[]()
The Australian Federal Police (AFP) on Monday disclosed it’s working to gather “crucial evidence” and that it’s collaborating with overseas law enforcement authorities following the hack of telecom provider Optus.
“Operation Hurricane has been launched to identify the criminals behind the alleged breach and to help shield Australians from identity fraud,” the AFP [said]() in a statement.
The development comes after Optus, Australia’s second-largest wireless carrier, [disclosed]() on September 22, 2022, that it was a victim of a cyberattack. It claimed it “immediately shut down the attack” as soon as it came to light.
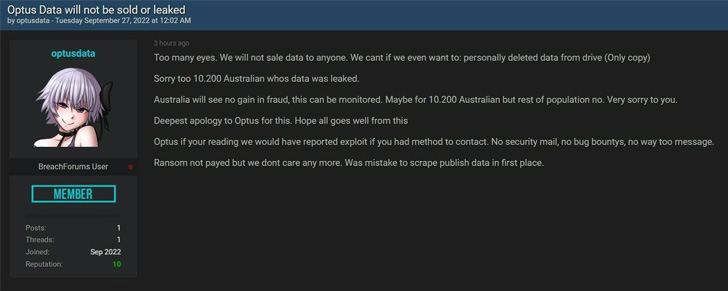
The threat actor behind the breach also briefly released a sample of 10,200 records from the breach putting those users at heightened risk of fraud in addition to asking for $1 million as part of an extortion demand. The dataset has since been taken down, with the attacker also claiming to have deleted the only copy of the stolen data.
Optus, which is a wholly-owned subsidiary of Singtel, is [estimated]() to have over 10 million subscribers as of December 2019. The telco did not reveal when the incident took place.
Although Optus has not yet confirmed how many customers may have been impacted by the breach, it said the unauthorized access could have exposed their names, dates of birth, phone numbers, email addresses, and, for a subset of customers, addresses, ID document numbers such as driver’s license or passport numbers.
[]()
To make matters worse, information belonging to former customers are also said to have been affected, raising concerns about how long telecom providers should be required to retain such data. Payment details and account passwords, however, have not been compromised.
Optus, in its privacy policy, notes that while customers can request to have their personal information deleted, it may not always be able to do so, citing legal obligations. “The [Telecommunications Interception and Access Act 1979]() (Cth) may require us to hold some of your personal information for a period of time,” it [says]().
The company has yet to share more details on how the hack took place, but according to ISMG security journalist [Jeremy Kirk](), it involved gaining access through an unauthenticated API endpoint “api.www.optus.com[.]au,” which appears to have been [publicly accessible as early as January 2019]().
Optus customers are recommended to take steps to secure their online accounts, primarily bank and financial services, as well as monitor them for any suspicious activity and be on the lookout for potential scams and phishing attempts.
To mitigate the risk of identity theft, the company further said it’s offering its “most affected current and former customers” a free 12-month subscription to credit monitoring and identity protection service Equifax Protect.
“Scammers may use your personal information to contact you by phone, text or email,” the Australian Competition and Consumer Commission (ACCC) [said](). “Never click on links or provide personal or financial information to someone who contacts you out of the blue.”
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More

