[]()
Microsoft on Thursday warned of a consumer-facing attack that made use of rogue OAuth applications on compromised cloud tenants to ultimately seize control of Exchange servers and spread spam.
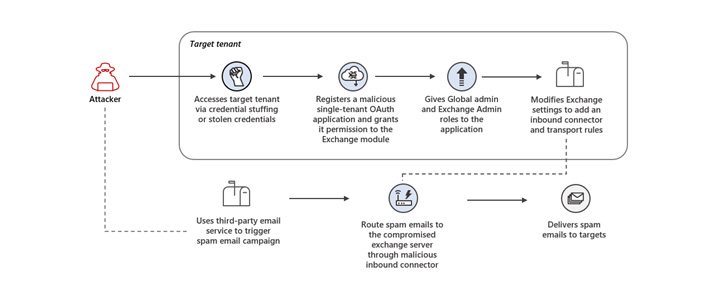
“The threat actor launched credential stuffing attacks against high-risk accounts that didn’t have multi-factor authentication (MFA) enabled and leveraged the unsecured administrator accounts to gain initial access,” the Microsoft 365 Defender Research Team said.
The unauthorized access to the cloud tenant permitted the adversary to register a malicious OAuth application and grant it elevated permissions, and eventually modify Exchange Server settings to allow inbound emails from specific IP addresses to be routed through the compromised email server.
“These modifications to the Exchange server settings allowed the threat actor to perform their primary goal in the attack: sending out spam emails,” Microsoft [said](). “The spam emails were sent as part of a deceptive sweepstakes scheme meant to trick recipients into signing up for recurring paid subscriptions.”
[]()
The email messages urged the recipients to click on a link to receive a prize, doing so which redirected the victims to a landing page that asked the victims to enter their credit card details for a small shipping fee to collect the reward.
The threat actor further carried out a number of steps to evade detection and continue its operations for extended periods of time, including using the malicious OAuth application weeks or even months after it was deployed and deleting the modifications made to the Exchange Server after each spam campaign.
Microsoft’s threat intelligence division said that the adversary has been actively running spam email campaigns for several years, typically sending high volumes of spam emails in short bursts through a variety of methods.
Although the primary goal of the attack appears to be to trick unwitting users into signing up for unwanted subscription services, it could have posed a far more serious threat had the same technique been used to steal credentials or distribute malware.
“While the follow-on spam campaign targets consumer email accounts, this attack targets enterprise tenants to use as infrastructure for this campaign,” Microsoft said. “This attack thus exposes security weaknesses that could be used by other threat actors in attacks that could directly impact affected enterprises.”
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More

