[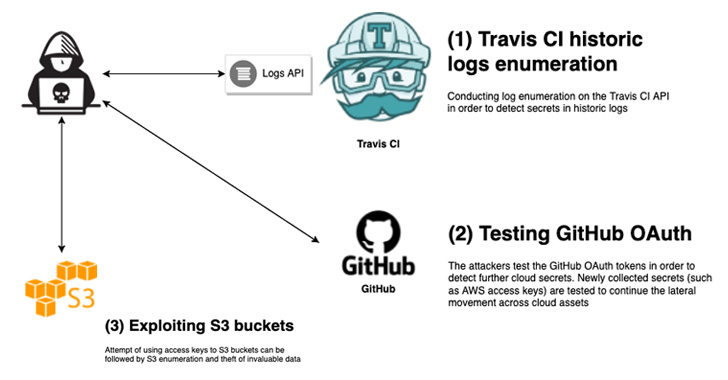]()
An unpatched security issue in the Travis CI API has left tens of thousands of developers’ user tokens exposed to potential attacks, effectively allowing threat actors to breach cloud infrastructures, make unauthorized code changes, and initiate supply chain attacks.
“More than 770 million logs of free tier users are available, from which you can easily extract tokens, secrets, and other credentials associated with popular cloud service providers such as GitHub, AWS, and Docker Hub,” researchers from cloud security firm Aqua [said]() in a Monday report.
Travis CI is a [continuous integration]() service used to build and test software projects hosted on cloud repository platforms such as GitHub and Bitbucket.
The issue, previously reported in 2015 and [2019](), is rooted in the fact that the [API]() permits access to historical logs in cleartext format, enabling a malicious party to even “fetch the logs that were previously unavailable via the API.”
The logs go all the way back to January 2013 and up until May 2022, ranging from log numbers 4,280,000 to 774,807,924, which are used to retrieve a unique cleartext log through the API.
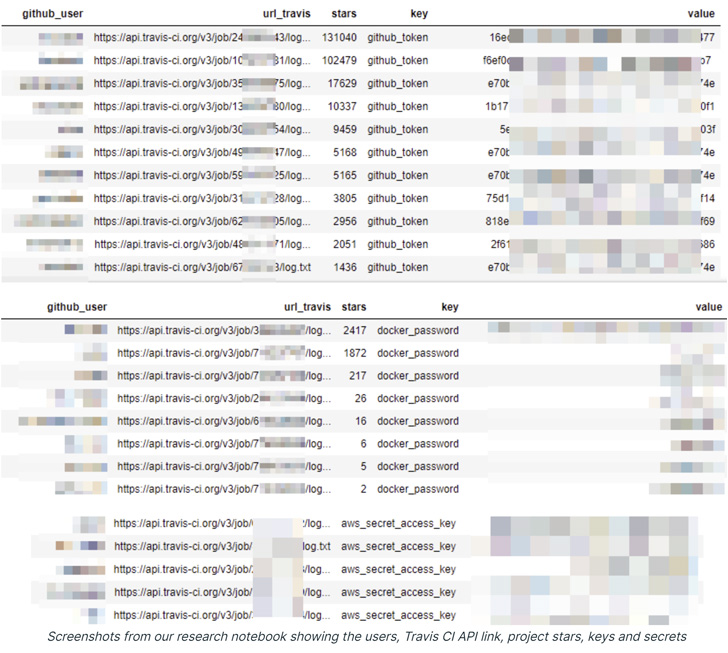
What’s more, further analysis of 20,000 logs revealed as many as 73,000 tokens, access keys, and other credentials associated with various cloud services like GitHub, AWS, and Docker Hub.
[]()
This is despite Travis CI’s attempts to [rate-limit the API]() and [automatically filter out]() secure environment variables and tokens from build logs by displaying the string “[secure]” in their place.
One of the critical insights is that while “github_token” was obfuscated, 20 other variations of this token that followed a different naming convention including github_secret, gh_token, github_api_key, and github_secret weren’t masked by Travis CI.
“Travis CI slowed down the velocity of API calls, which hinders the ability to query the API,” the researchers said. “In this case however, this was not enough. A skilled threat actor can find a workaround to bypass this.”
“However, combining the ease of accessing the logs via the API, incomplete censoring, accessing ‘restricted’ logs, and a weak process for rate limiting and blocking access to the API, coupled with a large number of potentially exposed logs, results in a critical situation.”
Travis CI, in response to the findings, has said the issue is “by design,” necessitating that users follow best practices to avoid leaking secrets in build logs and periodically rotate tokens and secrets.
The findings are particularly significant in the wake of an [April 2022 attack campaign]() that leveraged stolen OAuth user tokens issued to Heroku and Travis CI to escalate access to NPM infrastructure and clone select private repositories.
Found this article interesting? Follow THN on [Facebook](), [Twitter _?_]() and [LinkedIn]() to read more exclusive content we post.Read More

