[ ]()
Amazon Web Services (AWS) has resolved a cross-tenant vulnerability in its platform that could be weaponized by an attacker to gain unauthorized access to resources.
The issue relates to a [confused deputy problem](), a type of privilege escalation where a program that doesn’t have permission to perform an action can coerce a more-privileged entity to perform the action.
The shortcoming was reported by Datadog to AWS on September 1, 2022, following which a patch was shipped on September 6.
“This attack abuses the AppSync service to assume [identity and access management] [roles]() in other AWS accounts, which allows an attacker to pivot into a victim organization and access resources in those accounts,” Datadog researcher Nick Frichette [said]() in a report published last week.
In a coordinated disclosure, Amazon [said]() that no customers were affected by the vulnerability and that no customer action is required.
It described it as a “case-sensitivity parsing issue within AWS AppSync, which could potentially be used to bypass the service’s cross-account role usage validations and take action as the service across customer accounts.”
[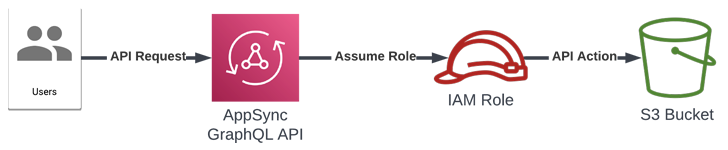]()
AWS AppSync [offers]() developers GraphQL APIs to retrieve or modify data from multiple data sources as well as automatically sync data between mobile and web applications and the cloud.
The service can also be used to integrate with other AWS services through specific roles designed to perform the necessary API calls with the required IAM permissions.
While AWS does have safeguards in place to prevent AppSync from assuming arbitrary roles by validating the role’s Amazon Resource Name (ARN), the problem stems from the fact that the check could be trivially bypassed by passing the “[serviceRoleArn]()” parameter in a lower case.
This behavior could then be exploited to provide the identifier of a role in a different AWS account.
“This vulnerability in AWS AppSync allowed attackers to cross account boundaries and execute AWS API calls in victim accounts via IAM roles that trusted the AppSync service,” Frichette said.
“By using this method, attackers could breach organizations that used AppSync and gain access to resources associated with those roles.”
Found this article interesting? Follow THN on [Facebook](), [Twitter _ï_]() and [LinkedIn]() to read more exclusive content we post.Read More

