[]()
Researchers have disclosed a new severe Oracle Cloud Infrastructure (OCI) vulnerability that could be exploited by users to access the virtual disks of other Oracle customers.
“Each virtual disk in Oracle’s cloud has a unique identifier called OCID,” Shir Tamari, head of research at Wiz, [said]() in a series of tweets. “This identifier is not considered secret, and organizations do not treat it as such.”
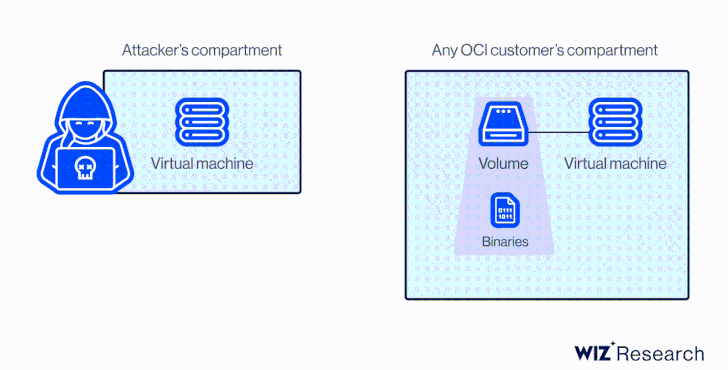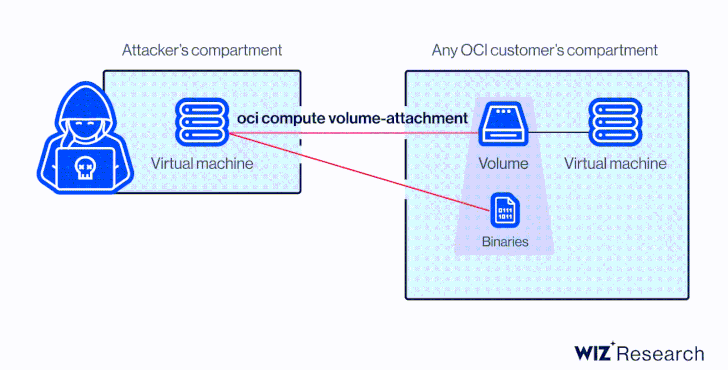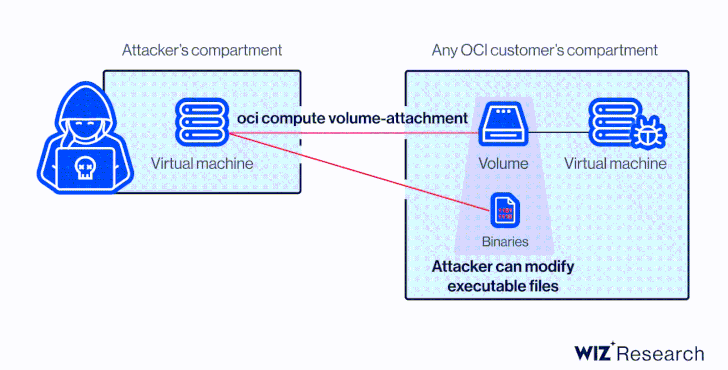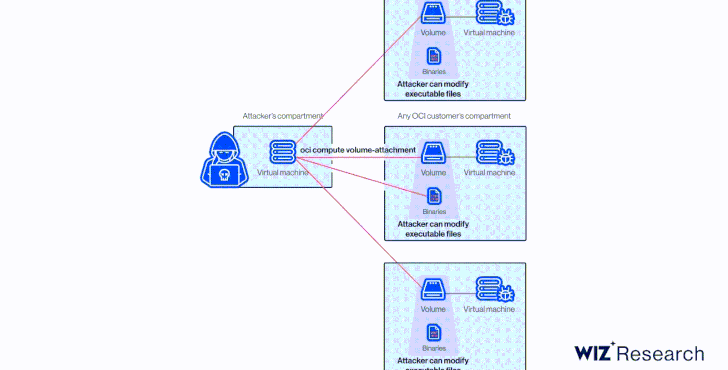
“Given the OCID of a victim’s disk that is not currently attached to an active server or configured as shareable, an attacker could ‘attach’ to it and obtain read/write over it,” Tamari added.
The cloud security firm, which dubbed the tenant isolation vulnerability “[**AttachMe**](),” said Oracle [patched the issue]() within 24 hours of responsible disclosure on June 9, 2022.
[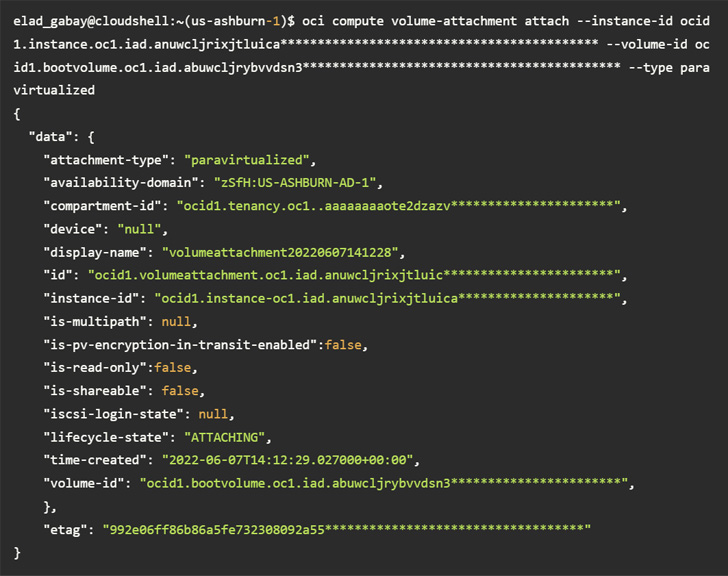]()
—
Accessing a volume using the CLI without sufficient permissions
At its core, the vulnerability is rooted in the fact that a disk could be attached to a compute instance in another account via the Oracle Cloud Identifier (OCID) without any explicit authorization.
This meant that an attacker in possession of the OCID could have taken advantage of AttachMe to access any storage volume, resulting in data exposure, exfiltration, or worse, alter boot volumes to gain code execution.
Besides knowing the OCID of the target volume, another prerequisite to pull off the attack is that the adversary’s instance must be in the same Availability Domain (AD) as the target.
“Insufficient validation of user permissions is a common bug class among cloud service providers,” Wiz researcher Elad Gabay said. “The best way to identify such issues is by performing rigorous code reviews and comprehensive tests for each sensitive API in the development stage.”
The findings arrive nearly five months after Microsoft [addressed]() a pair of issues with the Azure Database for PostgreSQL Flexible Server that could result in unauthorized cross-account database access in a region.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More
References

Back to Main


