[]()
Google’s Threat Analysis Group (TAG) on Thursday disclosed it had acted to block as many as 36 malicious domains operated by hack-for-hire groups from India, Russia, and the U.A.E.
In a manner analogous to the [surveillanceware ecosystem](), hack-for-hire firms equip their clients with capabilities to enable targeted attacks aimed at corporates as well as activists, journalists, politicians, and other high-risk users.
Where the two stand apart is that while customers purchase the spyware from commercial vendors and then deploy it themselves, the operators behind hack-for-hire attacks are known to conduct the intrusions on their clients’ behalf in order to obscure their role.
“The hack-for-hire landscape is fluid, both in how the attackers organize themselves and in the wide range of targets they pursue in a single campaign at the behest of disparate clients,” Shane Huntley, director of Google TAG, [said]() in a report.
“Some hack-for-hire attackers openly advertise their products and services to anyone willing to pay, while others operate more discreetly selling to a limited audience.”
A recent campaign mounted by an Indian hack-for-hire operator is said to have targeted an IT company in Cyprus, an education institution in Nigeria, a fintech company in the Balkans, and a shopping company in Israel, indicating the breadth of victims.
[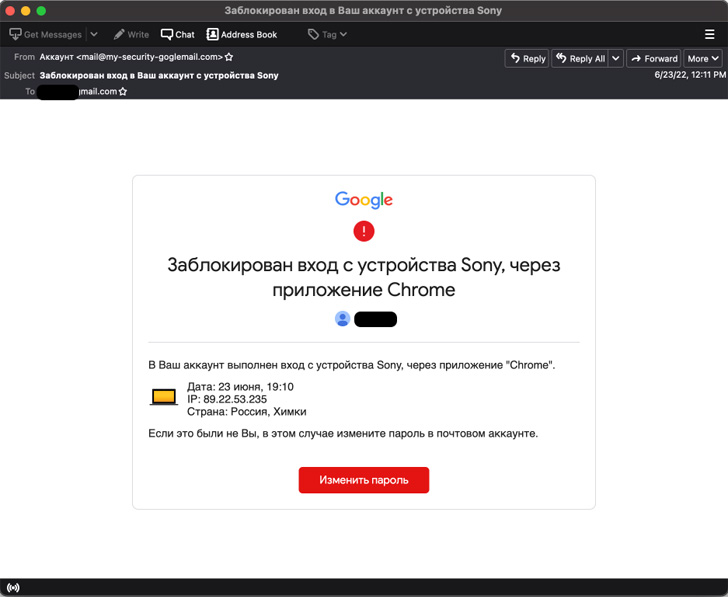]()
The Indian outfit, which Google TAG said it’s been tracking since 2012, has been linked to a string of credential phishing attacks with the goal of harvesting login information associated with government agencies, Amazon Web Services (AWS), and Gmail accounts.
The campaign involves sending spear-phishing emails containing a rogue link that, when clicked, launches an attacker-controlled phishing page designed to siphon credentials entered by unsuspecting users. Targets included government, healthcare, and telecom sectors in Saudi Arabia, the United Arab Emirates, and Bahrain.
Google TAG attributed the Indian hack-for-hire actors to a firm called Rebsec, which, according to its dormant [Twitter account](), is short for “[Rebellion Securities]()” and is based in the city of Amritsar. The company’s [website](), down for “maintenance” as of writing, also claims to offer corporate espionage services.
A similar set of credential theft attacks targeting journalists, European politicians, and non-profits has been linked to a Russian actor dubbed [Void Balaur](), a cyber mercenary group first documented by Trend Micro in November 2021.
[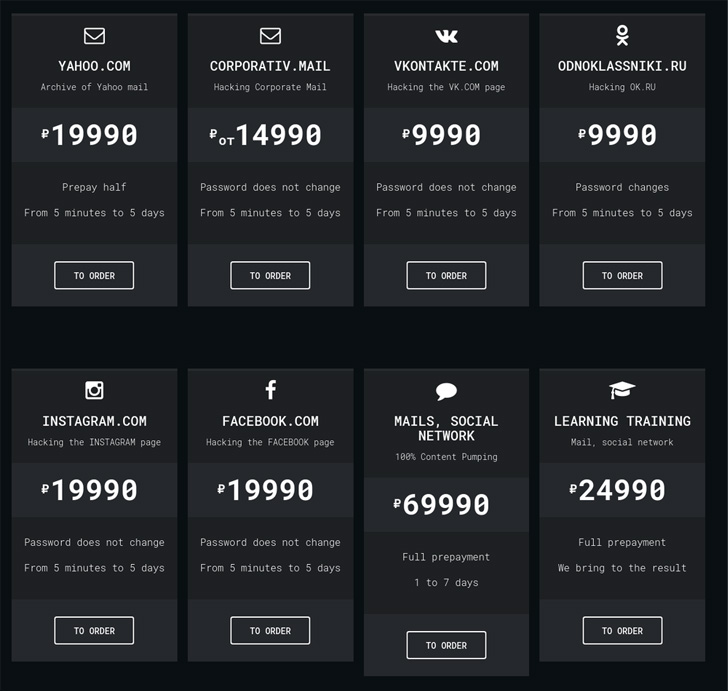]()
Over the past five years, the collective is believed to have singled out accounts at major webmail providers like Gmail, Hotmail, and Yahoo! and regional webmail providers like abv.bg, mail.ru, inbox.lv, and UKR.net.
Lastly, TAG also detailed the activities of a group based in the U.A.E. and has connections to the original developers of a remote access trojan called [njRAT]() (aka [H-Worm]() or [Houdini]()).
The phishing attacks, as previously uncovered by [Amnesty International]() in 2018, entail using password reset lures to steal credentials from targets in government, education, and political organizations in the Middle East and North Africa.
Following the account compromise, the threat actor maintains persistence by granting an OAuth token to a legitimate email application like Thunderbird, generating an [App Password]() to access the account via IMAP, or linking the victim’s Gmail account to an adversary-owned account on a third-party mail provider.
The findings come a week after Google TAG revealed details of an Italian spyware company named RCS Lab, whose “[Hermit]()” hacking tool was used to target Android and iOS users in Italy and Kazakhstan.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More

