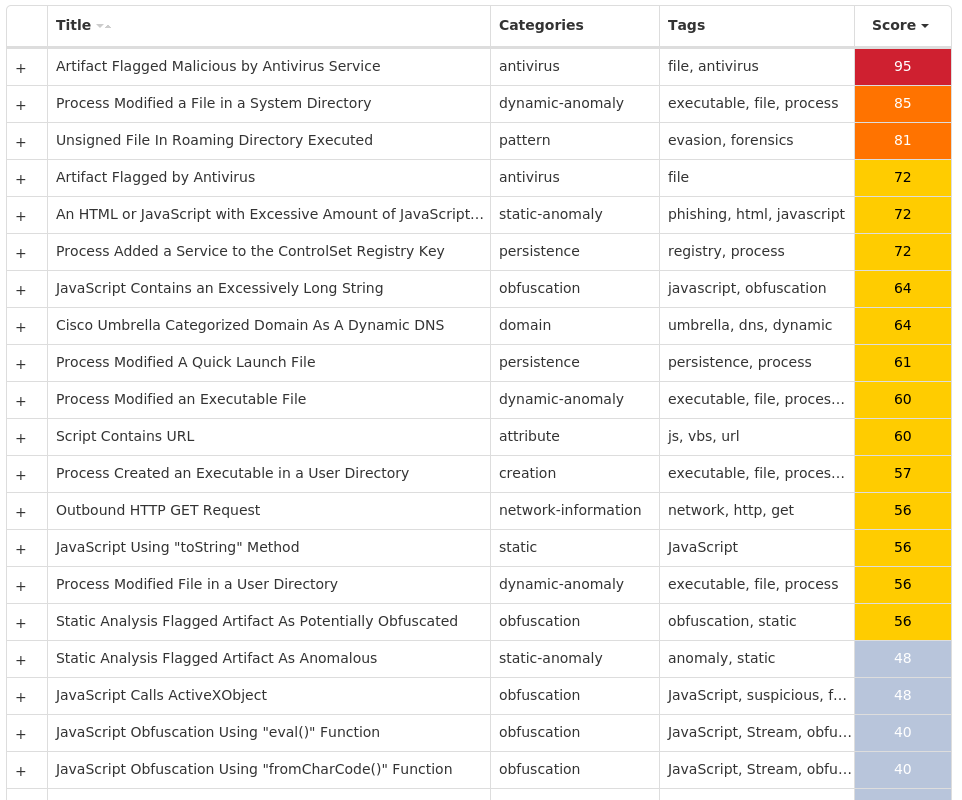
### Win.Malware.Barys-9980160-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 89 samples
Registry Keys| Occurrences
—|—
`SYSTEMCONTROLSET001SERVICESDNSSET`| 89
`SYSTEMCONTROLSET001SERVICESSTANS`| 89
`SYSTEMCONTROLSET001SERVICESZWEBNDS`| 89
`SYSTEMCONTROLSET001SERVICES`| 89
`SYSTEMCONTROLSET001SERVICES
Value Name: Type`| 89
`SYSTEMCONTROLSET001SERVICES
Value Name: Start`| 89
`SYSTEMCONTROLSET001SERVICES
Value Name: ErrorControl`| 89
`SYSTEMCONTROLSET001SERVICES
Value Name: Devname`| 89
`SYSTEMCONTROLSET001SERVICES
Value Name: ImagePath`| 89
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORERSTARTPAGE
Value Name: StartMenu_Balloon_Time`| 1
Mutexes| Occurrences
—|—
`Global4B565BD3ADE41C32BFE32C5F3FE1059D`| 89
`Global7632BD7EC1DECCA3E3E8`| 89
`GlobalD914CB10-68E3-098B-04C5-2DA38F00B471AD2-5C40-B890-3E86`| 89
`7632BD7EC1DECCA3E3E8`| 89
`4B565BD3ADE41C32BFE32C5F3FE1059D`| 89
`D914CB10-68E3-098B-04C5-2DA38F00B471AD2-5C40-B890-3E86`| 89
`XMX_XP2P_YT_3275`| 89
`XROExep_9725`| 89
`XROMain`| 89
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`204[.]27[.]62[.]70`| 89
`157[.]185[.]170[.]144`| 49
`157[.]185[.]177[.]205`| 19
`157[.]185[.]163[.]158`| 15
`180[.]95[.]234[.]241`| 10
`58[.]242[.]226[.]118`| 8
`113[.]1[.]0[.]101`| 7
`14[.]204[.]51[.]240`| 7
`221[.]204[.]209[.]149`| 6
`211[.]97[.]81[.]136`| 5
`116[.]130[.]221[.]52`| 5
`211[.]93[.]212[.]235`| 5
`211[.]93[.]212[.]144`| 4
`116[.]177[.]242[.]67`| 4
`157[.]185[.]158[.]198`| 3
`122[.]188[.]38[.]73`| 3
`211[.]93[.]211[.]219`| 3
`116[.]136[.]170[.]140`| 3
`14[.]204[.]51[.]250`| 2
`221[.]204[.]209[.]212`| 2
`116[.]153[.]4[.]126`| 2
`221[.]204[.]209[.]222`| 2
`116[.]162[.]164[.]140`| 2
`36[.]248[.]43[.]231`| 2
`138[.]113[.]159[.]20`| 2
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`www[.]58sky[.]com`| 89
`www[.]go890[.]com`| 89
`www[.]ip138[.]com`| 89
`ip[.]catr[.]cn`| 89
`ip[.]dnsexit[.]com`| 89
`wdx[.]go890[.]com`| 89
`cnwx[.]58ad[.]cn`| 1
Files and or directories created| Occurrences
—|—
`%HOMEPATH%FavoritesLinksWeb Slice Gallery.url`| 89
`%APPDATA%MicrosoftInternet ExplorerQuick LaunchLaunch Internet Explorer Browser.lnk`| 89
`%APPDATA%MicrosoftInternet ExplorerQuick LaunchUser PinnedTaskBarInternet Explorer.lnk`| 89
`%PUBLIC%DesktopMozilla Firefox.lnk`| 89
`%SystemRoot%CLOG.txt`| 89
`%SystemRoot%`| 75
`%ProgramData%`| 43
`%LOCALAPPDATA%`| 11
`%APPDATA%`| 10
`%SystemRoot%Ecwlfx.dll`| 1
`%ProgramFiles(x86)%qtYFJqH37c7de6f86d42b5c6b4d80d4c7d702dd7e3b91b16e889a993d9143dbf74951.exe`| 1
`%SystemRoot%TkfjQTfy.dll`| 1
`%ProgramData%gQggFKP1032d5ab9736fa60278d22aa886032e9f13a5ee3fb3b6fe33cee5dafacf71c3.exe`| 1
`%SystemRoot%iXPXOhc.dll`| 1
`%SystemRoot%AtPCE8nfVTo.sys`| 1
`%SystemRoot%IrivNwvL.dll`| 1
`%SystemRoot%mvdrxdQHKwLLAe.dll`| 1
`%SystemRoot%mvdrxdQIgFVsxMO.dll`| 1
`%SystemRoot%mvdrxdQJbVBclbtc.tmp`| 1
`%SystemRoot%mvdrxdQcmJAAa.dll`| 1
`%SystemRoot%mvdrxdQhpIfIHR.dll`| 1
`%SystemRoot%YbASbAvGJQweUYuK.dll`| 1
`%SystemRoot%YbASbAvGPnAmehBa.tmp`| 1
`%SystemRoot%YbASbAvGRsQAstc.dll`| 1
`%SystemRoot%YbASbAvGVAmVHnO.dll`| 1
*See JSON for more IOCs
#### File Hashes
`00c3d3d935cf466e6c49e7caae3bd1ab8981d5ce2ed7ea82ca7502907d986bd2`
`00e4eacd8244cb95c85e85ebe36f5346c1d83932885c73297094a47cec8cfb30`
`0286d495c8c312d7137c454819afc3cb758dbeb9c05e7dc5b862e33dc7b823ae`
`02faa23938688e793c12fd0943a29fc11140e496b1c2ca09ebd471f08798b78e`
`037c7de68f86d42b5c6b4d80d4c7d702dd7e3b91b16e889a993d9143dbf74951`
`03ca6e008111198b7f83edeb93c3a79b4d12b544732895f36816e0782dc23e23`
`03cbbdf8881067ef1496cb0570b06d18f8e366b6c50cad44e87485937b45bff1`
`0514abb557ccf4ddb5816faf36408564ad6f437c3d127d118d1cc06315ce8fca`
`054f446cbb85d2888d7efdc400d046030d4ac2a464d38ac462a5f5480970e513`
`08c188430f5ce2eb00e3d65cf84754076a29d29b6f0e4ae1c20fa0061078a671`
`09328e305bc112a33ee44e11fd761b70b5e38dafae6fd1f8b6cdf8ea91f66a28`
`0a532d1e28a71b6e10ca70f33c023bccc71fd893bb16a4c48e33568b2e55d304`
`0a786007500a90d32a5b6320b0963d95afefb773d4fee085b3e2d39a137d3e80`
`0afac1183779cd151cc6b14a7295a0c3c391390823dd8b3cf6127d6cf81f5c51`
`0cda14c54865aa6658ab09fe1f3868d37a783f92656b79e33a44a3782d05e098`
`0f7cc4f65420caf1e61a6d0ef6093efaddbc4a76b7d15c6bfb16bd2f9d745a13`
`1032d5ab9736fa60278d22aa886032e9f13a5ee3fb3b6fe33cee5ddafacf71c3`
`105dd942fc85f8673cdc6bedebd74d957eade073cd8f1f39c57643e9b8ec0842`
`10bf1b03551a065bd2409758531a416698374f9534682d12c59a33f17c091c87`
`112685ef356867dd420054f6f518deccbc954db40bd537d10ae0522885f2c3ab`
`12f8b850d7552377386d3ae4af5a29549cd7630ccf5893b8a3d4222134db64a3`
`139899c7e3759aceae5b5cc4c8715ae71da3a24ff2d22133302e5e9776b36fe7`
`13c08e48202968348a18df74d87be11cd997c90bbf91b1764fa438945562e9ac`
`15dcb870f787cf62e08f5e827fa2eddca2d0a7c2f11eb830c802870395d4ceee`
`164a59633d9bc80147208010c12bdbe557a39d54832e9d6da02279285578d968`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK
* * *
### Win.Ransomware.TeslaCrypt-9980162-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 15 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESSYSTEM
Value Name: EnableLinkedConnections`| 15
`.DEFAULTSOFTWARETRUEIMG`| 15
`SOFTWARETRUEIMG`| 15
`SOFTWARETRUEIMG
Value Name: ID`| 15
`Software`| 14
`Software
Value Name: data`| 14
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++vgwk`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++yqwy`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++cipe`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++doki`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++ibjn`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++qnch`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++tula`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++mesu`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++cqeu`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++ulau`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++vcta`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++tdao`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++pfgo`| 1
`SOFTWARE49FAE92EED457`| 1
`SOFTWARE49FAE92EED457
Value Name: data`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++ogri`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: +++hnnn`| 1
Mutexes| Occurrences
—|—
`9_9_9_9`| 15
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`139[.]59[.]22[.]50`| 15
`119[.]18[.]54[.]104`| 15
`104[.]112[.]19[.]80`| 14
`75[.]2[.]26[.]18`| 8
`23[.]3[.]13[.]129`| 8
`99[.]83[.]153[.]108`| 7
`23[.]3[.]13[.]152`| 3
`23[.]218[.]119[.]73`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`www[.]godaddy[.]com`| 15
`diwali2k15[.]in`| 15
`samuday[.]org`| 15
`maxmpl[.]com`| 15
`setprosports[.]info`| 15
`masterlegue[.]com`| 15
`toolaria[.]com`| 15
`apps[.]identrust[.]com`| 11
Files and or directories created| Occurrences
—|—
`%ProgramFiles%7-ZipLanglt.txt`| 15
`%ProgramFiles%7-ZipLanglv.txt`| 15
`%ProgramFiles%7-ZipLangmk.txt`| 15
`%ProgramFiles%7-ZipLangmn.txt`| 15
`%ProgramFiles%7-ZipLangmng.txt`| 15
`%ProgramFiles%7-ZipLangmng2.txt`| 15
`%ProgramFiles%7-ZipLangmr.txt`| 15
`%ProgramFiles%7-ZipLangms.txt`| 15
`%ProgramFiles%7-ZipLangnb.txt`| 15
`%ProgramFiles%7-ZipLangne.txt`| 15
`%ProgramFiles%7-ZipLangnl.txt`| 15
`%ProgramFiles%7-ZipLangnn.txt`| 15
`%ProgramFiles%7-ZipLangpa-in.txt`| 15
`%ProgramFiles%7-ZipLangpl.txt`| 15
`%ProgramFiles%7-ZipLangps.txt`| 15
`%ProgramFiles%7-ZipLangpt-br.txt`| 15
`%ProgramFiles%7-ZipLangpt.txt`| 15
`%ProgramFiles%7-ZipLangro.txt`| 15
`%ProgramFiles%7-ZipLangru.txt`| 15
`%ProgramFiles%7-ZipLangsa.txt`| 15
`%ProgramFiles%7-ZipLangsi.txt`| 15
`%ProgramFiles%7-ZipLangsk.txt`| 15
`%ProgramFiles%7-ZipLangsl.txt`| 15
`%ProgramFiles%7-ZipLangsq.txt`| 15
`%ProgramFiles%7-ZipLangsr-spc.txt`| 15
*See JSON for more IOCs
#### File Hashes
`04d4f30dd5f15c9b267d0a6742a9a9ef937805b68af1a5fb61d71e91d0b0ed96`
`04f600d977bd7b4235d43b3d2d29ed433b78435ab62197d7604230b97533c514`
`11777902d4032b544c3f39d542976d1ceba2027f8a13b48657d8f2adbe3621e7`
`2623054f04fa532dd2722f2f3a625bb7e75a9d0f3e2a9a40916a16e9d541b8b3`
`65eccc8382c9626f80f59c8510077986eeb7d2dbf4eb3bd834288d1512d52482`
`7112fcf7be31d84dea1ca57db000c4778ba949f58449d130424c704fbd5b68c6`
`8595a7e99fe4179b3998ba067c33fc2a9adbf20264672654631411c4a22e5e9a`
`85d1ee7d91a2e180a2b36d12c8ccfacfac58faf76f27fd6e5bb81c1c63745c55`
`8637deee136ebf5e12f628ede21c68f41de08ea0d1a9c824dd44ee68913200cf`
`8947aa09719857611f909b14eec93afbd6f2f79a93730958e98dae208730b210`
`8f9252108c9c3d3a51c9d7091eb77433182c778d3076c06c58b02e009217d302`
`a6794a139d3fff8ec52c4f47410295b1bb64ccb91793a5ba76b34aa7c6005867`
`c7fdfff40a2ea486671a8e9f940564b57fc20e94433d9524b20620d9c8d87763`
`d97fc2961c5e775ab73b47d3b6f8cbb53967e1906c381a1238ad0bb85b1be387`
`f384e5398f3e7f3504cbb09cbfd9c4a3a91c3263289c36da77ea193535cb9ada`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
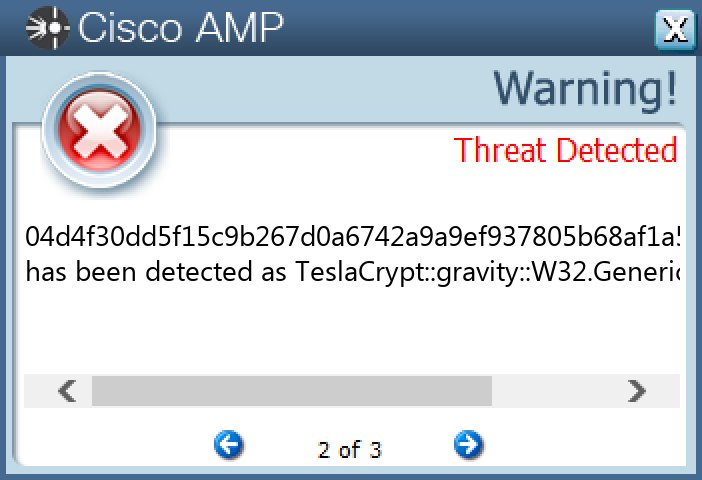
#### Secure Malware Analytics
#### MITRE ATT&CK
* * *
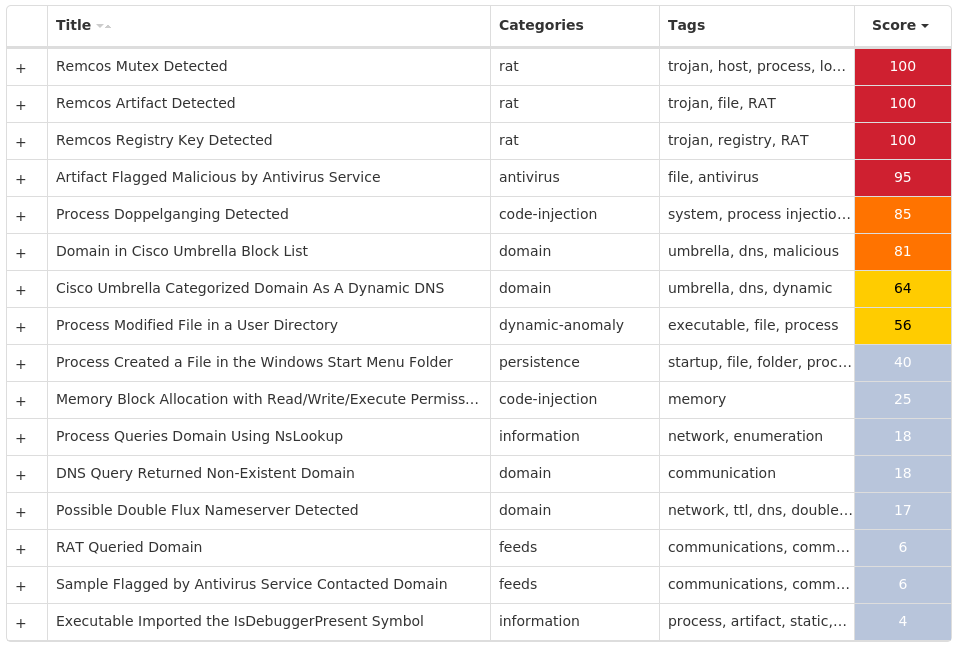
### Win.Dropper.Remcos-9980211-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 17 samples
Registry Keys| Occurrences
—|—
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: LanguageList`| 7
`S-1-5-21-2580483871-590521980-3826313501-500
Value Name: di`| 6
`ENVIRONMENT
Value Name: SEE_MASK_NOZONECHECKS`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-100`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-101`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-103`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32dhcpqec.dll,-102`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-1`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-2`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-4`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32napipsec.dll,-3`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-100`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-101`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-102`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32tsgqec.dll,-103`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32eapqec.dll,-100`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32eapqec.dll,-101`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32eapqec.dll,-102`| 6
`LOCAL SETTINGSMUICACHE8252C64B7E
Value Name: @%SystemRoot%system32eapqec.dll,-103`| 6
`SOFTWAREB97EB4B823F471563A37F56B08402D8E`| 4
`SOFTWAREB97EB4B823F471563A37F56B08402D8E
Value Name: [kl]`| 4
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: MyApp`| 2
`SOFTWAREB80B7F3A74788ADC36FE0A59F000A188`| 2
`SOFTWAREB80B7F3A74788ADC36FE0A59F000A188
Value Name: [kl]`| 2
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: newapp`| 1
Mutexes| Occurrences
—|—
`??kofhbzgh`| 17
`b97eb4b823f471563a37f56b08402d8e`| 4
`b80b7f3a74788adc36fe0a59f000a188`| 2
`Remcos_Mutex_Inj`| 1
`-`| 1
`LocalOfficeSharedLocks_BootMutex_00_S-1-5-18`| 1
`LocalOfficeSharedLocks_Heap_00_S-1-5-18`| 1
`Remcos_hgdfdv-X74SUU`| 1
`Global{fda47647-ddc0-4495-9b65-474fd1da1d12}`| 1
`3a1e266e-c6f2-4899-82cc-0a025adc38c1`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`41[.]190[.]3[.]209`| 4
`192[.]169[.]69[.]25`| 2
`3[.]230[.]36[.]58`| 2
`34[.]239[.]194[.]181`| 2
`37[.]235[.]1[.]177`| 1
`37[.]235[.]1[.]174`| 1
`54[.]174[.]11[.]26`| 1
`52[.]0[.]220[.]152`| 1
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`checkip[.]amazonaws[.]com`| 6
`oluya[.]duckdns[.]org`| 4
`brightgee[.]nsupdate[.]info`| 2
`moran101[.]duckdns[.]org`| 2
`larbivps[.]freemyip[.]com`| 1
`nnekamma[.]net-freaks[.]com`| 1
`alaincrestel1900[.]ddns[.]net`| 1
Files and or directories created| Occurrences
—|—
`%TEMP%00_.db`| 6
`%ProgramData%hhwwx.bmp`| 3
`%APPDATA%MyApp`| 2
`%APPDATA%MyAppMyApp.exe`| 2
`%APPDATA%newapp`| 1
`%APPDATA%newappnewapp.exe`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5Logs`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5LogsAdministrator`| 1
`%APPDATA%D19AB989-A35F-4710-83DF-7B2DB7EFE7C5run.dat`| 1
`%APPDATA%remcos`| 1
`%APPDATA%remcoslogs.dat`| 1
`%APPDATA%Imminent`| 1
`%APPDATA%ImminentLogs`| 1
`%APPDATA%ImminentMonitoring`| 1
`%APPDATA%ImminentMonitoringnetwork.dat`| 1
`%APPDATA%ImminentMonitoringsystem.dat`| 1
`%APPDATA%Postboxprofiles.ini`| 1
`%APPDATA%MicrosoftWindowsStart MenuProgramsStartupDuxyMxa.exe`| 1
`%APPDATA%ImminentLogs3-12-2022`| 1
#### File Hashes
`0d9c91a70cb6ef3ee203e3b567282e2c2516c616ffa9d30405d64121efc949ec`
`0e3e8fb6ae66a63a9b085514af208f1304f4b3255b17a4f2ba1990557835dc05`
`1441f8d1944520b632283d1efc22834dead226b3c19b921e5dacfa11e160e749`
`15cdb95a89888a9bfa89452569a16b207a7a7295ae61a10db6597d4789c4cc07`
`16f97d958631051e7def9b8771113567ca1b6b62faaa4431d5e2e9c22bd37499`
`1c3db036cfbbd66de809349070b0779e7e55bf95eba73bc03226a893157ea438`
`1f467584ef1ea939eee491e32224c2d6ad8a09e9e60632e24327287e38a62a95`
`5aaed2fc51f080c89338fbb2f2f6818ac81c171e741b1aa8cec594498257f041`
`67461eba2b2c3ab2a6aadca7f6b78a983db0a35c18848f21ed8b57a69aeb986b`
`6b0aa0eee21218db03f3723ddbd15470c4671b5a267d1a7c99a060d4c8ea7e5d`
`8886a57440f1867b19e5bfac523628cae4fa3b907f642bc7cab18b179f5929fa`
`9712034d5ede4484df452e0415e10a6b515c71e4ae7251eac7dc8508a9fa978a`
`98c5897c46204838ea5ef07c3ea40b3b0267f2d454de518794f9fa257afa1660`
`ae4d60251215497b30a1bc4dfcb126f948daedef4777650d2c03647aadb4ff64`
`bf5f3af820ab0d2c8117713369a31455fbaea57ee19a2a6474f850736c4e4eac`
`d59caa0f1181d3c3c21fbfe06c17621408ab1a3b6a10cdfea6b71e0659fbce91`
`ee65d409071b4d25b7d4c90c7658b3153bbd6b186402dd47e401865c12ddfa7b`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
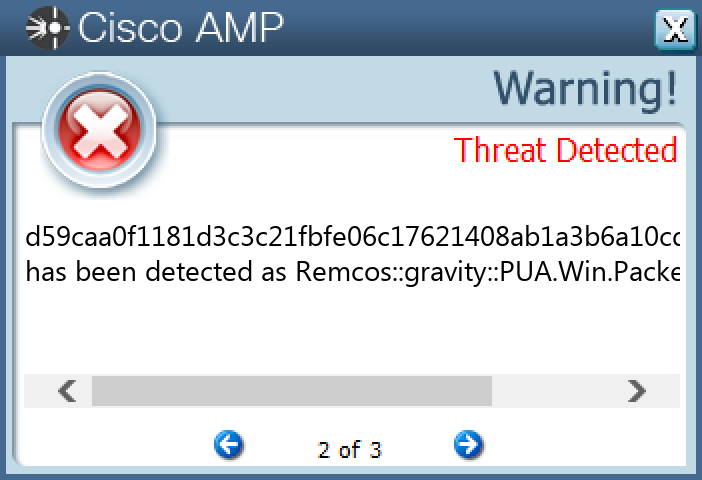
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
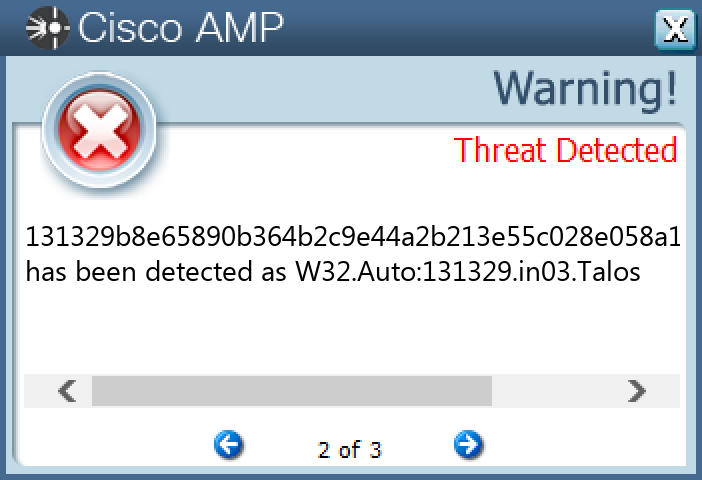
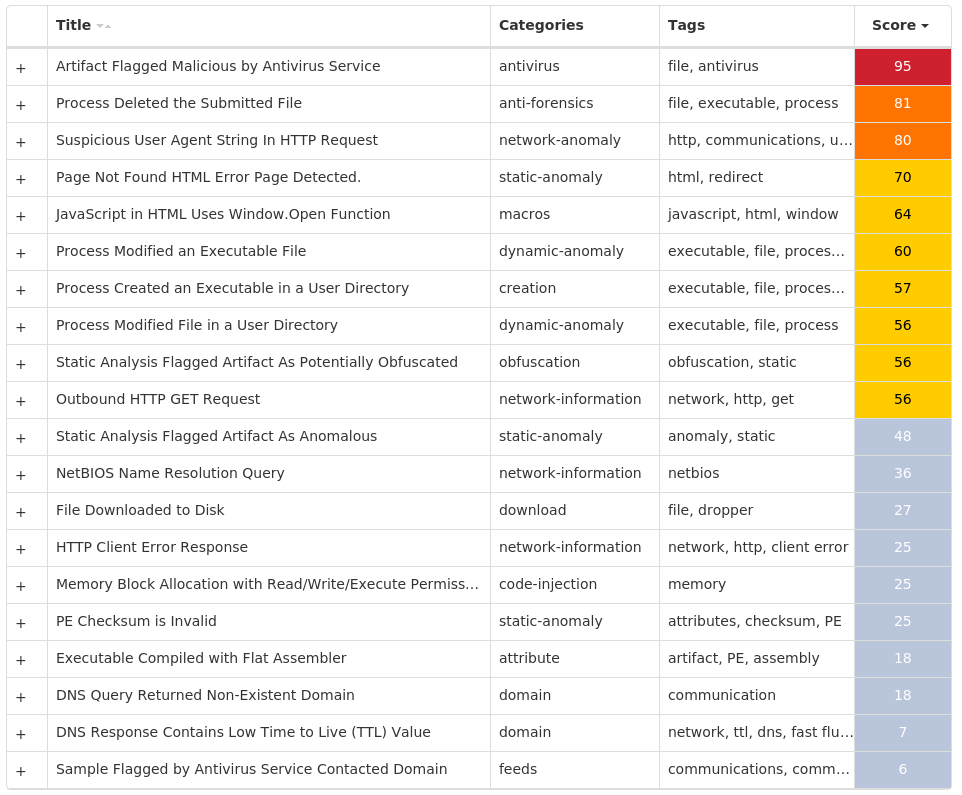
### Win.Downloader.Upatre-9980388-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 28 samples
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`204[.]11[.]56[.]48`| 28
`15[.]197[.]142[.]173`| 15
`3[.]33[.]152[.]147`| 13
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`clevelandeyedr[.]com`| 28
`goldbagshopping[.]com`| 28
`mumbaich[.]com`| 28
Files and or directories created| Occurrences
—|—
`%TEMP%viewpdf_updater.exe`| 28
`%TEMP%vmp018.exe`| 28
#### File Hashes
`03bd34b68369e6099343b0a7e6038af073510337b89e335d0341e547bf28cd79`
`0a49541ae72414290c682da49525b799a1789a2ece9ed3e8be0c03fdf76b8cac`
`0adfac375cc785cd223bd763a4c763a0be04554fb5864629d3ccc964e068e8a9`
`0b2162d48d4628dc0f6dc4b951c52d7d6e44d2ca39609807d2d21c1879e292f3`
`0c80f3060100a40cfade2a21921d24bcbece45aba2ee84982d1c9787b2025426`
`0f0fa1e9b6bcccc7e9b1ae2d8698faa61c8a9fbbebfd1a73ca0c0f9ccae65603`
`0f10bbae23aef2b3b1ecb1809792efd7c01971328bfe466d2f2ce3d8c2a55ae1`
`0f386a51c83c8ccf8d1ba888b985a0c98252ccd1c71ae88007b5e185c52783d7`
`106a09a4d636dff47577e4e61e2cb5288e8f362441d7ef616abb656653678162`
`10b56512d36259a0d2abb17ec619d3101cc5d7ccf03b71b3c12040625784434e`
`113d917fd3836e8c07605d1e0e33c289a503c62c23449e4e804620b047ec31d4`
`123cd6bf2891e5041fcfdd7bd870b6874617cda8fd220eb7d866be8f2918bd16`
`131329b8e65890b364b2c9e44a2b213e55c028e058a1b87887900941c77dab73`
`152cf54d2c6cdcb3445ec1f6d551d07de722dd7ca95b1e0ff9007dde5fcc9441`
`16f3108515a1c01e5c75a0e7410a8048f654538d2a018dfc03043fd5b73257f8`
`185484d712fd80d63470f507b5126023312ebe42ac74073de497bd4356f02df6`
`1caaabe8671c38c8352ad9de7ad60a4f485d42eb545c810c8a376a75a58790ab`
`1ccd596f95725fa85fb671208e48ac70b072b034f9321c8da00818e15cb9c742`
`1f1cf3dc196dc4eed263ea87fe90ef2ce1c998f777c1548e3d7c7e74439f7560`
`1f1d1d4d9d531552b6395c8e0b8bec1961d2986c1b5c813efd32ad6718afdda9`
`2132db193504ff23e252067ddadab293842140e733bb5cedaf1ad853ec28bc3e`
`239b9bcfc39e2b980610e415f0273123e5dc1de166b7c2c4804c1f2c4aeebad5`
`23a55cf164200b98f31ef1029f43ccc07199ba251a32292eca59fc34285f43a0`
`29836335873c0daa793f9943d4741f59c8f09a59db0a37d7591a1d2d8a889901`
`2c7a2f9853c7b80f87b980dbef0e69ec98e9808b306505d12f701da4f2d3ae1a`
*See JSON for more IOCs
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
#### MITRE ATT&CK

* * *
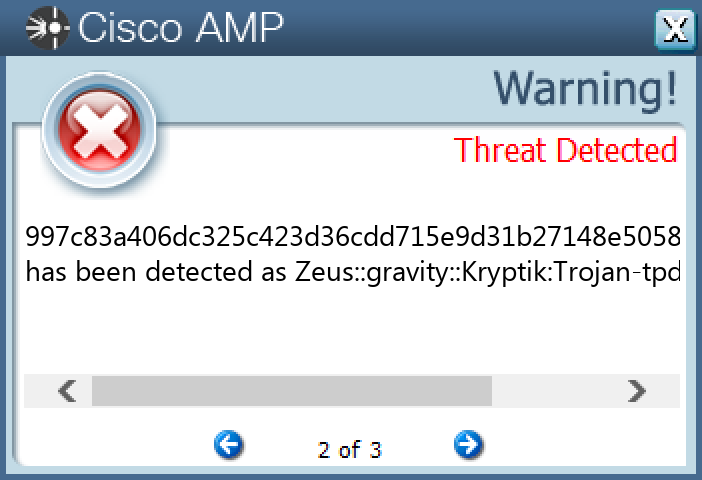
### Win.Dropper.Zeus-9980208-0
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 15 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTINTERNET EXPLORERPRIVACY
Value Name: CleanCookies`| 2
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: {2EC645E8-BA31-AD44-55BA-04D54CAC27C8}`| 2
`SOFTWAREMICROSOFTXYKE
Value Name: 10f2f269`| 1
`SOFTWAREMICROSOFTXYKE
Value Name: 31638d6j`| 1
`SOFTWAREMICROSOFTXYKE`| 1
`SOFTWAREMICROSOFTXYKE
Value Name: 14afb6i7`| 1
`SOFTWAREMICROSOFTEVAXEW
Value Name: 183d225f`| 1
`SOFTWAREMICROSOFTEVAXEW
Value Name: 2dh3617d`| 1
`SOFTWAREMICROSOFTEVAXEW`| 1
`SOFTWAREMICROSOFTEVAXEW
Value Name: 1bfaae7h`| 1
Mutexes| Occurrences
—|—
`Local{C8D239CA-C613-4B50-55BA-04D54CAC27C8}`| 2
`Local{C8D239CB-C612-4B50-55BA-04D54CAC27C8}`| 2
`Local{E9745CFB-A322-6AF6-55BA-04D54CAC27C8}`| 2
`GLOBAL{}`| 2
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`76[.]24[.]245[.]251`| 2
`98[.]250[.]118[.]10`| 2
`114[.]76[.]43[.]251`| 2
`62[.]103[.]170[.]90`| 2
`178[.]174[.]147[.]10`| 2
`64[.]60[.]153[.]210`| 2
`173[.]62[.]135[.]174`| 2
`68[.]44[.]81[.]30`| 2
`206[.]111[.]155[.]66`| 2
`74[.]235[.]18[.]69`| 2
`75[.]181[.]168[.]129`| 2
`69[.]255[.]22[.]49`| 2
`24[.]39[.]46[.]222`| 2
`2[.]30[.]33[.]121`| 2
`69[.]222[.]104[.]51`| 2
`72[.]184[.]101[.]206`| 2
`75[.]8[.]122[.]220`| 2
Files and or directories created| Occurrences
—|—
`%TEMP%tmp340c54f4.bat`| 1
`%APPDATA%Osep`| 1
`%APPDATA%Osepowycu.exe`| 1
`%APPDATA%Ugugvy`| 1
`%APPDATA%Ugugvyakoda.epy`| 1
`%TEMP%tmp3b41dc6e.bat`| 1
`%APPDATA%Loro`| 1
`%APPDATA%Loroonib.zya`| 1
`%APPDATA%Ucpyus`| 1
`%APPDATA%Ucpyusluiv.exe`| 1
#### File Hashes
`26a1f6f7c8eca58ed6568b85e4f4f35f616855cbcba3af27bee2ff8fdcfe2ff0`
`4268dfa589395d2cee82720b5551df6a65aa52e813fda2ca04a5c8c90a563791`
`5f277f9d1c5f7b817fac6f0ea6625a23a30939d5c5e70a5eb6a4a25592af3a08`
`6408c65c930c0cb9b207fcb115c4040f26f8d6da05c4bbe1f0d04016e2e46e70`
`997c83a406dc325c423d36cdd715e9d31b27148e50582707f0ec8efca860a2ae`
`a66d3290182a378e3158b4d57a7cecf56dc85a5818d100d1ddedd9036a41adfa`
`b5ad4fcb21a22c937c60988e5f9bb40f9e38709ce975774cb65c9c00b77f9b29`
`c4b0f7a29389eeb1110a5a0a505cf78ea6b2fbcf95e7e4b0405e5961c41f302c`
`c697324e22a8c228389bc58895927768633ac8a7785782c45da8a62c6b3af9a1`
`c8722fc3ee68b13c50cfb7bb8c6318e00695b3c6e87ebb6e408c25cf94a9ad30`
`e174ebf6dd6e28d9d8bdec04d296c2ec6b009ad60bc3b91ee77ed43822e1f92c`
`eaf72d6fee7187054be9e80294fe34a3838e1461428281d0863d022229b5fe6b`
`f10864f952225473322c79a8b35bc241c2c10f4402490c519994de6d3396233e`
`f5bda6ec6f7a04ba5764a58b5721851de32b4686cd13dc77ad5c31db881003bd`
`f648715400b16728844c3dfa51efe790c2665c3fc9844d85b39ebda340201447`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| N/A
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| N/A
WSA| N/A
#### Screenshots of Detection
#### Secure Endpoint
#### Secure Malware Analytics
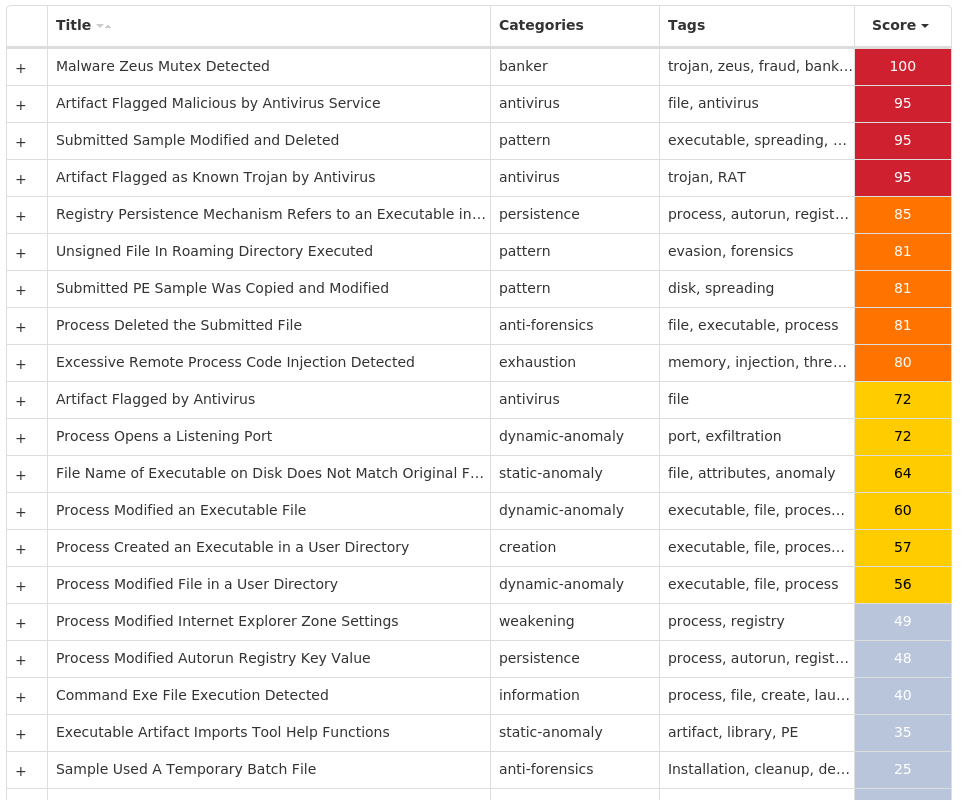
#### MITRE ATT&CK

* * *
### Win.Packed.Formbook-9980347-1
#### Indicators of Compromise
* IOCs collected from dynamic analysis of 21 samples
Registry Keys| Occurrences
—|—
`SOFTWAREMICROSOFTINTERNET EXPLORERINTELLIFORMSSTORAGE2`| 2
`SYSTEMCONTROLSET001SERVICESTASKKILL`| 2
`SYSTEMCONTROLSET001SERVICESTASKKILL
Value Name: ErrorControl`| 2
`SYSTEMCONTROLSET001SERVICESTASKKILL
Value Name: Type`| 2
`SYSTEMCONTROLSET001SERVICESTASKKILL
Value Name: Start`| 2
`SYSTEMCONTROLSET001SERVICESTASKKILL
Value Name: ImagePath`| 2
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: APP`| 2
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONPOLICIESSYSTEM
Value Name: EnableLUA`| 1
`SOFTWAREWOW6432NODEMOZILLAMOZILLA FIREFOX`| 1
`SOFTWAREWOW6432NODEMOZILLAMOZILLA FIREFOX20.0.1 (EN-US)MAIN`| 1
`SOFTWAREWOW6432NODEMOZILLAMOZILLA THUNDERBIRD`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONNOTIFICATIONS`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONNOTIFICATIONSSETTINGS`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: C72C6807598A4C8FAB7BF329B542ADF5`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 1BF87F4277E4430D8A09A4F766D4318D`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 0E0F6CEE3A5841B9A3412C81368FE961`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 0C74521719F24DE19A690E011E9E347F`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: CC0C0971387244718DE410BE7F7F6978`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 1429371977834B68AA3C3659F5DB5476`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 448B16A21F084978A57492DBB010F904`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: 319826B543B04630A7D69D8C16253318`| 1
`SOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN
Value Name: DE5E4284832A4DB59F2EB81EC0AE4422`| 1
Mutexes| Occurrences
—|—
`8-3503835SZBFHHZ`| 5
`S-1-5-21-2580483-1244450747859`| 2
`KN6QTO9VC-1JF942`| 2
`LocalMSCTF.Asm.MutexRemoteDesktop1`| 1
`LocalMSCTF.CtfMonitorInstMutexRemoteDesktop1`| 1
`S-1-5-21-2580483-1244982918396`| 1
`3L792CR58BH9WL-2`| 1
`327499-267B7KzeD`| 1
`Globalfb988221-72c1-11ed-9660-0015177d1530`| 1
`88PM4-A43-E4JG3B`| 1
`O880S08F13FUxFz8`| 1
`12PANRQ7W93XC-CJ`| 1
`PreIzXewwN`| 1
`S-1-5-21-2580483-1244891868769`| 1
`LQOPQ0P1XT3V3C8z`| 1
`S-1-5-21-2580483-1244172325477`| 1
`t5013175GUU3F24Y`| 1
IP Addresses contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`80[.]76[.]51[.]188`| 4
`34[.]102[.]136[.]180`| 2
`64[.]190[.]63[.]111`| 2
`44[.]230[.]85[.]241`| 1
`52[.]33[.]207[.]7`| 1
`23[.]227[.]38[.]74`| 1
`103[.]20[.]127[.]61`| 1
`217[.]160[.]0[.]249`| 1
`142[.]250[.]65[.]211`| 1
`209[.]17[.]116[.]163`| 1
`34[.]117[.]168[.]233`| 1
`185[.]87[.]187[.]245`| 1
`3[.]33[.]152[.]147`| 1
`8[.]212[.]24[.]67`| 1
`52[.]20[.]78[.]240`| 1
`3[.]232[.]242[.]170`| 1
`109[.]70[.]148[.]44`| 1
`192[.]64[.]112[.]158`| 1
`199[.]59[.]243[.]222`| 1
`45[.]33[.]6[.]223`| 1
`109[.]107[.]191[.]169`| 1
`65[.]108[.]204[.]97`| 1
`35[.]241[.]11[.]162`| 1
`15[.]197[.]136[.]110`| 1
`5[.]77[.]63[.]144`| 1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness| Occurrences
—|—
`api[.]ipify[.]org`| 2
`www[.]jimsnell[.]xyz`| 2
`www[.]kfcvn3[.]tech`| 1
`www[.]ednateixeirabrand[.]com`| 1
`www[.]wineshopsonline[.]com`| 1
`www[.]thejoy[.]run`| 1
`www[.]hfhxfcawc[.]xyz`| 1
`www[.]alfakhamahusa[.]net`| 1
`www[.]58worchester[.]info`| 1
`www[.]gracepropertyandevent[.]com`| 1
`www[.]7pijj[.]com`| 1
`www[.]laesperanzarealista[.]com`| 1
`www[.]oyshoppesay[.]pro`| 1
`www[.]longergolf[.]com`| 1
`www[.]mastermindenterprises[.]info`| 1
`www[.]kirkzero318[.]top`| 1
`www[.]exozuvy[.]bond`| 1
`www[.]stnicholaswtc[.]store`| 1
`www[.]reviewmgmtsystem[.]com`| 1
`www[.]karengillen[.]com`| 1
`www[.]kaity[.]site`| 1
`www[.]sensing[.]rest`| 1
`www[.]myrgroupinc[.]com`| 1
`www[.]niveaguide[.]com`| 1
`www[.]midtowndistrictsantafe[.]info`| 1
*See JSON for more IOCs
Files and or directories created| Occurrences
—|—
`%LOCALAPPDATA%Yandex`| 4
`%LOCALAPPDATA%YandexYaAddon`| 4
`%APPDATA%APP`| 2
`%APPDATA%APPAPP.exe`| 2
`x5cx55x73x65x72x73x5cx41x64x6dx69x6ex69x73x74x72x61x74x6fx72x5cx41x70x70x44x61x74x61x5cx4cx6fx63x61x6cx5cx54x65x6dx70x5cx418x438x441x443x441x2ex73x79x73`| 2
`%ProgramFiles%Microsoft DN1`| 1
`%TEMP%sqlite3.dll`| 1
`%TEMP%tmpC873.tmp`| 1
`%TEMP%sqlite3.def`| 1
`%TEMP%tmp81FF.tmp`| 1
`%TEMP%wx4tdx.zip`| 1
`%TEMP%tmp19E7.tmp`| 1
`%TEMP%tmpA57F.tmp`| 1
#### File Hashes
`03fcbab82603df2858f7d6fefdb6ae3cc8e17393af6d44f24634d28fccf3f181`
`0f9e27ec1ed021fd7375ca46f233c06b354d12d57aed44132208cd9308bfee11`
`1c1fcc4133af77f07d0c0299d0320aa9f447748ebead74b429f73c44d950e38b`
`22962d59a066795696464868700fa7d3f735bfdb494a7a879fb54668a0ca3d46`
`373a86e36f7e808a1db263b4b49d2428df4a13686da7d77edba7a6dd63790232`
`4068637c121888476533a3bbb16bec6bc3b4f81f7b9de635ef3576d56dc54c75`
`40df5a6e6dcadbe576ce4a8b01cfb82bf3f56a87bae674200e60814eab666c6d`
`41ea8f9a9f2a7aeb086dedf8e5855b0409f31e7793cbba615ca0498e47a72636`
`6c367333c677c2268df9deaff6ad4e711e73e53504aa1aa845bebfbfe635f1d2`
`70a6d43a56d267aa4fdac5a96722a2ff05e2ac1cc9ba996d173f0b3252e09898`
`76e129552a30fa5c914d9f946f40b2ec2bbbbeb4e5e2f324e70455725030e157`
`770e7d287fe352f12757ebfbb4502b10f61001630d70ddf414157b12e1f5e9a3`
`8a0d6e40e545d40956194230f03608859f2a47420a9b11b199142641bc6419ee`
`8fa81f6341b342afa40b7dc76dd6e0a1874583d12ea04acf839251cb5ca61591`
`95793df9284fe35c0491e5cfa36bc8f49fd426ccdf35f5fe2f098e07d160a4dc`
`ae4f3b6c43d5ea8ee68d862362d4e8d7b317889eb9abead948a9b791ad9d7071`
`b1c9b356c50230629c4697b0527fd7a0fa8d6f0e8342a1eb5b5a4f90d8f0eb86`
`cd4c821e329ec1f7bfe7ecd39a6020867348b722e8c84a05c7eb32f8d5a2f4db`
`d5eda02ff2f05d1e0d06a69018de463ab36497048a1ef2b69af93aa76ccfc07d`
`f570b6c46a5bb5a8757b1125c7d4b5d4aca2c7e9354ed1d34b78fd4f08280e30`
`f6aba045ca29ba39bbdcb2f8bde63efc971d138f88bf03aea2d13ddec88a0483`
#### Coverage
Product| Protection
—|—
Secure Endpoint| 
Cloudlock| N/A
CWS| 
Email Security| 
Network Security| 
Stealthwatch| N/A
Stealthwatch Cloud| N/A
Secure Malware Analytics| 
Umbrella| 
WSA| 
#### Screenshots of Detection
#### Secure Endpoint
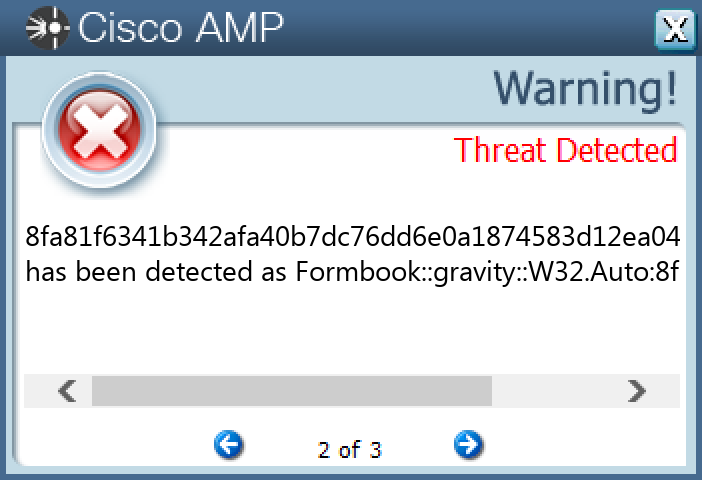
#### Secure Malware Analytics
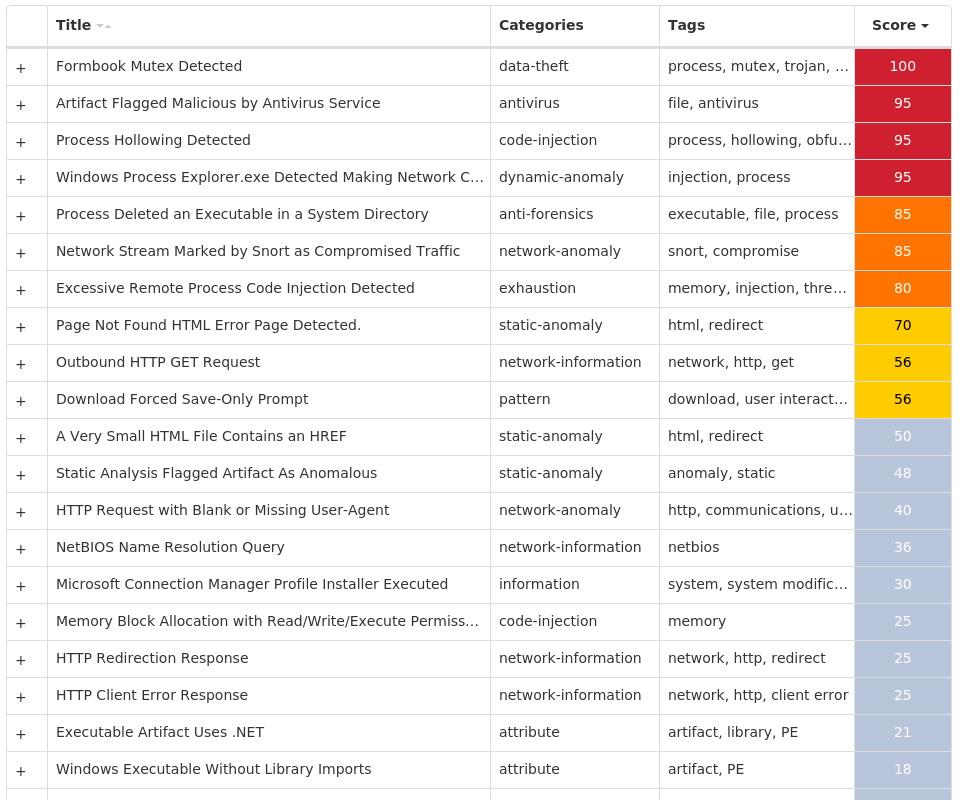
#### MITRE ATT&CK

* * *Read More

