[]()
D4TA-HUNTER is a tool created in order to automate the collection of information about the employees of a company that is going to be audited for ethical hacking.
In addition, in this tool we can find in the “search company” section by inserting the domain of a company, [emails]( “emails” ) of employees, [subdomains]( “subdomains” ) and IP’s of servers.
# GET API KEY
Register on
# Install
git clone https://github.com/micro-joan/D4TA-HUNTER
cd D4TA-HUNTER/
chmod +x run.sh
./run.sh
After executing the application launcher you need to have all the components installed, the launcher will check one by one, and in the case of not having any component installed it will show you the statement that you must enter to install it:
[]()
# Use
First you must have a free or paid api-key from BreachDirectory.org, if you don’t have one and do a search D4TA-HUNTER provides you with a guide on how to get one.
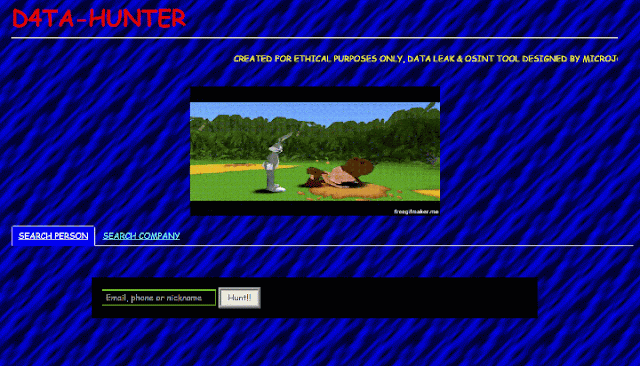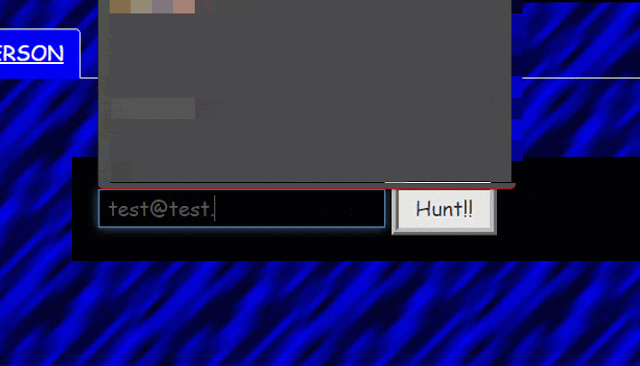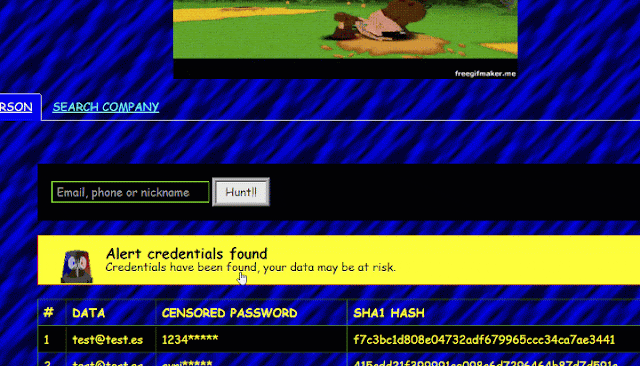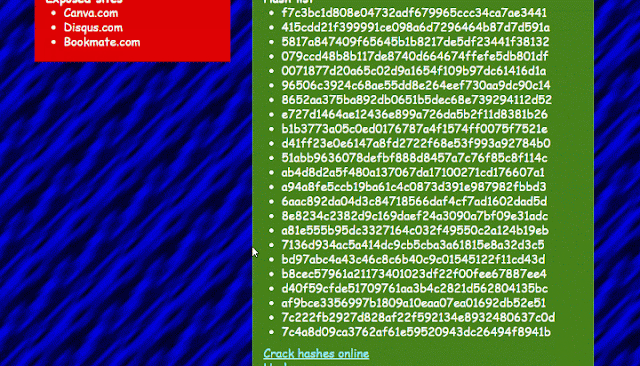
Once you have the api-key you will be able to search for emails, with the advantage of showing you a list of all the password hashes ready for you to copy and paste into one of the online resources provided by D4TA-HUNTER to crack [passwords]( “passwords” ) 100 % free.
[]()
You can also insert a domain of a company and D4TA-HUNTER will search for employee emails, subdomains that may be of interest together with IP’s of machines found:
[]()
# Apis and tools
Service | Functions | Status
—|—|—
BreachDirectory.org | Email, phone or nick leaks |
â
ï
(free plan)
[TheHarvester]( “TheHarvester” ) | Domains and emails of company |
â
Free
[Kalitorify]( “Kalitorify” ) | Tor search |
â
Free
Video Demo:
My website:
My blog:
Buy me a coffee:
# DISCLAIMER
This [toolkit]( “toolkit” ) contains materials that can be potentially damaging or dangerous for social media. Refer to the laws in your province/country before accessing, using,or in any other way utilizing this in a wrong way.
This Tool is made for educational purposes only. Do not attempt to violate the law with anything contained here. If this is your intention, then Get the hell out of here!
**[Download D4TA-HUNTER]( “Download D4TA-HUNTER” )**Read More

